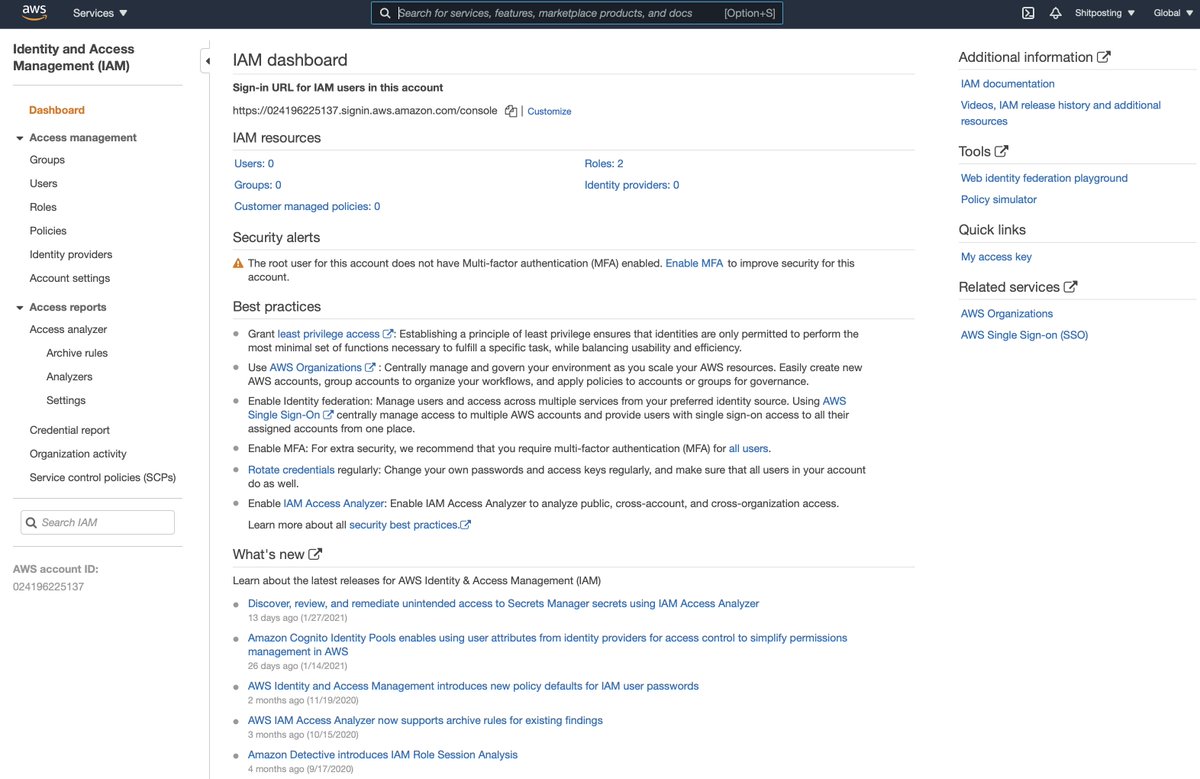
Been a while since I put on my New User Hat. What cloud service should I work with today?
I'll pick.... @awscloud. Welcome to the hot seat!
I'll pick.... @awscloud. Welcome to the hot seat!
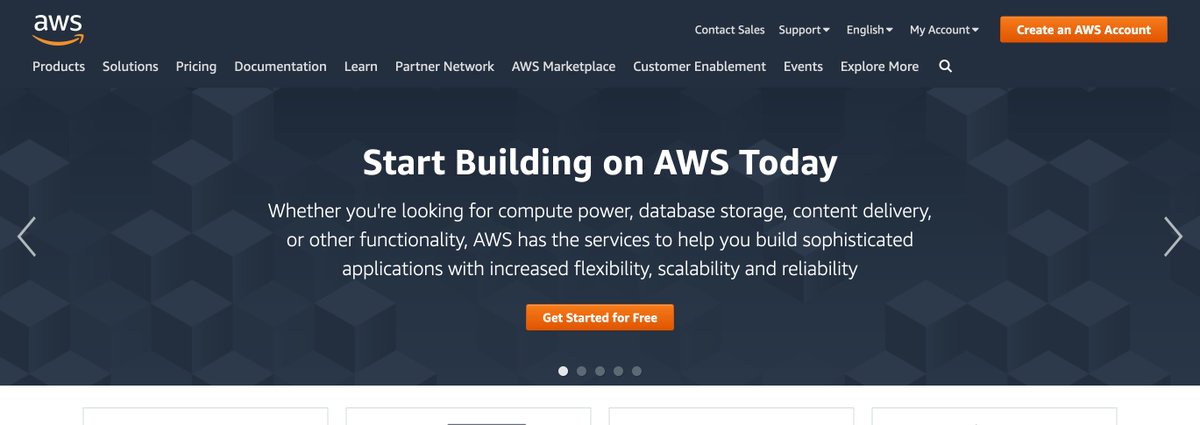
Small typo there: there should really be a GIANT FREAKING ASTERISK next to "free." "Get started" drops me to the sign-in page which is also a bit disconcerting. "Create new account" is hanging out at the bottom.
The copy here could use some love. I'd be willing to bet the majority of first-time users aren't really clear on EC2, S3 they recognize from scary headlines, and "what the hell is a DynamoDB" is the DynamoDB team's motto.
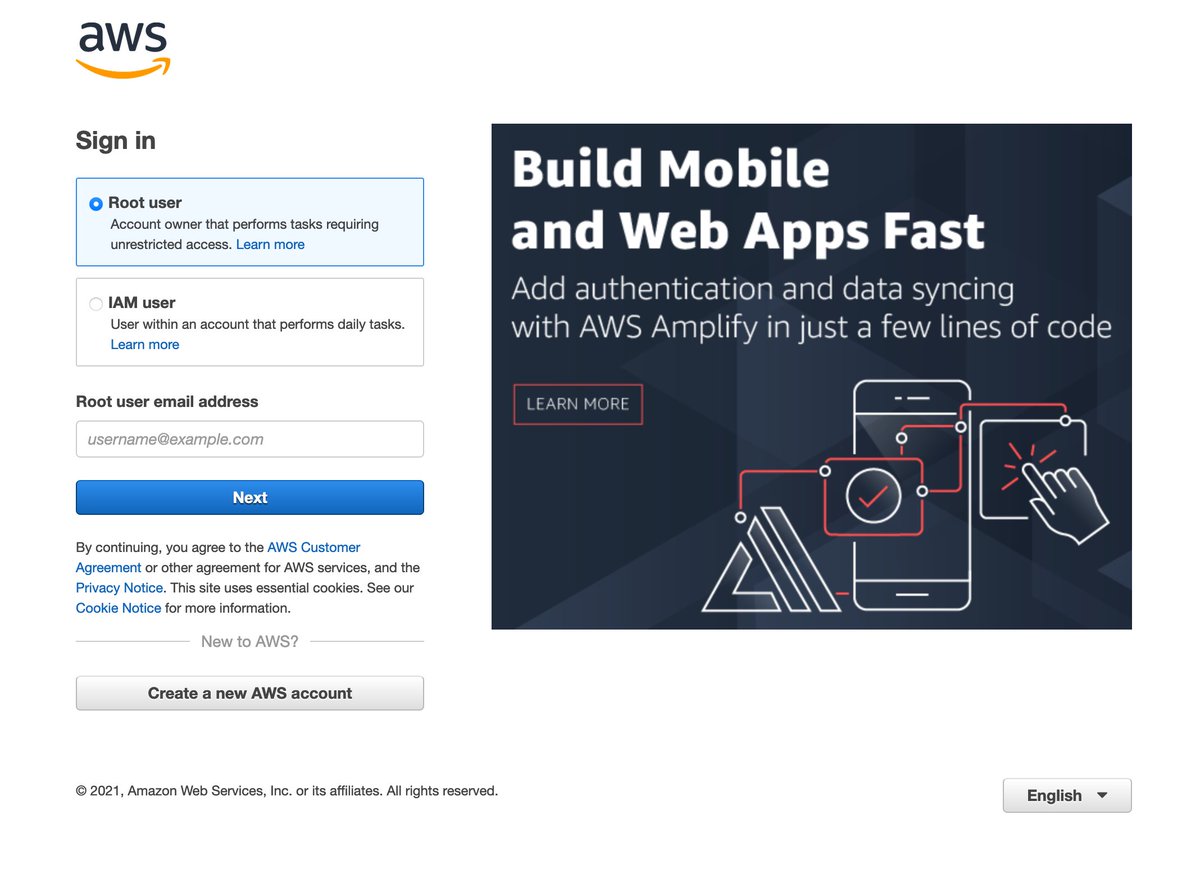
I have 1Password generate a password and autofill it. Suddenly the "your password isn't strong enough" stuff fires until I put in a legit email.
Who would have guessed that AWS would struggle with web interfaces?
Who would have guessed that AWS would struggle with web interfaces?
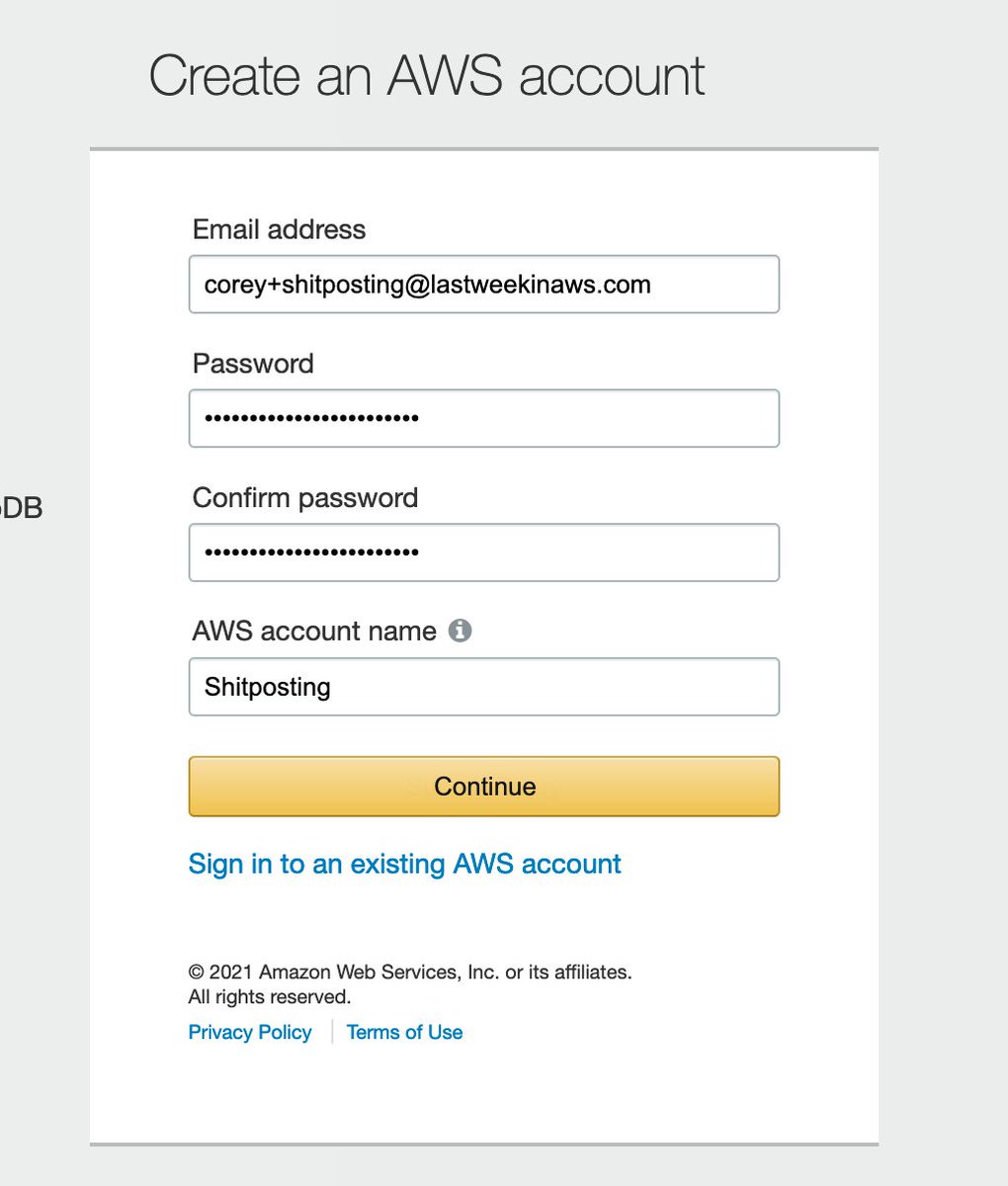
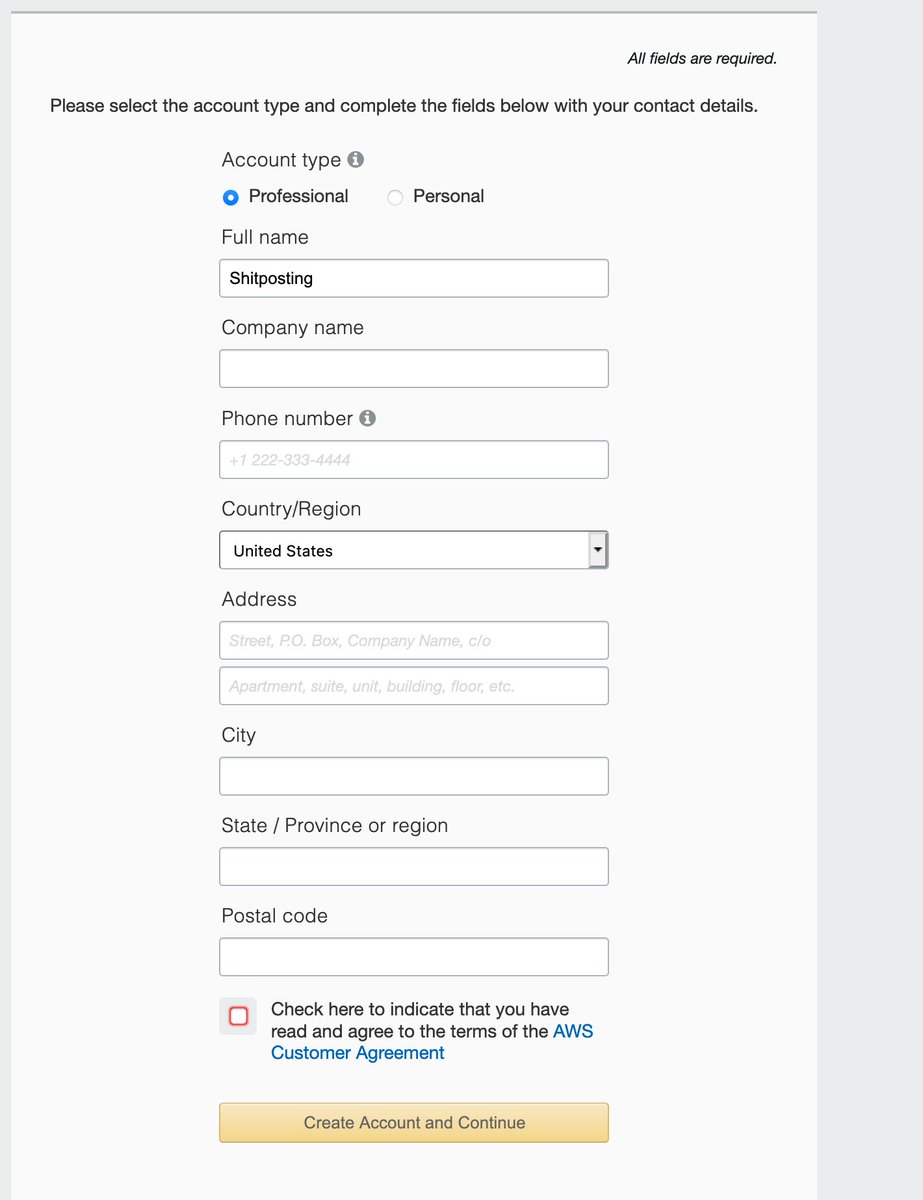
I... wait? Why would the Account Name field also be considered my name? "Shitposting" was my father, @awscloud.
