I’m bored. Let’s talk about Russ Ramsland, and Allied Special Operations Group, the “cyber security” company that he works for, that also happens to be conducting the “forensic audit” of voting machines in Antrim County Michigan - https://www.freep.com/story/news/politics/elections/2020/12/06/trump-legal-team-examining-antrim-county-voting-equipment/3847931001/
You probably first heard of Ramsland from his affadavits included in the Kraken case that famously confused Michigan and Minnesota
https://www.politifact.com/factchecks/2020/dec/04/russell-james-ramsland-jr/affidavit-michigan-lawsuit-seeking-overturn-electi/ https://www.courtlistener.com/recap/gov.uscourts.gand.284055/gov.uscourts.gand.284055.1.10_1.pdf
https://www.politifact.com/factchecks/2020/dec/04/russell-james-ramsland-jr/affidavit-michigan-lawsuit-seeking-overturn-electi/ https://www.courtlistener.com/recap/gov.uscourts.gand.284055/gov.uscourts.gand.284055.1.10_1.pdf
Ramsland's affadavit makes some pretty lofty claims. He supposedly holds degrees from Harvard and Duke, and claims to have worked with NASA and MIT. He doesn't claim to have a cybersecurity background himself, but leans heavily on the experience of other employees at ASOG
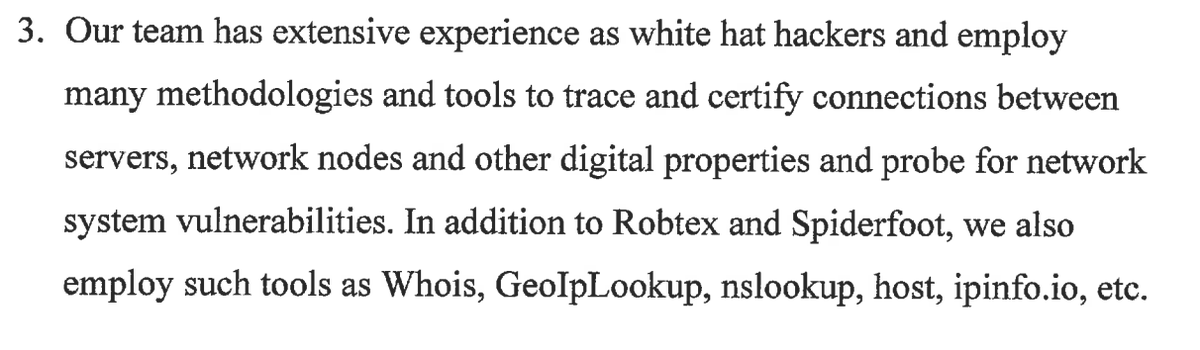
