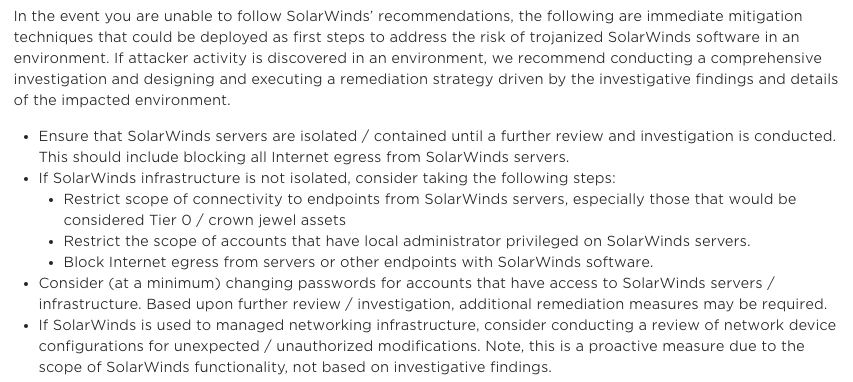
IR FOLKS - Look here
IR FOLKS - Look here - more in comments - If you are on a bridge right now... you need to jump on this GitHub... FireEye released signatures (Snort, YARA, and Clam) for Sunburst. These are all the detections they know of for the Solarwinds issue. https://github.com/fireeye/sunburst_countermeasures
- more in comments - If you are on a bridge right now... you need to jump on this GitHub... FireEye released signatures (Snort, YARA, and Clam) for Sunburst. These are all the detections they know of for the Solarwinds issue. https://github.com/fireeye/sunburst_countermeasures
FireEye Breakdown of what they know about how the Solarwinds issue works - https://www.fireeye.com/blog/threat-research/2020/12/evasive-attacker-leverages-solarwinds-supply-chain-compromises-with-sunburst-backdoor.html
Solarwinds Advisory that includes what versions are impacted and when hotfixes are coming - https://www.solarwinds.com/securityadvisory
Washington Post article claiming recent major high profile government breaches were all related to this issue (The folks above you will want this) - https://www.washingtonpost.com/national-security/russian-government-spies-are-behind-a-broad-hacking-campaign-that-has-breached-us-agencies-and-a-top-cyber-firm/2020/12/13/d5a53b88-3d7d-11eb-9453-fc36ba051781_story.html
Need the bullets?:
1. Crank logging of Solarwinds systems.
2. Kill outbound access from Solarwinds servers.
3. Magnifying glass on all outbound connectivity from sensitive segments.
4. Deploy detections now - https://github.com/fireeye/sunburst_countermeasures
1/x
1. Crank logging of Solarwinds systems.
2. Kill outbound access from Solarwinds servers.
3. Magnifying glass on all outbound connectivity from sensitive segments.
4. Deploy detections now - https://github.com/fireeye/sunburst_countermeasures
1/x
5. Are you on a vulnerable version? - https://www.solarwinds.com/securityadvisory
6. Hotfix expected on 12/15 - If you are on a vulnerable version, get the your change request in now.
7. Start preparing to reset everyones access to Solarwinds AND every monitoring credential it uses.
2/x
6. Hotfix expected on 12/15 - If you are on a vulnerable version, get the your change request in now.
7. Start preparing to reset everyones access to Solarwinds AND every monitoring credential it uses.
2/x
8. If it looks like you won't be able to patch. Follow FireEye recommendations. https://www.fireeye.com/blog/threat-research/2020/12/evasive-attacker-leverages-solarwinds-supply-chain-compromises-with-sunburst-backdoor.html
9. Schedule a meeting with your stakeholders, let them know this is evolving, start finding out what the plan/impact is if you need to shutdown Solarwinds.
God speed. <FIN>
9. Schedule a meeting with your stakeholders, let them know this is evolving, start finding out what the plan/impact is if you need to shutdown Solarwinds.
God speed. <FIN>
11:19ish - CISA Tweet - https://twitter.com/USCERT_gov/status/1338337481654218753
Tomorrow (12/14) at 5pm ET - @MalwareJake will be summarizing what they know so far - https://sansurl.com/solarwinds
An amazing break down from @KimZetter - https://twitter.com/KimZetter/status/1338305089597964290?s=20
SANS ISC Diary - https://isc.sans.edu/diary/rss/26884
More excellent analysis. Includes places to look for the malicious DLL. https://twitter.com/kylehanslovan/status/1338506923642122243
Solarwinds SEC filing - https://twitter.com/campuscodi/status/1338538285929541632
Veloxity write up on a group they called Dark Halo that seems to be the same threat actor.
https://www.volexity.com/blog/2020/12/14/dark-halo-leverages-solarwinds-compromise-to-breach-organizations/
https://www.volexity.com/blog/2020/12/14/dark-halo-leverages-solarwinds-compromise-to-breach-organizations/

 Read on Twitter
Read on Twitter