IronBank ($CREAM) was exploited on $37.5M, let’s take a quick look at what happened.
1/ Attacker used Alpha Homora for borrowing sUSD from IronBank.
Each time they borrow twice as much as in the previous one.

1/ Attacker used Alpha Homora for borrowing sUSD from IronBank.
Each time they borrow twice as much as in the previous one.
2/ They do this through two transactions and each time they lend the funds back into IronBank, receiving cySUSD.
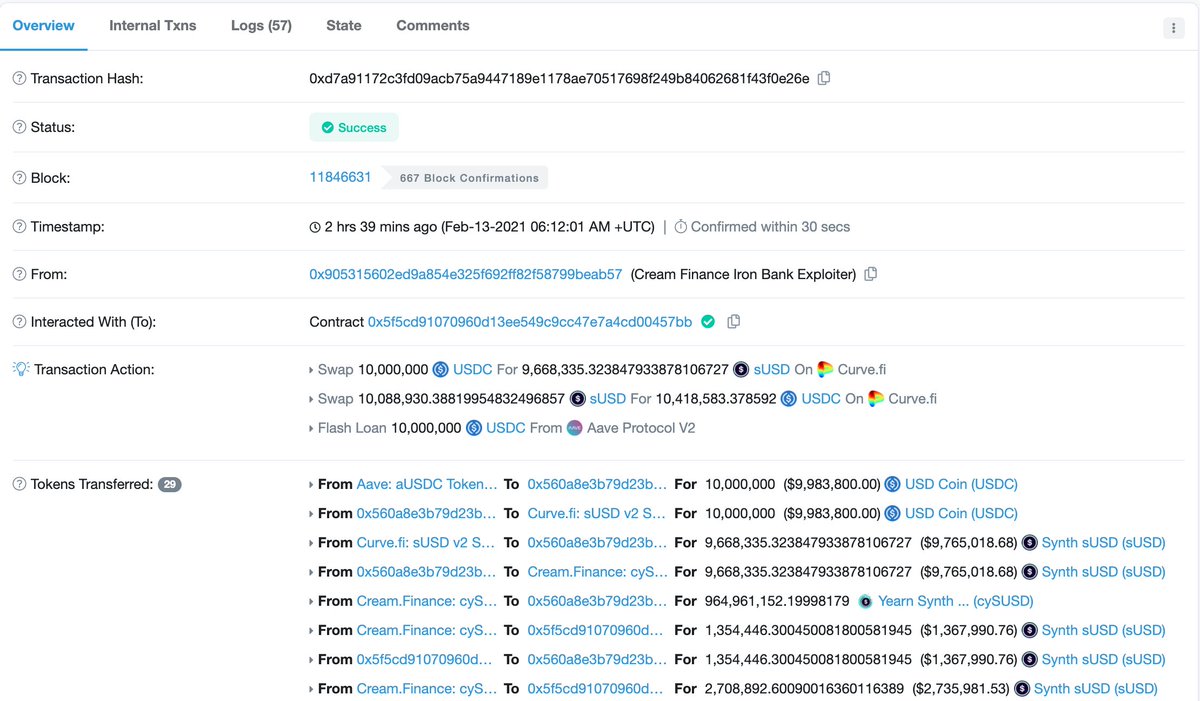
3/ At some point exploiter took $1.8M USDC flash loan from Aave v2 and swapped USDC to sUSD using Curve.
3/ At some point exploiter took $1.8M USDC flash loan from Aave v2 and swapped USDC to sUSD using Curve.
4/ They lend these sUSD to IronBank, which allows them to continue borrowing and lending them, receiving cySUSD.
5/ Of course, some sUSD are spent on repayment of the flash loan.
5/ Of course, some sUSD are spent on repayment of the flash loan.
6/ Also, a 10M USD flash loan is taken, which is also used to increase the number of cySUSD.
7/ In the end, the number of their cySUSD reaches an incredible amount, which allows them to borrow anything from IronBank.
7/ In the end, the number of their cySUSD reaches an incredible amount, which allows them to borrow anything from IronBank.
