Finishing up this session at #enigma2021 is from Trey Herr speaking about "BREAKING TRUST – SHADES OF CRISIS ACROSS AN INSECURE SOFTWARE SUPPLY CHAIN"
[ *cough* #SolarWinds #SolarWindsHack *cough* ]
https://www.usenix.org/conference/enigma2021/presentation/herr
[ *cough* #SolarWinds #SolarWindsHack *cough* ]
https://www.usenix.org/conference/enigma2021/presentation/herr
The software supply chain is huge and reaches everywhere.
In the US and elsewhere there's a lot of COTS (commercial off the shelf) software being used.
We don't build most of the software that we use, from mobile phones to container architechture.
In the US and elsewhere there's a lot of COTS (commercial off the shelf) software being used.
We don't build most of the software that we use, from mobile phones to container architechture.
Our mental models around supply chain (and regulatory architecture) are built around the hardware supply chain
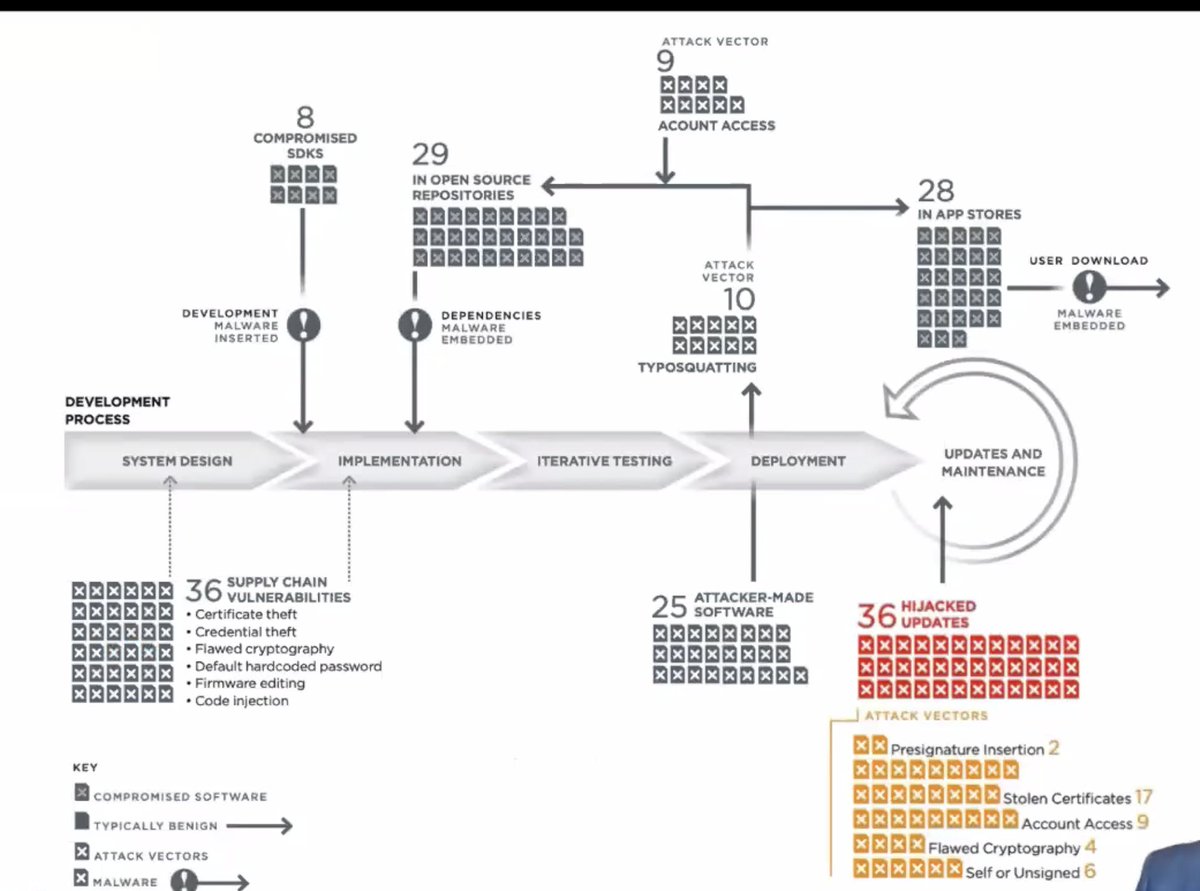
A software supply chain attack is when attackers access and edit software somewhere in the complex supply chain to compromise down the chain.
