Infosec fail thread:
So, in the last couple of weeks I've been looking into a product we were thinking of offering to our customers.
This time, we were looking into the FootfallCam 3D plus. A counter system to measure how many people are in a building.
1/n
So, in the last couple of weeks I've been looking into a product we were thinking of offering to our customers.
This time, we were looking into the FootfallCam 3D plus. A counter system to measure how many people are in a building.
1/n
As per usual, I usually do some basic security / sanity checks on a product before offering it to our customers.
So, we powered it on, and followed the instructions to set it up. It gets powered over Ethernet, but also has WiFi to count the number of devices passing it.
2/n
So, we powered it on, and followed the instructions to set it up. It gets powered over Ethernet, but also has WiFi to count the number of devices passing it.
2/n
The first thing that caught our eye, is that it sets up a network, with a broadcasted SSID and a default password. Bit strange, since it's also connected over Ethernet, but fine. Whatever.
Except: you can't change the SSID or the password!
Ouch!
3/n
Except: you can't change the SSID or the password!
Ouch!
3/n
Also, you can't change the admin password (it's 123456 by the way) and the interface looks like a quickly pulled together HTML5 Bootstrap app that includes several open source libraries to achieve what it does (count blobs of color passing the camera).
4/n
4/n
The interface is accessible both over ethernet and over WiFi. Hmh, that sounds a bit suspect, but let's carry on.
Let's open it up.
Yes, it's a Raspberry Pi Compute Module.
5/n
Let's open it up.
Yes, it's a Raspberry Pi Compute Module.
5/n
Well, that's easy, we can dump the firmware quite easily. Let's plug it in to a Raspberry Pi CM IO board and dump it.
Looks like a normal Raspbian installation, with a lot of opensource packages and some very suspicious files.
6/n
Looks like a normal Raspbian installation, with a lot of opensource packages and some very suspicious files.
6/n
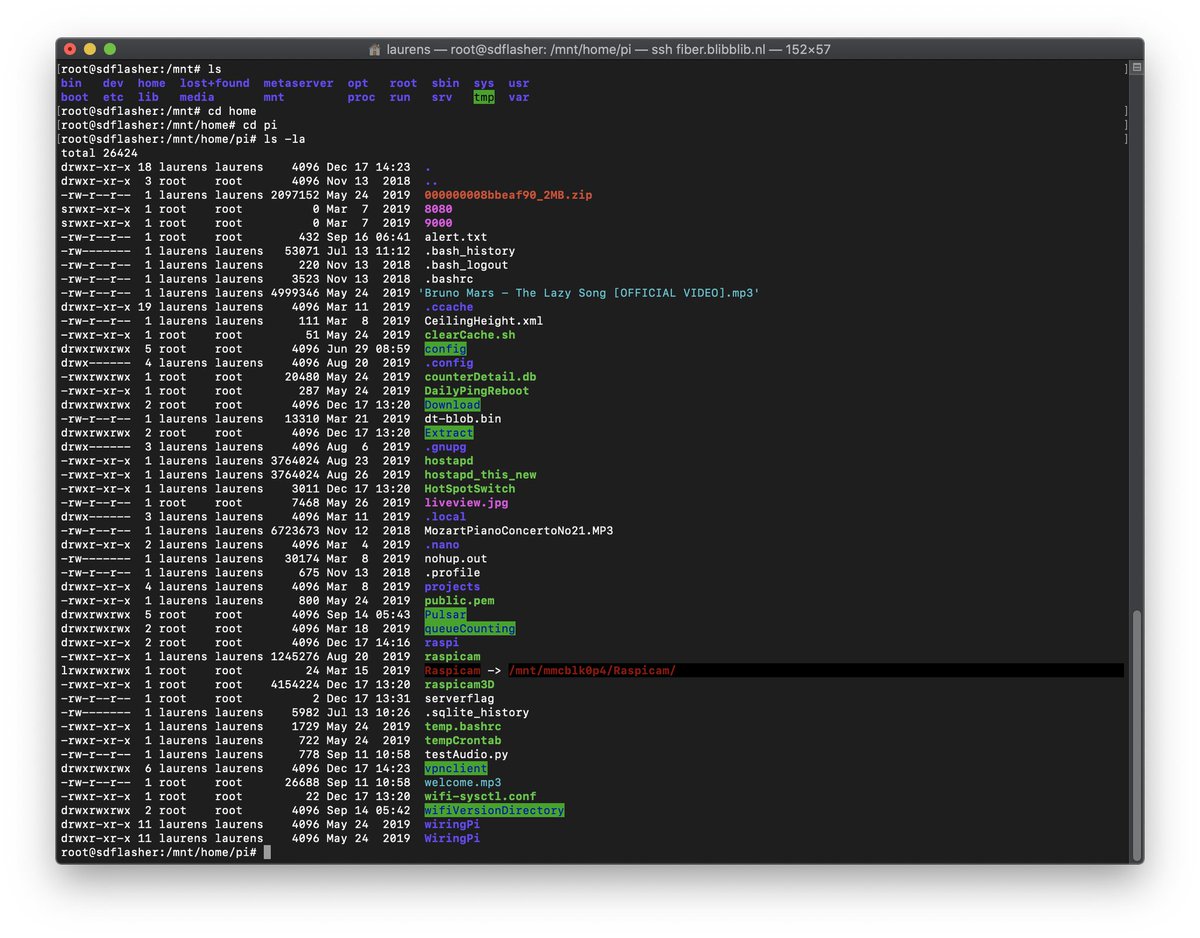
Hmh, the pi user is still active. This is the home directory...