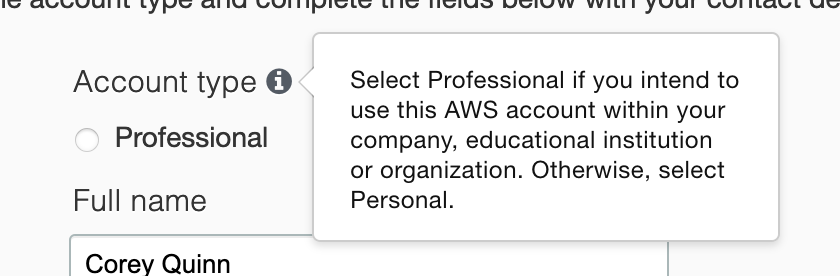
"Professional" vs "personal" is hard. I intend to use this AWS account within *their* organization.
I've never had a personal account so let's try that.
I've never had a personal account so let's try that.
That red box is tricksy. Big Companies will generally get an Enterprise Agreement in place that supersedes this. It offers a host of awesome terms for companies that they care about.
There is never a moment in which you're able to spin up a resource and @awscloud is unable to bill SOMEONE for it. This is by design.
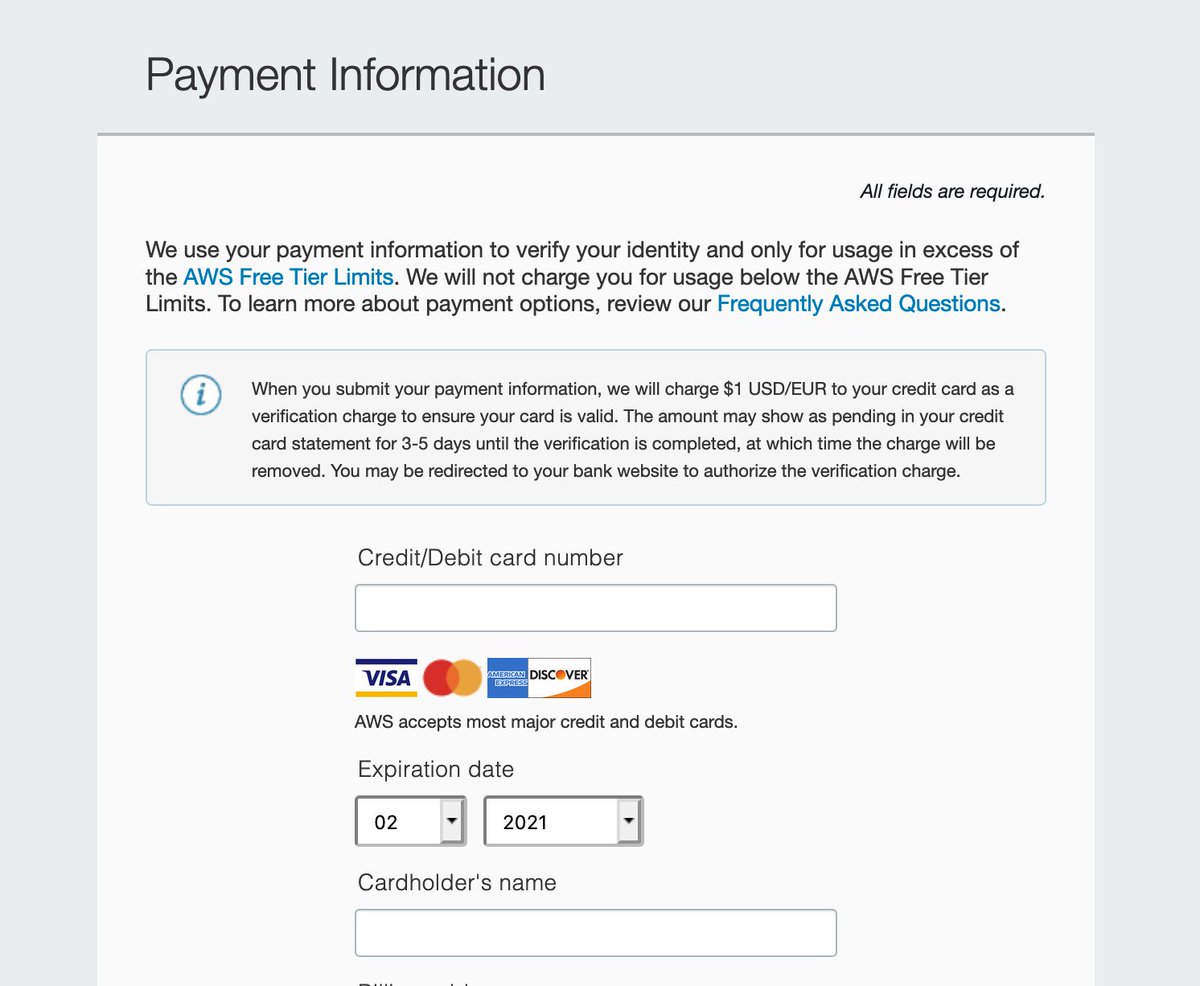
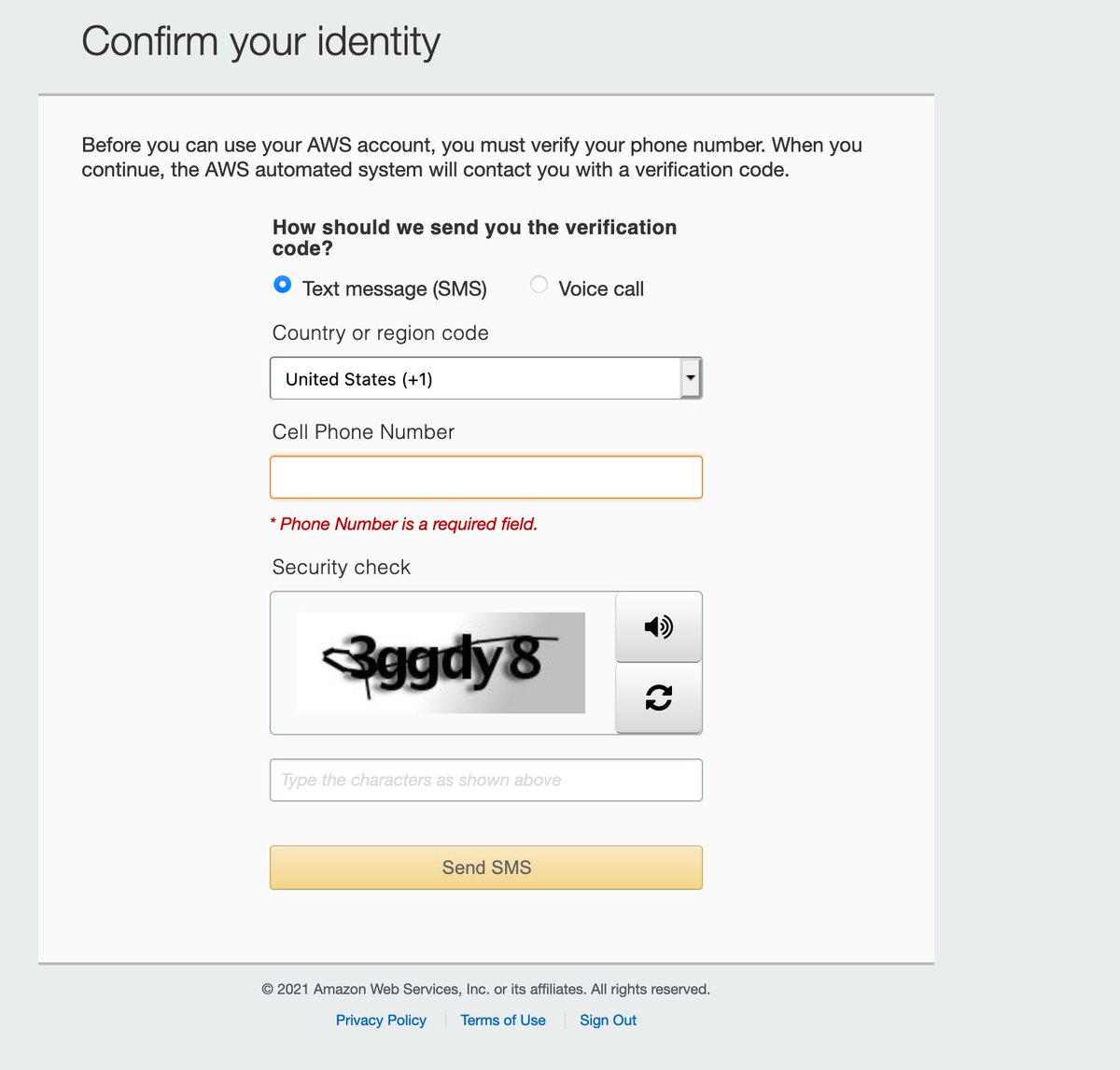
Now they want a cell phone number and me to help train Rekognition / prove I'm not going to be "an accessibility problem."
I dunno, the console hasn't turned blood red and begun shrieking so it may not have been as verified as you think, AWS.
