#Phalse-Phlag phishings are in preparation. They'll be blamed on Russia. Inevitably that will drag Trump into it and the end-game will have begun. #Wakeupsheeple. #Russiagate is back.
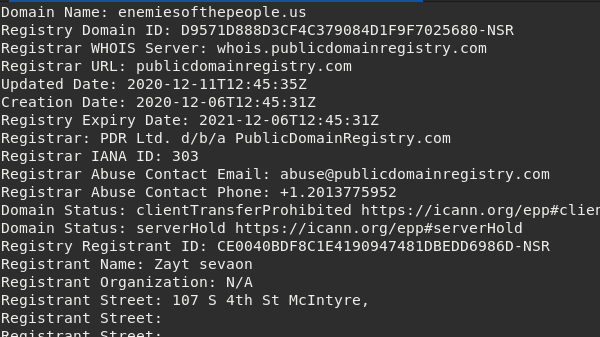
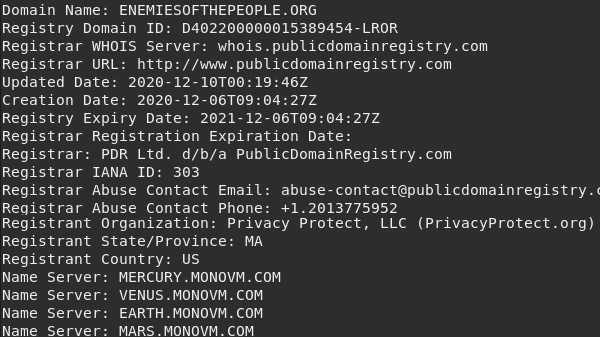
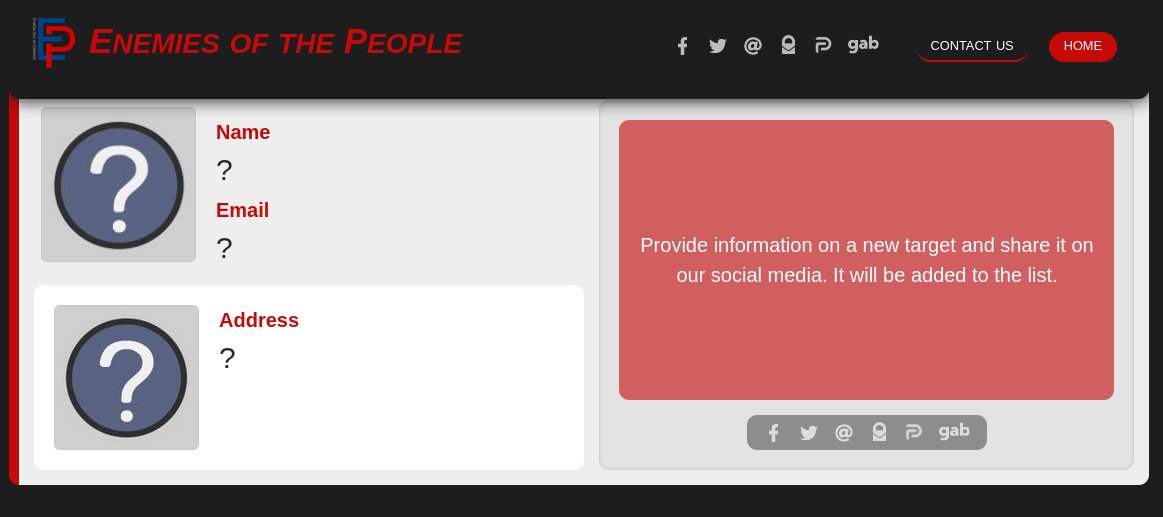
Yesterday I noticed a story doing the rounds about some websites set up by (note the quotes) "Trump Supporters." Their names tell the story: enemiesofthepeople[.org]/[.us] & enemiesofthenation[.org]/[.com]. Election officials & Dominion employees were marked for death.
