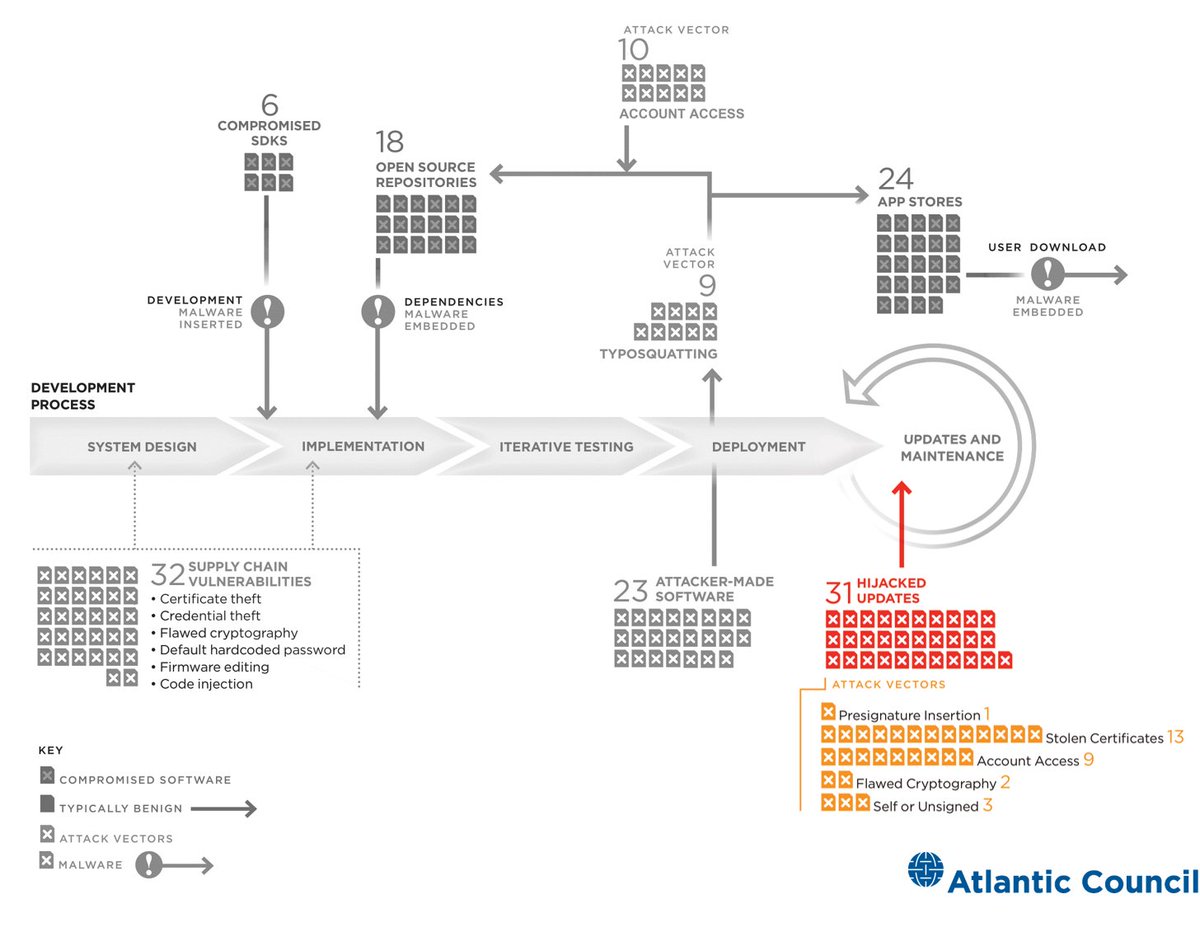
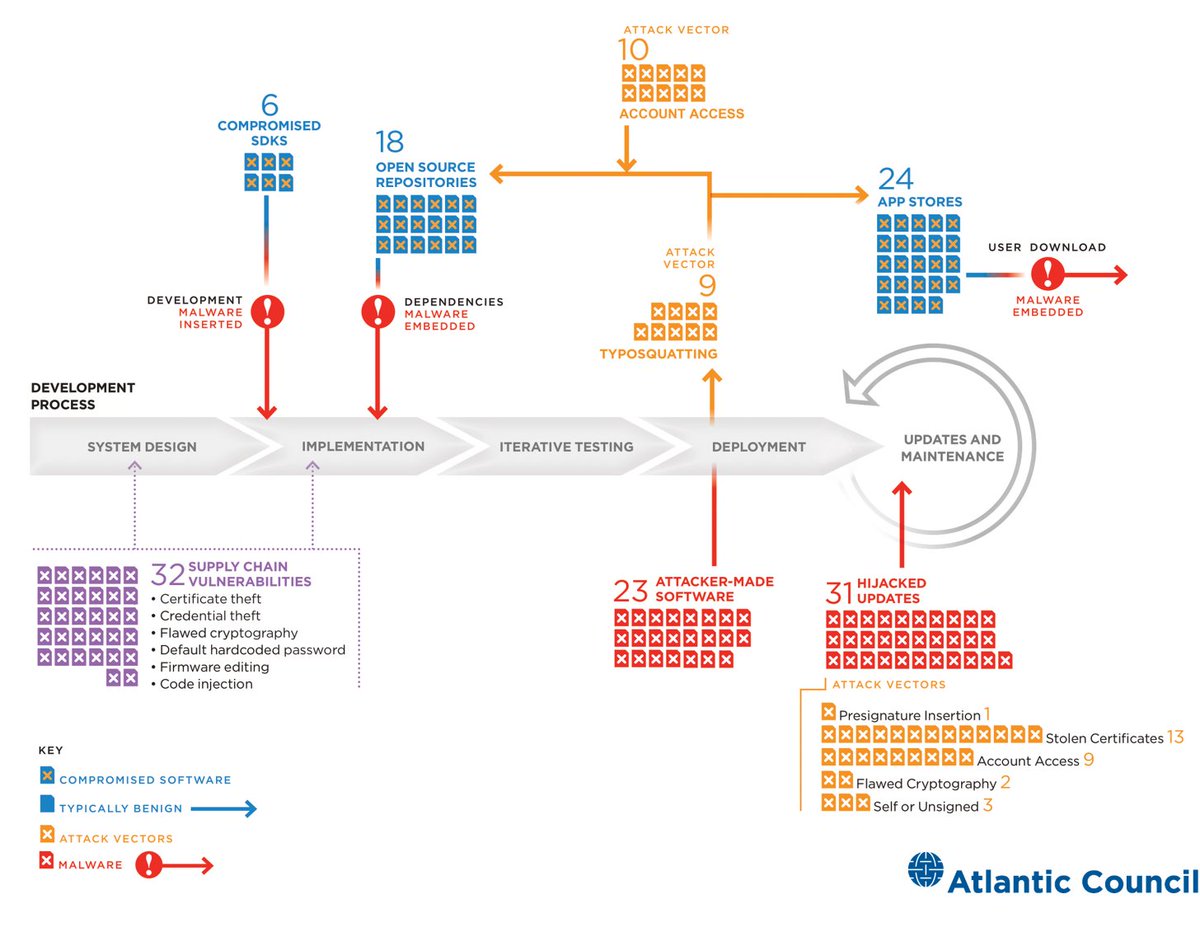
Since 2010, there have been at least 31 distinct attacks targeting updates in the software supply chain, of which 17 compromised build servers or altered code. Of those, more than half were attributed to state affiliated groups. 6/16
See report data set: https://bit.ly/3mtVzvq
See report data set: https://bit.ly/3mtVzvq
Software security needs to be equally about secure design and secure deployment. @NIST should lead, w/industry partnership, the development of a software lifecycle security overlay that builds on existing frameworks and controls and unifies them. 7/16
Developers don’t need new security controls; they need existing controls to be automated and made easier to implement. If your best practices and standards fit into a developer’s workflow  If they come via PDF or a color-coded spreadsheet
If they come via PDF or a color-coded spreadsheet  8/16
8/16
 If they come via PDF or a color-coded spreadsheet
If they come via PDF or a color-coded spreadsheet  8/16
8/16
PULLED UPDATE: SolarWinds customers downloaded the compromised update, which then patiently waited, hidden, for up to 2 weeks. 9/16
Compromised software updates are especially pernicious because users believe they can trust updates and fixes. If attackers have hidden their malware effectively, as in the 2017 ShadowPad incident, targets are unlikely to dig deeper. 10/16
. @NIST should work w/concerned agencies/cloud providers to push adoption of a software supply chain overlay in critical infrastructure. Securing software won’t help if we ignore the challenges of secure deployment throughout the lifecycle, esp across Operational Technology. 11/16
INITIAL FOOTHOLD: Following an approx. 2-week dormancy, the Sunburst malware reached out - disguised as legitimate Orion network traffic - to a set of shifting command and control servers and, on certain targets, downloaded additional malware. 12/16 https://www.fireeye.com/blog/threat-research/2020/12/evasive-attacker-leverages-solarwinds-supply-chain-compromises-with-sunburst-backdoor.html
