Dangerous misunderstanding spreading that @Cellebrite_UFED can 'crack' & intercept @signalapp.
This is FALSE.
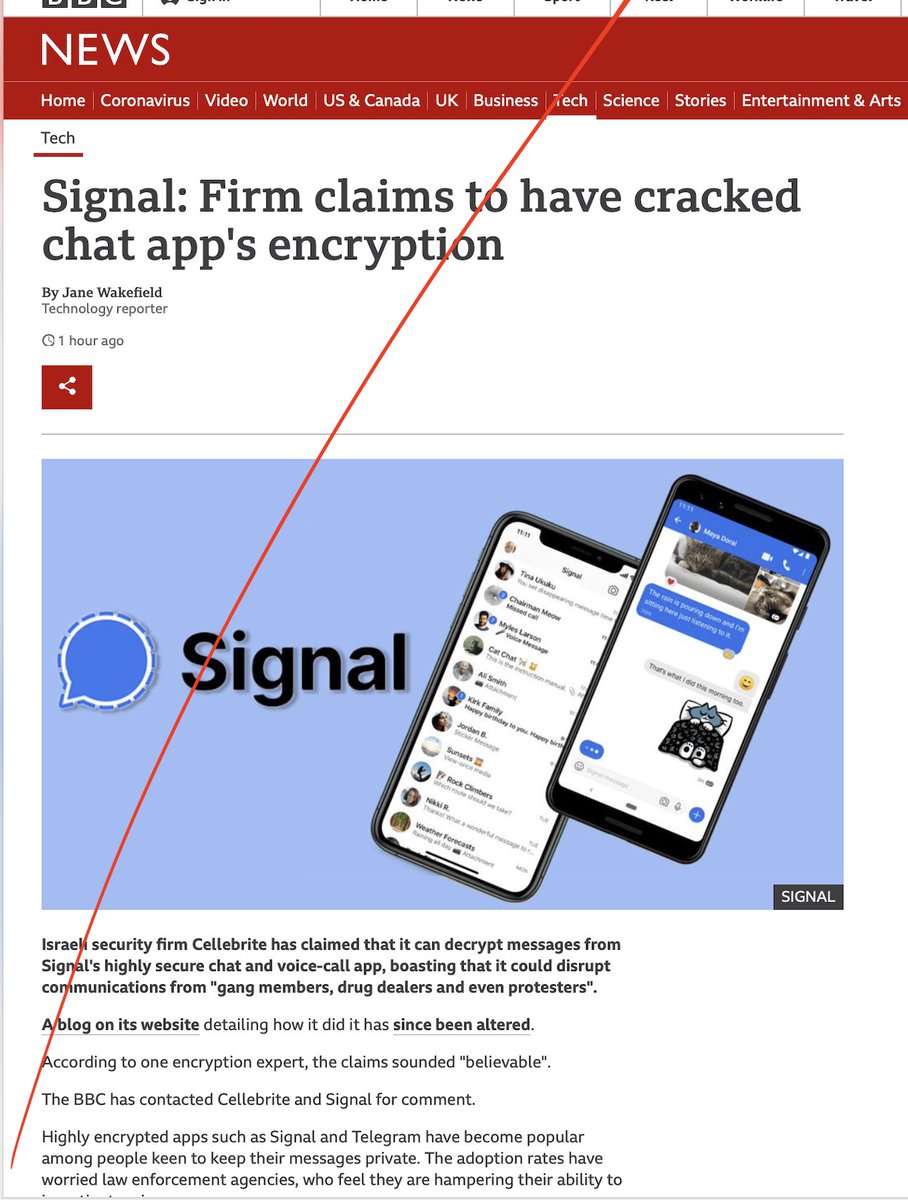
Modest reality: Cellebrite claimed to extract the Signal chat database from an unlocked Android in their possession.
Please RT. cc @BBCNews @janewakefield THREAD 1/
This is FALSE.
Modest reality: Cellebrite claimed to extract the Signal chat database from an unlocked Android in their possession.
Please RT. cc @BBCNews @janewakefield THREAD 1/
2/ Why DANGEROUS? This misinformation is nudging security behaviors *away* from evidence-backed practices that took years to teach.
