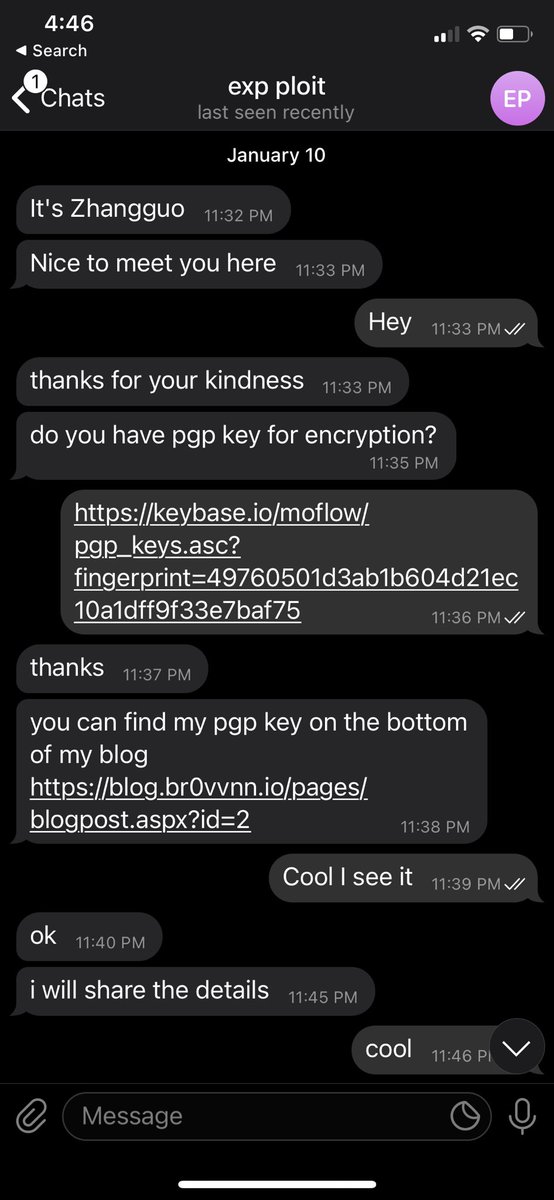
WARNING! I can confirm this is true and I got hit by @z0x55g who sent me a Windows kernel PoC trigger. The vulnerability was real and complex to trigger. Fortunately I only ran it in VM.. in the end the VMDK I was using was actually corrupted and non-bootable, so it self-imploded https://twitter.com/ShaneHuntley/status/1353856344655204352
Here’s their first contact.. Twitter has deleted the acct but they just said “hi” and “hello” to prompt the first two messages and then asked if I can do Windows kernel exploitation
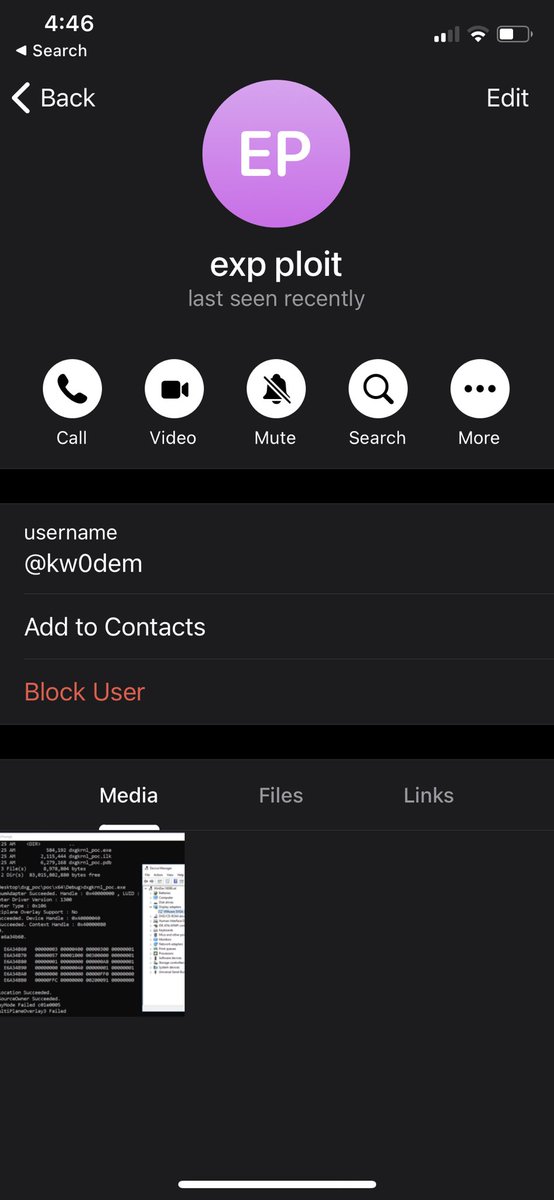
Hi @ShaneHuntley see my thread, z0x55g targeted me and is currently still active on Telegram under user kw0dem. I can provide the .suo sample if it will help

 Read on Twitter
Read on Twitter