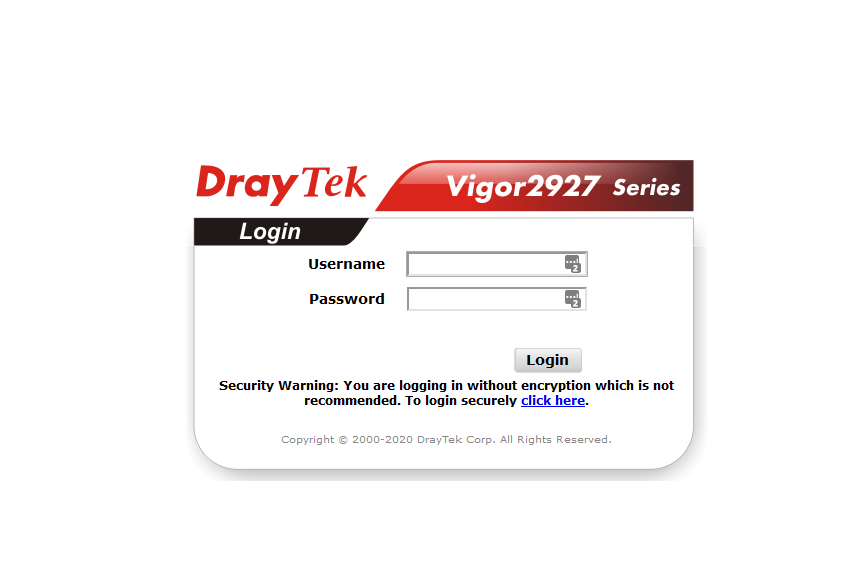
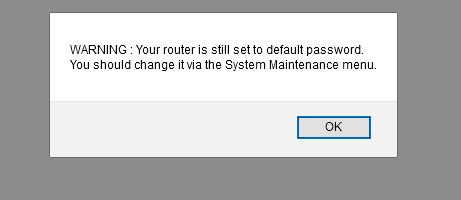
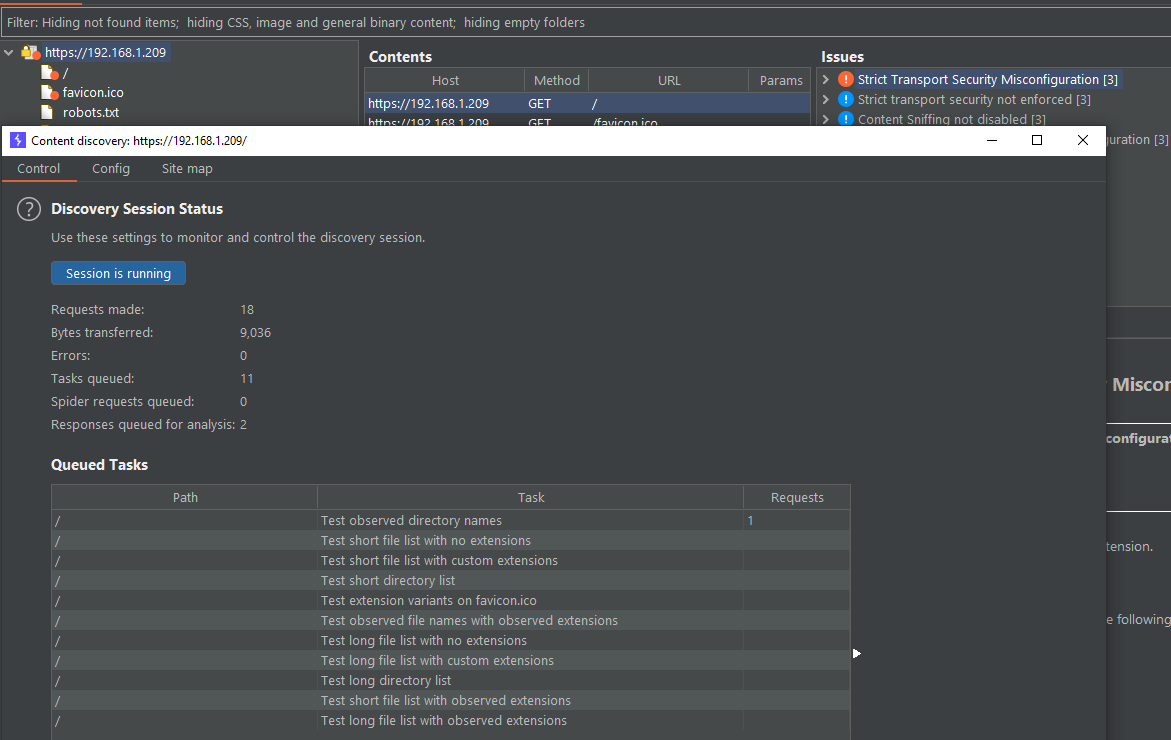
ok so default IP is 192.168.1.1 on a /24... no suprise there the admin interface on the LAN side is running on 80 and i assume 443... to the nmap we go! admin:admin should get us in!