Ramsland talks about the tools that Allied Security Operations Group employs (Also known as "Allied Special Operations Group"). For those unfamiliar, these tools are a mix of OSINT/infosec search engines and basic command line tools. It's info sec 101 stuff, nothing special.
Ramsland's affadavit leans heavily on statistical analysis that supposedly indicates fraud occurred. Since I'm not a statistician, I'll point you to the thorough tear down submitted by the defense in the Georgia Kraken case - https://www.courtlistener.com/recap/gov.uscourts.gand.284055/gov.uscourts.gand.284055.62.3.pdf
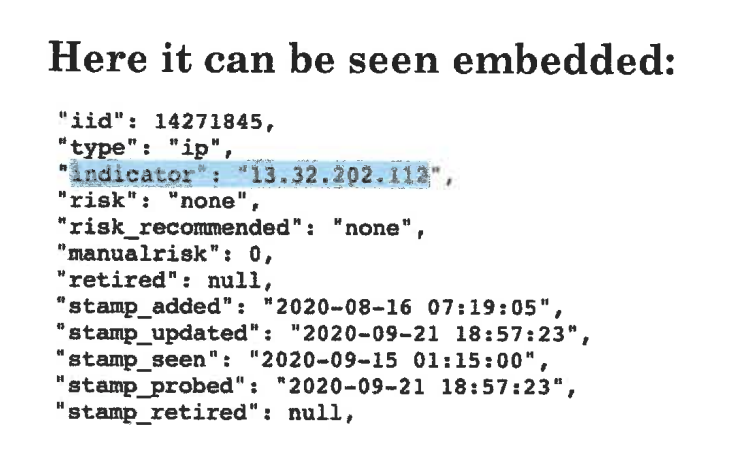
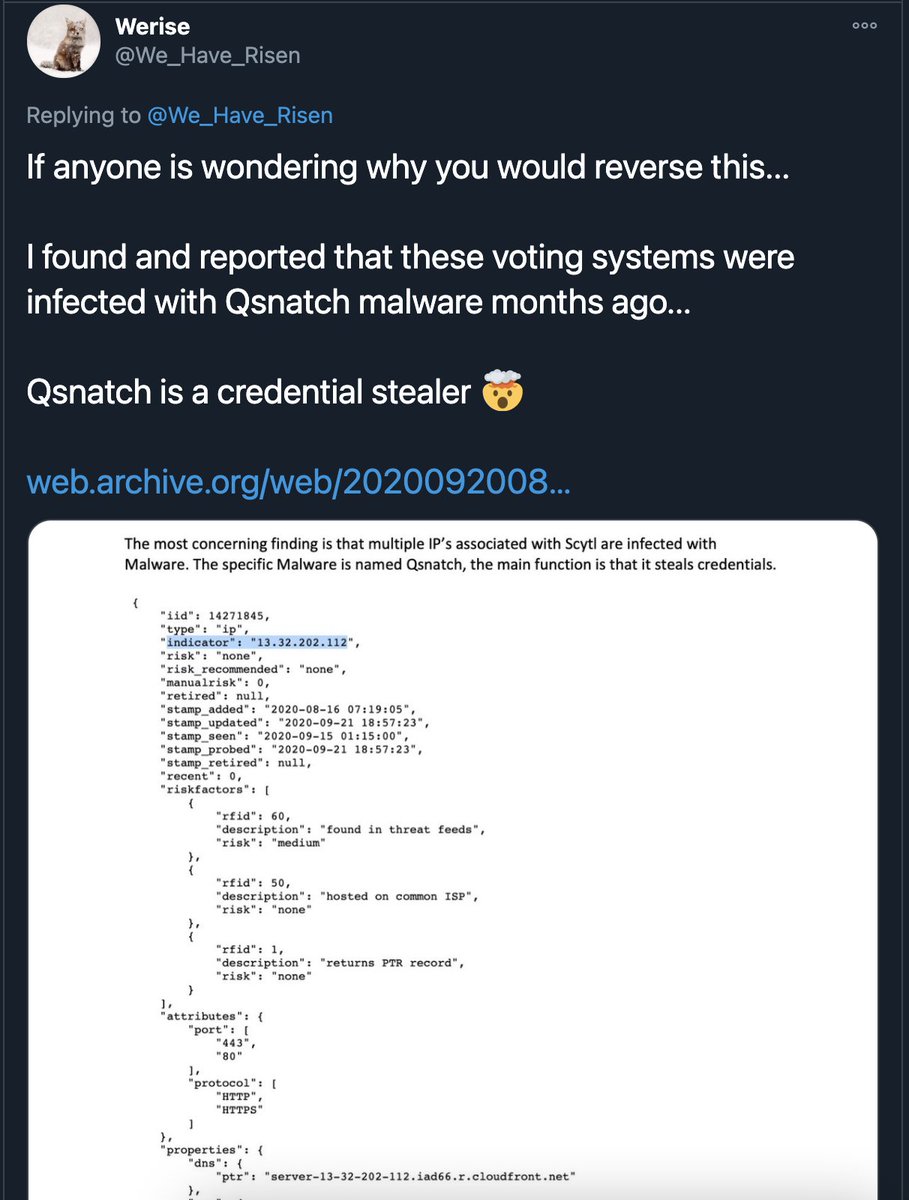
However, the affidavit makes some interesting infosec claims. First, they claim that a domain, ' http://staging.scytl.us ', was infected with Qsnatch, a strain of malware that infects QNAP NAS devices. They "prove" this by pasting in a screenshot of JSON blob from a threat feed
On the left, you can see the information included with the Ramsland GA affidavit. On the right, you can see that same information, complete with the same highlighted text, in a tweet posted on 11/11. It really looks like he just cropped the tweet and pasted it in the affadavit
So either the OP of the tweet works for ASOG - OR - Ramsland is implying the data included in the affidavit originated from ASOG, when it in fact came from a random Twitter user.
