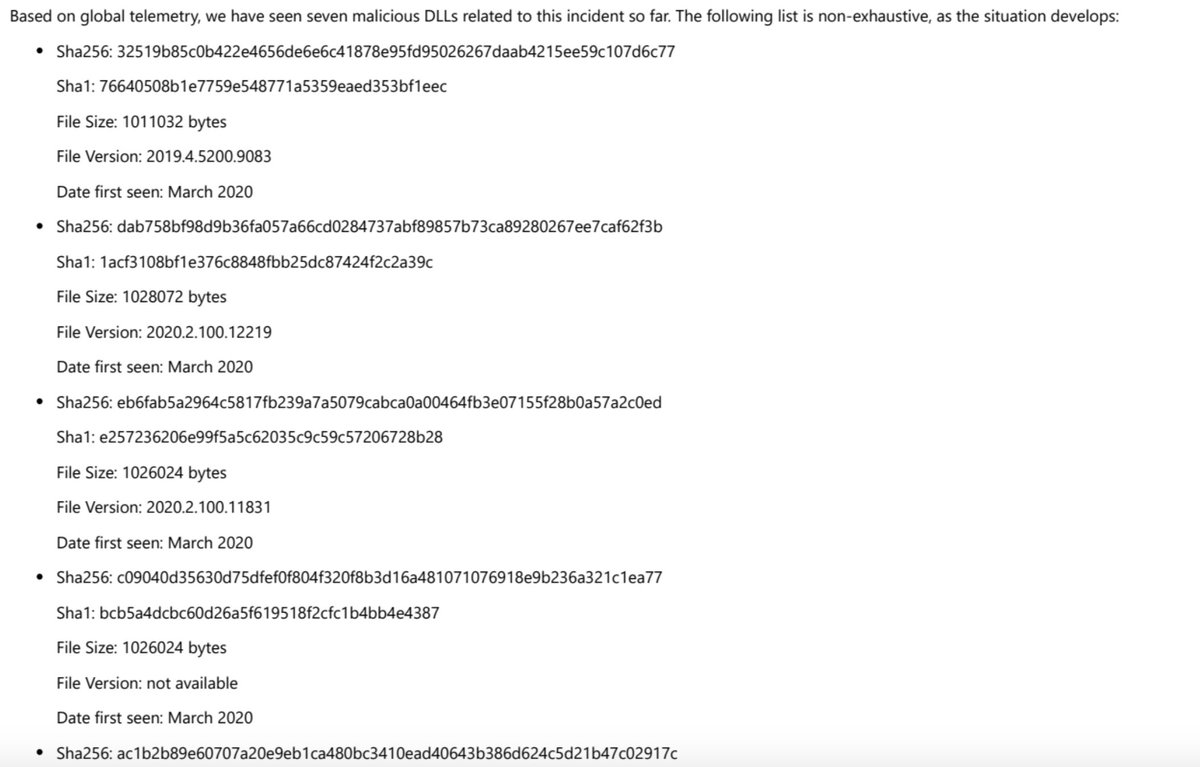
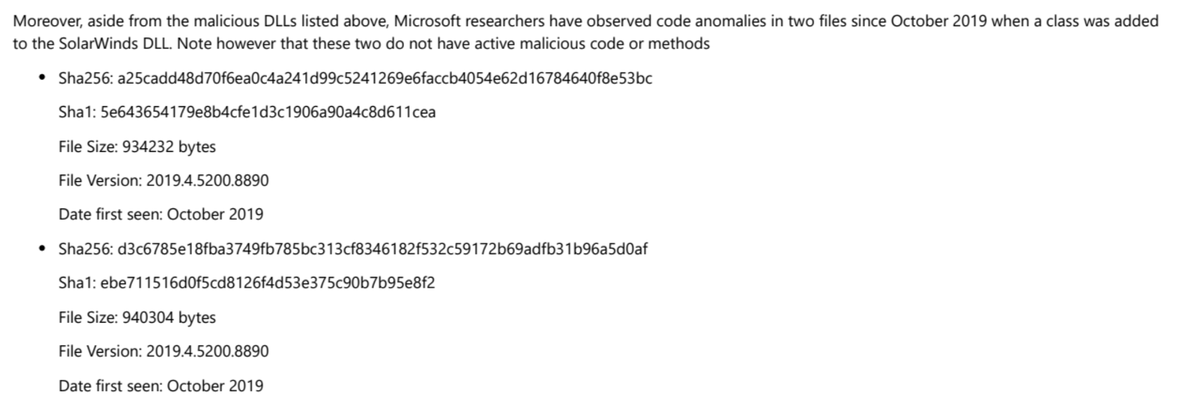
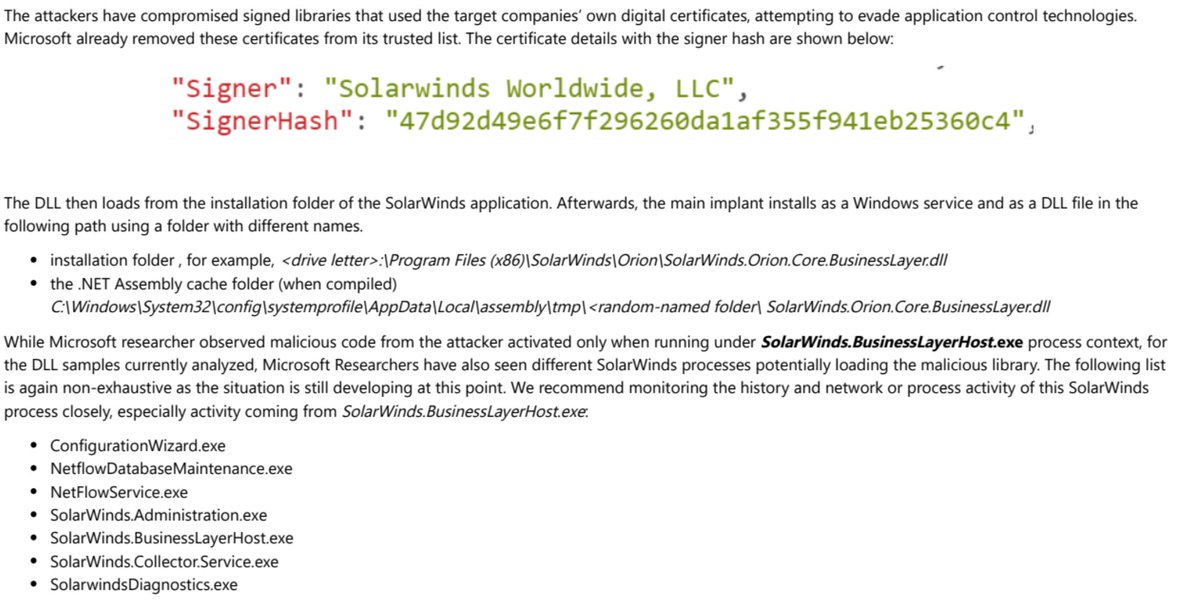
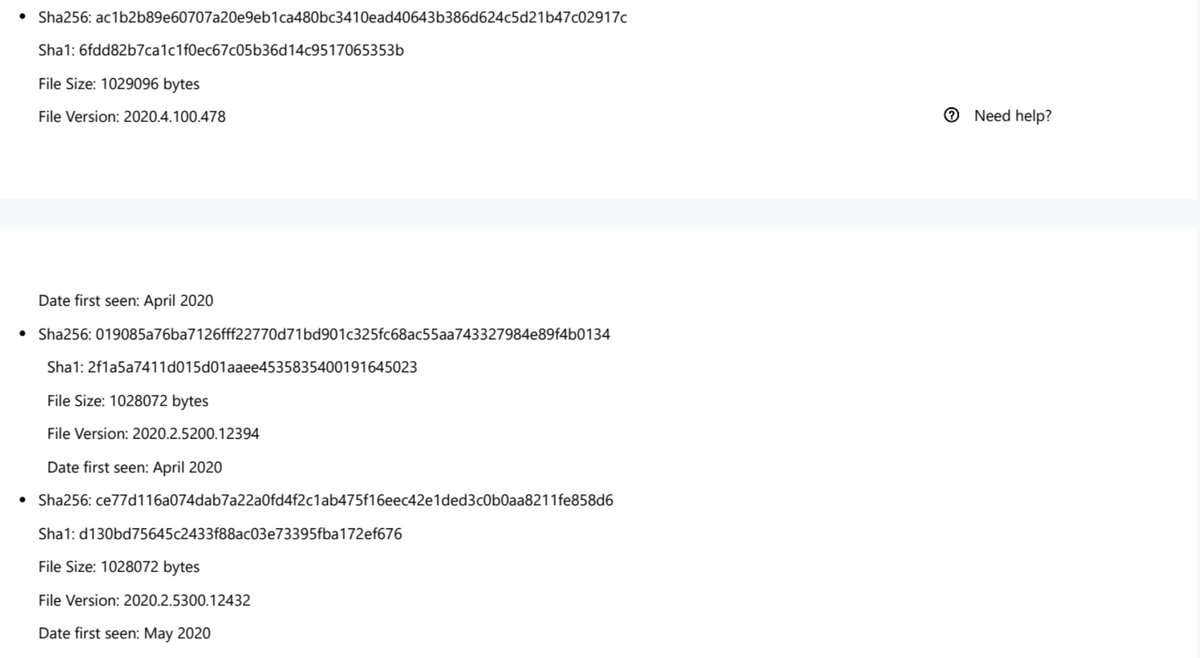
"While updating the SolarWinds application, the embedded backdoor code loads before the legitimate code runs. Organizations are misled into believing that no malicious activity has occurred and that the program or application dependent on the libraries is behaving as expected."
"The malicious DLL calls out to a remote network infrastructure using the domains http://avsvmcloud.com . to prepare possible second-stage payloads, move laterally in the organization, and compromise or exfiltrate data"
Oh, and it looks like Microsoft released a patch for the SolarWinds hack yesterday, which it is calling "Solorigate."
"Microsoft detects the main implant and its other components as Solorigate." https://www.microsoft.com/en-us/wdsi/threats/malware-encyclopedia-description?Name=Behavior:Win32/Solorigate.C!dha&ThreatID=2147771132
"Microsoft detects the main implant and its other components as Solorigate." https://www.microsoft.com/en-us/wdsi/threats/malware-encyclopedia-description?Name=Behavior:Win32/Solorigate.C!dha&ThreatID=2147771132

 Read on Twitter
Read on Twitter