Wow, a 49 min master class on vishing (phone attacking) by @navalny himself to an FSB officer involved in his own attempted nerve agent murder. Excellent work by @bellingcat.
I’ll break down the pretext and exact stand out vishing moments in this thread. https://www.bellingcat.com/news/uk-and-europe/2020/12/21/if-it-hadnt-been-for-the-prompt-work-of-the-medics-fsb-officer-inadvertently-confesses-murder-plot-to-navalny/
I’ll break down the pretext and exact stand out vishing moments in this thread. https://www.bellingcat.com/news/uk-and-europe/2020/12/21/if-it-hadnt-been-for-the-prompt-work-of-the-medics-fsb-officer-inadvertently-confesses-murder-plot-to-navalny/
Let’s start with timing, 6:30 am Moscow time. Timing is essential in setting the stage for a time-boxed (urgent) pretext. This encourages target to respond quicker. We see @navalny reinforce this time-box with “let’s just say I would not call at 7 am if this was not urgent”.
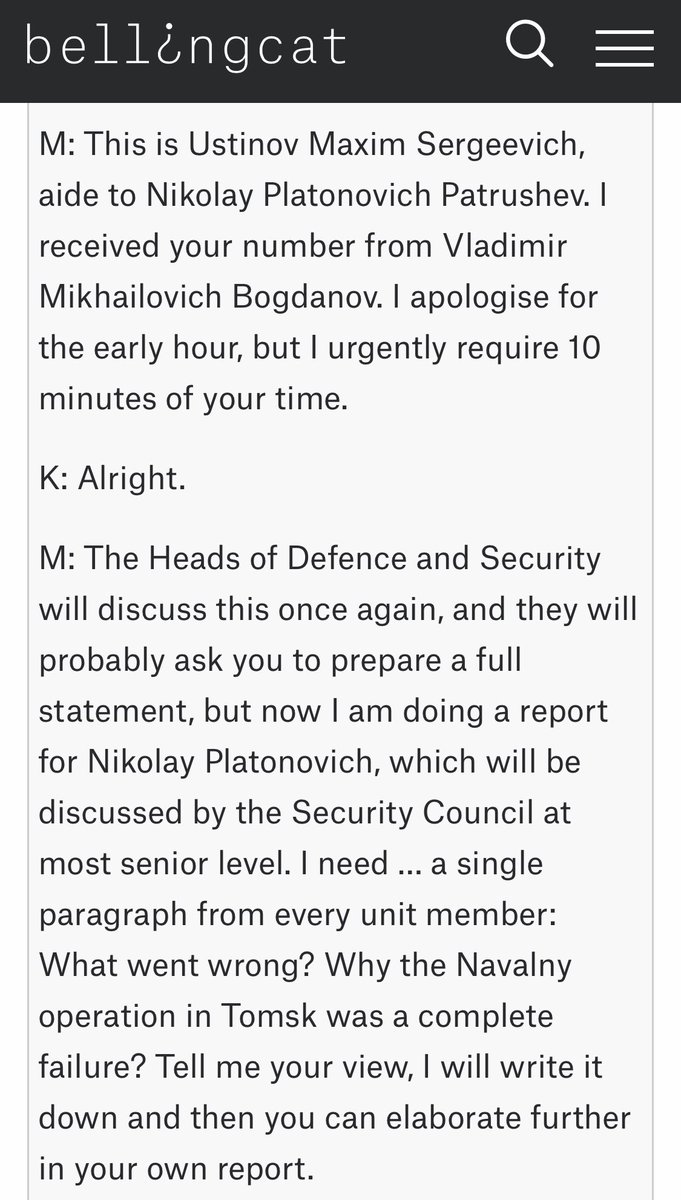
Let’s get into @navalny’s pretext: Maxim, fake aide to Chairman of Russia’s Security Council, Patrushev. Demanding an oral report for his boss on failure in poisoning op. Spoofed phone # for FSB.
Boss demands are a strong pretext for me bc of blame displacement & empathy drive.
Boss demands are a strong pretext for me bc of blame displacement & empathy drive.
We also see a name drop within the pretext opening: Vladimir has authorized the call. This leverages the @RobertCialdini Principles of Persuasion of Social Proof + Authority to build credibility & rapport fast — drop a senior person’s name and create a trust transfer.
This @navalny pretext is an “urgent report” — a strong pretext to use here bc it sets up the expectation that the caller will be asking questions in succession, and it will be less of a discussion. Without this pretext, the call will feel journalistic and phishy fast to a target.