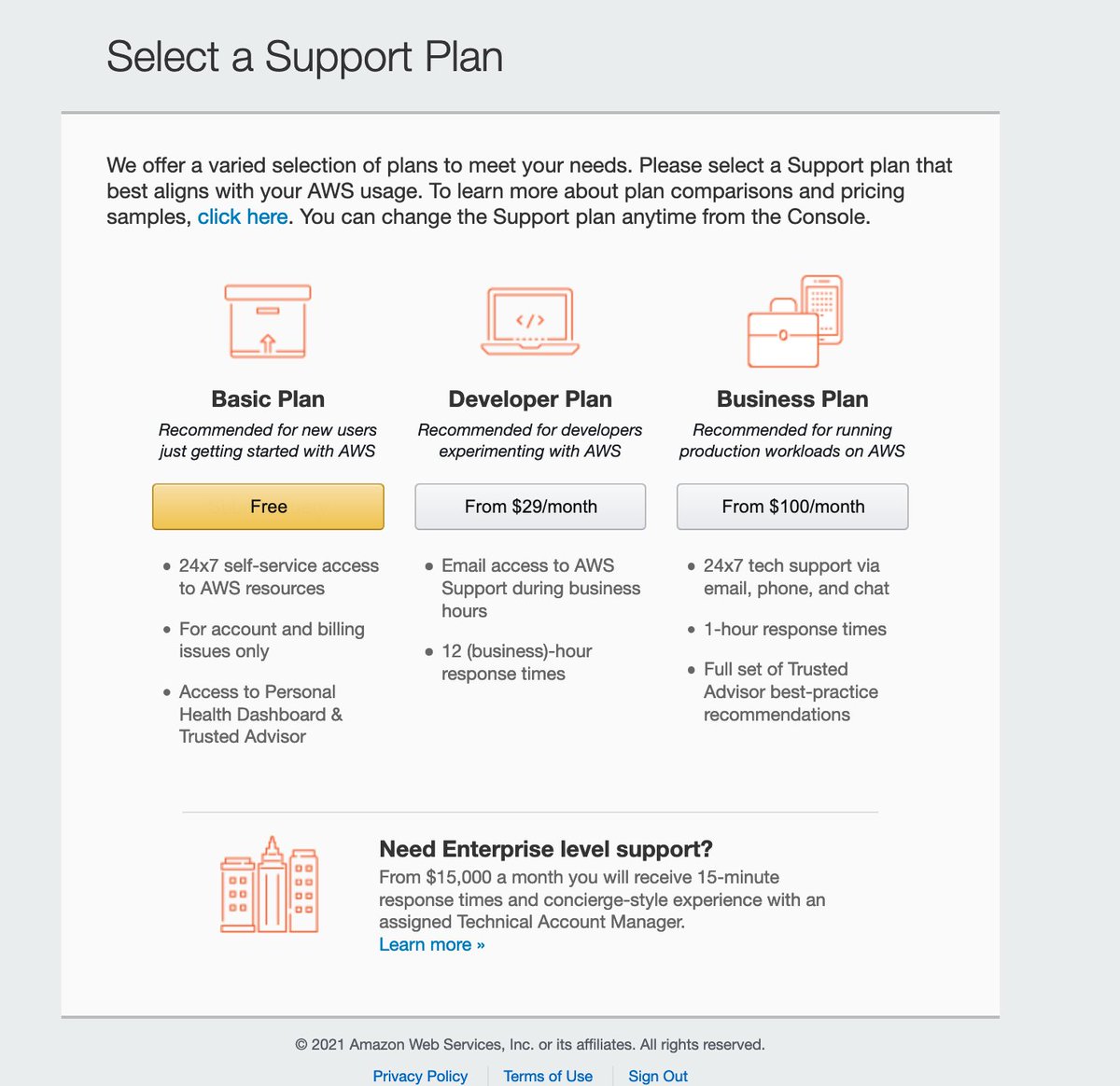
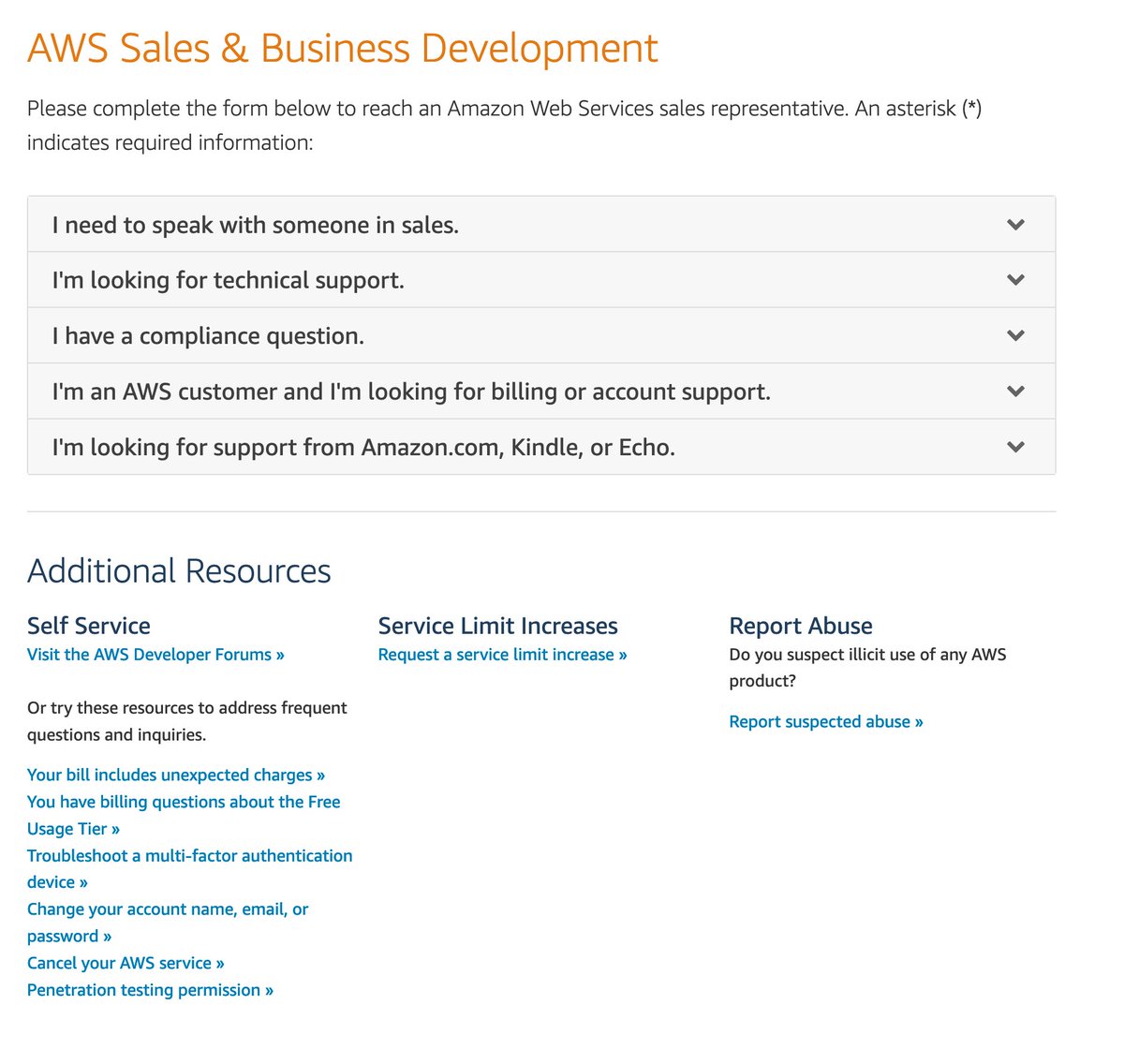
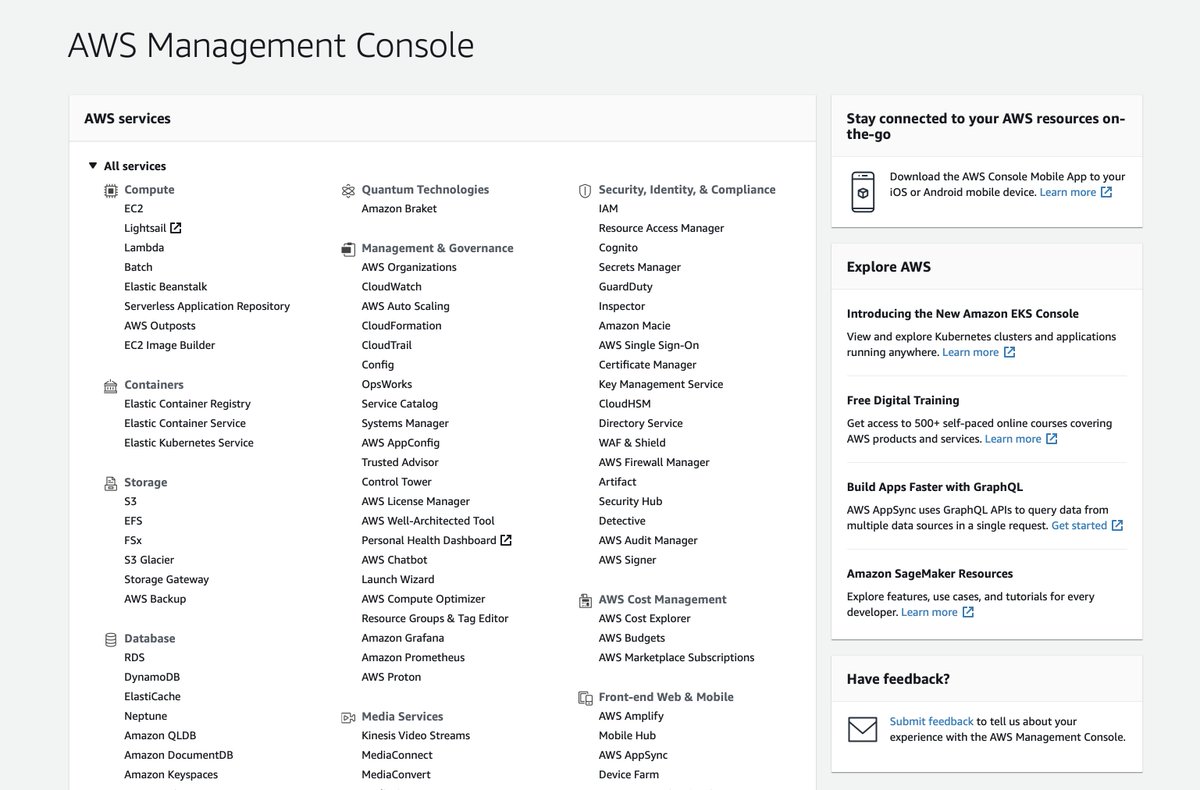
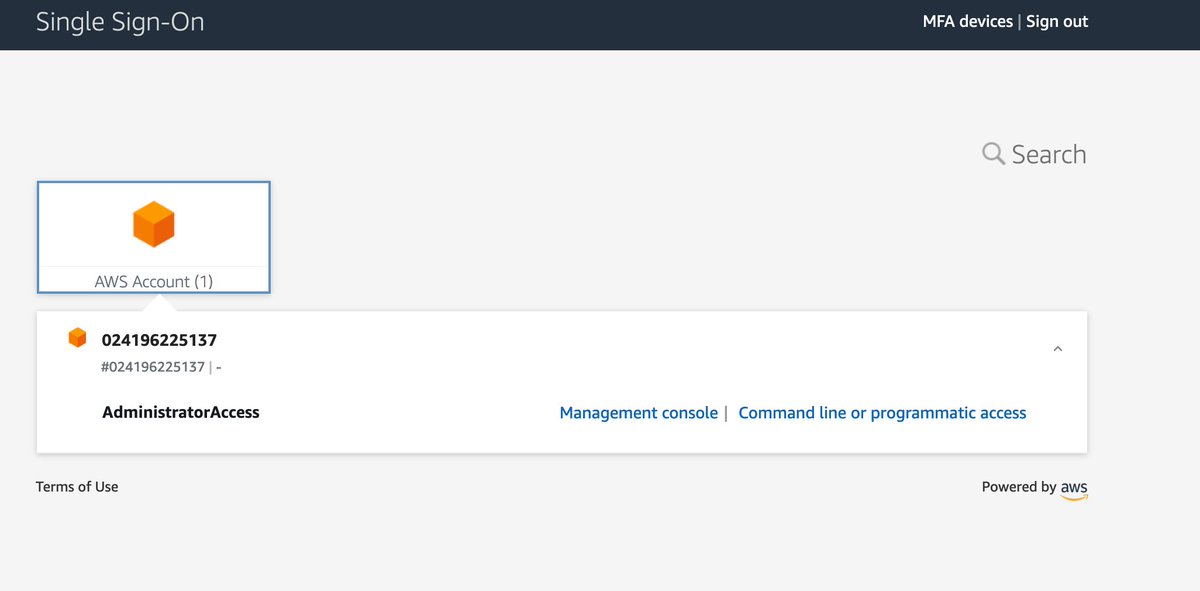
So many things from which to choose. The list of frequent questions in the lower left could be titled "The Ways In Which We Are Disappointing Our Customers."
