This graphic taken from the U.S. military Joint Publication 3-12 Cyberspace Operations demonstrates how current doctrine includes cyberspace attack for DEFENSIVE purposes. DCO-RA, specifically. Also included is the language used to describe DCO-RA.
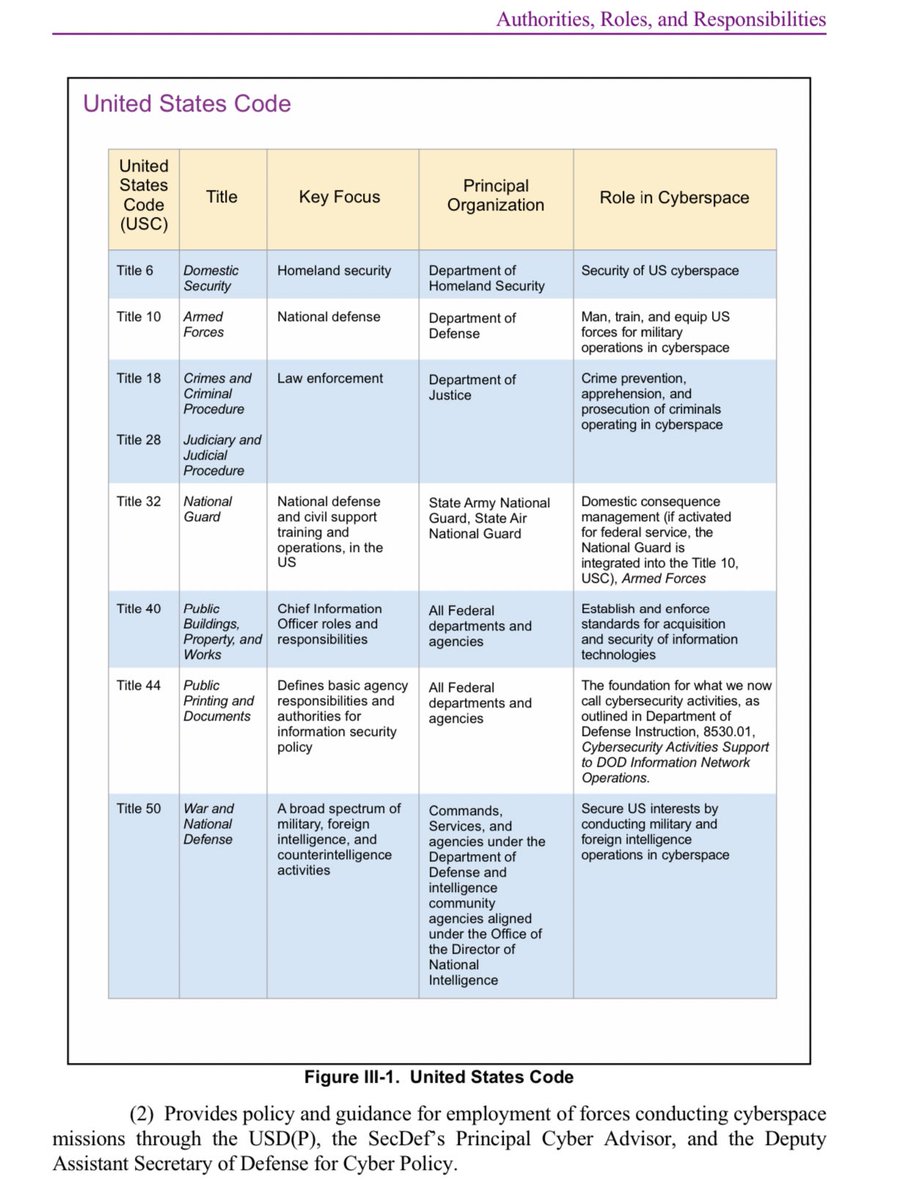
This is a nice chart aligning authorities, roles, and responsibilities. I’m sure some of this is new to you, or a surprise. There’s a reason why lawyers get paid.
I love this portion discussing attribution. I especially appreciate the mention that attribution isn’t actually necessary for self-defense, which is something people commonly misrepresent in discussions about defensive actions.
