Have you ever thought to yourself "boy, I sure wish I had to use passwords more often"? No, of course not. Passwords suck. Good passwords are long and hard to remember and easy to remember passwords aren't good. They're inherently portable and easy to steal.
We've known this a great many years and platforms like Active Directory and Windows have supported better options like smart cards for 20 years because of this. So what is it about passwords that make them so hard to protect?
First of all, we need them to be random. Random means people can't guess them. Suppose I pick a simple 5 letter password from the lowercase alphabet. That's 26 letters and 5 positions, or 26^5, or ~11.8 million combinations.
As a human it'll take you forever to guess it, but it'll take a computer less than a second to generate all 11.8 million combinations. But I'm also human so I'm going to pick something easy for me to remember: "riley". That's super easy to guess if you've looked me up.
So we start to enforce strength requirements: must be 8 characters with uppercase, lowercase, numbers, symbols, one reoccurring character from season 6 of your favorite TV show. This gives you (say) 92 characters and 8 positions or 92^8 or 5132 trillion combinations.
So my password is now aSdX3$CC;^k@. I can barely remember what I had for lunch yesterday, am I expected to remember this? Oh, and I have to change it every 90 days? Ugggggh.
But it turns out this is equally easy for a computer to guess anyway, so.  https://twitter.com/TerahashCorp/status/1155112559206383616?s=20
https://twitter.com/TerahashCorp/status/1155112559206383616?s=20
 https://twitter.com/TerahashCorp/status/1155112559206383616?s=20
https://twitter.com/TerahashCorp/status/1155112559206383616?s=20
Of course, suppose you don't have $30k to drop on a password cracking rig and you don't have benefactors that will donate to the cause, brute-forcing your way through is out of the question. So you attack the next best thing: Windows.
To attack Windows you have to understand how authentication works in Windows. In simple terms you have a high value credential (password) which you exchange for a medium value credential (TGT/PRT), that is exchanged for low value credentials (service tickets/access tokens).
You can think of them as first order, which derives a second order, which then derives a third order credential, all with decreasing capabilities as you go further out. This is sort of the mantra for solutions like Credential Guard: protect the first and second order credentials.
That's all well and good however technologies like Credential Guard serve very specific and well defined purposes and aren't holistic catch-all solutions.
This is important: there's never a one-size-fits-all solution to security.
This is important: there's never a one-size-fits-all solution to security.
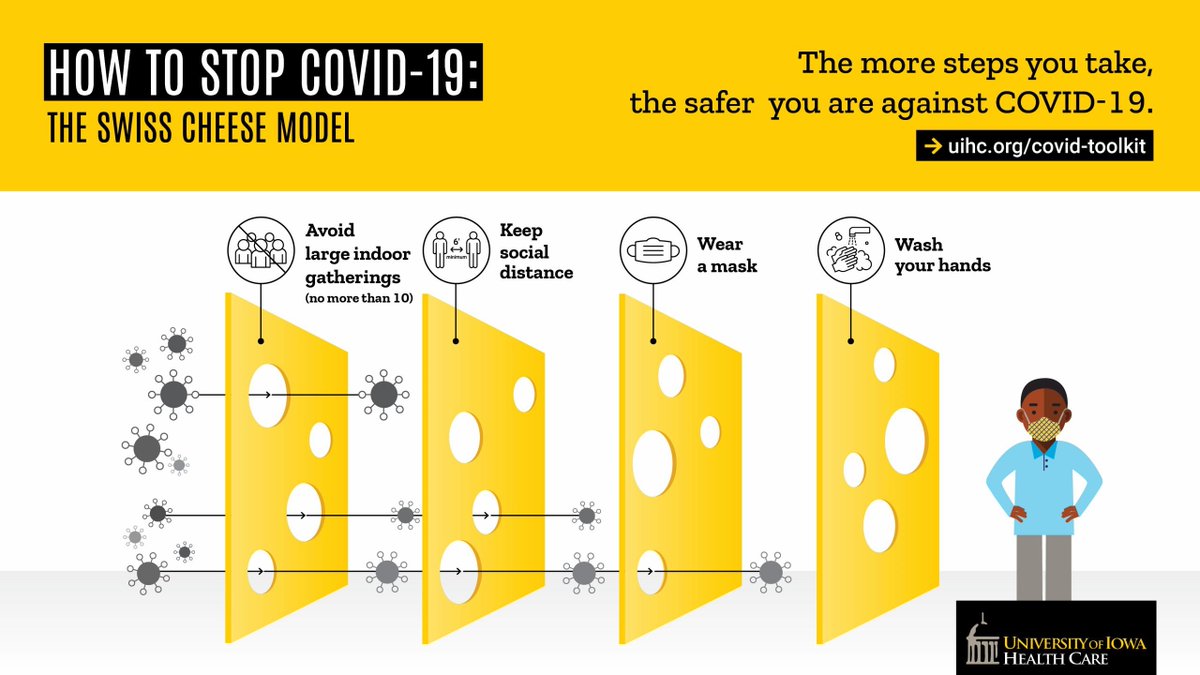
Securing complex systems like Windows, or your enterprise network, requires many layers. It's like the swiss cheese analogy for stopping the spread of COVID-19. Layer one stops something very specific. Layer two stops another thing, layer three... etc.
