New phishing attack uses Morse code to hide malicious URLs - @LawrenceAbrams https://www.bleepingcomputer.com/news/security/new-phishing-attack-uses-morse-code-to-hide-malicious-urls/
A phishing campaign starting at the beginning of the month uses a novel approach of utilizing Morse code to obfuscate the malicious URLs used to generate a login form.
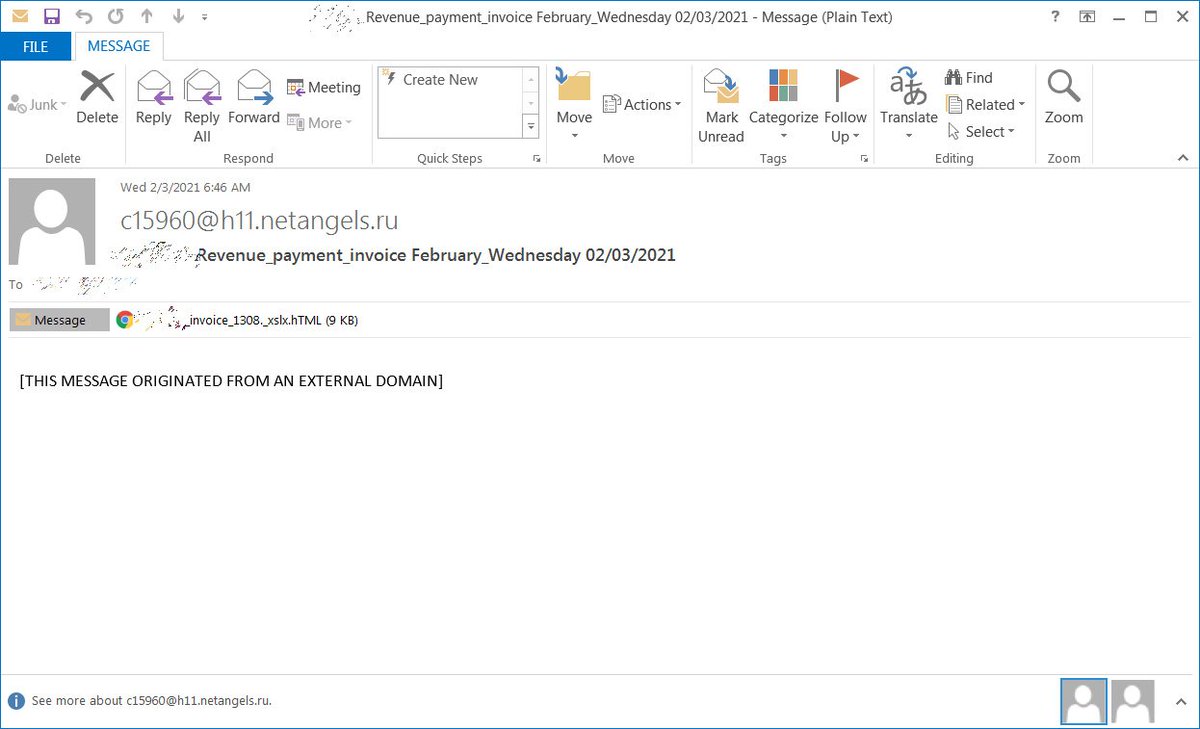
The campaign starts with a simple email pretending to be an invoice with a HTML attachment disguised as an Excel spreadsheet.