We also see that @navalny made the calls to targets when some of them had COVID-19 — a unique timing impact on the clarity of mind of the call recipients. Taking advantage of an already confused, exhausted and worn down target. Not sure if intentional but is effective for sure.
Next we see another @RobertCialdini tactic: micro-yes. We see @navalny get his target “up the yes ladder” by stating what we should all agree with: if these people did their job well, why did the murder fail?
The target quickly moves toward yes and rapport w/ this argument.
The target quickly moves toward yes and rapport w/ this argument.
During phone attacks we often have targets attempt to stop the call, redirect to other phones or emails, and we must quickly redirect to stay on the line. Here we see @navalny is particularly skilled at redirection and persistence in his phone attack, getting back on track often.
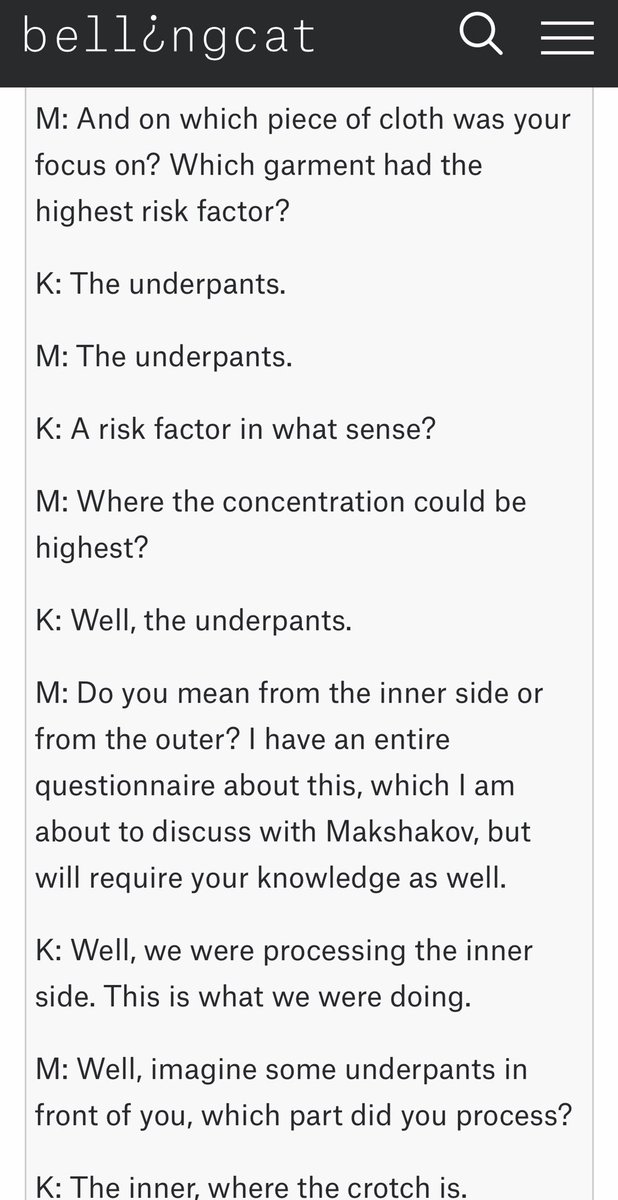
We see @navalny ask hard questions skillfully during the call. “Which garment had the highest risk factor?” is a strong and in-pretext “urgent report” method of asking “so what happened exactly?”
This ability to question in-character on the fly is essential in phone attacks.
This ability to question in-character on the fly is essential in phone attacks.
We also see my fave vishing technique employed in the @navalny call: giving false info in order to get corrected with the right info.
Likely not done on purpose here, but the method worked regardless — the target disclosed previously unknown details while correcting the caller.
Likely not done on purpose here, but the method worked regardless — the target disclosed previously unknown details while correcting the caller.
Always interesting to see how folks, even the ones who are involved in clandestine operations like nerve agent murder, are convinced of identity by caller id spoofing (among other things). I can spoof a phone number in 10 seconds for $1 — even use a dynamic voice changer. https://twitter.com/cnn/status/1341013050577575936
Interesting that @navalny called many before a successful call. Some hung up, another had COVID, 1 picked up and said “I know who you are” likely recognizing @navalny voice. Remote work under COVID likely impacted FSB’s internal ability to communicate a vishing attempt in action.
We see here that many tend to be less aware of phone attacks, pretexting, + spoofing capabilities — falsely believing caller id, name drops, & pretexts. This false sense led to the target giving up *the whole team* & *method of attack — nerve agent in underwear* during the call.

 Read on Twitter
Read on Twitter