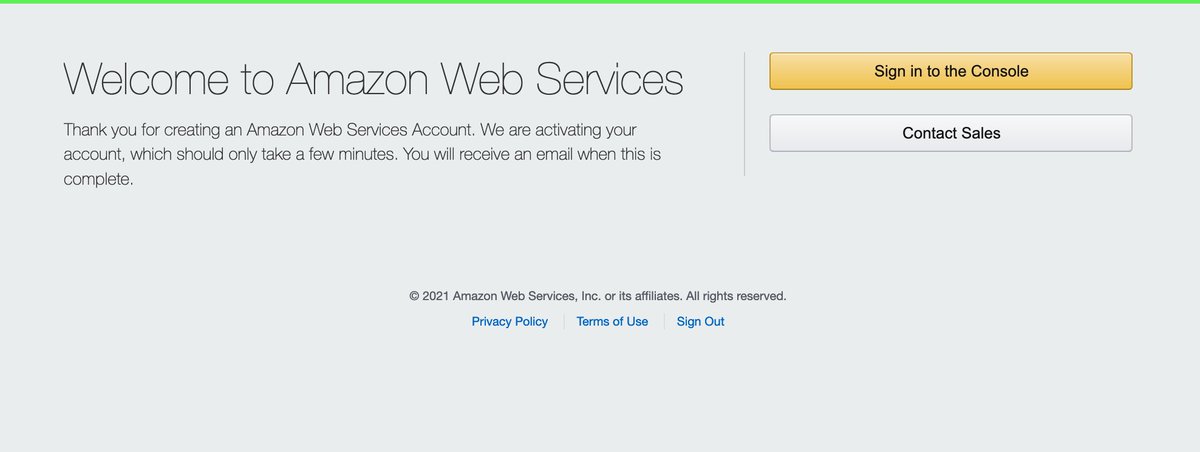
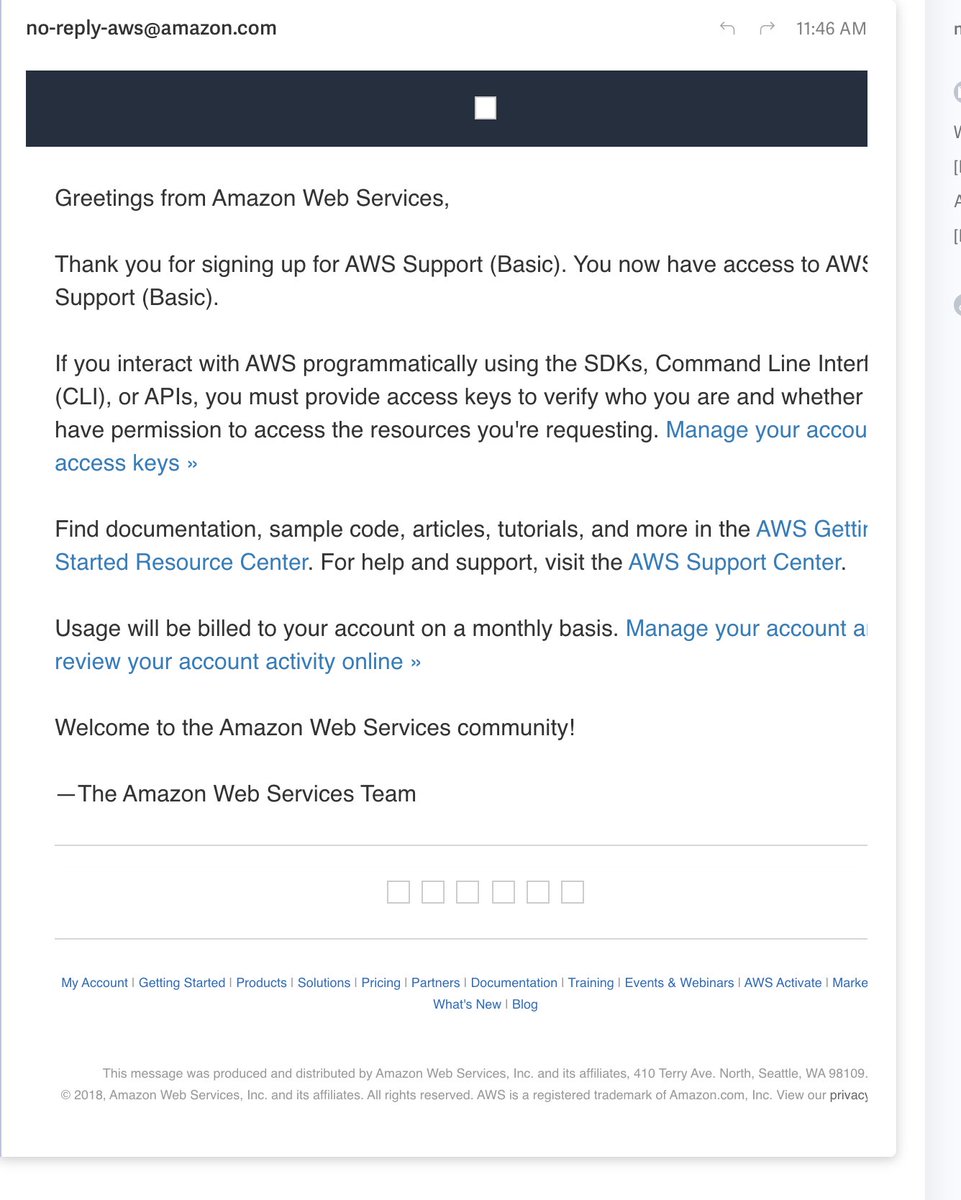
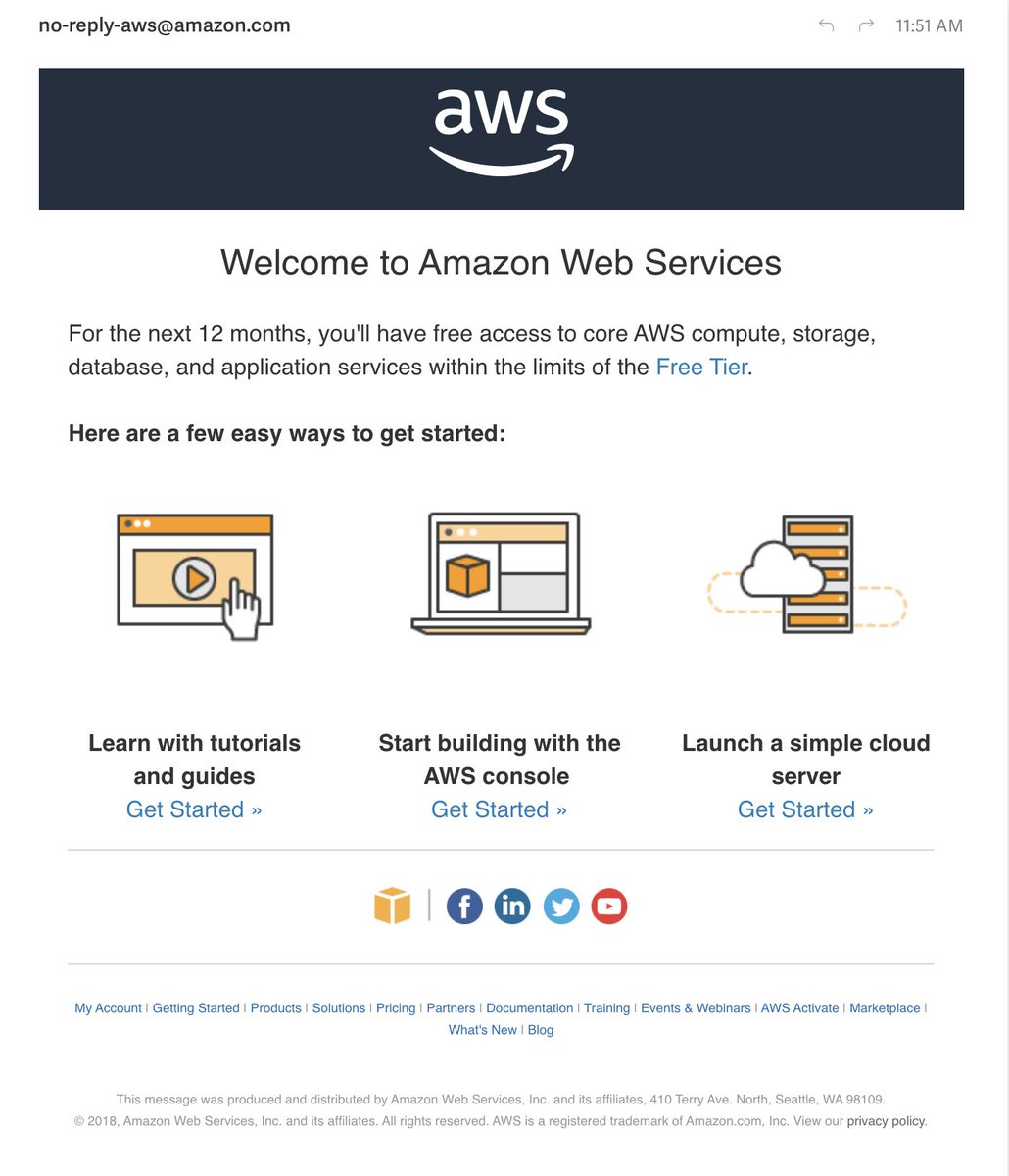
I have two emails. The first welcomes me to the Twitter Support tier which they've typo'd as "Basic."
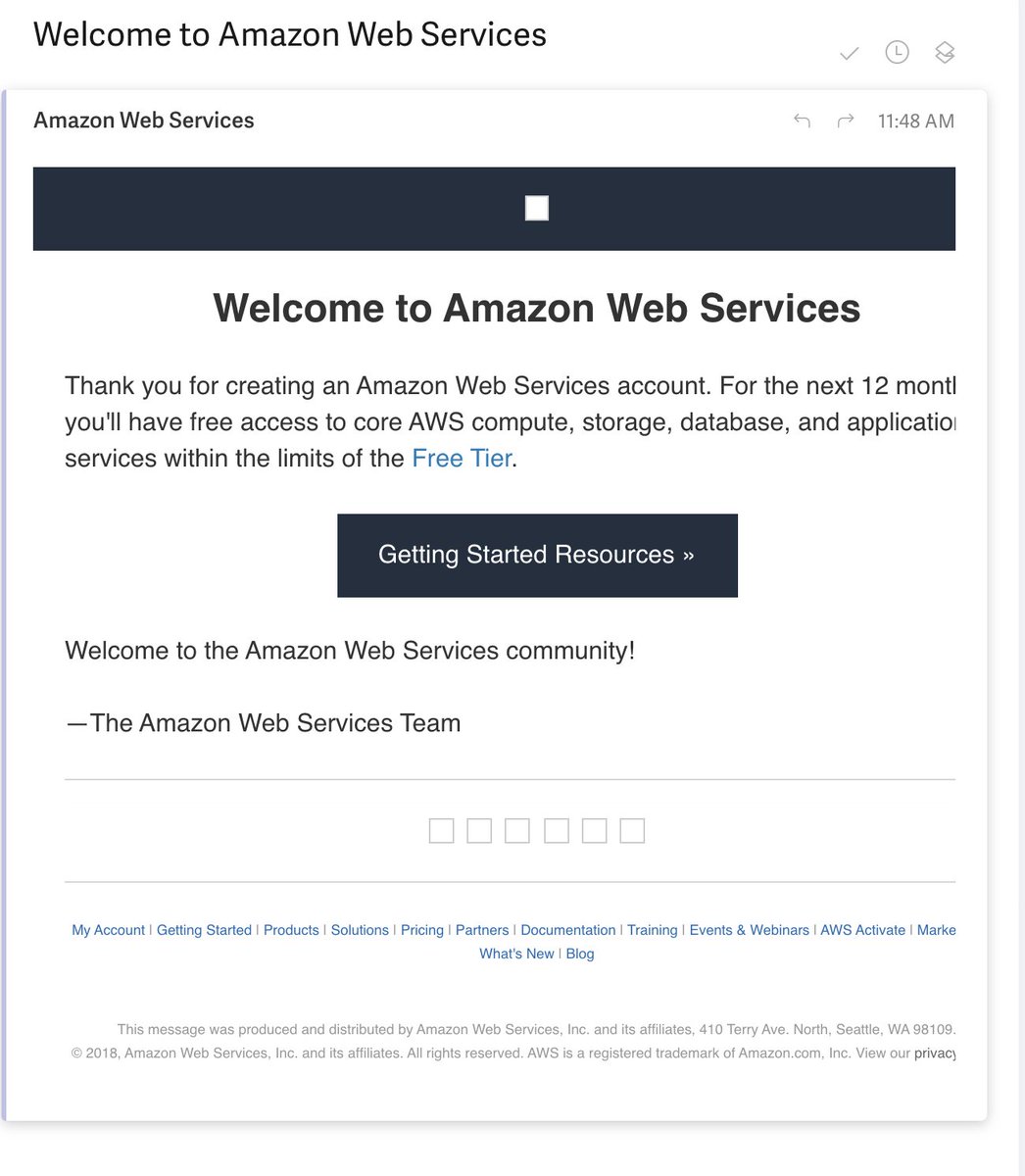
The second screws up the CSS and tells untruths about the free tier (many are permanently free). I can see how this trips people up.
The second screws up the CSS and tells untruths about the free tier (many are permanently free). I can see how this trips people up.
It defaults me to using us-east-2, and confronts me with an immediate popup on my initial login telling me what's new.
The competition here must be fierce; the top three suggestions are all viable paths to "build a website."
The competition here must be fierce; the top three suggestions are all viable paths to "build a website."
