So you want to talk about the massive software supply chain intrusion & the most carefully-planned, complex espionage I’ve ever helped uncover?
Start here: https://www.fireeye.com/blog/threat-research/2020/12/evasive-attacker-leverages-solarwinds-supply-chain-compromises-with-sunburst-backdoor.html
But then what?? Let’s talk about some post-compromise techniques...
Start here: https://www.fireeye.com/blog/threat-research/2020/12/evasive-attacker-leverages-solarwinds-supply-chain-compromises-with-sunburst-backdoor.html

But then what?? Let’s talk about some post-compromise techniques...
Please read the above blog to appreciate multiple backdoors used, careful & unique tradecraft used on-premise...
We just published more details on what we’ve been finding post-compromise: https://blogs.microsoft.com/on-the-issues/2020/12/13/customers-protect-nation-state-cyberattacks/
ADFS key material compromise, SAML shenanigans, OAuth keys added...
We just published more details on what we’ve been finding post-compromise: https://blogs.microsoft.com/on-the-issues/2020/12/13/customers-protect-nation-state-cyberattacks/
ADFS key material compromise, SAML shenanigans, OAuth keys added...
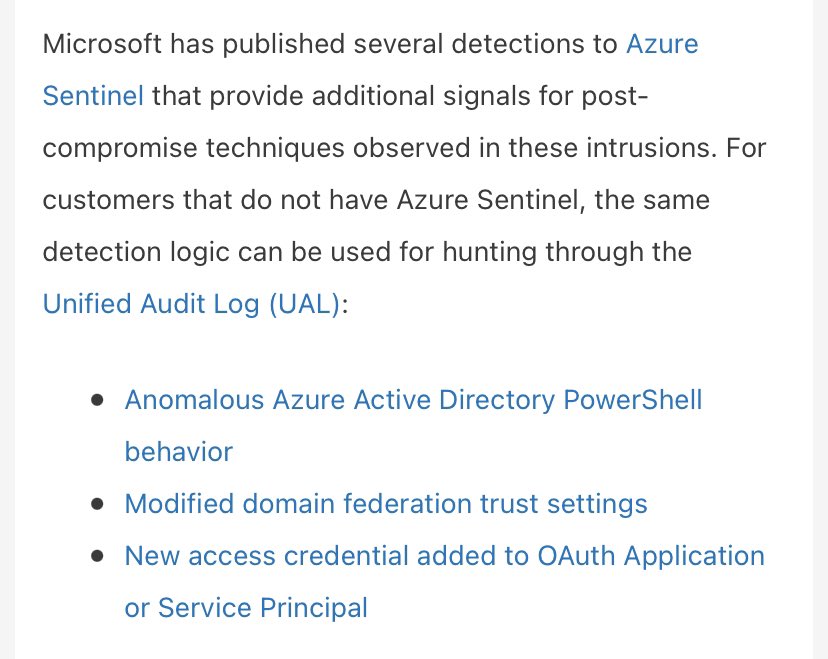
Within the technical companion blog ( https://msrc-blog.microsoft.com/2020/12/13/customer-guidance-on-recent-nation-state-cyber-attacks/) we provide some late stage killchain activity observed many places.
I want to highlight the additional detections pushed to cover these techniques in @MSAzureSentinel (but anyone can use on the UAL for #DFIR) ...
I want to highlight the additional detections pushed to cover these techniques in @MSAzureSentinel (but anyone can use on the UAL for #DFIR) ...
AAD PowerShell tomfoolery:
Logic to expose when a user or application signs in using Azure Active Directory PowerShell to access non-Active Directory resources, such as the Microsoft Graph
 https://github.com/Azure/Azure-Sentinel/pull/1442/files
https://github.com/Azure/Azure-Sentinel/pull/1442/files
Logic to expose when a user or application signs in using Azure Active Directory PowerShell to access non-Active Directory resources, such as the Microsoft Graph
 https://github.com/Azure/Azure-Sentinel/pull/1442/files
https://github.com/Azure/Azure-Sentinel/pull/1442/files
Domain federation trust horseplay:
Logic to highlight when an Active Directory Federated Service (ADFS) TrustedRealm object, such as a signing certificate, is added to the domain
 https://github.com/Azure/Azure-Sentinel/pull/1443/files
https://github.com/Azure/Azure-Sentinel/pull/1443/files
Globally rare event. Always interesting.
Logic to highlight when an Active Directory Federated Service (ADFS) TrustedRealm object, such as a signing certificate, is added to the domain
 https://github.com/Azure/Azure-Sentinel/pull/1443/files
https://github.com/Azure/Azure-Sentinel/pull/1443/filesGlobally rare event. Always interesting.
OAuth App Credential Hijinks
Finds new credentials added to to an App/SP.
With sufficient privileges, an actor can add alternate authentication material for direct access to resources using this credential.
More from @_dirkjan https://dirkjanm.io/azure-ad-privilege-escalation-application-admin/
 https://github.com/Azure/Azure-Sentinel/pull/1381
https://github.com/Azure/Azure-Sentinel/pull/1381
Finds new credentials added to to an App/SP.
With sufficient privileges, an actor can add alternate authentication material for direct access to resources using this credential.
More from @_dirkjan https://dirkjanm.io/azure-ad-privilege-escalation-application-admin/
 https://github.com/Azure/Azure-Sentinel/pull/1381
https://github.com/Azure/Azure-Sentinel/pull/1381
What an honor to work with such talented people who didn’t let setbacks (or sleep) get in the way of finding evil and cracking the case.
See those names throughout the blogs; and there are more.
Alright; so much work to be done now!
Don’t give up along the way.


 https://twitter.com/itsreallynick/status/1336907125591855106
https://twitter.com/itsreallynick/status/1336907125591855106
See those names throughout the blogs; and there are more.
Alright; so much work to be done now!
Don’t give up along the way.



 https://twitter.com/itsreallynick/status/1336907125591855106
https://twitter.com/itsreallynick/status/1336907125591855106
Oh and I must say... I was in the same spot as @SwiftOnSecurity (and let’s be honest, most everyone else) on SAML security. How could anyone know all of this??
Of course @cglyer somehow knows it and helped me along.
and helped me along.
Then #MSTIC brought in the big guns in Microsoft Identity https://twitter.com/swiftonsecurity/status/1338387127374065667
https://twitter.com/swiftonsecurity/status/1338387127374065667
Of course @cglyer somehow knows it
 and helped me along.
and helped me along.Then #MSTIC brought in the big guns in Microsoft Identity
 https://twitter.com/swiftonsecurity/status/1338387127374065667
https://twitter.com/swiftonsecurity/status/1338387127374065667
The benefit of understanding & detecting/hunting the above techniques is they can help identify post-compromise activity, even if* it's a different threat actor or a different initial infection vector: https://twitter.com/ItsReallyNick/status/1338532106629222400?s=20

 Read on Twitter
Read on Twitter