#CyberGirlSafety and security is an important topic. Dr. Ananth Prabhu has created a series of usecases with the law enforecement personnnel. Sharing the details here in this thread.
Please do spread this as much as possible for women to be safe and secure. https://twitter.com/InfoSecAwa/status/1255091323788550144
Please do spread this as much as possible for women to be safe and secure. https://twitter.com/InfoSecAwa/status/1255091323788550144
#UseCase 1: MOBILE RECHARGE SHOP
Mobile Recharge Shop is where scamsters can gain access to your cellphone number because you have provided it to the recharge vendor.
They will misuse your number to call/ text you, exploit your ignorance or even emotionally manipulate you.
Mobile Recharge Shop is where scamsters can gain access to your cellphone number because you have provided it to the recharge vendor.
They will misuse your number to call/ text you, exploit your ignorance or even emotionally manipulate you.
There's nothing called FREE.
Everything comes for a Charge and in case of Recharge, there’s no Free Charge!
#ICYMI #betibachaobetipadhao
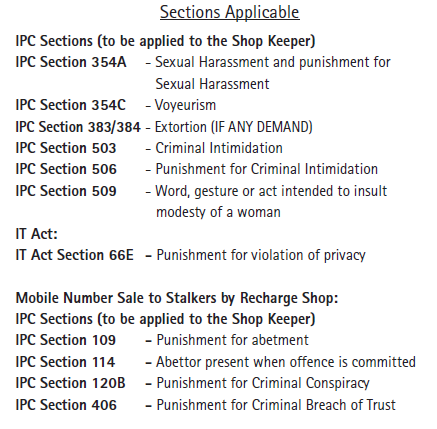
The following sections in #IndianPenalCode come into effect to help you and punish the #scamster. Don't hesitate, go ahead and file an FIR
Everything comes for a Charge and in case of Recharge, there’s no Free Charge!
#ICYMI #betibachaobetipadhao
The following sections in #IndianPenalCode come into effect to help you and punish the #scamster. Don't hesitate, go ahead and file an FIR
#UseCase 2: Debit Card/ Credit Card CLONING
Debit Card #skimming happens when PIN is revealed to another person.
A scamster who knows the PIN and has possession of the card even for a short while can replicate the card with a skimming device and withdraw cash.
Debit Card #skimming happens when PIN is revealed to another person.
A scamster who knows the PIN and has possession of the card even for a short while can replicate the card with a skimming device and withdraw cash.
NEVER ever reveal your PIN to anyone.
Activate #TwoFactorAuthentication for all your accounts.
Your entire savings may get wiped out.
#ICYMI Eventhough following safeguards are available, if the PIN has been used during a transaction, banks define it as valid transaction.
Activate #TwoFactorAuthentication for all your accounts.
Your entire savings may get wiped out.
#ICYMI Eventhough following safeguards are available, if the PIN has been used during a transaction, banks define it as valid transaction.
#Usecase 3: Keyloggers are simple malicious programs that can be installed on the your computer. They record your keystrokes and scamster can collect your login details and hence, other files in your computer.
ALWAYs, lock your computers.
#dataprotection #passwords #Privacy
ALWAYs, lock your computers.
#dataprotection #passwords #Privacy
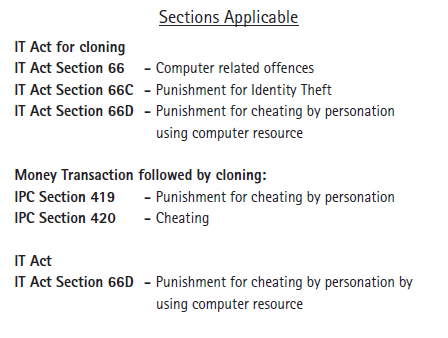
Better be safe than sorry. Eventhough, the following sections in #ITAct in India can help you, but damage caused can't be reversed easily.
#StrongPasswords Remember, these days, your laptops, mobiles have so much data about you, they can replicate you completely in #cyberspace
#StrongPasswords Remember, these days, your laptops, mobiles have so much data about you, they can replicate you completely in #cyberspace
Just to give you a glimpse of how much data you are releasing into the market everyday, follow this thread.
When I say "market", know that your data is available for anyone who pays for it. Your smartphones, smartTVs, smartdevices are listening devices. https://twitter.com/smnayak/status/1348297716170850305?s=20
When I say "market", know that your data is available for anyone who pays for it. Your smartphones, smartTVs, smartdevices are listening devices. https://twitter.com/smnayak/status/1348297716170850305?s=20

 Read on Twitter
Read on Twitter