For your lunchtime* long read this afternoon, I'd like to point you to some work I'm quite proud of that was published today.
SophosLabs found what we now suspect may be an APT Android malware targeting people with a connection to Pakistan.
*in N America https://news.sophos.com/en-us/2021/01/12/new-android-spyware-targets-users-in-pakistan/
SophosLabs found what we now suspect may be an APT Android malware targeting people with a connection to Pakistan.
*in N America https://news.sophos.com/en-us/2021/01/12/new-android-spyware-targets-users-in-pakistan/
So I'm sure you're thinking like, hey, it's Pakistan, why should I care?
Let's get to the core of the problem with this question:
- nobody deserves to be hit with very intrusive surveillance
- Pakistan is a nuclear-armed nation in tense relationships with its neighbors
Let's get to the core of the problem with this question:
- nobody deserves to be hit with very intrusive surveillance
- Pakistan is a nuclear-armed nation in tense relationships with its neighbors
Here's the other problem with minimizing this because "this was just an attack on [not my country]"
The malware didn't actually care where you were located; All it wanted was every last piece of sensitive or personal data from the infected phone.
I ran it from the US.
The malware didn't actually care where you were located; All it wanted was every last piece of sensitive or personal data from the infected phone.
I ran it from the US.
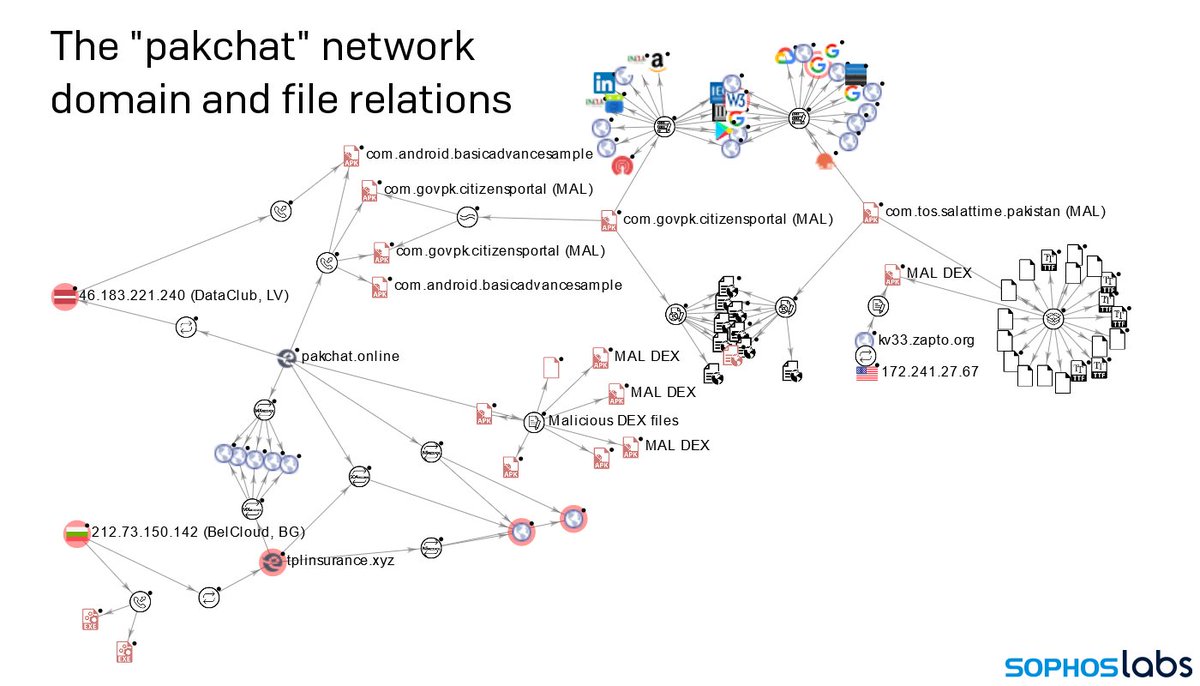
Then there was the way the malware and its associated websites were thematically connected.
One of the malicious apps was called Pakistan Chat. The C2 for that malware was pakchat[.]online.
One was a fake version of "TPL Insurance." C2: tplinsurance[.]xyz
Not a coincidence.
One of the malicious apps was called Pakistan Chat. The C2 for that malware was pakchat[.]online.
One was a fake version of "TPL Insurance." C2: tplinsurance[.]xyz
Not a coincidence.