What should I see instead?
* A polite "Hey jackass, set up an IAM user and don't use root."
* "Here's how to set up a billing alarm."
* "Let us get to know you so we're not doing S3 Basics marketing to some company's chief cloud architect."
* A polite "Hey jackass, set up an IAM user and don't use root."
* "Here's how to set up a billing alarm."
* "Let us get to know you so we're not doing S3 Basics marketing to some company's chief cloud architect."
This is prominently featured and is a horrible mistake--both in its execution, as well as the fact that it exists instead of a responsive design.
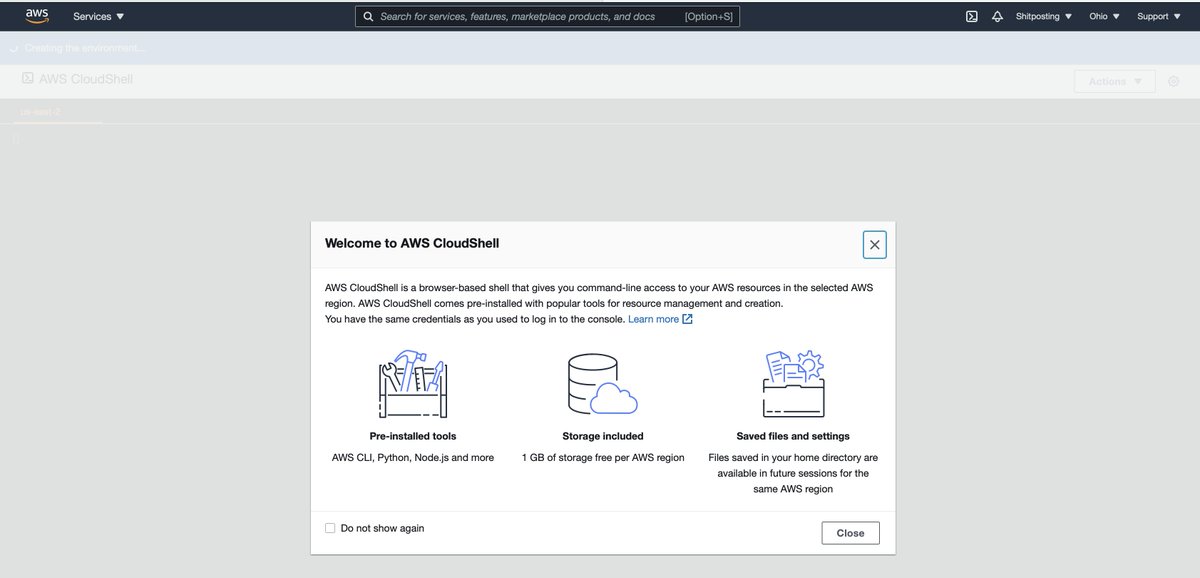
I click the Cloud Shell icon and get this page instead of the correct behavior, which again is a screaming "OH MY GOD NO, YOU'RE LOGGED IN AS ROOT. HOLY HELL, STOP STOP STOP."
At this point I pause for a scheduled strategy meeting with my executive team in which I pretend to be a responsible grown-up instead of three shitposters in a trenchcoat. I will return afterwards and pick this back up.
My executive team goes back to burying their heads in their hands over my shenanigans, and I go back to check my email. This came in. They sure are pushing the @awscloud free tier hard for something that's bound to break your heart harder than your first love.
What's also missing is any hint of "heyyyyy, so real quick before you start standing things up that might be load bearing, let's have a quick chat about Control Tower / Organizations / account structure / SSO." That's a hidden one-way door.
I head over to IAM because I'm not a dangerous loon. Where I'd expect to see a "HOLY CRAP STOP USING ROOT" I instead see so much text I can only surmise that they're @jim_scharf's meeting notes or something.
The only splash of color is a "turn on MFA" without a sidenote warning that if this email address is also tied to an http://Amazon.com account this will at some point ruin your entire morning.
Pretty sure Safari does support U2F but I'm no expert. (I normally use Firefox but I wanted an untainted browser history).
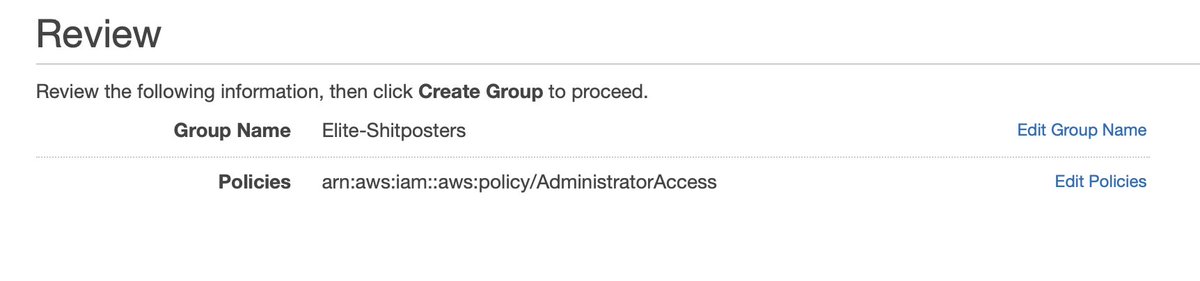
"I'm going to add myself an IAM user" is the wrong direction here. There's nothing that tells you this explicitly, but you want to build a GROUP, then add users to that group to have permissions. Source: didn't do this previously, lived to regret it.
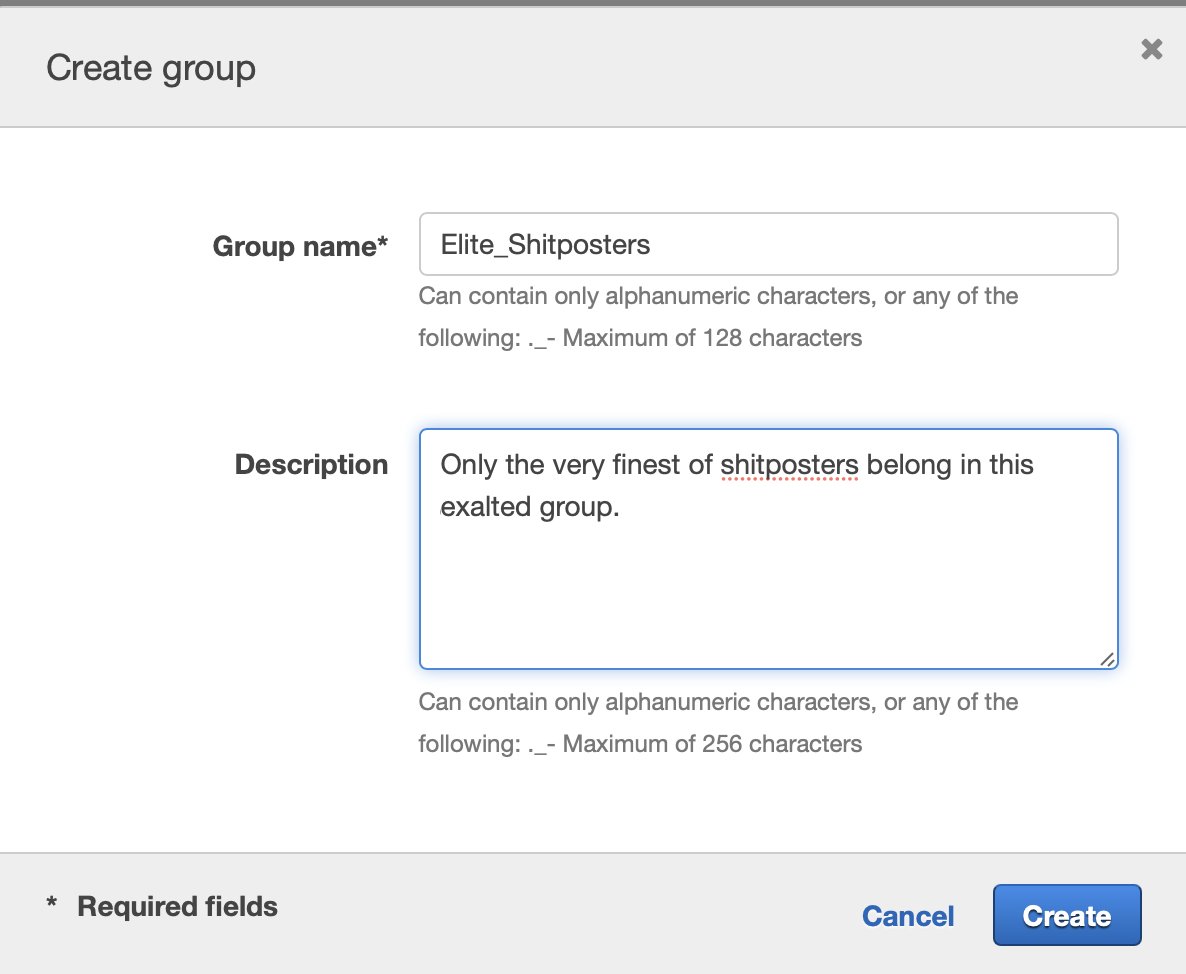
I create a group that's almost but not quite as dangerous as the root user because it can't change my Support plan.
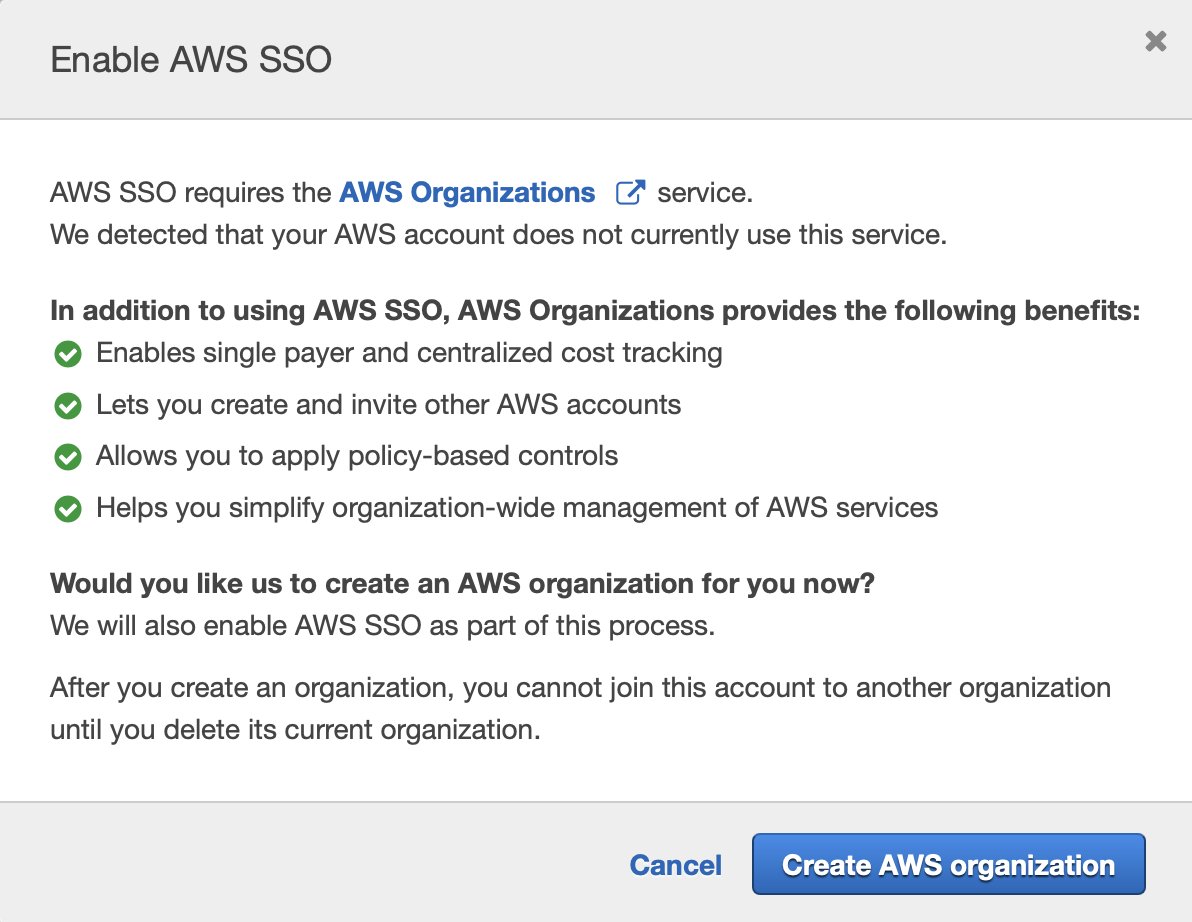
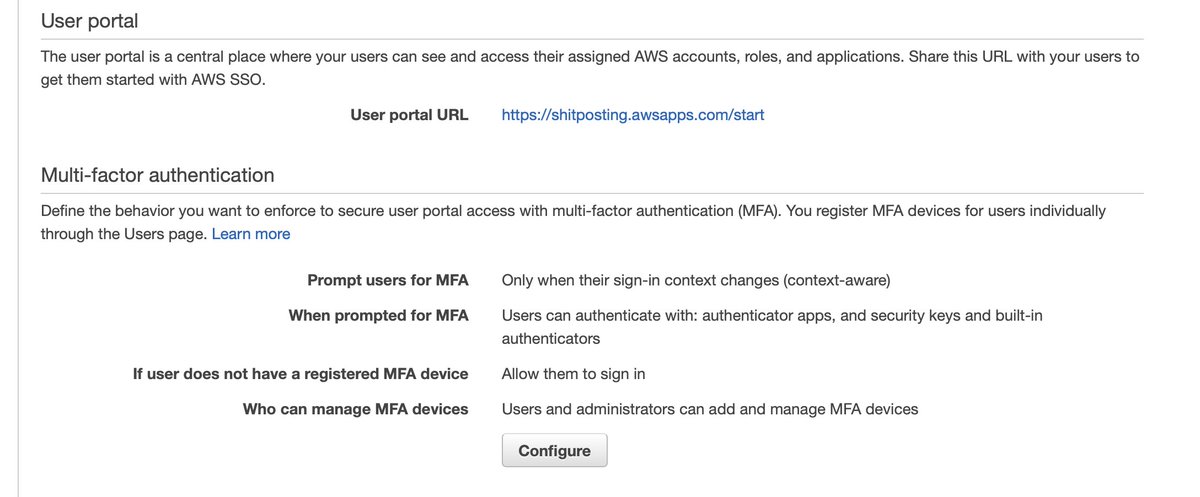
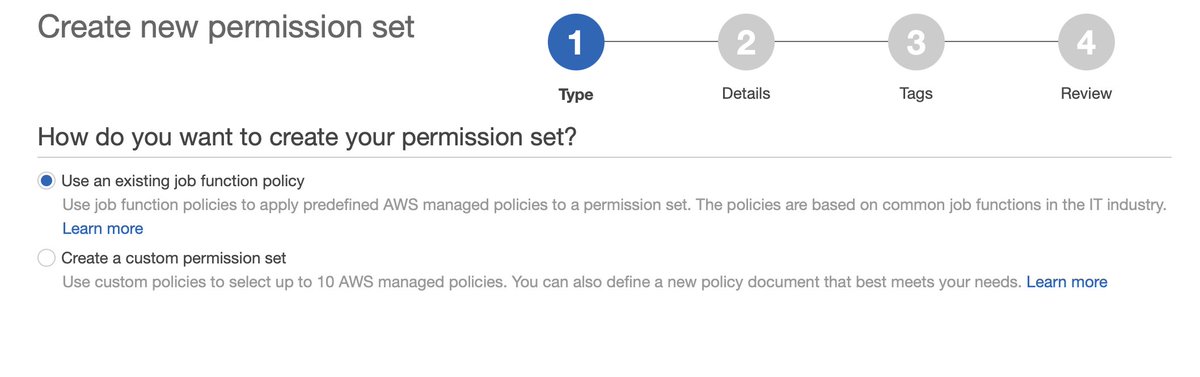
All right, let's back this out a bit and try AWS SSO. https://twitter.com/darrengruber/status/1359249144389459969?s=20
SSO isn't within IAM because of course it isn't. We'll suspend credulity and navigate to the service directly.
