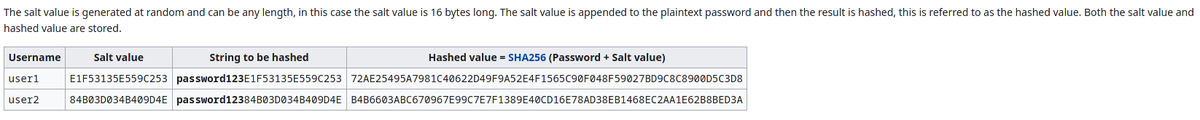
Hashing Passwords - Security 101.
The purpose of a password is to prevent anybody but the user logging in to their account.
If they were stored in plain-text in a database, then the admin would be able to see everybody's passwords.
MANY problems with this:
1. ...
The purpose of a password is to prevent anybody but the user logging in to their account.
If they were stored in plain-text in a database, then the admin would be able to see everybody's passwords.
MANY problems with this:
1. ...
1. The admin may:
- sell the passwords
- get fired and decide to cause mayhem
- log in a user's account on ANOTHER service, if the user has reused the password (way too common!)
2. If a hacker manages to get a hold of your database - all your passwords are exposed.
Solution...
- sell the passwords
- get fired and decide to cause mayhem
- log in a user's account on ANOTHER service, if the user has reused the password (way too common!)
2. If a hacker manages to get a hold of your database - all your passwords are exposed.
Solution...
The Solution - Hashing.
Hashing a one way conversion of data.
This means if I hash the string "password" the output hash can not be used to derive the original string (as opposed to encryption, which is two-way but requires keys)
Hashing a one way conversion of data.
This means if I hash the string "password" the output hash can not be used to derive the original string (as opposed to encryption, which is two-way but requires keys)
When a user logs in the password he enters is hashed as well and the result is compared to the original hash.
The key is - we know whether the password used is correct without knowing what it actually is!
The key is - we know whether the password used is correct without knowing what it actually is!
So hashing passwords means even if one has access to your user database, he won't learn all users' passwords.
But attackers know some passwords are very common - 1234, qwerty, password, password1...
They create "Rainbow Tables" full of common passwords' hashes.
But attackers know some passwords are very common - 1234, qwerty, password, password1...
They create "Rainbow Tables" full of common passwords' hashes.

 Read on Twitter
Read on Twitter