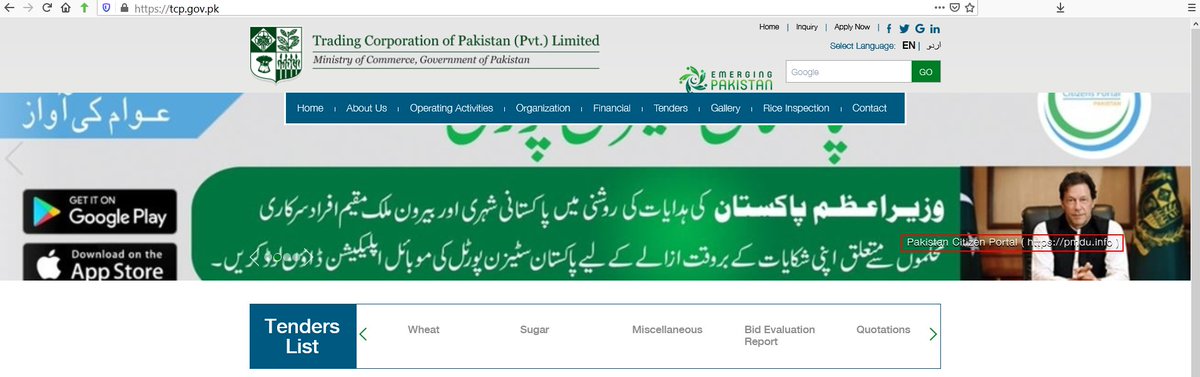
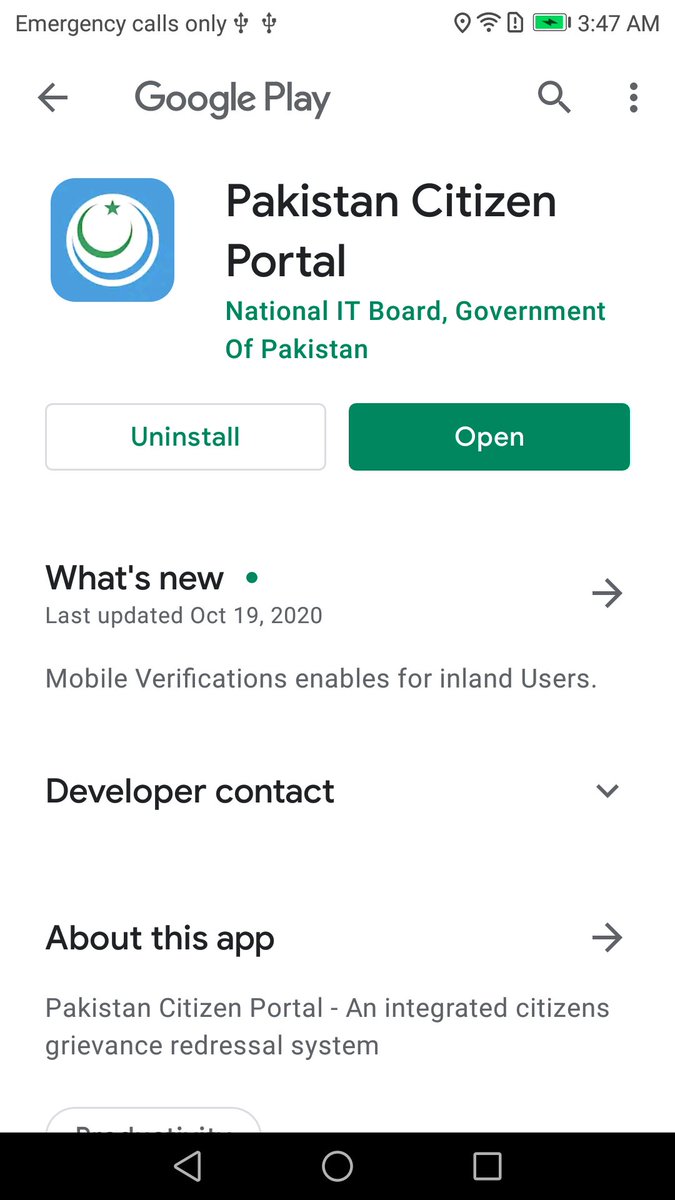
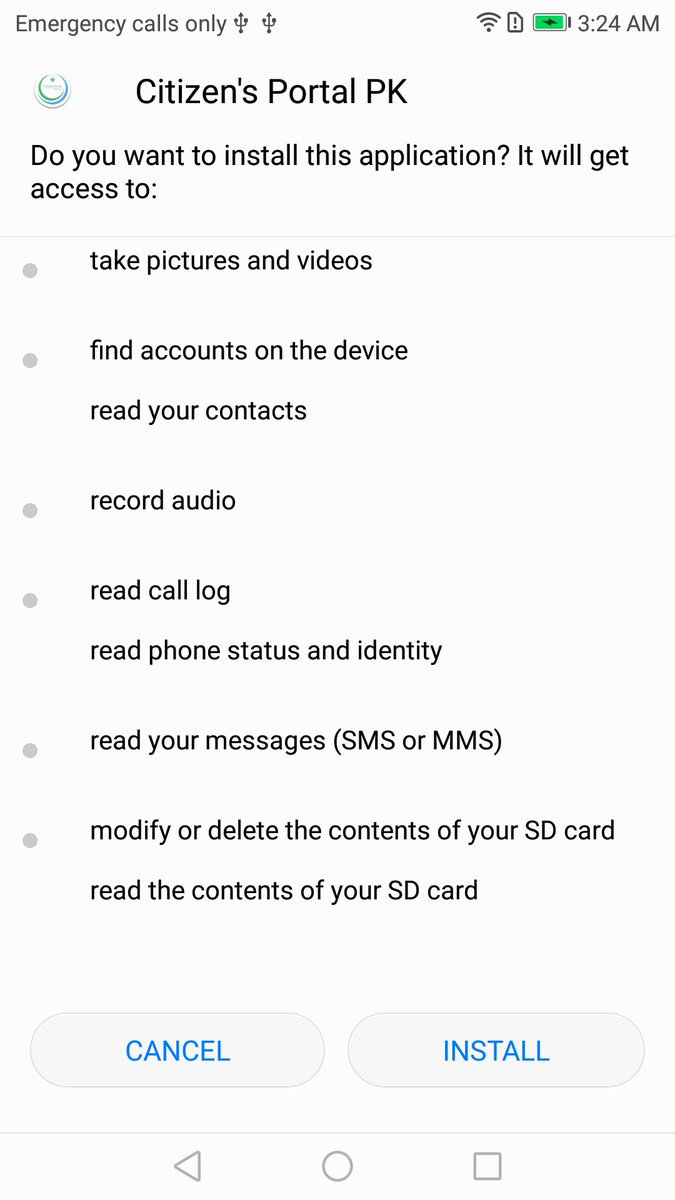
The most OPSEC effort seems to have gone into the app for the Pakistan Citizen Portal. That's the Pakistani government's (legitimate, official) "file a complaint" app. The real version is on Google Play (shown here for comparison)
Because it's a semi-official government app, the Pakistani Citizen Portal requires you to provide things