So Credential Guard protects your 1st and second order credentials at rest *once* they've entered the system. To understand why this matters it's important to go back to how credentials are processed by Windows.
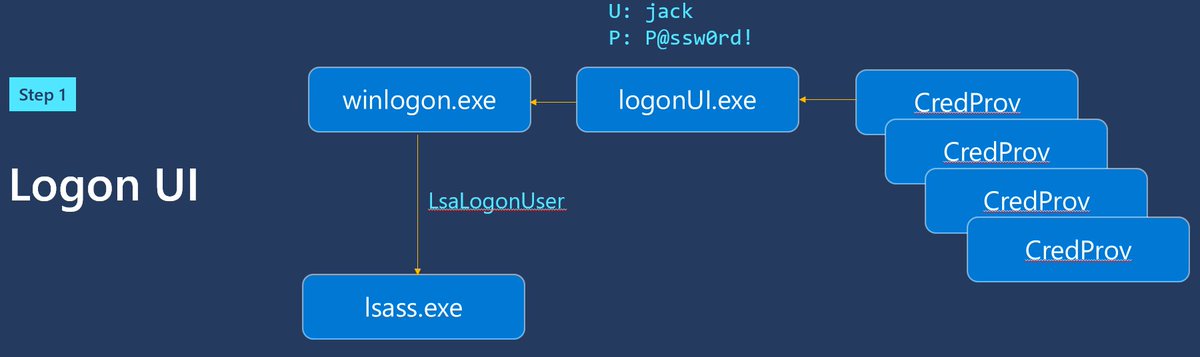
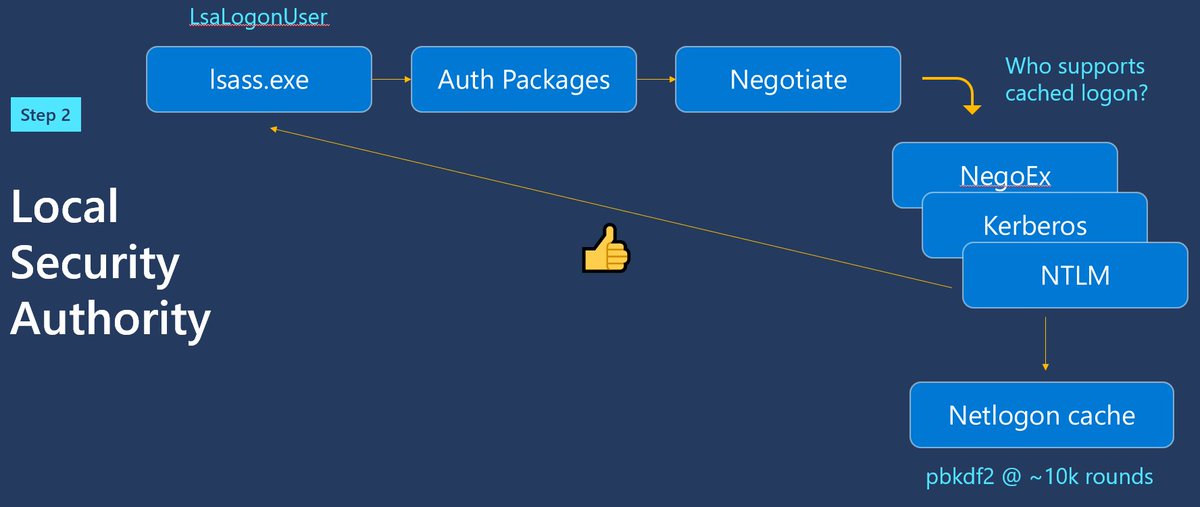
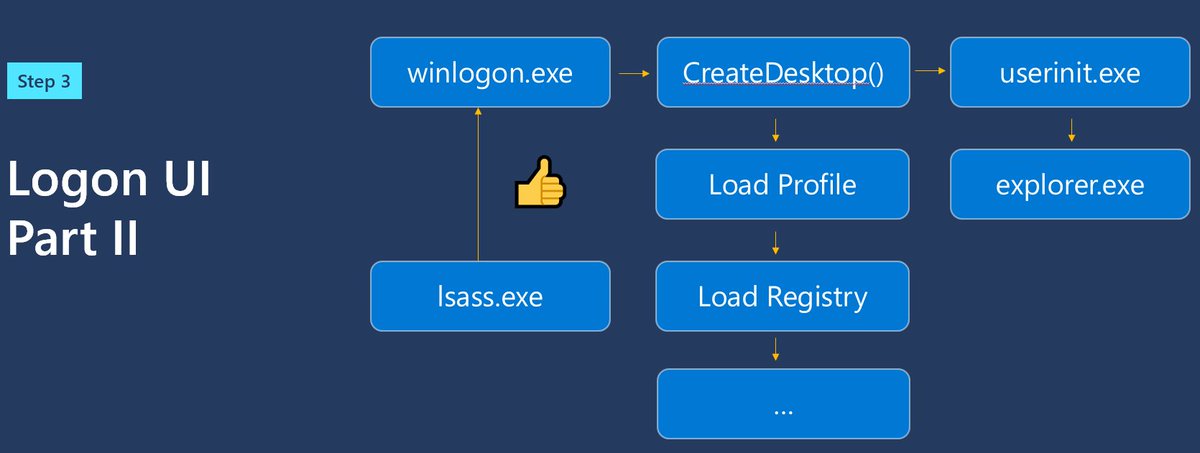
Passwords enter your computer through credential providers, into LSA, and processed by AD or AAD. I've explained this in great detail in both text and video form. https://syfuhs.net/what-happens-when-you-type-your-password-into-windows
But this is all very hand-wavy. Along the way there are built-in extensibility points where third parties can add in their own code to make the login work however they need it to, because sometimes that's just how things be.
You can drop in your own credential provider that looks just like the password credprov. You can install a custom LSA authentication package that listens for passwords. Or you can install a subauth module and log the password.
But we have solutions for that. LSA Protected Process mode is one. It prevents anyone from loading third party code into LSA so they can't touch those extensibility points. But you can bypass LSAPPL -- so we have HVCI to enforce it. Lots of solutions here.
But there's more to this. Your password doesn't magically go from your keyboard to the credprov. It gets converted to electrical signals and sent along a wire into your computer to be processed by the CPU in a driver in the kernel and then converted back to text.
So now you have to worry about hardware keyloggers snooping the wire. Or kernel-mode keyloggers listening to the drivers. The latter is easier to handle: limit what kinds of drivers can be installed through something like Windows Defender Application Control. The former though?
Not a lot you can do to protect from hardware keyloggers. To truly protect this whole stack you need dedicated hardware that guarantees nothing is listening to the electrical signals. That's hard even with specialized hardware. It's impossible for general purpose systems.