(It has a different user here, as the UID is the same as my account, that's my name ;))
Those are some very strange files for a production device...
Is that... A Bruno Mars MP3?
7/n
(It has a different user here, as the UID is the same as my account, that's my name ;))
Those are some very strange files for a production device...
Is that... A Bruno Mars MP3?
7/n
Yes, yes it is. It almost looks like they just took the home directory from the developers machine and plopped it on the eMMC of the camera!
Ofcourse the BASH and SQLite history files were filled to the brim with instructions.
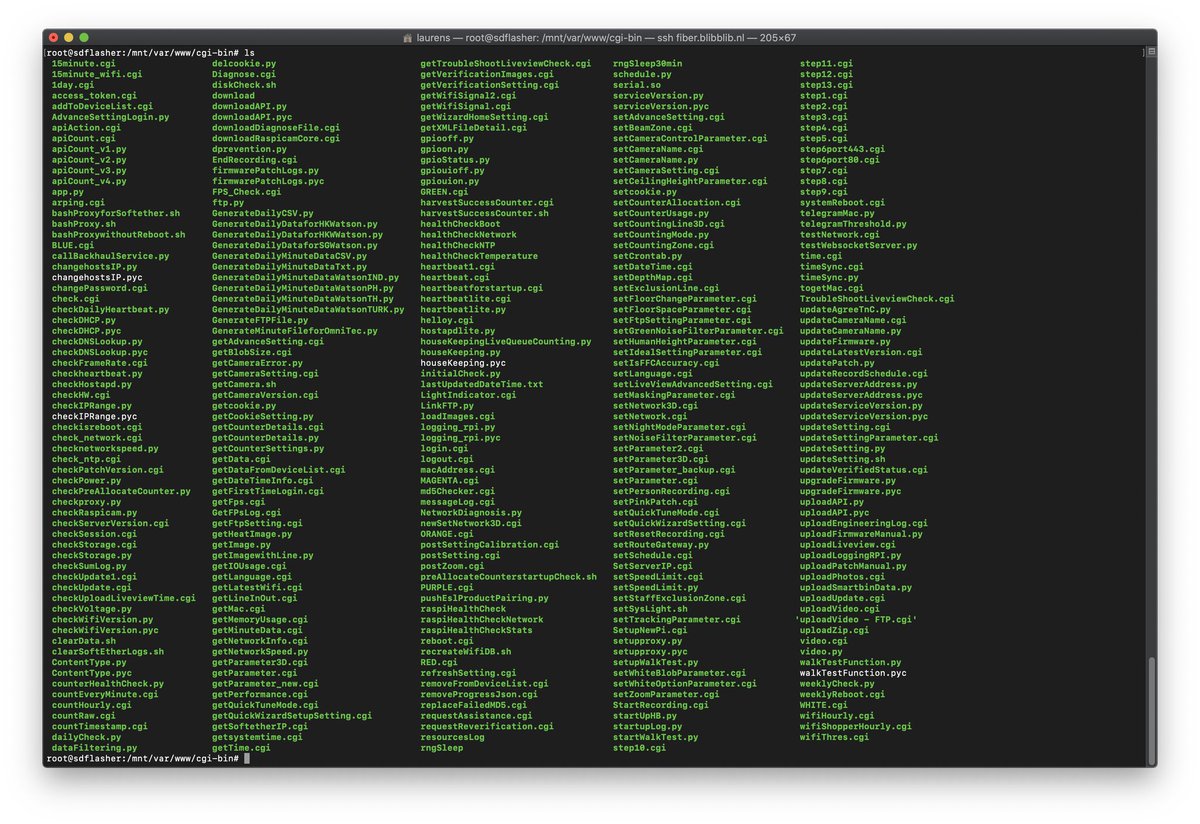
Let's take a look at the web server directory.
8/n
Ofcourse the BASH and SQLite history files were filled to the brim with instructions.
Let's take a look at the web server directory.