Regardless, the Qsnatch link is specious at best. The information in the screenshot came from Pulsedive, a threat intel service. You can view the exact information yourself by visiting this link: https://pulsedive.com/api/?pretty=true&iid=14271845
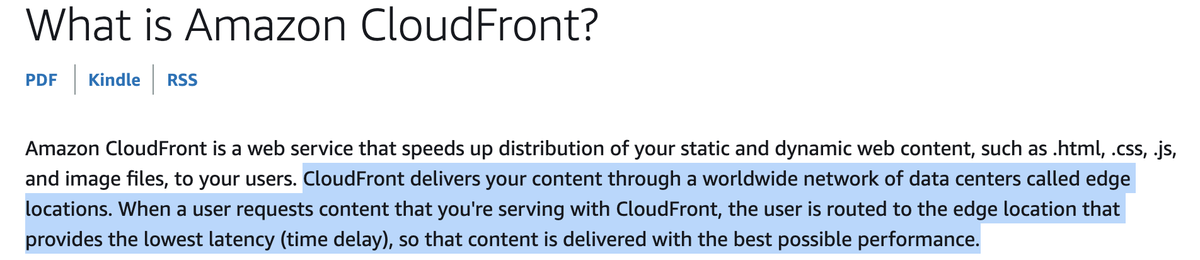
The IP is a CloudFront IP. Let's talk about Cloudfront
The IP is a CloudFront IP. Let's talk about Cloudfront
CloudFront is Amazon Web Service's CDN (Content Delivery Network). CDN's are how the internet stays afloat. Instead of everyone accessing your website on a single server, CDN's help spread the load by serving your site from hundreds or thousands of servers
CDN's like CloudFront will often use some DNS magic to serve you content from a server closest to your physical location, in order to reduce latency. Since CDN's are dynamic, there's a good chance the same site will be served from many different IP addresses
Since AWS is..."the cloud", more or less...they have *a lot* of IP addresses. And a single CloudFront IP address can serve content from *multiple* different customers, even within a short time span. What's this mean for Ramsland's QSnatch claim?
It means that, at one time, ' http://staging.scytl.us ' resolved to a CloudFront IP that also, at one time, was fronting a server infected with Qsnatch. So that IP ended up in a threat feed. That *does not*, in any way, indicate that Scytl was infected with Qsnatch
Could Scytl have been or be infected with Qsnatch? Sure. But there's *no way* to know that from the data in the affidavit. It's like when you get calls on your cell from debt collectors looking for the person that had the number before you.
This should all be obvious and easily understood by someone who claims to be involved with an elite cybersecurity company. But like I pointed out earlier, he didn't even bother pulling Pulsedive report himself, *he copied it from a tweet*
And about the "Server in Germany" storyline -- my guess is that was a similar situation. AWS has data centers in Frankfurt. Scytl uses CloudFront. It would not be weird for an AWS Frankfurt IP to serve Scytl content.
If they have more conclusive data that Scytl was infected with Qsnatch, they haven't included it in any of the Kraken affidavits I've looked at so far. Now let's see what else Ramsland has to say about Qsnatch
Something about those bullet's looks familiar though. Let's revisit the tweet that seems to have..."inspired" Ramsland's affidavit, and check out the link included - https://web.archive.org/web/20200920081214/https://www.ncsc.gov.uk/files/NCSC%20CISA%20Alert%20-QNAP%20NAS%20Devices.pdf
https://twitter.com/We_Have_Risen/status/1326697422362435585
https://twitter.com/We_Have_Risen/status/1326697422362435585
That link goes to a security bulletin put out jointly by the British National Cyber Security Centre and...CISA, the DHS CyberSecurity org that recently made headlines after Trump fired the head, @C_C_Krebs. The irony's rich, considering the Q crowd think Krebs is deep state
Deep state or not, Ramsland must be a fan of the CISA report on Qsnatch, because there seem to be some similarities between his affidavit (left) and the CISA report (right)
So Ramsland basically copied and pasted the content from the NCSC/CISA report into the affidavit, with one notable exception - he decided to flesh out the 'Credential Scraping' bullet point with his own commentary. His is on the left, and the right is the NCSC/CISA report
Before taking a closer look at his comments, it's worth re-iterating that Qsnatch affects only QNAP NAS devices, which are networked file stores. These are typically accessible via an internal network - it would be extremely weird to put a CloudFront distribution in front of one
So let's see what Ramsland says (left), and compare that to a report on Qsnatch done by an actual security firm (right). The two descriptions...do not match. At all. I'll break it down in the next tweet https://s3.amazonaws.com/ssc-corporate-website-production/documents/qsnatch-technical-report.pdf
In order for his claims to be accurate, Scytl would 1) have to be using Qnap NAS devices and 2) create accounts for "every administrator whose system loads information into Scytl" on those devices. This would be...extremely weird. His explanation doesn't really make sense at all
Oh, and of course, all of my analysis so far is completely glossing over the fact that there's *no connection* between Scytl and Dominion, so the entire Qsnatch tangent in the affidavit is moot anyways. Unless we see more conclusive proof of his claims, he's flat out wrong.
