Let's talk about attribution. In a few weeks, we've gone from discovery of #SUNBURST and the #SolarWindsHack to public attribution of Russia. But there is currently scant public evidence for this claim. #thread 1/
Some researchers have pointed to #apt41 / #Barium as an alternate actor. APT41, tracked by @RecordedFuture as #Winnti Unbrella Group, is an actor who has previously used several of the techniques/tools seen in #SUNBURST including supply chain poisoning https://twitter.com/juanandres_gs/status/1341175012540223488?s=20 2/
We looked at open source info on #UNC2452 to find what other insight they have. @jfslowik ( @DomainTools) wrote a fantastic piece uncovering CNAME links to the second-stage C2. https://www.domaintools.com/resources/blog/unraveling-network-infrastructure-linked-to-the-solarwinds-hack 3/
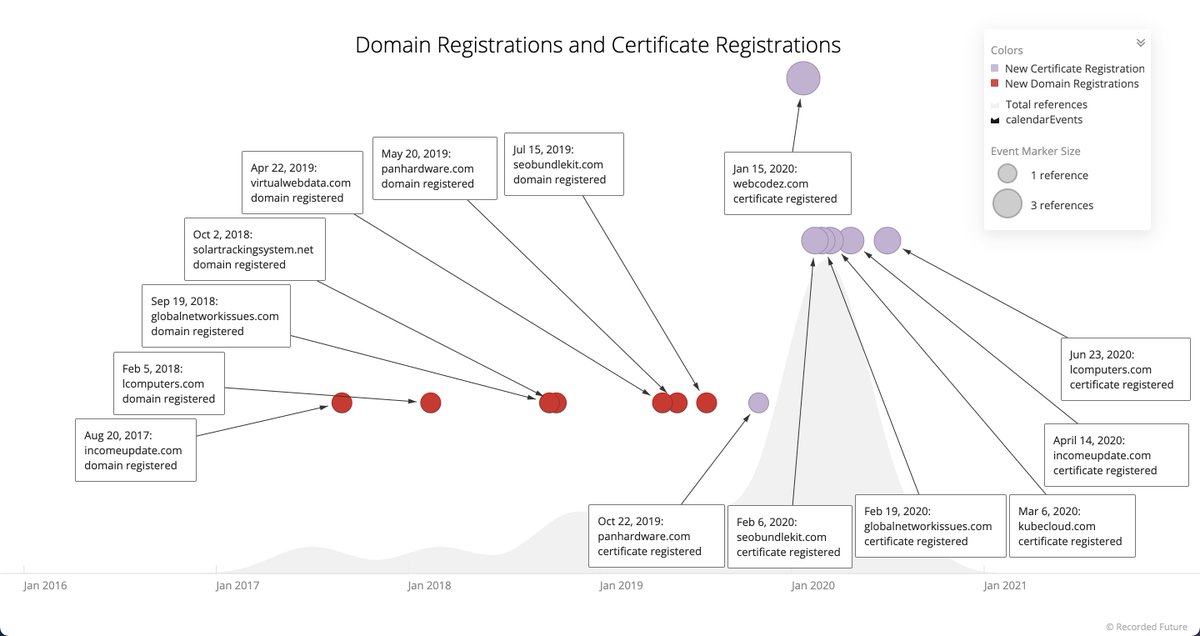
Here's a @RecordedFuture timeline showing C2 linked domains registrations and certification registrations, suggesting domain registration activity as early as August 2017, far earlier than discussed. This may indicate "aging" of domains, but this needs to be further explored. 4/
Historical analysis can supplement and support evidence towards attribution, as well as show techniques defenders should map for coverage and gap identification. We attempted technique analysis using MITRE ATT&CK on #UNC2452, but ran into several challenges, which we wrote up 5/
Would love to hear others thoughts about #attribution in #SolarWindsHack or the opinions stated here. Undoubtedly, USG IC has more information than they are disclosing here, but improving defenses includes a serious look at how our processes for identifying actors happens. /end
Link to blog and white paper: https://www.recordedfuture.com/solarwinds-attribution/

 Read on Twitter
Read on Twitter