Also have to look at vulns -- those can easily become attacks!
Also have to look at vulns -- those can easily become attacks!
Disclaimer: this is based on public information, so it probably undercounts certain high-value targets or places which aren't so covered by press.
What we compile and the dependencies we use matter a lot.
There is not going to be one silver bullet.
Updates are a problem; there's an opportunity to push fixes but require a lot of trust
There is not going to be one silver bullet.
Updates are a problem; there's an opportunity to push fixes but require a lot of trust
* Software supply chain attacks have been popular and are going to be more so [*cough* #SolarWinds *cough*]
* They're high-impact -- you can get a lot of targets with one hack
* Used to great effect by state attackers
* They're high-impact -- you can get a lot of targets with one hack
* Used to great effect by state attackers
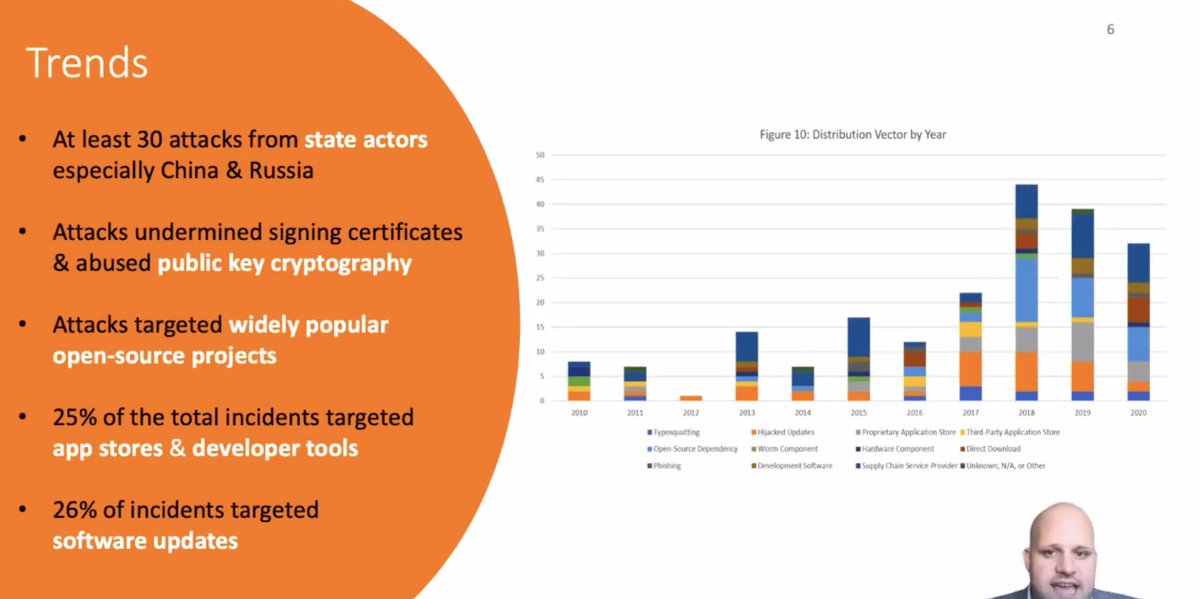
Trends:
* state attacks especially China and Russia
* attacks undermined public-key cryptography (code signing)
