New work out today from our Tech team & China research team: @joinClubhouse app recently became popular in
New work out today from our Tech team & China research team: @joinClubhouse app recently became popular in  . We looked at its data security practices & found a potential risk to mainland Chinese users.
. We looked at its data security practices & found a potential risk to mainland Chinese users. https://cyber.fsi.stanford.edu/io/news/clubhouse-china
https://cyber.fsi.stanford.edu/io/news/clubhouse-chinaHere are our key findings



(1/8)
(1) . @AgoraIO, a Shanghai-based startup, provides the backend platform to Clubhouse. This has been widely suspected.
(2/8)
(2/8)
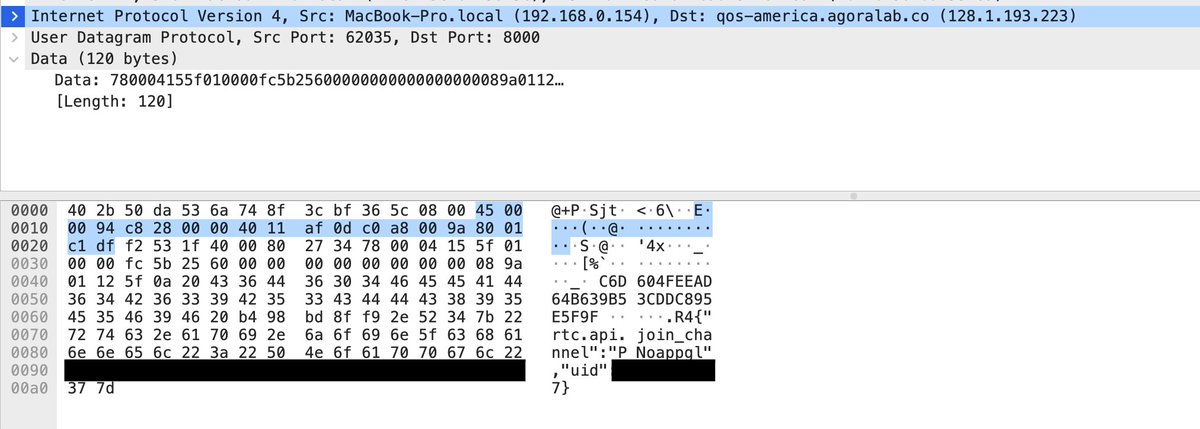
(2) . @joinClubhouse user IDs (not their username — more like a unique serial number) are transmitted in plaintext over the internet, making them trivial to intercept. Chatroom IDs (again, more like serial number) also transmitted in plaintext.
(3/8)
(3/8)
Any observer of internet traffic could easily match IDs on shared chatrooms to see who is talking to whom. For mainland Chinese users, this is troubling
(4/8)
(4/8)
(3) Users’ raw audio is likely but not certainly available to @agoraIO. AgoraIO says it does not store client audio, but PRC Cybersecurity Law could compel the firm to cooperate on handing over user data
@jeromeacohen @fryan
(5/8)
@jeromeacohen @fryan
(5/8)
(4) . @joinClubhouse terms state that it temporarily records user audio on its own servers. Unclear where servers are, or how long is “temporary.” If servers are in the US, Chinese govt is unlikely to receive legal access to them
@Riana_Crypto
(6/8)
@Riana_Crypto
(6/8)
(5) We also explore how the Chinese govt could crack down on mainland Chinese Clubhouse users, even in subtle ways. We also discuss why China banned the app now
@jenjpan @mollyeroberts
(7/8)
@jenjpan @mollyeroberts
(7/8)
Thank you to our team @elegant_wallaby @jackhcable @noUpside @alexstamos @debutts & @Riana_Crypto for their analysis on this post.
(8/8)
(8/8)

 Read on Twitter
Read on Twitter