My inbox = filled with w/ worried journalists, activists & politicians trying to decide if they must delete @signalapp immediately

 .
.
My inbox = filled with w/ worried journalists, activists & politicians trying to decide if they must delete @signalapp immediately


 .
.
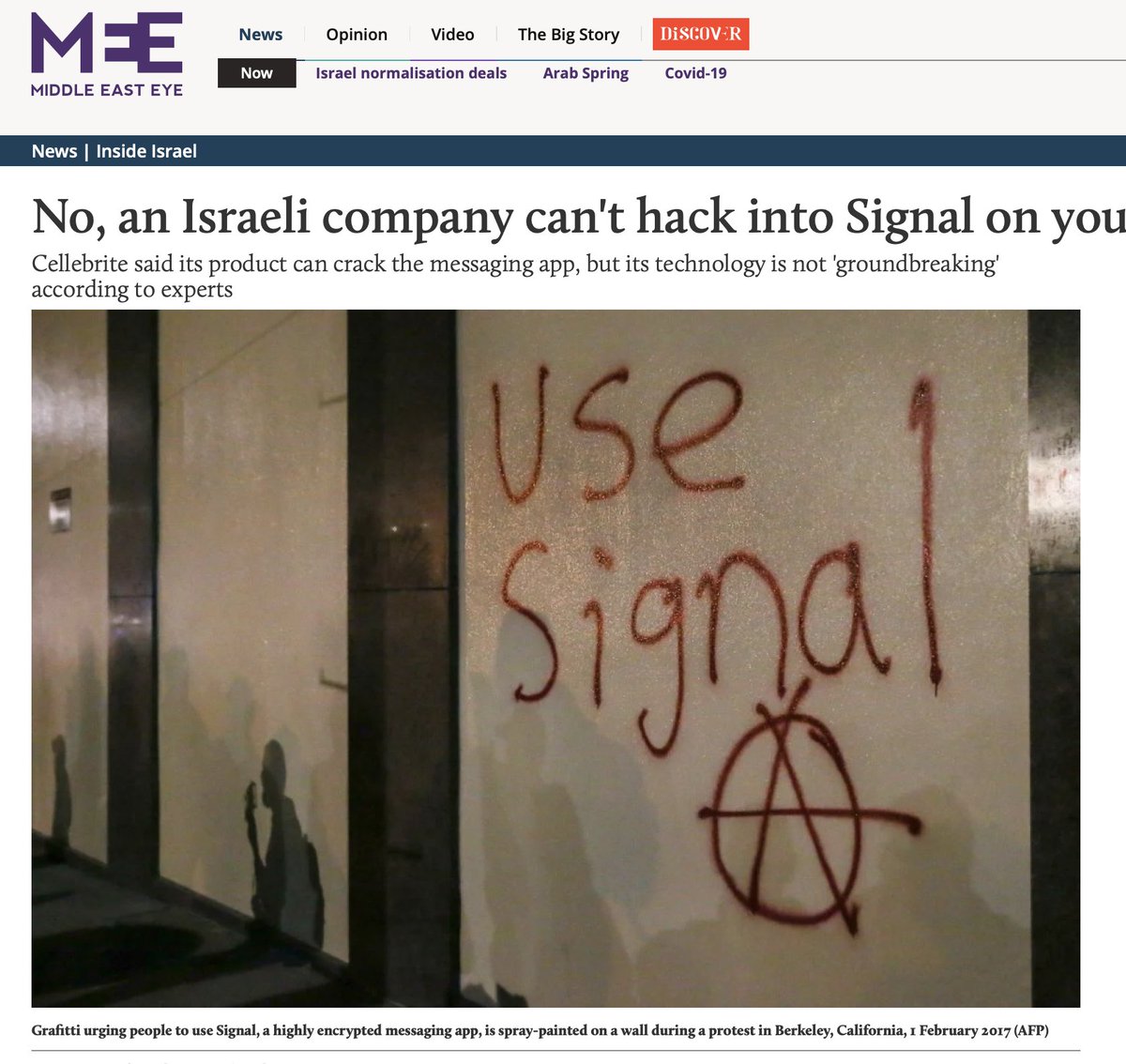
3/ Quick search would have revealed that this misleading claim has been debunked for ~ a week. Even whole stories stating this (random ex. pictured). Or, read @signalapp's lead @moxie's response. https://twitter.com/moxie/status/1337434126186553345