* attacks targeted widely-used open-source projects
* 25% of these incidents targeted app stores and developer tools
* 26% of incidents targeted software updates
* state attacks especially China and Russia
* attacks undermined public-key cryptography (code signing)
* attacks targeted widely-used open-source projects
* 25% of these incidents targeted app stores and developer tools
* 26% of incidents targeted software updates
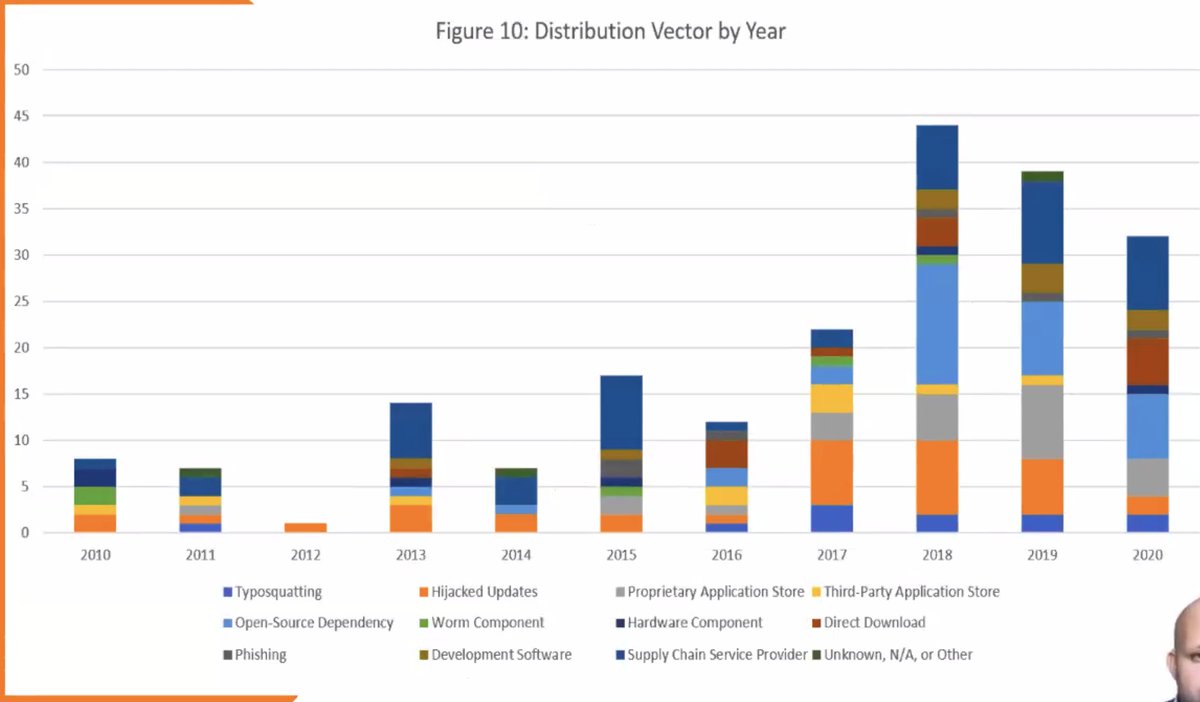
Distribution vector by year -- that orange bar is attacks on software updates. About half that were targeting build infrastructure.
Nearly 1/3 of the state attackers target updates.
Let's talk about #SolarWinds !
* Compromised at least as early as 2019
* Malicious code was carried through dev pipeline and released to the world
* Could compromise 18k+ different companies based on that
* Compromised at least as early as 2019
* Malicious code was carried through dev pipeline and released to the world
* Could compromise 18k+ different companies based on that
Recommendations:
