Can we just have one quiet weekend... https://twitter.com/Bing_Chris/status/1338194968389840897
Can confirm @Bing_Chris's report that several federal agencies incl NTIA are investigating breaches seemingly tied to nation-state hackers.
"It's not entirely certainly what vulnerability they're using, how they got in, but it continues to be a problem," a U.S. official told me.
"It's not entirely certainly what vulnerability they're using, how they got in, but it continues to be a problem," a U.S. official told me.
"The FBI's on site" at the Commerce Department, the parent agency of NTIA, per this official.
Emergency NSC meeting yesterday, this person said.
"It seems like it's gonna be a much bigger issue, but there's not a lot of firm understanding of how broad the scale is."
Emergency NSC meeting yesterday, this person said.
"It seems like it's gonna be a much bigger issue, but there's not a lot of firm understanding of how broad the scale is."
In addition to the FBI, CISA is providing support, and ODNI and U.S. Cyber Command have gotten involved.
"When CyberCom starts getting involved in something, it's a big deal," U.S. official said. "The implication is that it's a nation-state confrontation."
"When CyberCom starts getting involved in something, it's a big deal," U.S. official said. "The implication is that it's a nation-state confrontation."
The attack appears to have involved victims' Microsoft authentication tokens, raising concerns that the same techniques could be used on a wider scale.
"This seems to be connected to microsoft in some way," U.S. official said.
"This seems to be connected to microsoft in some way," U.S. official said.
. @nakashimae is reporting that Russia's foreign intelligence service, the SVR, is behind these federal agency intrusions: https://www.washingtonpost.com/national-security/russian-government-spies-are-behind-a-broad-hacking-campaign-that-has-breached-us-agencies-and-a-top-cyber-firm/2020/12/13/d5a53b88-3d7d-11eb-9453-fc36ba051781_story.html
The SVR was also reportedly behind the FireEye hack.
The SVR was also reportedly behind the FireEye hack.
When FireEye announced its breach, it said that it was working with Microsoft to investigate.
Seems possible that these attacks are connected in terms of technique not just perpetrator.
Seems possible that these attacks are connected in terms of technique not just perpetrator.
From Reuters' story: "Hackers broke into the NTIA’s office software, Microsoft’s Office 365. Staff emails at the agency were monitored by the hackers for months..."
The hackers were "able to trick the Microsoft platform’s authentication controls..." https://www.reuters.com/article/us-usa-cyber-amazon-com-exclsuive/exclusive-u-s-treasury-breached-by-hackers-backed-by-foreign-government-sources-idUSKBN28N0PG
The hackers were "able to trick the Microsoft platform’s authentication controls..." https://www.reuters.com/article/us-usa-cyber-amazon-com-exclsuive/exclusive-u-s-treasury-breached-by-hackers-backed-by-foreign-government-sources-idUSKBN28N0PG
A bit more specificity on timing, per a U.S. official: Investigators believe that the hackers had been monitoring federal workers' emails since June.
Fear is that "the same techniques…could have been leveraged against other agencies," since "everybody uses Microsoft products."
Fear is that "the same techniques…could have been leveraged against other agencies," since "everybody uses Microsoft products."
Solar Winds' other government customers, per its website: Census Bureau, DOJ, Oak Ridge and Sandia National Labs, VA, Army, Air Force, Navy, and Marine Corps. https://www.solarwinds.com/federal-government/it-management-solutions-for-government
Plus state, local, educational, and foreign customers, e.g. Texas, NHS, and European Parliament. https://twitter.com/nakashimae/status/1338244109107163137
Plus state, local, educational, and foreign customers, e.g. Texas, NHS, and European Parliament. https://twitter.com/nakashimae/status/1338244109107163137
CISA statement: “We have been working closely with our agency partners regarding recently discovered activity on government networks. CISA is providing technical assistance to affected entities as they work to identify and mitigate any potential compromises.”
NTIA referred to Commerce, which said: "We can confirm there has been a breach in one of our bureaus. We have asked CISA and the FBI to investigate, and we cannot comment further at this time."
NSC spokesman John Ullyot: “The United States government is aware of these reports and we are taking all necessary steps to identify and remedy any possible issues related to this situation.”
FBI and Treasury Department have not provided comments yet.
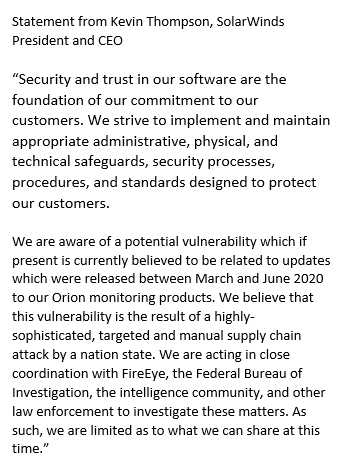
Solar Winds, IT firm used by federal agency victims, says "a highly-sophisticated, targeted and manual supply chain attack by a nation state" compromised the software updates released earlier this year for its Orion IT monitoring platform.
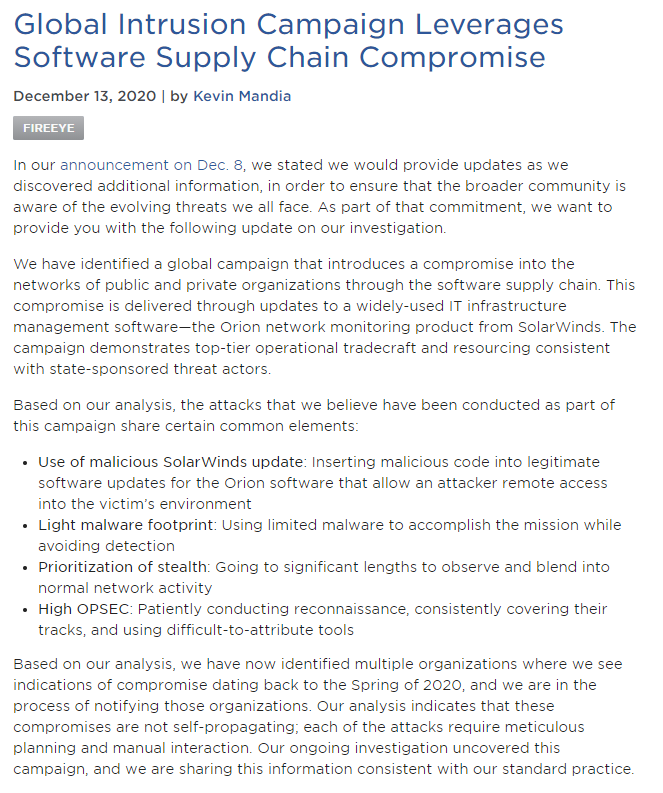
Confirming earlier suspicions, FireEye says that its breach was part of a global campaign of cyberattacks leveraging a compromised SolarWinds Orion software update.
FireEye is notifying victims it discovers.
https://www.fireeye.com/blog/products-and-services/2020/12/global-intrusion-campaign-leverages-software-supply-chain-compromise.html
Technical details: https://www.fireeye.com/blog/threat-research/2020/12/evasive-attacker-leverages-solarwinds-supply-chain-compromises-with-sunburst-backdoor.html
FireEye is notifying victims it discovers.
https://www.fireeye.com/blog/products-and-services/2020/12/global-intrusion-campaign-leverages-software-supply-chain-compromise.html
Technical details: https://www.fireeye.com/blog/threat-research/2020/12/evasive-attacker-leverages-solarwinds-supply-chain-compromises-with-sunburst-backdoor.html

 Read on Twitter
Read on Twitter