We'll further suspend credulity and assume a new user wouldn't run screaming at first sight:
We'll further suspend credulity and assume a new user wouldn't run screaming at first sight:
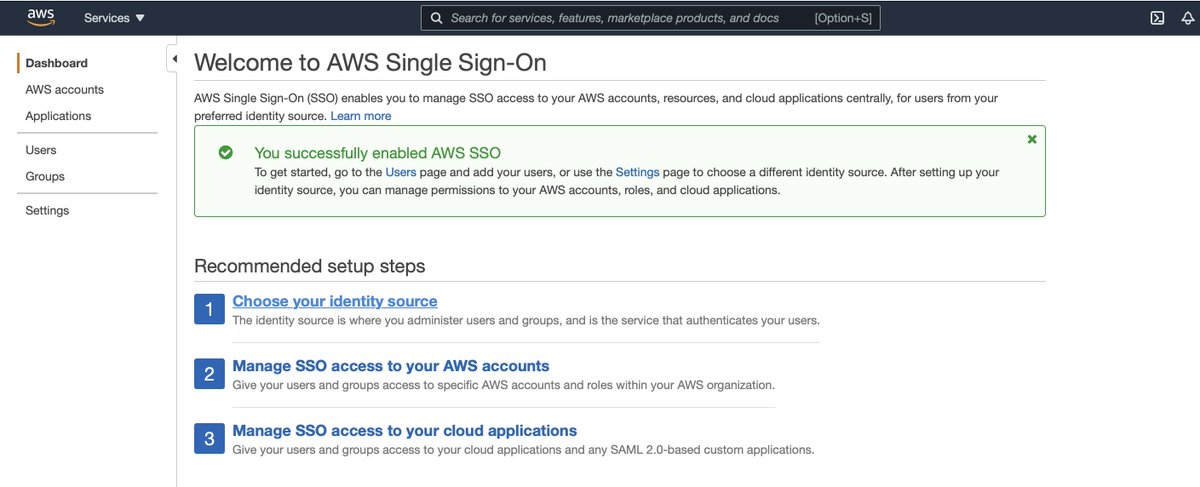
We're well and truly into fantasy-land here for the new user use case unless the new user's day job is " @awscloud Principal Solutions Architect." With a focus on Identity.
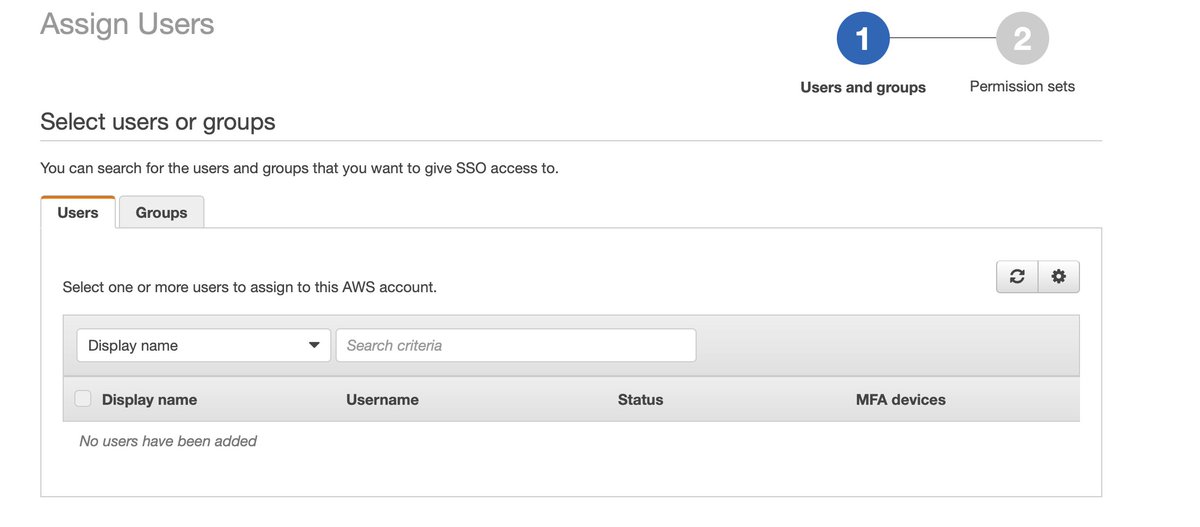
Now it prompts me to assign users and groups to grant access. The resulting dialogue is @gcpsupport levels of helpful.
Lies, damned lies, and the "allowed character" set on the second text field. This submission was accepted.
We pause again for my "weekly marketing sync" meeting.
"Corey, why were you late?"
"I was marketing."
The entire team visibly flinches.
"Corey, why were you late?"
"I was marketing."
The entire team visibly flinches.
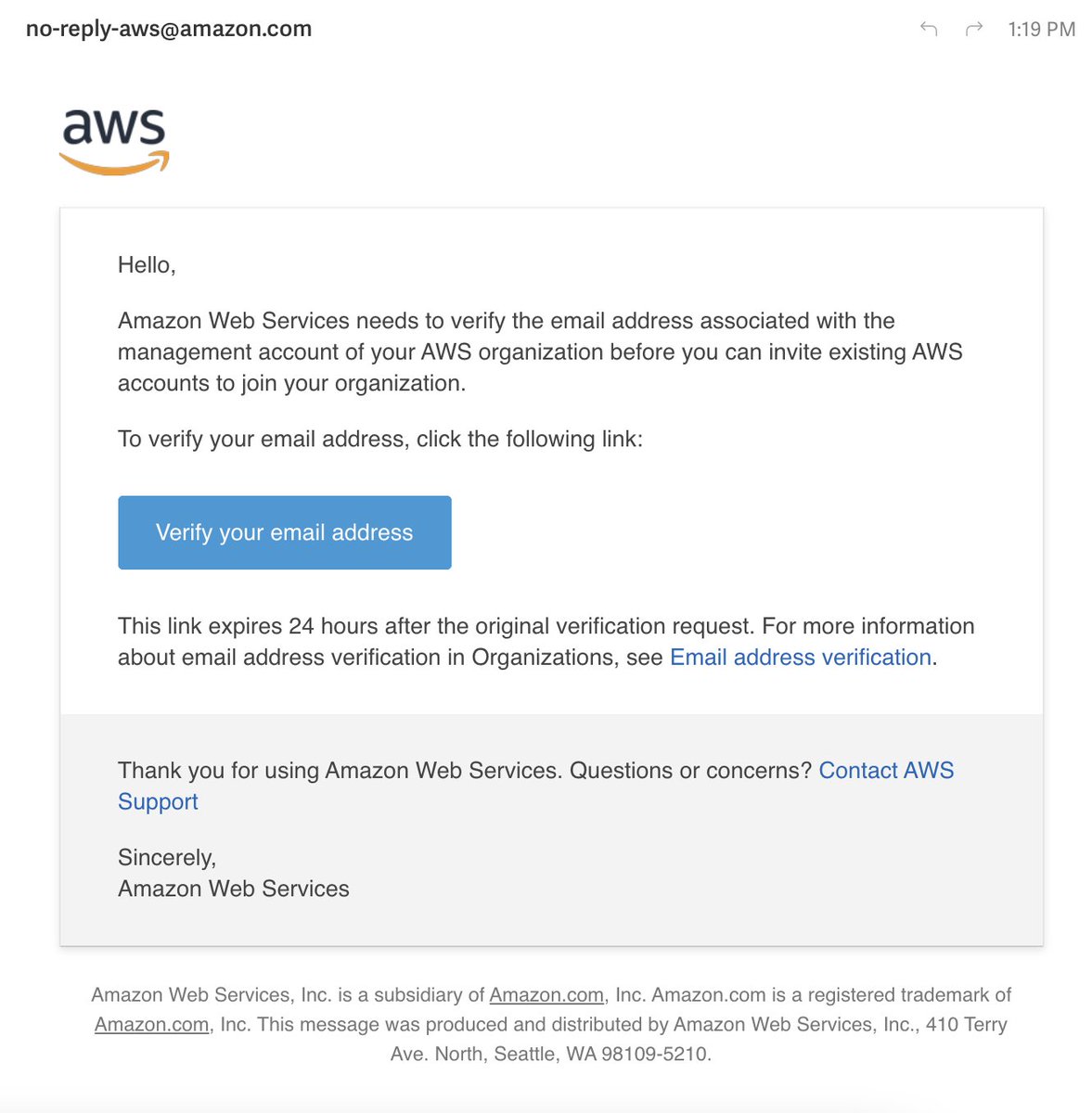
While I was marketing, @awscloud was emailing. Unclear if this is a phishing attempt, from AWS, or a phishing attempt from AWS.
Gotta say, @awscloud's SSO offering has more insight into the way enterprises work than any AWS billing offering I've ever seen.