* US government needs to get smartest about assessing risk and creating a risk register and fund improving IT
* the security issues of software supply chains are not new and not going to get better fast
* it's hard to have the baseline level of security
* US government needs to get smartest about assessing risk and creating a risk register and fund improving IT
* the security issues of software supply chains are not new and not going to get better fast
* it's hard to have the baseline level of security
* too much focus on dev, not enough on deploy
* the risk management strategies are too much in PDF, not code
* the risk management strategies are too much in PDF, not code
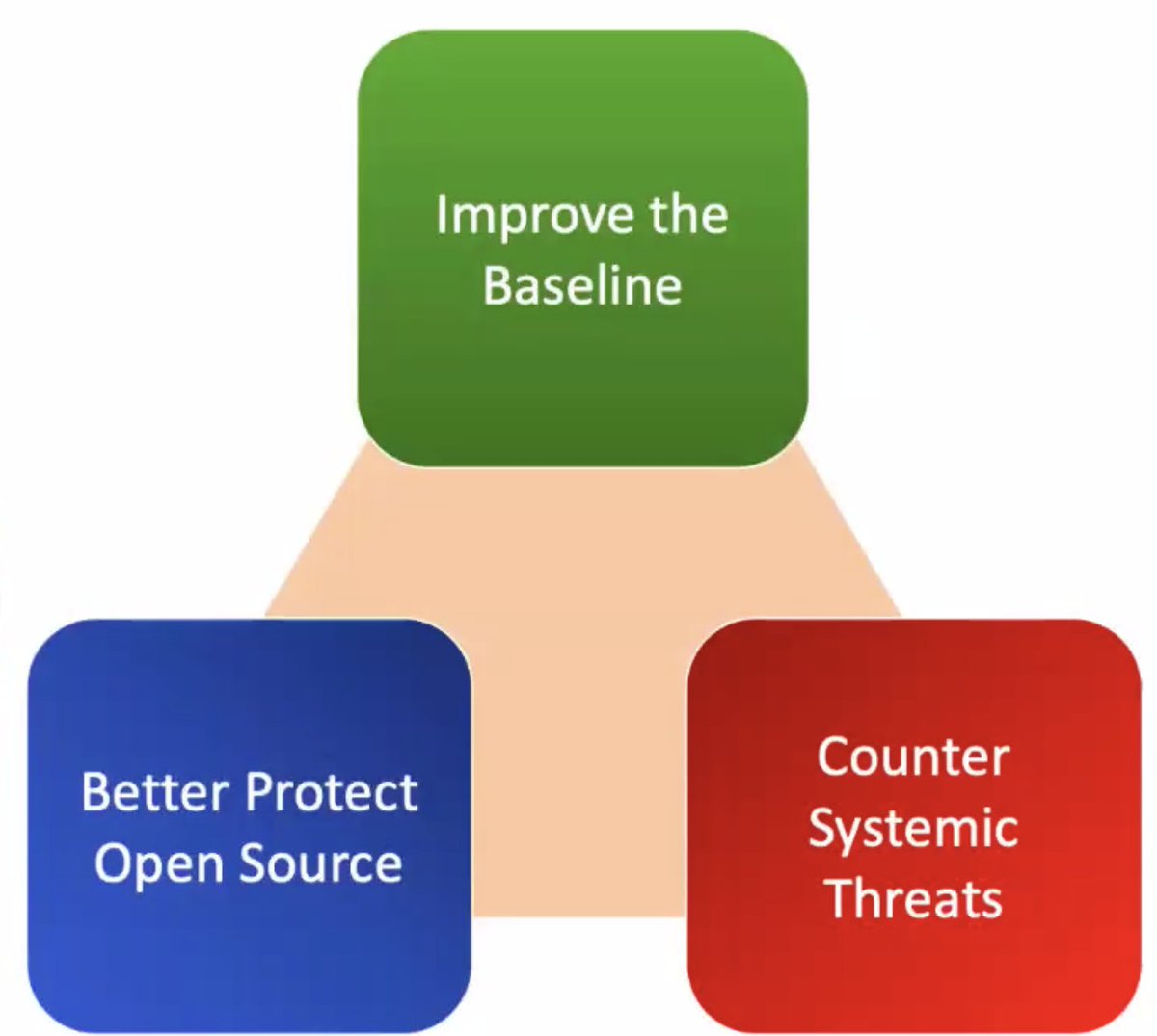
Improve the baseline: make it easier to have good supply chain security
Better protect open source: fund it!
Counter systemic threats: the US can't do this alone and should be working with allies on this
Support strong cryptography and tools!
Better protect open source: fund it!
Counter systemic threats: the US can't do this alone and should be working with allies on this
Support strong cryptography and tools!