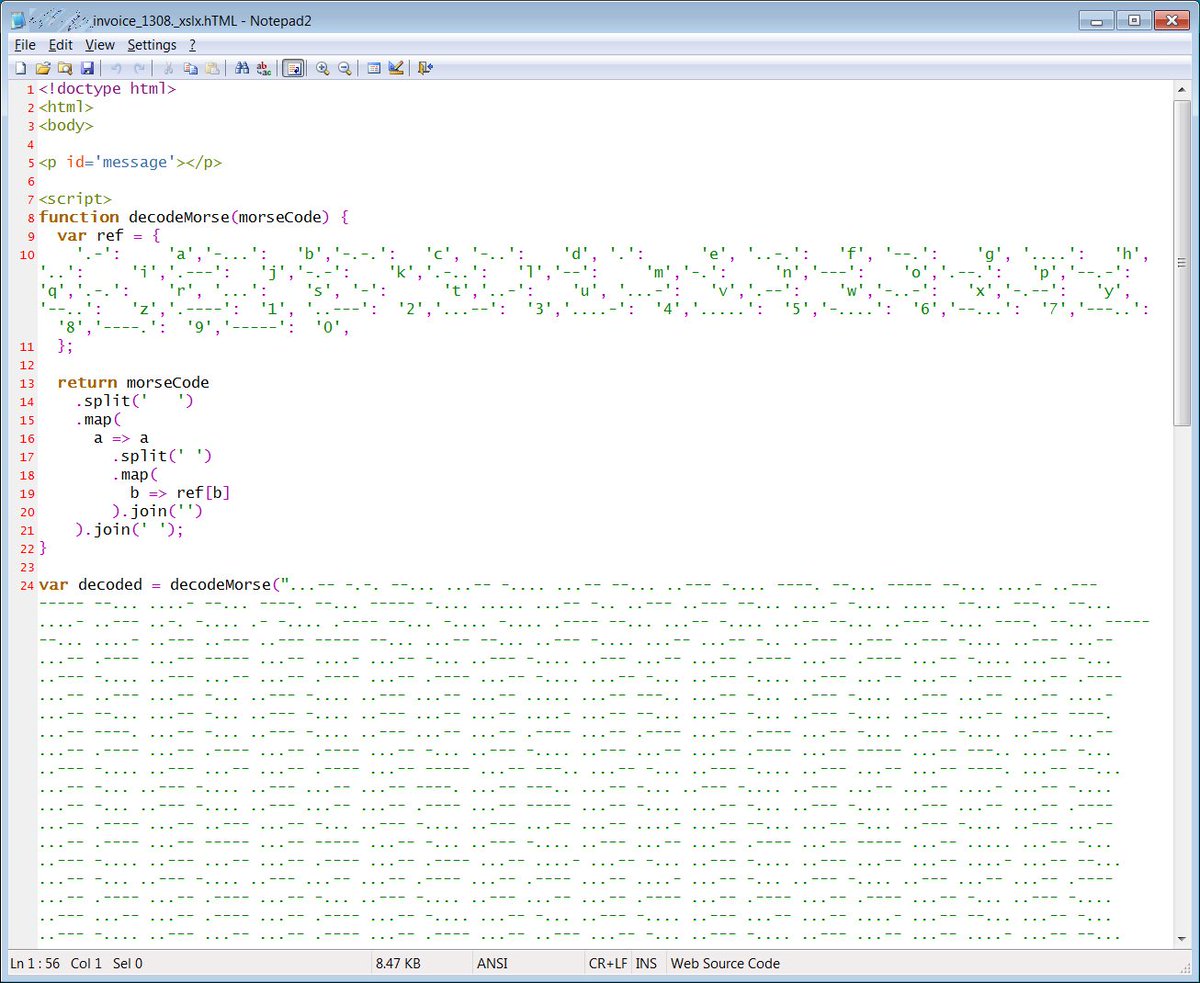
The HTML in harmless at first glance but does contain JavaScript that maps letters and numbers to their Morse code equivalent in dits (periods) and dahs (dashes).
The script then decodes a Morse code string that leads to two <script> statements that are then injected into the HTML document when opened.
These two scripts contain the meat of the phishing page, including the login form, images to use, a fake excel background, etc.
These two scripts contain the meat of the phishing page, including the login form, images to use, a fake excel background, etc.
To display company logos for the targeted companies, the attachment uses http://logo.clearbit.com/ to automatically fetch a logo via a domain name.
For example, http://logo.clearbit.com/microsoft.com pulls down Microsoft's logo.
This allows for a dynamic approach to rendering the login form.
For example, http://logo.clearbit.com/microsoft.com pulls down Microsoft's logo.
This allows for a dynamic approach to rendering the login form.
This ultimately displays a login form in the browser that pretends to be an Excel spreadsheet where the user needs to login again to view it.
For those who want to play with this phishing attachment, I have removed the original recipient and replaced them with BleepingComputer equivalents here. https://pastebin.com/JbdhvP3h

 Read on Twitter
Read on Twitter