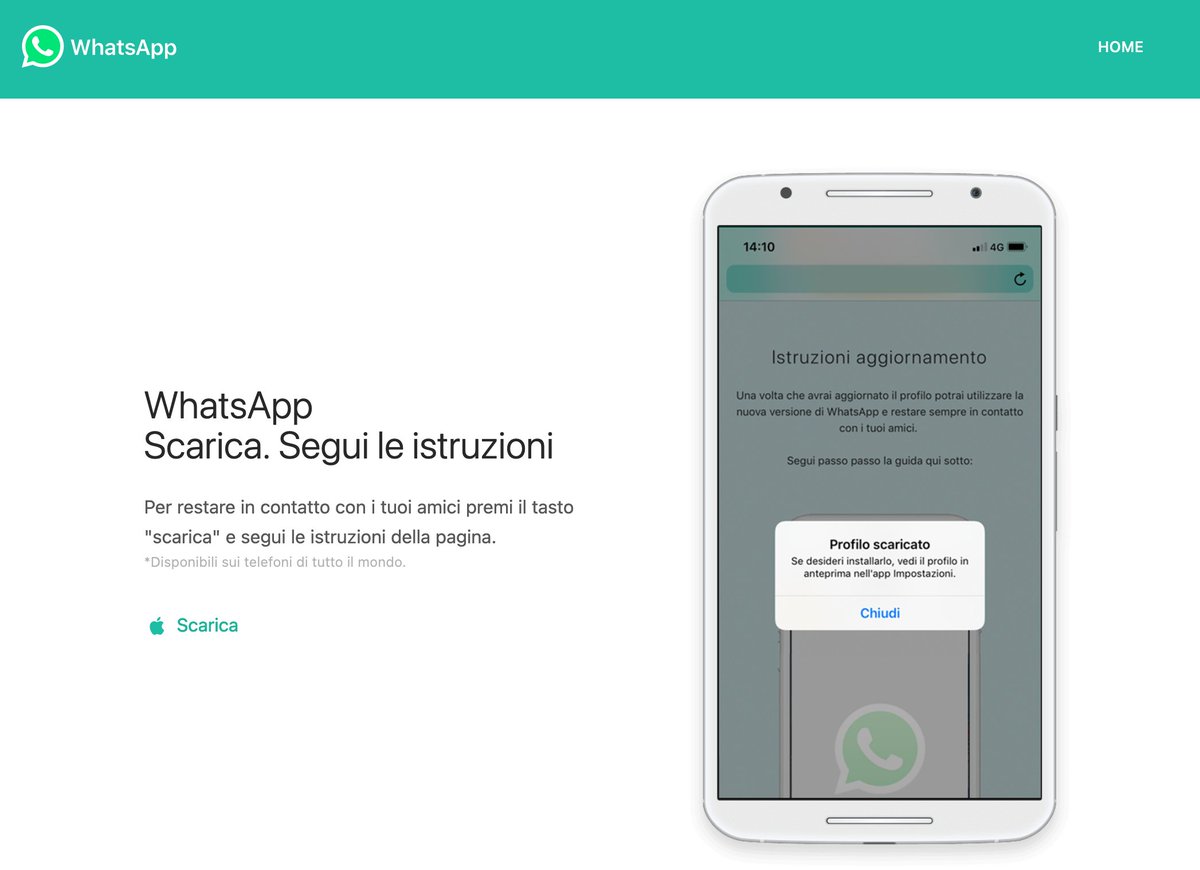
NEW: We found a spy company’s malicious, fake WhatsApp download page.
Technical analyses by Citizen Lab and Motherboard found links between the fake version of WhatsApp and Cy4gate, a provider of surveillance technology based in Rome, Italy. https://www.vice.com/en/article/akdqwa/a-spyware-vendor-seemingly-made-a-fake-whatsapp-to-hack-targets
Technical analyses by Citizen Lab and Motherboard found links between the fake version of WhatsApp and Cy4gate, a provider of surveillance technology based in Rome, Italy. https://www.vice.com/en/article/akdqwa/a-spyware-vendor-seemingly-made-a-fake-whatsapp-to-hack-targets
The company denied that the fake WhatsApp page and others linked servers have anything to do with them. But we found certs signed by the company and a login page that displays the company logo and the logo of their spyware product.

 Read on Twitter
Read on Twitter