@jfslowick first spotted that some of the infrastructure was based in #Russia. His article was spotted by the "calm and rational" @thedailybeast who reported that the FBI were "investigating." Yes. The irony. https://pylos.co/2020/12/10/terrorism-or-information-operation/
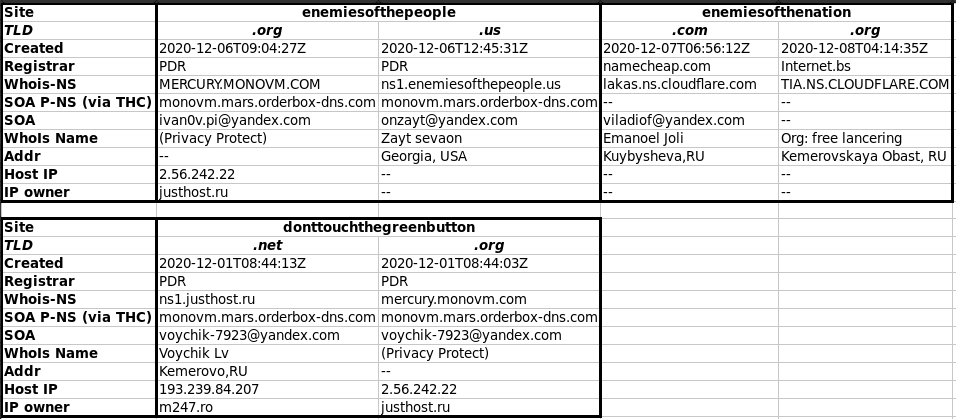
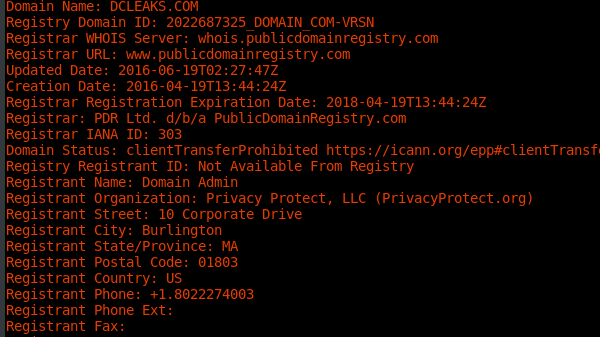
As you may know I just finished a book on G2.0, Fancy & Cozy Bear, DCLeaks, IRA etc. *ALL* false-flags, and these 2020 vigilante sites share much of the infrastructure. Same registrars. Same DNS IPs as DCLeaks and 100's of others blamed on the GRU. https://www.amazon.com/dp/B08MSZHMGP
The E-of-the-P websites are only the tip of the iceberg. I've found 174 phishing sites they've set-up in Fancy Bear's distinctive style. The SOA of each one shows they all use the same nameservers as DCLeaks. List on pastebin. https://pastebin.com/1NjdKEYZ https://archive.is/91dXo
The targetted entities are obvious from the spoof domain names; usamilitary[.us], ustreasury[.us], cbnn[.us], citibanks[.org], emirate-ae[.net], imfgov[.org], internationalmonetaryfund[.us], unccc[.org], ucso[.net] and many others. Imagine the outcry if phishing successful.
Be warned that it's coming and will be blamed on Trump `colluding again with Russia' because the vigilante sites pretended to be run by US based Trump supporters. One gave an address in Georgia USA. However, the "Russian fingerprints" were beyond blatant. Note: dcleaks similar.
Some gave addresses in Russia and most had http://yandex.com emails. The HTML contained a Russian language IP logger and their Parler account put their IP in posts: 2.56.242.22 is justhost[.ru] in Moscow. Yes. Moscow.
https://web.archive.org/web/20201210214616/https://parler.com/profile/EnemiesOfTheNation
https://web.archive.org/web/20201210214616/https://parler.com/profile/EnemiesOfTheNation
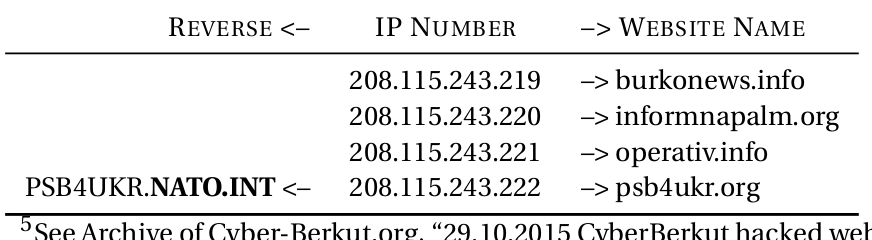
Where have we seen this before? Vigilate websites run by folks that want us to think Russia is attacking?: Ukraine. It's inspired by the sinister: http://psb4ukr.org a/k/a “The Peacemaker.” It also invited people to dox "criminal pro-Russian Terrorists." Compare the two:
It was supported by the SBU (~FBI in UA) who used it at checkpoints and investigations. It out-sourced intelligence, encouraged suspicion and fear, shamed pro-Russia voices, and legitimised vigilantism. People were murdered. http://archive.is/i5Tr5
https://archive.is/da9pVlegitimized
https://archive.is/da9pVlegitimized
Like the "Peacemaker," E-of-the-P allows for psychos to "provide information on a new *target* and share it on our social media. It will be added to the list." No evidence is required. No trial. People are so angry right now that this is a dangerous game.