All of this adds up to a particularly complicated mess that is hard to fit into your head and harder to defend. Surely there are better options here?
This is why we've been pushing passwordless. Sure, it's partly a marketing thing, but it's also a line in the sand. Passwords just genuinely suck. We can do better and we want to do better.
So we have smart cards. These were our first go at passwordless 20 years ago. They are more secure than passwords for a few good reasons...
First, they rely on asymmetric crypto (passwords = symmetric), which means you split the key into two separate pieces: a secret (private) key and a public key. You can share the public key with anyone, but you keep the private key to yourself.
To authenticate the user you ask them to perform an operation that only the holder of the private key can perform, which is then verified against the public portion.
This turns out to be an incredibly useful property. With smart cards you can store the private key in a tiny integrated circuit embedded into a piece of plastic. When you need to authenticate you plug it in to a reader which lets the computer ask the IC to perform operations.
This makes the key portable and also prevents you from copying the key off the IC, since the IC is hardened to protect against that sort of thing (in theory).
There's an obvious problem here: anyone can steal the card and use it. So we introduce PINs that unlock the card. You type a PIN into your computer, which is sent to the card and if it's correct that tells the card that it's safe to perform the requested operation.
So smart cards for everyone!! Except, they didn't really take off. Why? Well, a few reasons.
They require dedicated readers.
They're expensive to manufacture.
They're easy to lose.
They're easy to break.
The standards bodies were...insane.
They require dedicated readers.
They're expensive to manufacture.
They're easy to lose.
They're easy to break.