8/n
Aaah, a random assortment of compiled and uncompiled python files. Just what you need to get a certain "eeewwww" feeling from a production device.
Ofcourse, NONE of the files does any authentication. They can be called by anyone at any time.
9/n
Ofcourse, NONE of the files does any authentication. They can be called by anyone at any time.
9/n
So, let's inform the vendor. I don't want to sell this product to my customers, unless there's some serious reworking of the software.
That was 5 weeks ago. Didn't hear anything back...
So let's dig a little deeper.
10/n
That was 5 weeks ago. Didn't hear anything back...
So let's dig a little deeper.
10/n
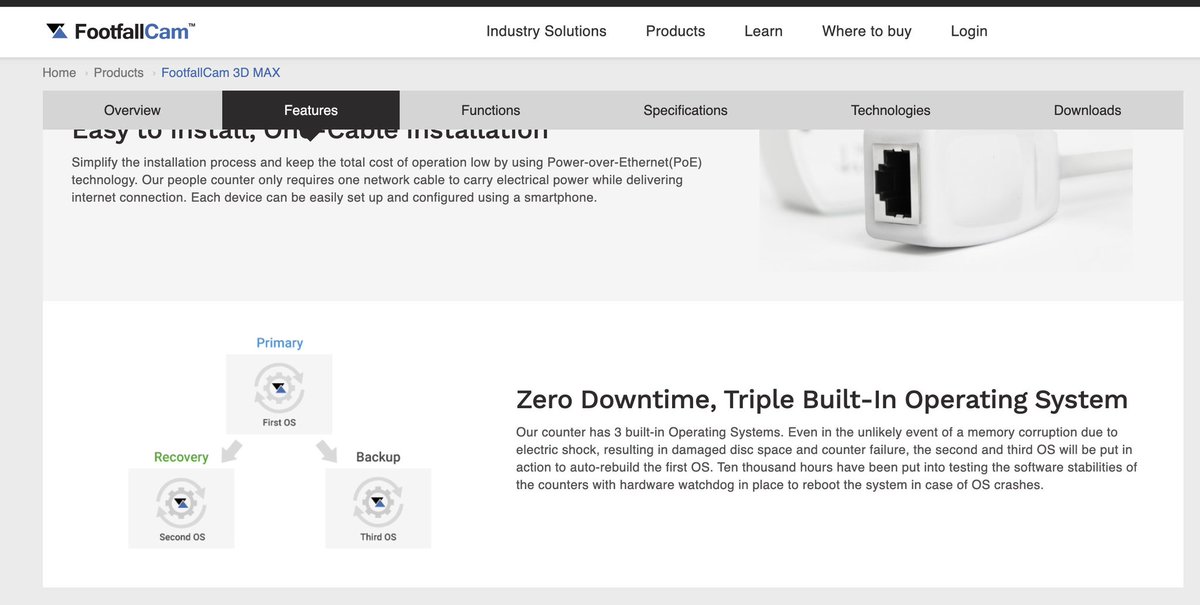
Look at what their website says. "Triple Built-In OS"
This is clearly OBVIOUSLY bullshit. It's running standard Raspbian. With a standard pi user. WITH SSH ENABLED.
Oh yes, it gets even worse!
11/n
This is clearly OBVIOUSLY bullshit. It's running standard Raspbian. With a standard pi user. WITH SSH ENABLED.
Oh yes, it gets even worse!
11/n
The pi user is still active and allowed on a running SSH server. They did change the password, but that shadow file certainly comes in handy.
I will not post the password here, but it's not exactly difficult to crack OR guess.
12/n
I will not post the password here, but it's not exactly difficult to crack OR guess.
12/n
So, now we have a device. In a customers corporate network. Broadcasting an SSID with an unchangeable password, running SSH, with a user that uses a standard unchangeable password, that has sudo ability.
You can see why this is bad.
13/n
You can see why this is bad.
13/n
If you know the default SSID password, and default user password, you have full access to the network that it's connected to.
Yeah. Great product guys.
14/n
Yeah. Great product guys.
14/n
So what more do they say about their product on their website?
AI image processing? No, you must mean an opensource library, conveniently called "Footfall".
It uses machine learning (Tensorflow) and LITERALLY uses the same example code as the library.
15/n
AI image processing? No, you must mean an opensource library, conveniently called "Footfall".
It uses machine learning (Tensorflow) and LITERALLY uses the same example code as the library.
15/n
Wow, this is going great. Certainly a product I want to offer to my customers.
They haven't responded to me or any of my colleagues in 5 weeks now. They don't really seem to care and since I don't have an NDA, I'm posting it on Twitter. :)
16/n
They haven't responded to me or any of my colleagues in 5 weeks now. They don't really seem to care and since I don't have an NDA, I'm posting it on Twitter. :)
16/n
I don't want to really dig into any more gory details (there are many), but it hasn't happened often that I come across such an unfinished product that they claim is installed in tens of thousands of offices.