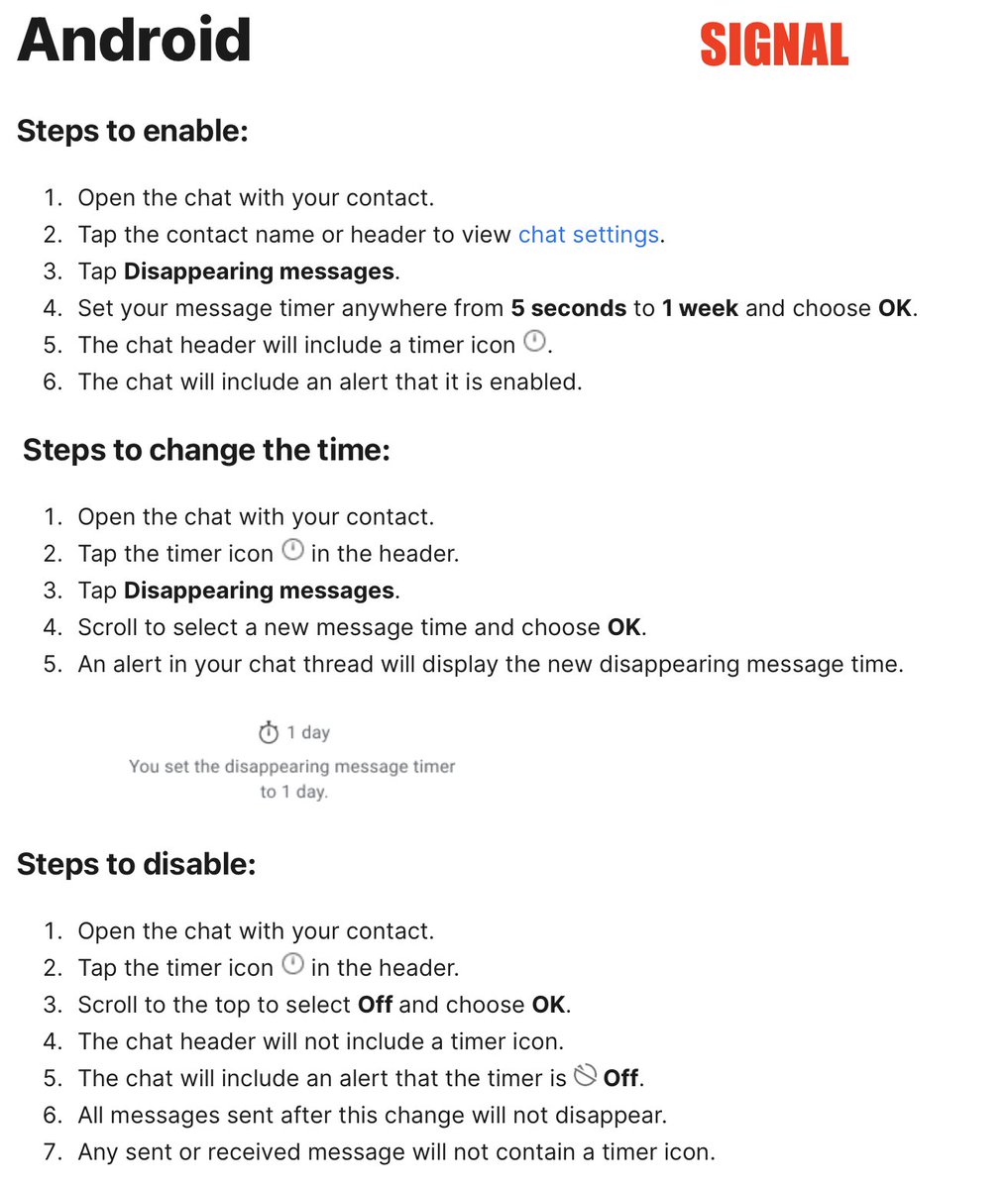
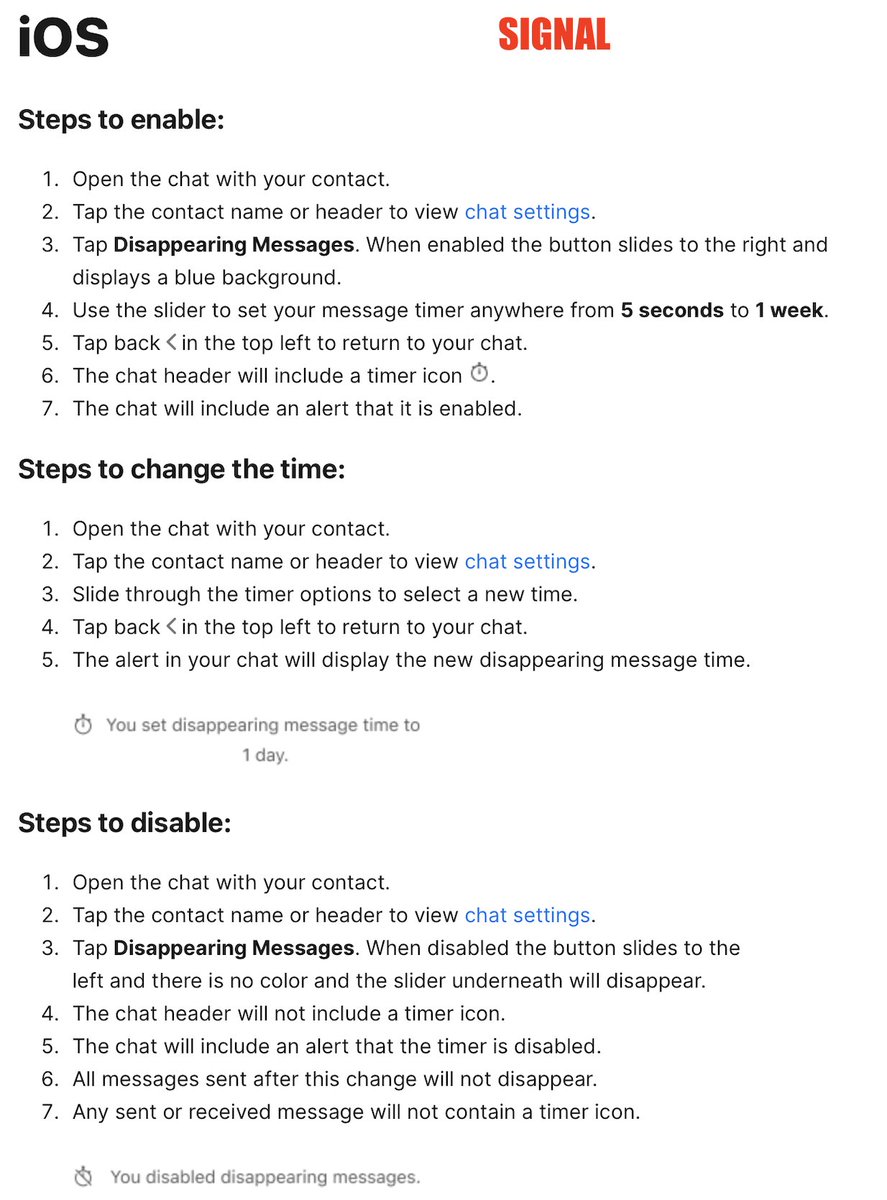
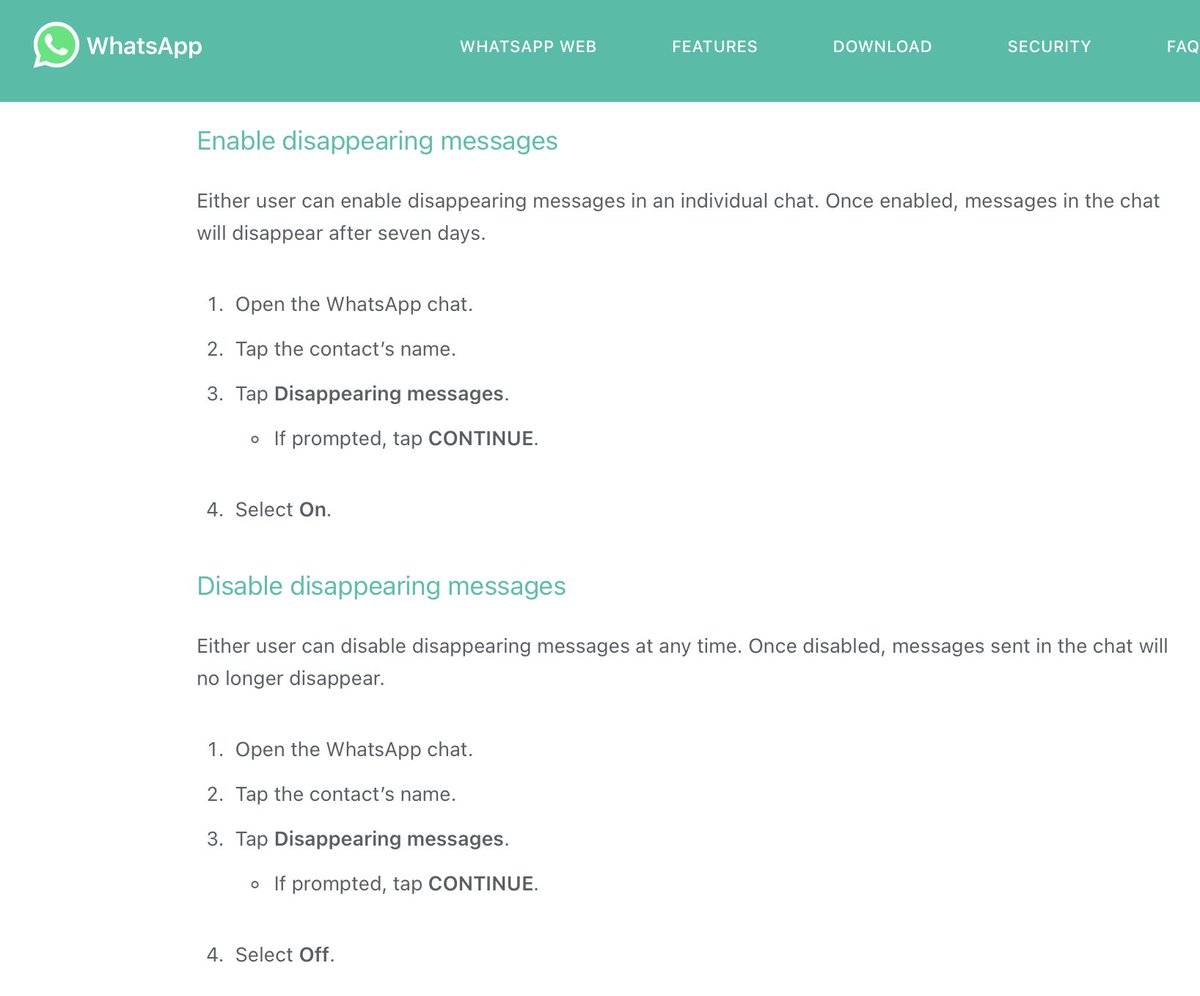
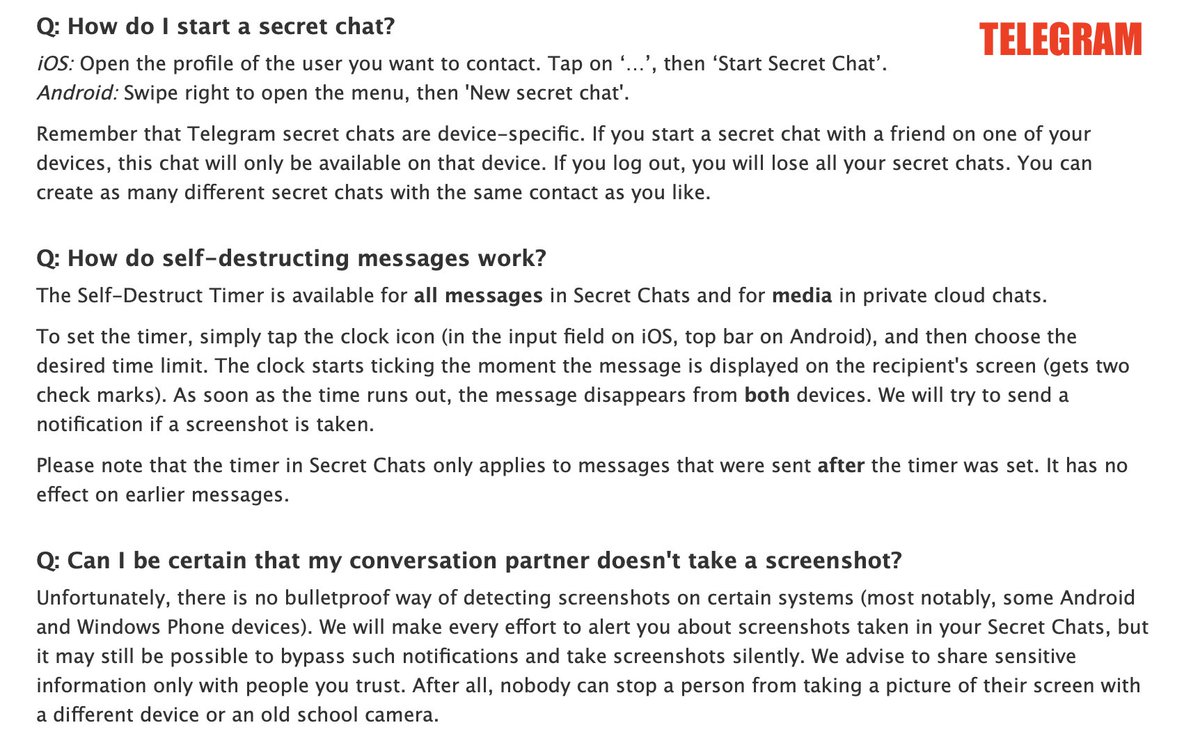
4/ ACTION: USE DISAPPEARING MESSAGES to protect against someone taking your phone & reading your chats. Here