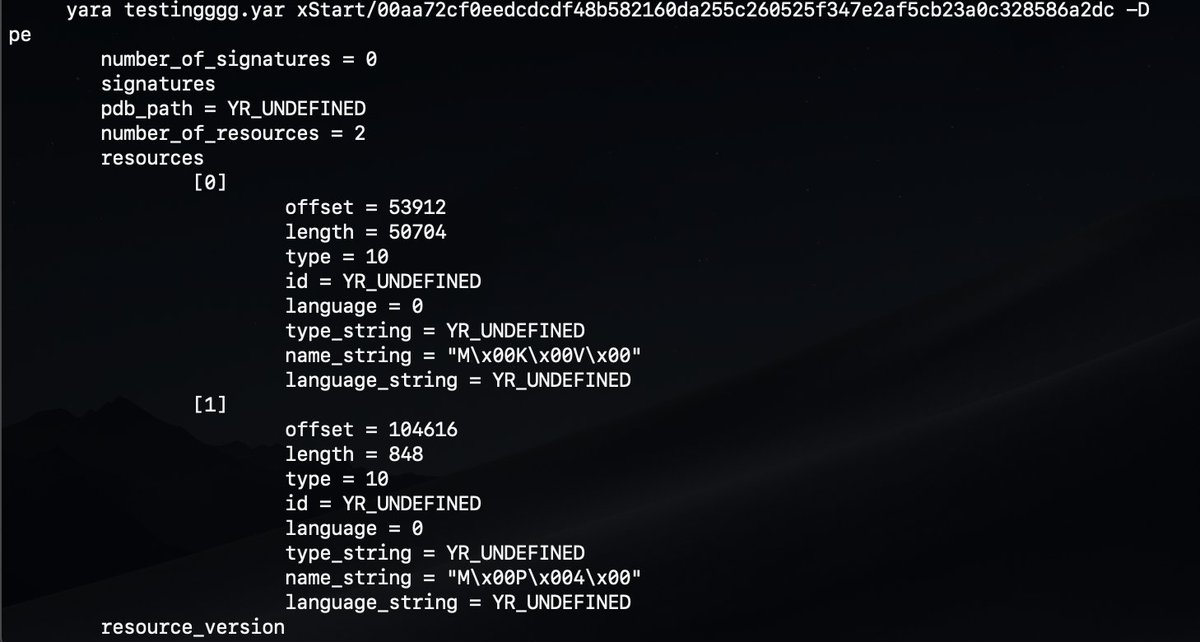
Late night (or early morning?) #dailyyara thread on PE resources and yara, inspired by @BitsOfBinary recent SANS talk: https://github.com/PwCUK-CTO/SANSCTISummit2021-xStart/blob/main/yara/xstart.yar
Just like other aspects of PEs, attackers leave fingerprints or tool marks on the resource section. The xStart family contained resources named after media file types (MKV, MP4) seen via yara's -D flag
An older example, called Lucifer, used some odd type strings to bundle additional payloads and tooling https://www.netscout.com/blog/asert/lucifers-spawn
So we have name strings and type strings where actors leave their dirty fingerprints - both are optional fields in the PE. I think we can develop something similar to @stvemillertime 's engines but for resources! https://twitter.com/stvemillertime/status/1352336955346874368
Example loop in condition:
for any i in (0.. pe.number_of_resources - 1): (
pe.resources[i].name_string == "S\\x00H\\x00E\\x00L\\x00L\\x00"
or pe.resources[i].type_string contains "S\\x00H\\x00E\\x00L\\x00L\\x00"
)
thanks @ConnorSecurity ;)
for any i in (0.. pe.number_of_resources - 1): (
pe.resources[i].name_string == "S\\x00H\\x00E\\x00L\\x00L\\x00"
or pe.resources[i].type_string contains "S\\x00H\\x00E\\x00L\\x00L\\x00"
)
thanks @ConnorSecurity ;)
We can use == or contains, depending on how much data you’d like to pull back. Try some of the strings from this tweet! I don’t have the viz to verify that all/none of them have results. But some interesting strings with families:
REGISTRY (SmokeLoader, Shamoon)
BIN (DTrack)
EXE (Mamba ransomware, KGH_SPY)
SHELL (Lucifer, LoadMoney)
ROOTKIT (Turkojan)
BIN (DTrack)
EXE (Mamba ransomware, KGH_SPY)
SHELL (Lucifer, LoadMoney)
ROOTKIT (Turkojan)
of course, PE other resources contain other fun for pivots/signatures like embedded icons (mimikatz) or executables, but this was a fun, very loose set of queries.

 Read on Twitter
Read on Twitter