like National ID numbers and other identifying information. The malicious version steals all that, along with anything else it can scrape up.
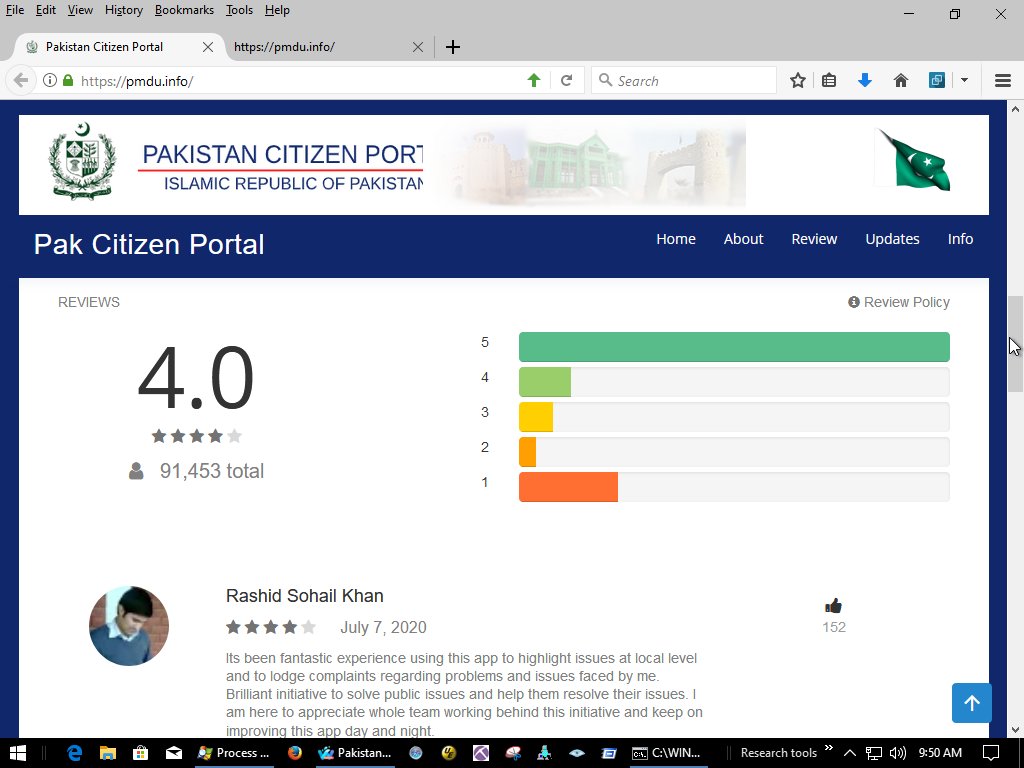
Worse, we found a website hosting a download of the malicious Pakistan Citizen Portal app at pmdu[.]info. The page is decorated to look like the Google Play store page, but only produces the malicious version of the app when you click either the Google Play or Download button.