This is key. US DoD understands the challenges in categorizing activity in cyberspace. They opt for a generic “malicious cyberspace activity” over “it’s all an attack” language. This is smart, and I’m glad they’re doing it even if the rest of industry and media struggle
This is how they describe different layers of cyberspace and how cyberspace attack is deliberately described.

 Read on Twitter
Read on Twitter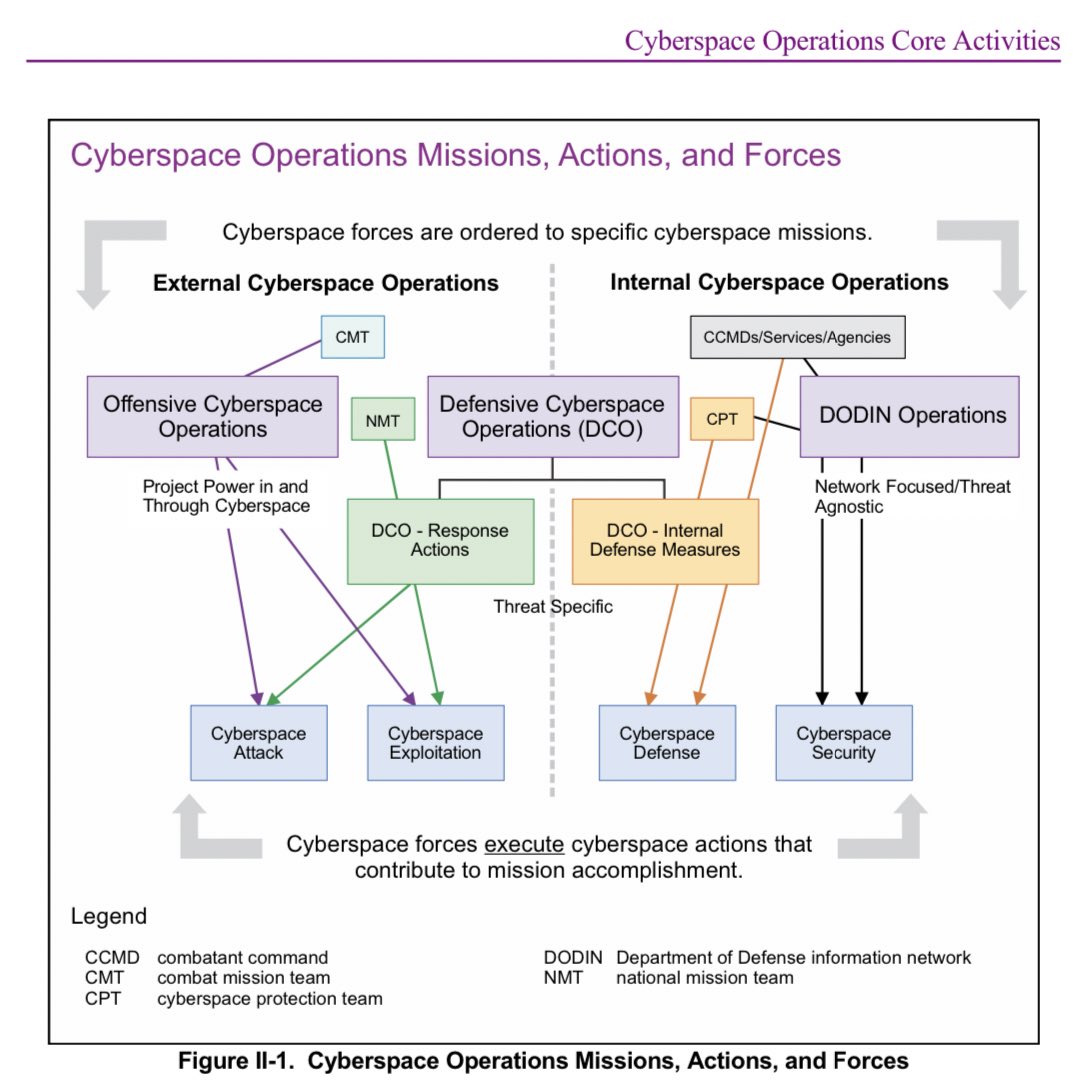





 .
.