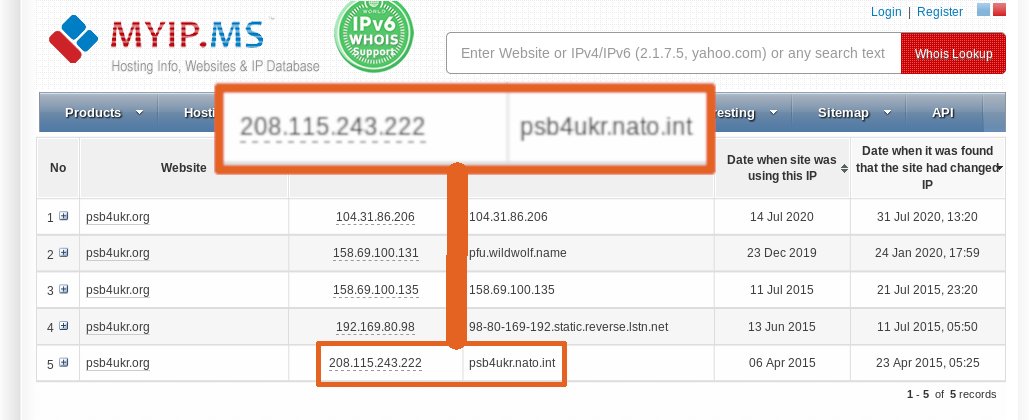
In Oct 2015 pro-Russian hackers Cyber Berkut claimed to have hacked Anton Geraschenko. They released a doc with details. It's *that* doc that G2.0 used for his "Russian fingerprints." A key detail in it was http://psb4ukr.org was a NATO Psy-Op. http://archive.is/WunsT
Web crawlers confirm the site was originally hosted by NATO. Within days the E-of-the-P site that used the Russian IP was taken down. By whom? I can't confirm, but it must be the Russians. By contrast, the FBI left DCLeaks & G2.0's websites online for four years.
It's a set-up. The final narrative has been set in motion. There'll be more games when Biden arrives to "heal us all" with -->Blinken Bad<-- as SoS.
https://www.thedailybeast.com/a-vile-website-doxxing-trumps-enemies-has-caught-the-eye-of-the-fbi
https://www.thedailybeast.com/a-vile-website-doxxing-trumps-enemies-has-caught-the-eye-of-the-fbi
Edit: One of the domains was ustreasury[.us]. @Mehringer2001 and @JonathanFC229 pointed out that today at ~18:00 GMT this happened ....
https://archive.is/JfJhj
https://archive.is/JfJhj
@with_integrity pointed out people within Russia can't (easily) get a http://Yandex.COM email account. They are redirected to http://yandex.ru . Also, here's the MX (email) record for all the #phalsephlag domains: https://archive.is/niyys Note the us2. subdomain=USA.
Edit --- EDIT F-IN-EDIT: https://twitter.com/nakashimae/status/1338226993775714309

 Read on Twitter
Read on Twitter![Yesterday I noticed a story doing the rounds about some websites set up by (note the quotes) "Trump Supporters." Their names tell the story: enemiesofthepeople[.org]/[.us] & enemiesofthenation[.org]/[.com]. Election officials & Dominion employees were marked for death. Yesterday I noticed a story doing the rounds about some websites set up by (note the quotes) "Trump Supporters." Their names tell the story: enemiesofthepeople[.org]/[.us] & enemiesofthenation[.org]/[.com]. Election officials & Dominion employees were marked for death.](https://pbs.twimg.com/media/EpIsDW5XIAAJAEs.png)

![Edit: One of the domains was ustreasury[.us]. @Mehringer2001 and @JonathanFC229 pointed out that today at ~18:00 GMT this happened .... https://archive.is/JfJhj Edit: One of the domains was ustreasury[.us]. @Mehringer2001 and @JonathanFC229 pointed out that today at ~18:00 GMT this happened .... https://archive.is/JfJhj](https://pbs.twimg.com/media/EpJZCm4XIAoIM89.png)