are directions for @signalapp @WhatsApp& @telegram
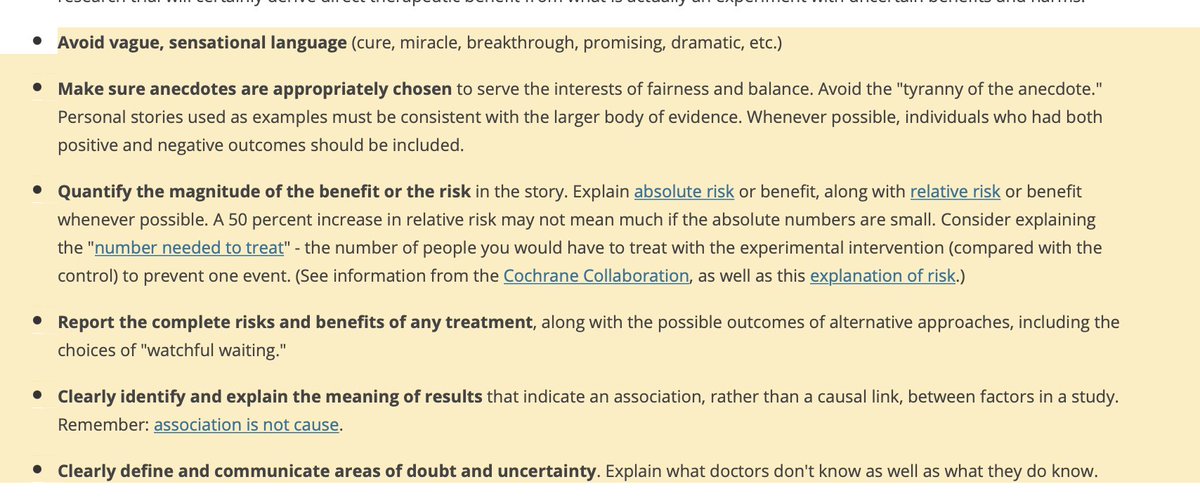
5/ BIG PICTURE: Security journalism, esp. about personal security practices, looks a lot like health journalism & has similar real-life stakes.
Adapting standards e.g. from the Assn. of Health Care Journalists @AHCJ would be a good way forward.
https://healthjournalism.org/principles
Adapting standards e.g. from the Assn. of Health Care Journalists @AHCJ would be a good way forward.
https://healthjournalism.org/principles

 Read on Twitter
Read on Twitter