Okay, so you want to figure out why fast.com below doesn't turn into a link, dont you? Okay, let's walk through the process in this thread and find how to reverse-engineer this trick. https://twitter.com/SwiftOnSecurity/status/998334747125407744
First, know that everything you see on a screen is potentially a lie. You need machine analysis to figure out what's actually inside my tweet, and to know why Twitter isn't creating the link, which would normally look like this: http://fast.com
We need a Unicode analyzer. Unicode is how modern systems encode text, and it has thousands of weird tricks you can't see.
1.) Copy this text into your clipboard:
fast.com
2.) Search for a Unicode analyzer on Google, or use this: http://www.fontspace.com/unicode/analyzer/
3.) Paste and hit "GO!"
1.) Copy this text into your clipboard:
fast.com
2.) Search for a Unicode analyzer on Google, or use this: http://www.fontspace.com/unicode/analyzer/
3.) Paste and hit "GO!"
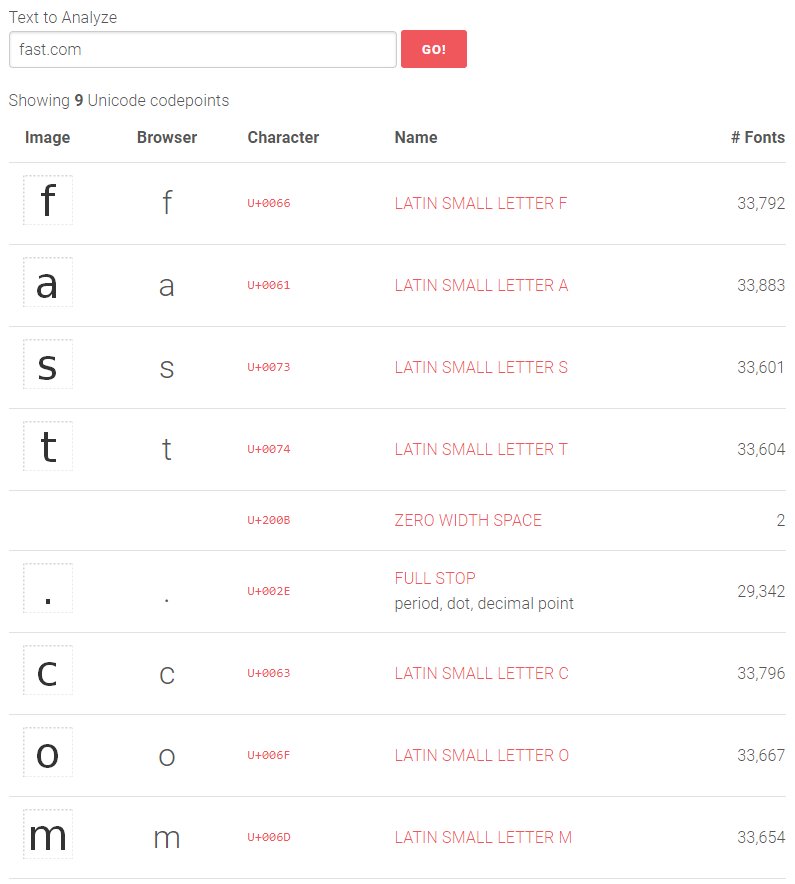
Okay, here's the analysis of fast.com.
Everything looks good, until the fifth line.
"U+200BZERO WIDTH SPACE"
What the heck is that? As I said before, there are thousands of typesetting tricks required for machines to properly manipulate text in all its forms, and this is one.
Everything looks good, until the fifth line.
"U+200BZERO WIDTH SPACE"
What the heck is that? As I said before, there are thousands of typesetting tricks required for machines to properly manipulate text in all its forms, and this is one.
Here's the Wikipedia article on the ZERO WIDTH SPACE, or ZWSP
https://en.wikipedia.org/wiki/Zero-width_space
Now, that's great, but how do you use this character? How do you type or copy a something that has a size of zero? Luckily, there's a Windows utility for this!
https://en.wikipedia.org/wiki/Zero-width_space
Now, that's great, but how do you use this character? How do you type or copy a something that has a size of zero? Luckily, there's a Windows utility for this!
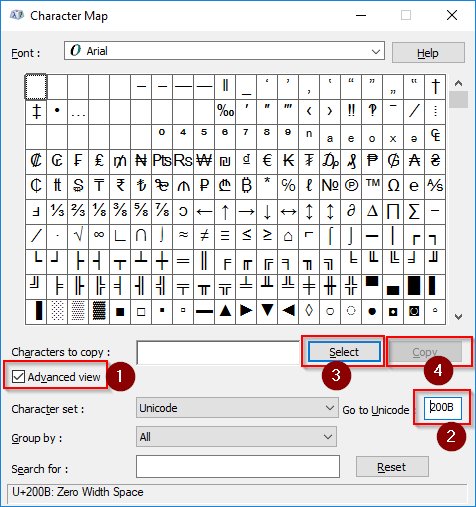
Go to Start, type "charmap" and hit Enter.
1.) Click Advanced
2.) The unicode CODEPOINT for this character is 200B, so type that in and hit ENTER
3.) It will find it in the grid above for you, then hit SELECT
4.) Hit COPY
5.) Go to Twitter, type "FAST" hit CTRLV then type ".COM"
1.) Click Advanced
2.) The unicode CODEPOINT for this character is 200B, so type that in and hit ENTER
3.) It will find it in the grid above for you, then hit SELECT
4.) Hit COPY
5.) Go to Twitter, type "FAST" hit CTRLV then type ".COM"
And that's how you use Unicode to subvert the system and make a tweet that says google.com
ư͍̗̤͔͎͕̝n͖͝i̤̱̠̭c̮͚̤̠o̺̖̼̣ͅd̵͉e͔͕̭̪̺ ͙͇̲͎̬̫̜m̧̳e̤̞̠̝̱a̜̦̬͍̩͡n͞s҉̭ ͙̜̟̱̤̙͎c̹h̬͈͝a̳̜̩̤̭̤̥͜o͎̙͇̟̙͙̺͡s̞
THIS is also why REPORTERS AND SOURCES should NOT COPY AND PASTE SOURCE MATERIAL. You should really type it.
There are many, many tricks like this you can use to "watermark" text that __LOOKS NORMAL TO HUMANS__ but will actually let internal threat investigators track the source
There are many, many tricks like this you can use to "watermark" text that __LOOKS NORMAL TO HUMANS__ but will actually let internal threat investigators track the source
Now, I don't know if there are any products on the market that can inject into Exchange and watermark company email distributions per individual, but I wouldn't put it past an incredibly secretive organization, it's not something I would assume against.
Like, Palantir, there are some smart people working there, world-class. I wouldn't fuck with that stuff.
This concludes Learning Unicode with Taylor Swift.
I probably shouldn’t be broadcasting Internal Threat detection tricks sonce I’m apparently on that team now too.
Respect to @axios retyping the complete document to prevent latent tracing based on printer or hidden typesetting marks. (See thread above) https://twitter.com/jonathanvswan/status/1092148604700119040
Curious how #COVIDー19 is trending if dashes break hashtags?
Because it’s not a dash. It’s a Japanese Unicode character.
U+30FC : KATAKANA-HIRAGANA PROLONGED SOUND MARK
https://www.babelstone.co.uk/Unicode/whatisit.html
Because it’s not a dash. It’s a Japanese Unicode character.
U+30FC : KATAKANA-HIRAGANA PROLONGED SOUND MARK
https://www.babelstone.co.uk/Unicode/whatisit.html

 Read on Twitter
Read on Twitter