[end of talk]
Report from @CyberStatecraft here: https://www.atlanticcouncil.org/in-depth-research-reports/report/breaking-trust-shades-of-crisis-across-an-insecure-software-supply-chain/
Report from @CyberStatecraft here: https://www.atlanticcouncil.org/in-depth-research-reports/report/breaking-trust-shades-of-crisis-across-an-insecure-software-supply-chain/

 Read on Twitter
Read on Twitter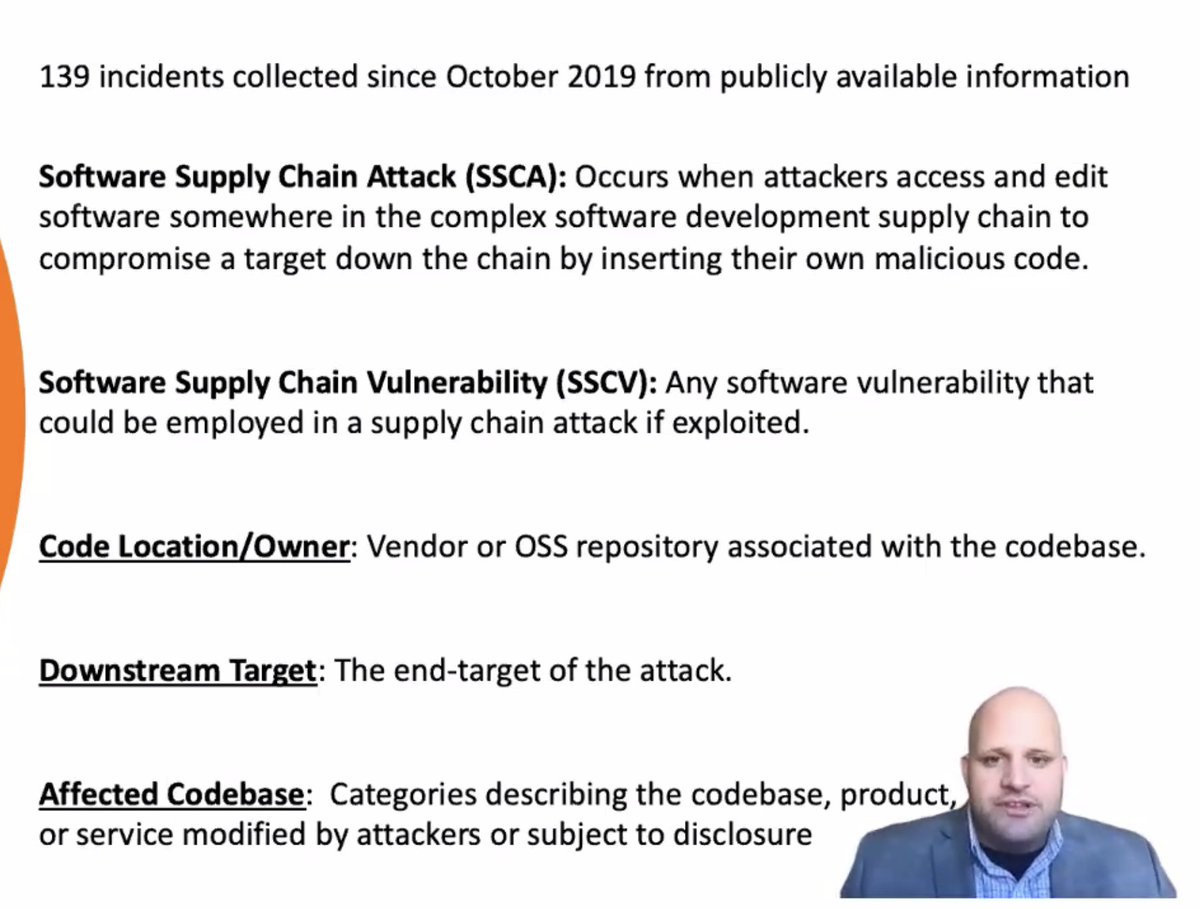
![[yes this is hard to read. sorry]Software supply chain attacks land all through the chain. [yes this is hard to read. sorry]Software supply chain attacks land all through the chain.](https://pbs.twimg.com/media/EtPcWLKVcAABzjn.jpg)
![* Software supply chain attacks have been popular and are going to be more so [*cough* #SolarWinds *cough*]* They're high-impact -- you can get a lot of targets with one hack* Used to great effect by state attackers * Software supply chain attacks have been popular and are going to be more so [*cough* #SolarWinds *cough*]* They're high-impact -- you can get a lot of targets with one hack* Used to great effect by state attackers](https://pbs.twimg.com/media/EtPc13dUcAAOjj0.jpg)