If you see one, please notify the owner it is unsafe.
17/n
If you see one, please notify the owner it is unsafe.
17/n
This thread wasn't sponsored, I wasn't paid to do this. It's just... So bad.
Has anyone come across something this bad before? It's not unsafe because of bugs. It's just extreme oversight and lack of security.
18/18
Has anyone come across something this bad before? It's not unsafe because of bugs. It's just extreme oversight and lack of security.
18/18
Hey @cybergibbons , I'm allowed to talk about it now. ;)
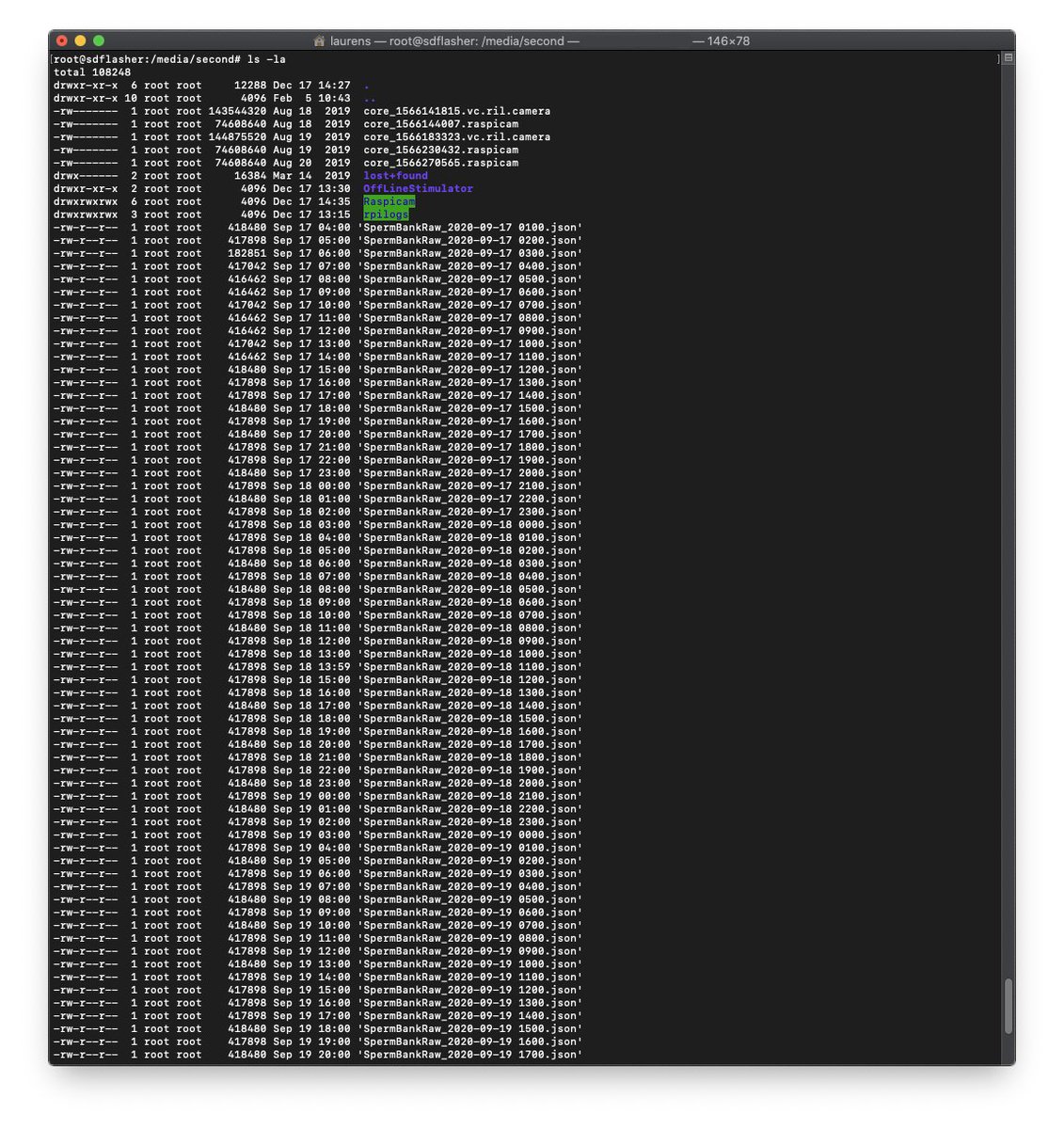
I mean, it looks like it's just counter logging data, but why are the files called SpermBankRaw?!
And do they also have SpermBankWellDone? Asking the important questions here.
And do they also have SpermBankWellDone? Asking the important questions here.

 Read on Twitter
Read on Twitter