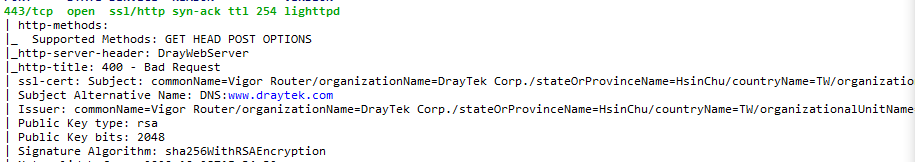
yeah ok that's on TCP 443 using HTTPs we can see the firmware likely isn't up to date due to the copyright date
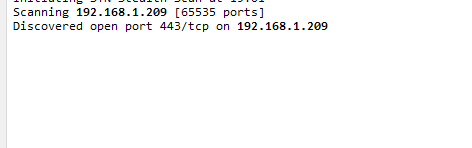
ok we have TCP 21, 22, 23,80,443 and 1194 open by default (full 65535 ports scanned timing mode 4)
ok that's still port scanning.. time to check out the WAN interface!
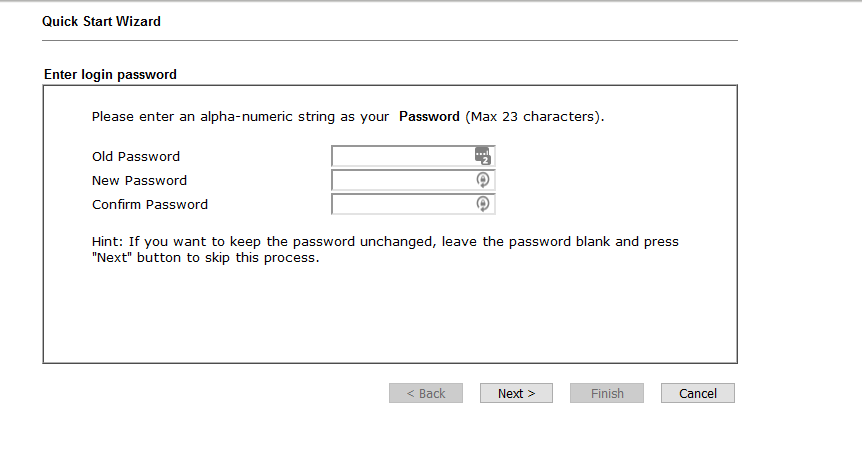
ther quick start wizard has a max password of 23 chars. we'll abort that and go see if we can find the WAN IP
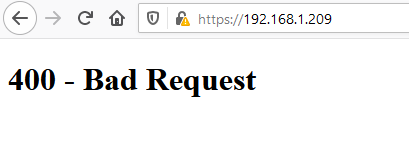
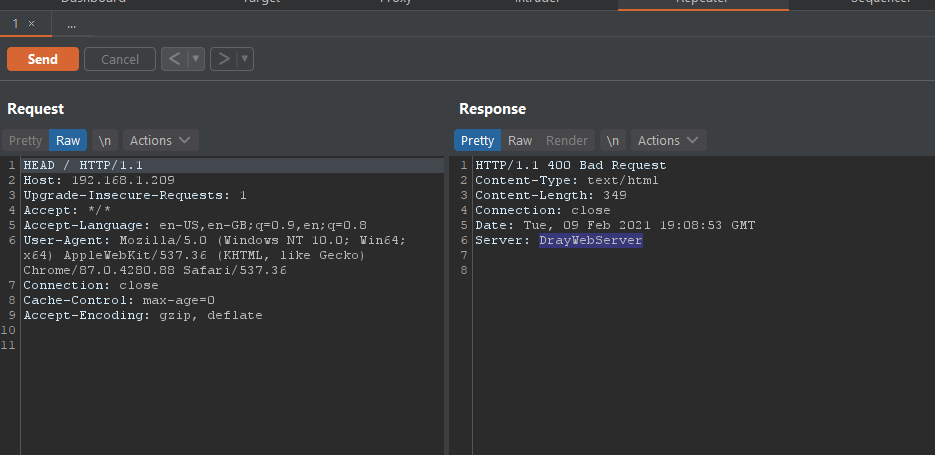
n0000000000000000000000000000000000000000000 interface exposed on TCP 443 but... bad request.. also TCP 1194 (openvpn?) (the WAN IP is 192.168.1.x on purpose for those confused - i flicked the LAN ip to .200.1/24
this is what we see! i got a work meeting shortly but if anyone knows more about this web service shout tweeps!

 Read on Twitter
Read on Twitter