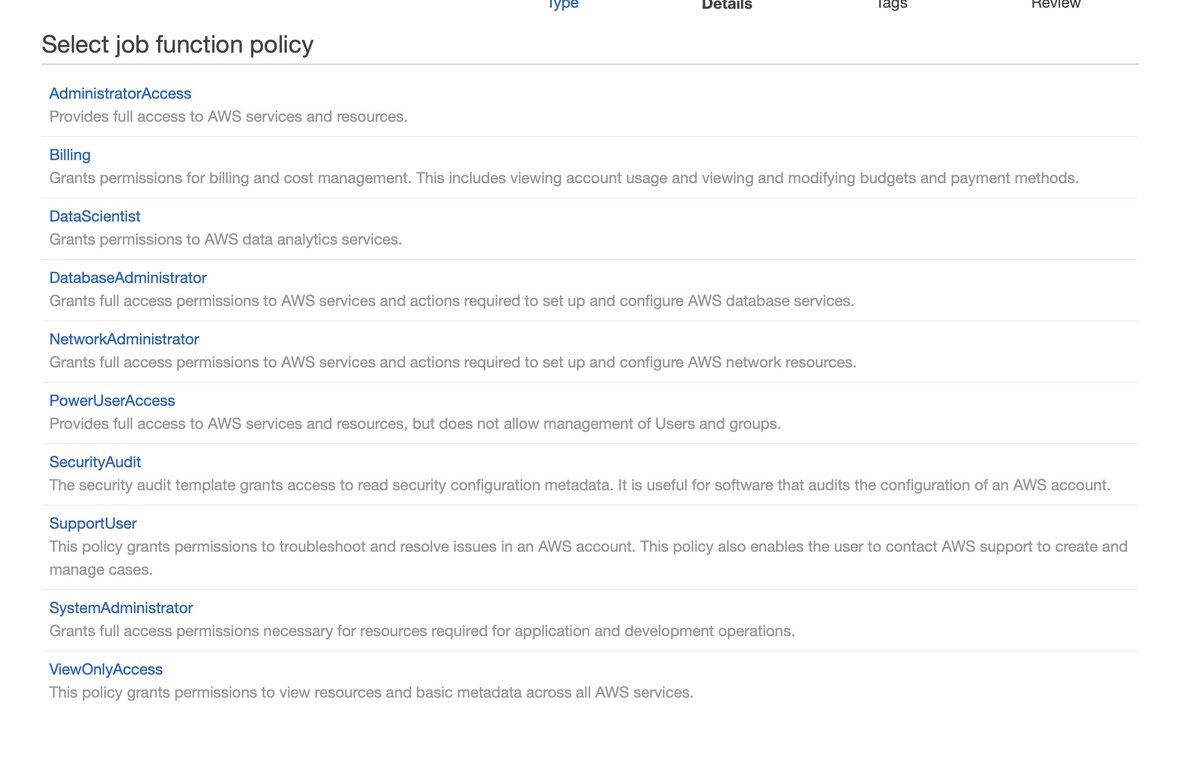
Note that a "Permission Set" is not the same thing as a user, a group, a role, a security group, an ACL, or anything else you may be familiar with.
There is zero chance that the permissions assigned to each of these roles will not make someone gravely upset.
"Go ahead and assign some arbitrary tags. It likely won't hurt you until after you realize it can hurt you."
Aha! The SSO dashboard is now populated. Much like the ill-fated time I attempted to court a data scientist in my 20s, AWS is now speaking to me mostly in numbers.
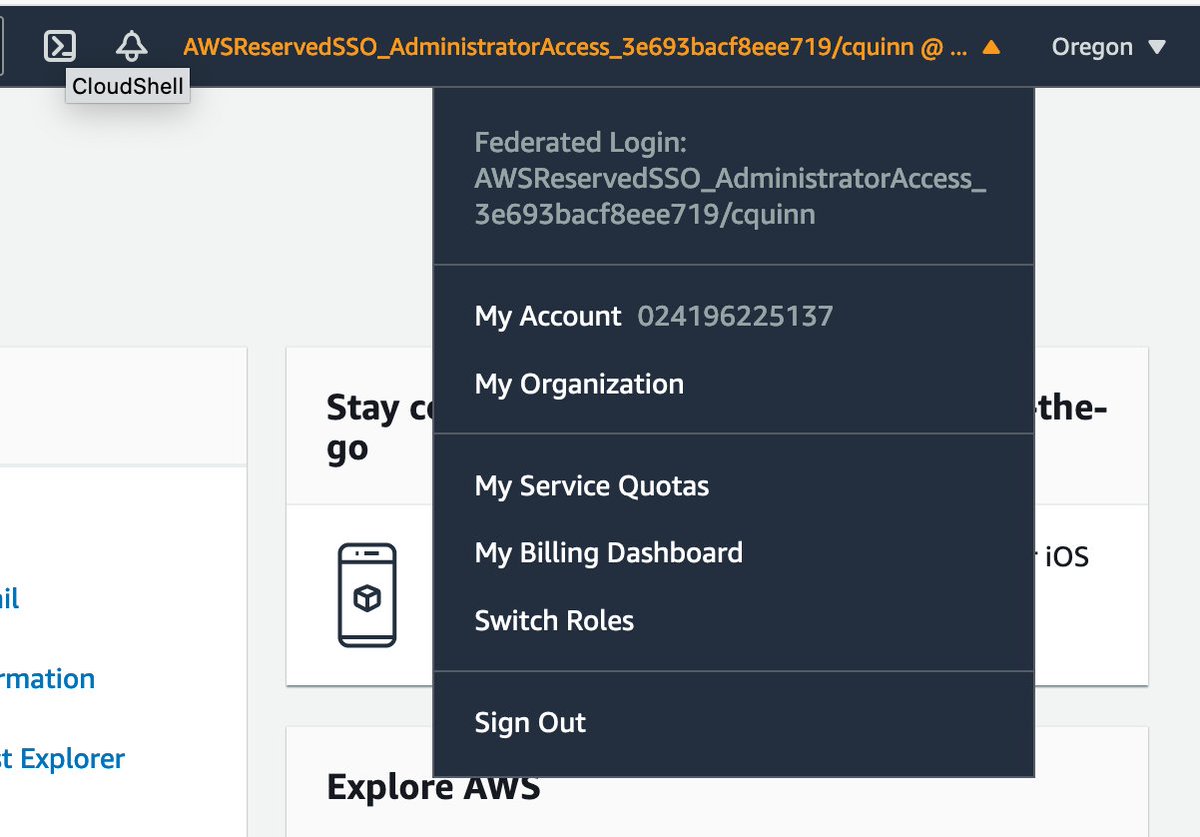
The synergy continues; I click into the Management Console, and I want to throw up. So does the logged-in-user string.
Remember how I was logged in by default to the Ohio region as root? Now that I'm using SSO I'm in Oregon, as a delightful surprise for me to discover after a week of effort.
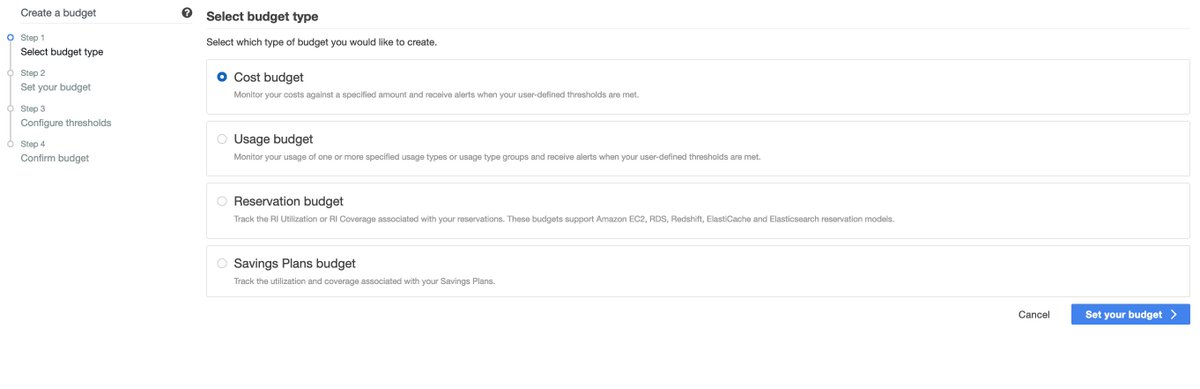
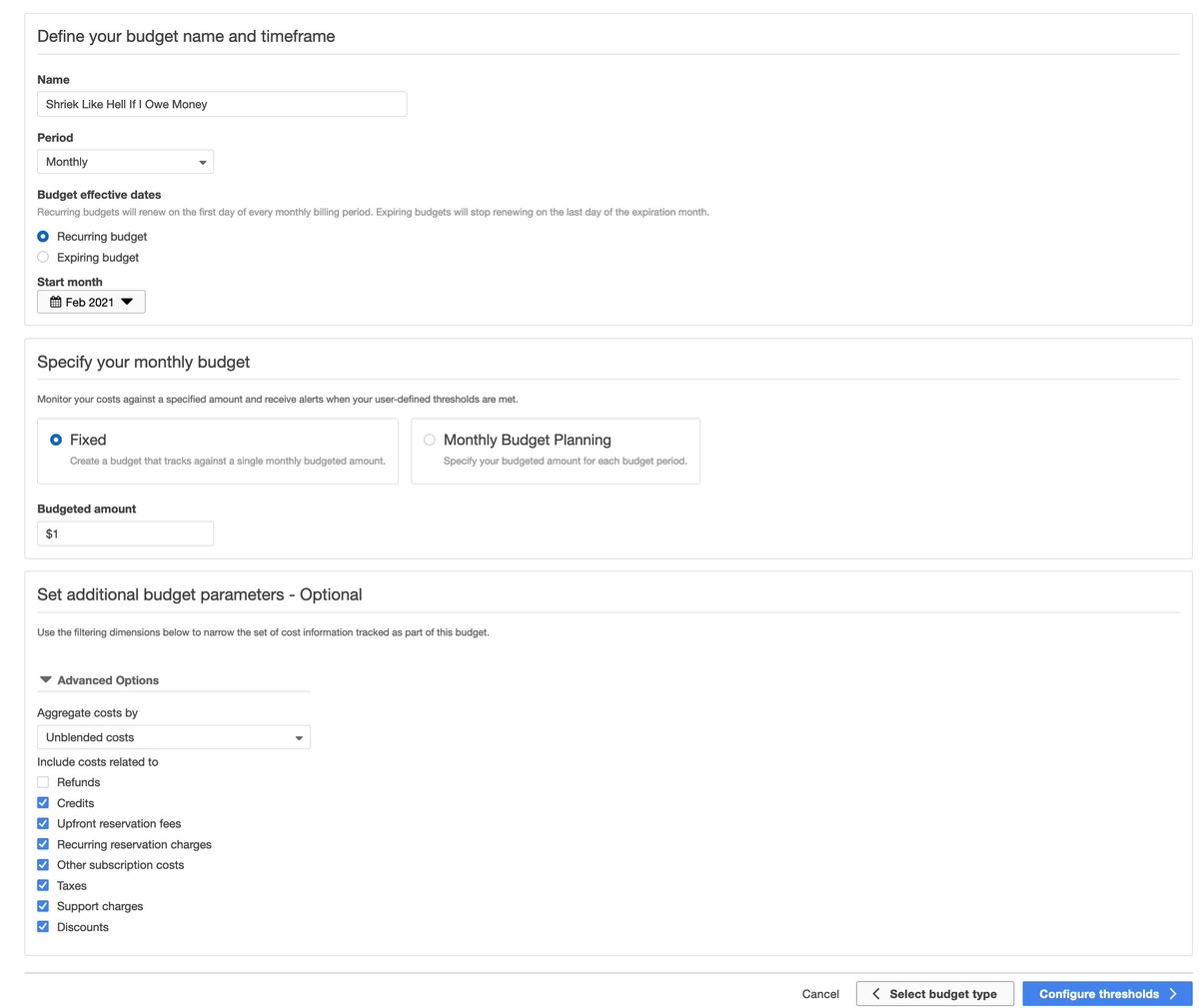
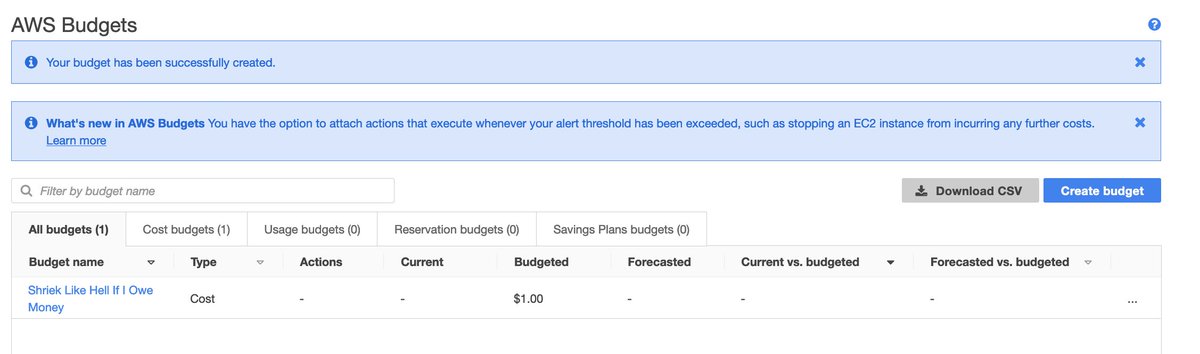
Let's do the responsible thing and set up some billing alerts FIRST.
Not so fast! @awscloud is on to my tricks by now.
Not so fast! @awscloud is on to my tricks by now.