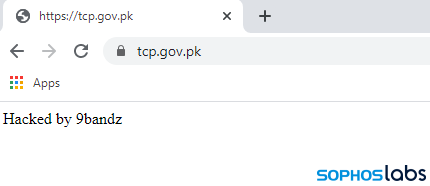
For a while we couldn't figure out how people were finding the malicious domain. We suspected someone might be spamming SMS messages to people in Pakistan. But then we also found that someone hacked and modified an official Pakistani government webpage to link to it.
Over the past weekend, the official government webpage that was linking to the malware was defaced and then went offline. The defacer apparently advertised in December that they are "selling government web shells with full access" to the files on the webserver.
So this has been a quite elaborate attack, in that the attackers:
- set up a fake website
- made an effort to make it look real
- hacked and very subtly modified a real Pakistani government website to link to the fake website
- registered domains thematically connected to apps
- set up a fake website
- made an effort to make it look real
- hacked and very subtly modified a real Pakistani government website to link to the fake website
- registered domains thematically connected to apps
And now a lot of the trail leading back to the attackers is going cold, having been burned by our reporting and, possibly, by our repeated attempts to alert the Pakistani authorities to the problem.
There's a deeper problem that this highlights. https://news.sophos.com/en-us/2021/01/12/new-android-spyware-targets-users-in-pakistan/
There's a deeper problem that this highlights. https://news.sophos.com/en-us/2021/01/12/new-android-spyware-targets-users-in-pakistan/
Because the malware looks nothing like the more typical Android spyware apps we've researched in the past, I would welcome outside groups who investigate nation-state espionage attacks to take a look at the IoCs and reach out to me if you know anything. https://github.com/sophoslabs/IoCs/blob/master/Android-pakchat.csv
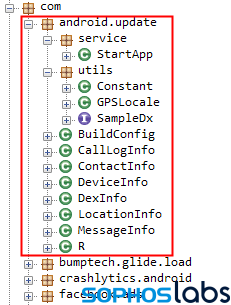
The fact the attackers went to great lengths to hide what they were doing behind a plausible facade, even using the names of legitimate Android code library classes to camouflage their malicious embedded code, speaks to the level of sophistication of the attackers. Sketchy.
One of the modified apps is a muslim prayer clock, which can tell you the correct time to pray if you're observant. This app, like the others, wanted to know everyone you talked to, messaged with, and could turn on the mic and camera on demand - targeted at a specific religion.

 Read on Twitter
Read on Twitter![Here's the other problem with minimizing this because "this was just an attack on [not my country]"The malware didn't actually care where you were located; All it wanted was every last piece of sensitive or personal data from the infected phone.I ran it from the US. Here's the other problem with minimizing this because "this was just an attack on [not my country]"The malware didn't actually care where you were located; All it wanted was every last piece of sensitive or personal data from the infected phone.I ran it from the US.](https://pbs.twimg.com/media/ErjjIh_XMAAW5XS.png)
![Then there was the way the malware and its associated websites were thematically connected. One of the malicious apps was called Pakistan Chat. The C2 for that malware was pakchat[.]online. One was a fake version of "TPL Insurance." C2: tplinsurance[.]xyzNot a coincidence. Then there was the way the malware and its associated websites were thematically connected. One of the malicious apps was called Pakistan Chat. The C2 for that malware was pakchat[.]online. One was a fake version of "TPL Insurance." C2: tplinsurance[.]xyzNot a coincidence.](https://pbs.twimg.com/media/ErjloSYWMAwgaG-.png)
![Worse, we found a website hosting a download of the malicious Pakistan Citizen Portal app at pmdu[.]info. The page is decorated to look like the Google Play store page, but only produces the malicious version of the app when you click either the Google Play or Download button. Worse, we found a website hosting a download of the malicious Pakistan Citizen Portal app at pmdu[.]info. The page is decorated to look like the Google Play store page, but only produces the malicious version of the app when you click either the Google Play or Download button.](https://pbs.twimg.com/media/ErjnQHKXIAAxzg7.jpg)