The standards bodies were...insane.
Over time these issues were overcome. We got better form factors, the manufacturing costs went down, the standards bodies mostly came to their senses.
Alas, the standards still kind of aren't great and making changes to them is hard to do.
But there's also another more insidious problem with them in that we're back to typing secrets (your PIN) into a keyboard that translates into electrical signals across a wire into the kernel and
Always evolving we built Windows Hello. The simplest way to describe Windows Hello is you take a smart card and embed it into your computer. We store you private key on your hard drive, encrypted to a key derived from your TPM and something else.
When you want to use this private key to perform an operation, say to log in, you take that "something else", combine it with the TPM and out comes your private key. That "something else" could be a PIN you type in, or a biometric template from your face or fingerprint.
This solves so many fundamental problems with smart cards.
Nothing to physically lose.
Nothing to break.
Doesn't require a dedicated reader (ish).
Manufacturing costs are low(er).
Infinitely easier to use.
Nothing to physically lose.
Nothing to break.
Doesn't require a dedicated reader (ish).
Manufacturing costs are low(er).
Infinitely easier to use.
But there are tradeoffs. The credential isn't portable anymore. This is a positive and a negative. On the one hand you can't steal the private key and use it elsewhere. On the other hand you have to register yourself on every machine you use.
The cryptographic operations occur in the OS. Therefore you can snoop on the "something else" path and collect the PIN or parts of the biometric template. In a theoretical sense that's potentially very bad. Way way way waaaaay harder to attack than passwords, but still.
This was solved through some serious collaboration between hardware vendors and Windows folks and culminated in something called Windows Hello Enhanced Sign-in Security. https://docs.microsoft.com/en-us/windows-hardware/design/device-experiences/windows-hello-enhanced-sign-in-security
The gist of this is relatively simple: move all the important security (crypto) operations that occur in the normal world OS into VSM. Easy, right? Well no. This was a hard problem to solve. 

But now it's incredibly difficult to snoop any data between the hardware sensors through the kernel to VSM and back into LSA. There are no extensibility points that let you touch the raw creds. Now that first order high value cred is seriously protected.
Combine it with Credential Guard and now all you're left with is low value credentials. Not bad.
But we're back to the problem of portability. You need to register the credentials on each machine you use. To register credentials you need another high value credential AND you need MFA.
Did I mention that smart cards and Windows Hello are MFA? They are. They're something you have (card or PC) and something you know or are (PIN or face/fingerprint). You're not going to get a super-high value credential out of just a password, so you need to go the extra step.
Some folks don't like to recognize Windows Hello as MFA. They're wrong, it is MFA. However, it may not fit their requirements *for* MFA creds because you require separation of the credentials from the machine. Sure, that's fine.
So portability is critical here. Which is why we have this thing called FIDO. It's an industry consortium and set of standards that allow different parties to agree on the form of credentials used as well as their relative security worthiness or credibility.
The net product is this security key, which is kinda sorta like a smart card in that is stores a private key, and you have to unlock it before you can ask it to perform operations against that key.
What makes it special and better than smart cards is the implementation. The protocol is simpler, the metadata is structured for specific scenarios (SCs are generic and require things called middleware to interpret functions), and you can store many identities on a single key.
But most importantly the ability to unlock the key has multiple predefined mechanisms. You can use a PIN typed into your computer, or you can use a key-specific mechanism like using a fingerprint reader built into the key. Getting that to work with smart cards is...non-standard.
Actually, another important thing is that these keys are rated for security levels and those levels are imprinted on the authentication. With a smart card all the party knows is a certificate was used. With FIDO you know a hardware key certified to a certain level was used.
AND ANOTHER THING... smart cards expose certificates, which can be used for any number things (a good thing for sure), whereas FIDO exposes specific authentication protocols. When I log into a website with a smart card I'm using TLS client cert auth. FIDO is higher in the stack.
Plugging into the TLS transport stack is expensive and complicated and potentially leads to uuuuugly vulnerabilities. Moving the authentication to the application layer is architecturally more sound. It's safer and easier to implement.
Dangit, and another thing! FIDO isn't just about external keys. It's about abstracting away authentication methods. With FIDO and webauthn you can log into a website with your security key or with Windows Hello. Windows Hello IS a FIDO and webauthn key.
I guess I went off on a tangent there. Anyway...
So you see why passwords are pretty lousy, and why we don't think they should be the predominant method of authenticating people. /fin
So you see why passwords are pretty lousy, and why we don't think they should be the predominant method of authenticating people. /fin

 Read on Twitter
Read on Twitter