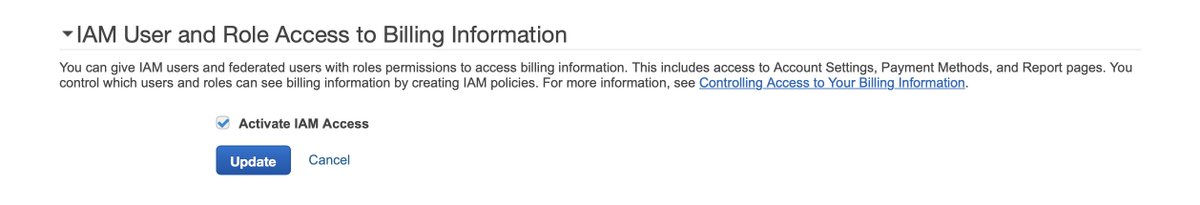
Back in the root account, well down the preferences page, behind a collapsed divider with only one entry, guarded by a leopard, we find this treasure.
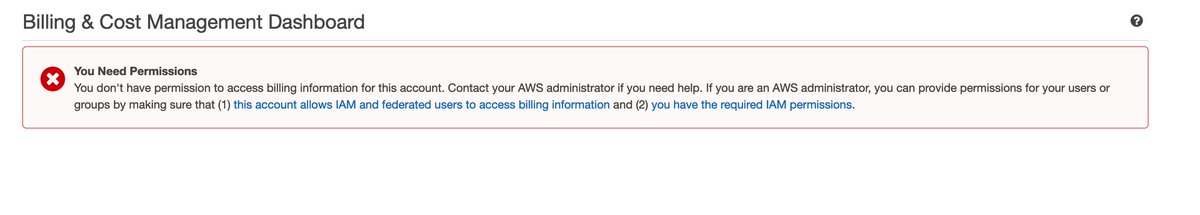
Suddenly the people who can incur bills get to see those bills as well.
This threatens the model.
Suddenly the people who can incur bills get to see those bills as well.
This threatens the model.
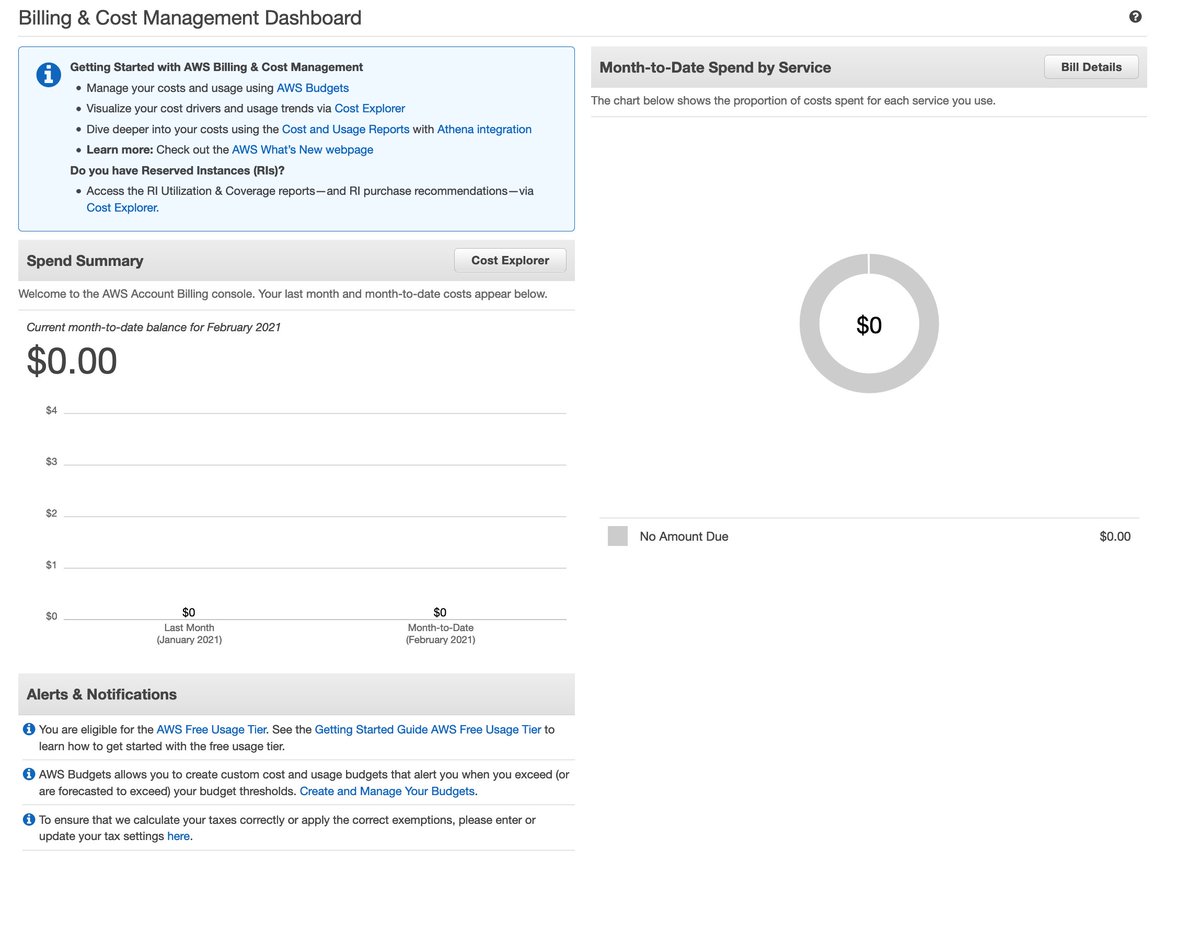
The billing dashboard opens before me. Given that I've not stood up a single billable resource so far, AWS swings into action, urging me to purchase a Reserved Instance.
I can get alerts when I approach my budget. If someone really wanted to Deliver Results, Twitter would also be an option.
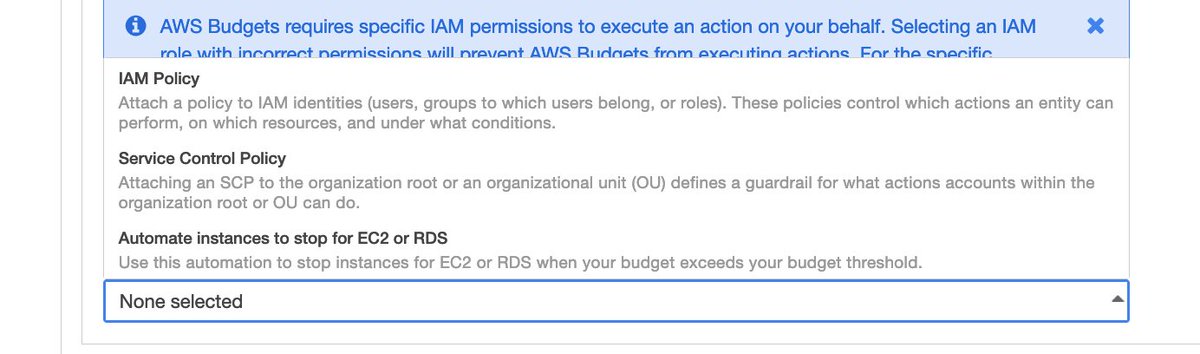
Sadly there is no Budget Action available for "find the thing that is costing me money and obliterate it."
Also, fun surprise that nobody mentions: This will optimistically be 8 hours behind reality, and occasionally more than that. If you think this is realtime, ouch.
Also, fun surprise that nobody mentions: This will optimistically be 8 hours behind reality, and occasionally more than that. If you think this is realtime, ouch.
And there we go; I should theoretically get email if I breach the free tier (or am projected to) by a dollar.
Let's see, other best practices.
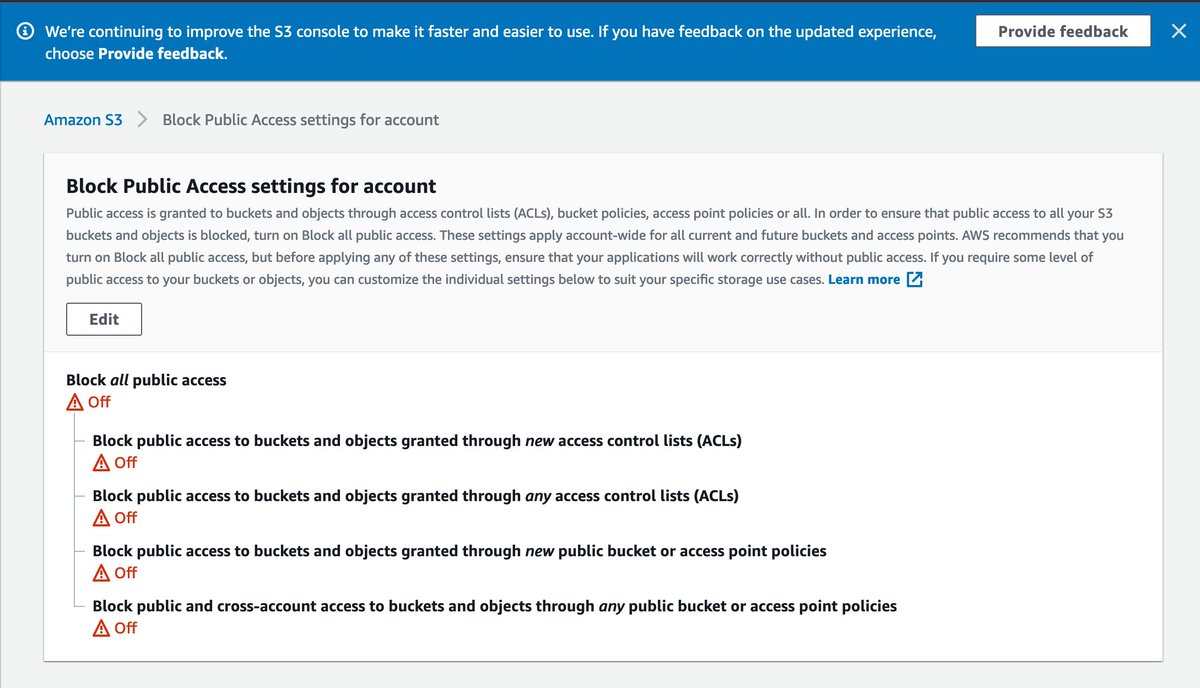
There are a few ways I want to be notified about security breaches, but "the front page of the New York Times" isn't one, so let's lock down my S3 buckets before I have them.
There are a few ways I want to be notified about security breaches, but "the front page of the New York Times" isn't one, so let's lock down my S3 buckets before I have them.
(If you misconfigure an S3 bucket, it's on you. This makes it harder to do. It also breaks a few valid use cases.)
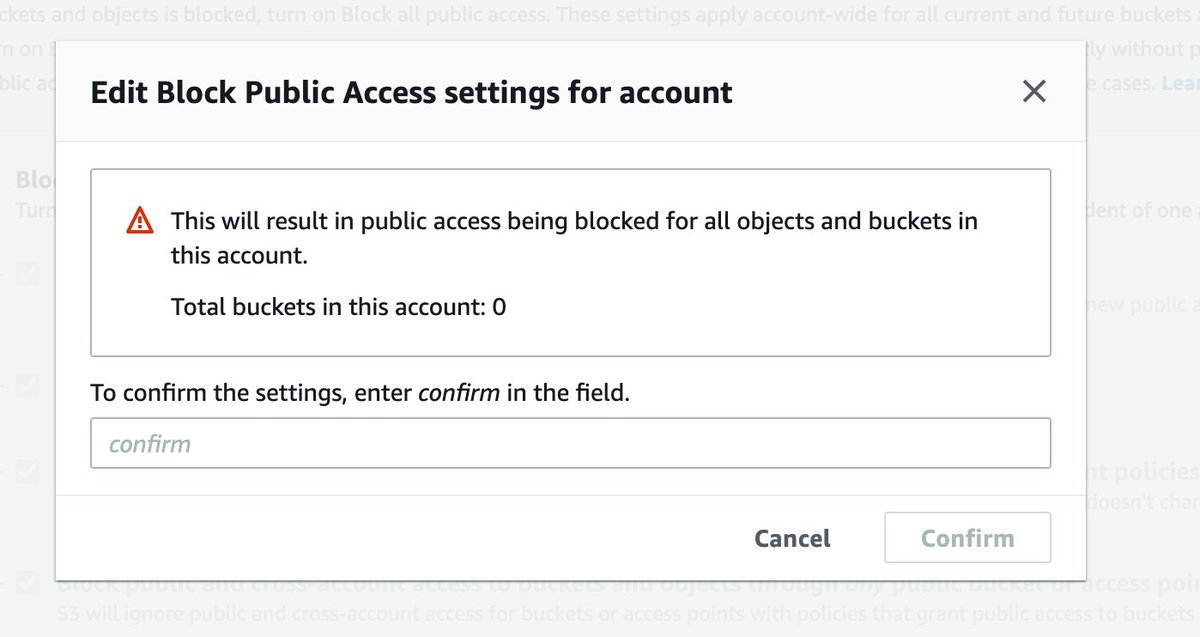
Every AWS service has Serious Consequences actions. Each one picks a different word to have you type.
Okay, so S3 public access blocked. Signing in is now marginally safer while being far more annoying (unless you dig to discover the aws cli v2's support for SSO). I've set up budget alarms and enabled non-root to see the bill.
Next time I'll attempt to actually get work done.
Next time I'll attempt to actually get work done.

 Read on Twitter
Read on Twitter