So, to recap, Ramsland's 5th point the GA affidavit was basically entirely copy/pasted from a tweet, yet he heavily implied the information originated from him and/or his company, Allied Security Operations Group
All of this brings up an interesting question. Does he know he's making shit up? He definitely knows he copy/pasted from this tweet. Does he think it's correct? Is it perjury either way? I'm not a lawyer, so I have no idea. https://twitter.com/We_Have_Risen/status/1326697422362435585
Now, on to the next point. This one should be easier to break down, and is also hilariously dumb. He basically claims that Dominion source code can be found on the dark web, and then includes a text snippet showing a "sample of what can be seen on Pirate Bay TORR" 





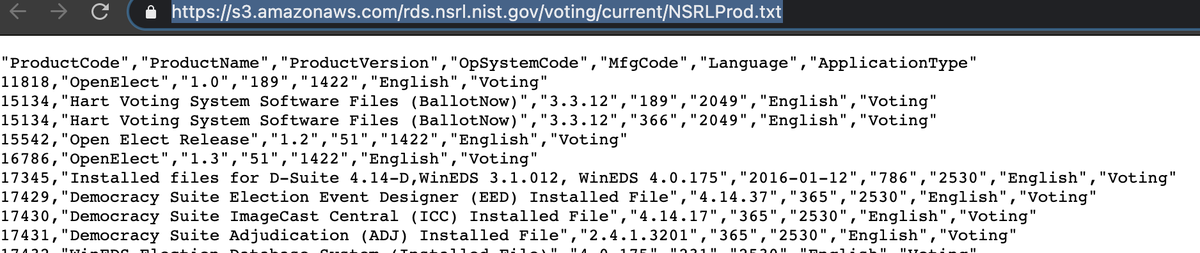
Aside from the fact that "Pirate Bay TORR" is the most boomer thing I've seen all night, the snippet he included actually comes from NISTS "Voting Software Reference Data Set" page, and *not* the dark web - https://www.nist.gov/itl/ssd/software-quality-group/voting-software-reference-data-set
https://s3.amazonaws.com/rds.nsrl.nist.gov/voting/current/NSRLProd.txt
https://s3.amazonaws.com/rds.nsrl.nist.gov/voting/current/NSRLProd.txt
So here's Russel Ramsland, including info published on a govt website in a sworn affidavit, and claiming it's proof that Dominion software has leaked onto the dark web. If he didn't know he was lying when he wrote that, he shouldn't be calling himself a cybersecurity pro
Like I mentioned earlier, the rest of his affidavit is a flawed statistical analysis that has been torn apart by the defense in the GA case, so I'll skip covering that
I need to wrap it up for the night, and this thread is already too long. I'll pick it back up tomorrow and cover what I found about ASOG - the company Ramsland is involved with - as well as profile some of the other ASOG execs and their backgrounds
I'm definitely curious to see what comes of this Antrim business though, because nothing I've seen so far makes me think that ASOG has the skills to forensically look for signs of voter fraud, let alone turn on a fucking computer.
Unrolled version: https://threadreaderapp.com/thread/1335836728905531393.html

 Read on Twitter
Read on Twitter