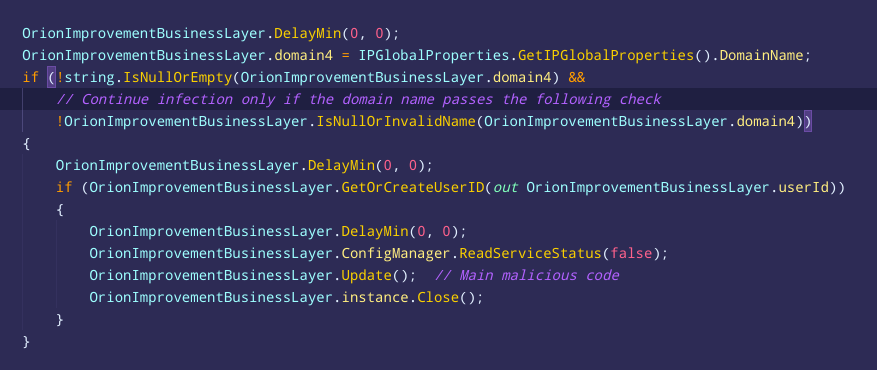
The attackers behind the #SUNBURST malware put a lot of effort into trying to avoid detection by analysts and security vendors. Not only this, but they also tried to make sure to stay under the radar of #SolarWinds developers and employees. A thread >>
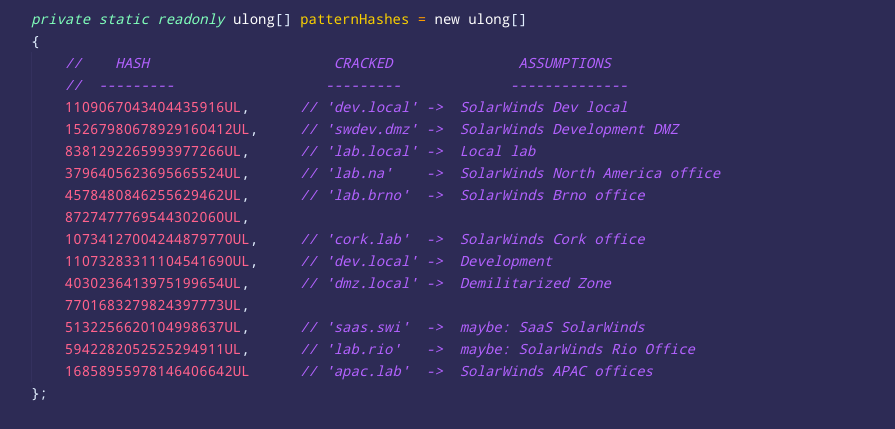
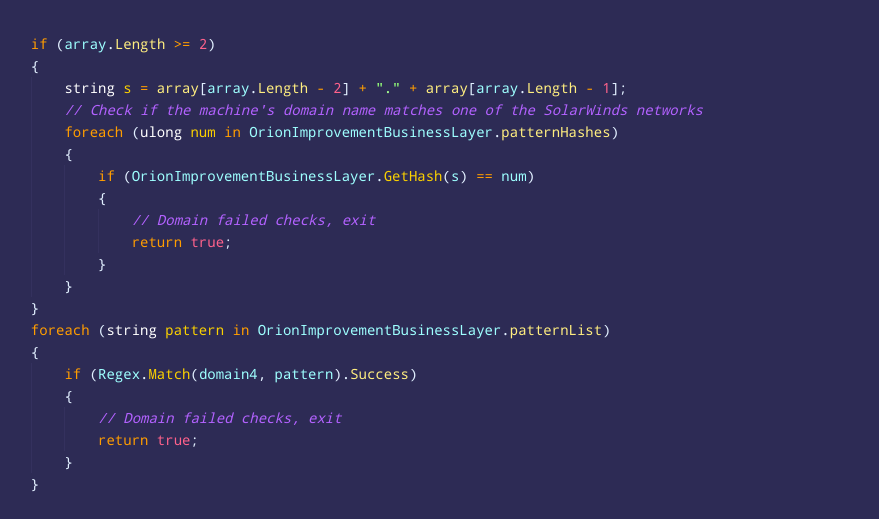
When brute-forcing the FNV-1a hashes embedded in #SUNBURST, I noticed that some of the cracked strings look like domain names of #SolarWinds internal networks across the globe. If the domain of the infected computer ends with one of these names, the malware would not run >>
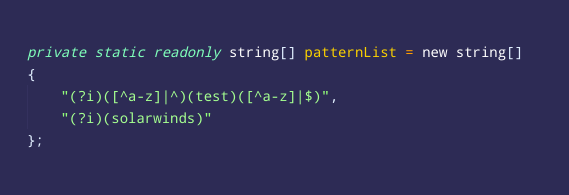
In addition to this, the #SUNBURST malware will match the domain name of the infected machine against two regular-expression patterns of "solarwinds" and "test" network domain names. >>
These checks might indicate that the attackers not only deeply learned the source code of #SolarWinds, but also learned the topology of their networks and internal development domain names to minimize the risk that a vigilant employee will notice the anomaly >>
Their efforts to stay undetected are impressive. They carefully tested the feasibility of the attack by first deploying a backdoor without malicious capabilities, wrote their code with #SolarWinds coding style, and avoided the infection of the company's internal networks.
wow.
wow.

 Read on Twitter
Read on Twitter