Supply chain exploits expose large # of machines which are used to find valuable targets. #Sunburst hit ~18k orgs but attackers likely exploited far fewer. Similarly, ShadowHammer in 2019 targeted ASUS and hit 500k laptops but exploited just 600. 13/16 https://www.vice.com/en/article/pan9wn/hackers-hijacked-asus-software-updates-to-install-backdoors-on-thousands-of-computers
SolarWinds is a global company so this compromise may be used to target clients in Asia and Europe. We propose that US IC & InfoSec build on collaboration with partners like UK’s NCSC to share data & coordinate for joint policy responses. 14/16
Report: https://bit.ly/37p4yKi
Report: https://bit.ly/37p4yKi
Society has a software problem. The #Sunburst compromise shows the challenge of asserting & transferring trust throughout the software supply chain. This is not likely to improve quickly. The last 10 years have seen >115 software supply chain attacks or disclosures. 15/16
Change can happen but must be systematic, treat industry/government as equal partners, & recognize that this kind of risk will forever be managed, never eliminated. We laid out a few ideas but there’s more to come & many more people to hear from. 16/16 https://www.atlanticcouncil.org/breaking-trust/
For more infosec goodness and on point analysis as #Sunburst unfolds, look to these awesome people– @C_C_Krebs @Bing_Chris @KimZetter @ItsReallyNick @jfslowik @likethecoins @MalwareJake @nickdothutton @dnvolz @Joseph_Marks_ @snlyngaas @SteveBellovin @razhael 1/2
… @BuchananBen @Jason_Healey @alexstamos @RobertMLee @allanfriedman @HostileSpectrum @eborghard @jcherz @beauwoods @brysonbort @wendynather @campuscodi @hacks4pancakes @MSTIC @FireEye 2/2

 Read on Twitter
Read on Twitter