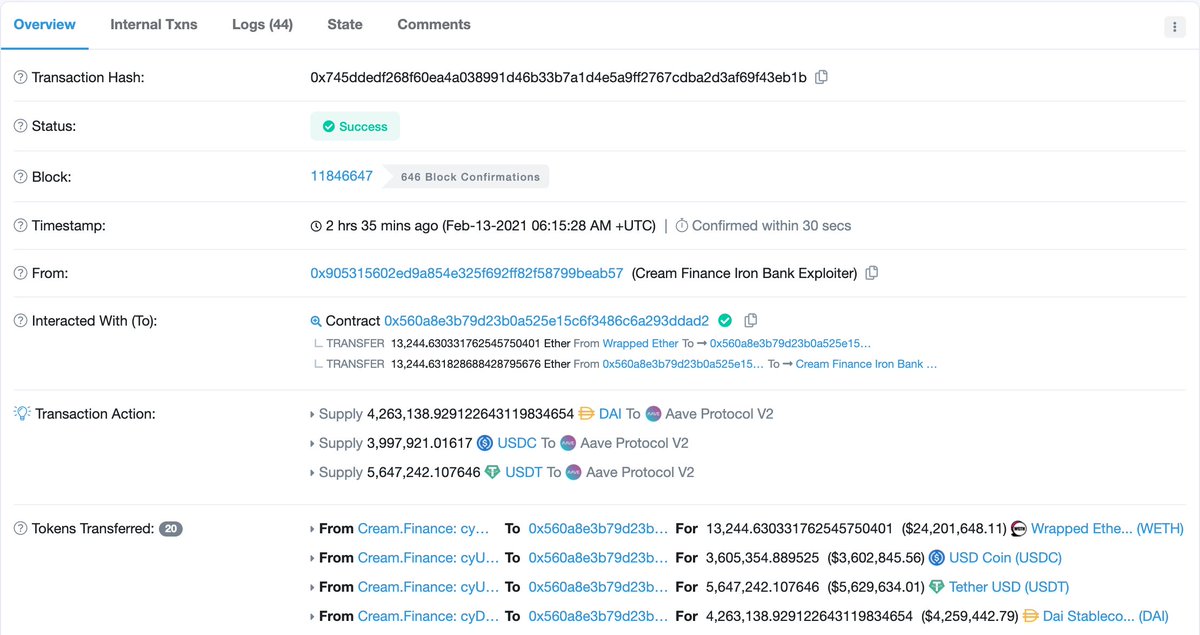
9/ Stablecoins have been deposited to Aave v2,
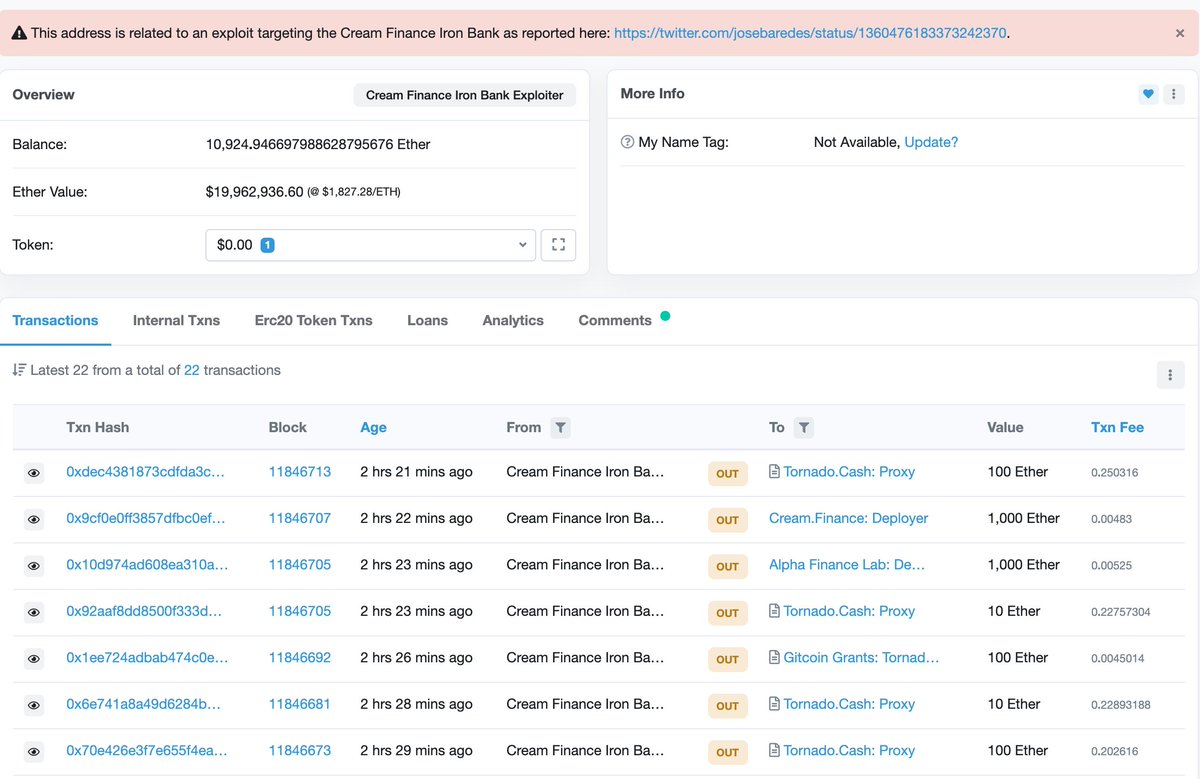
1k ETH to IronBank deployer,
1k ETH to Homora deployer,
220 ETH to Tornado,
100 ETH granted to Tornado
and almost 11k ETH remain on the exploiter balance.
https://etherscan.io/address/0x905315602ed9a854e325f692ff82f58799beab57
1k ETH to IronBank deployer,
1k ETH to Homora deployer,
220 ETH to Tornado,
100 ETH granted to Tornado
and almost 11k ETH remain on the exploiter balance.
https://etherscan.io/address/0x905315602ed9a854e325f692ff82f58799beab57

 Read on Twitter
Read on Twitter