Saw this article [1] on HN to block hardcoded DNS settings on Smart TVs and IoT devices. They'll just bypass this with DNS of HTTPS (DoH). If you're going this far, take 10 minutes and a couple additional steps to do it right. A thread.  1/
1/
[1] https://labzilla.io/blog/force-dns-pihole
 1/
1/[1] https://labzilla.io/blog/force-dns-pihole
The simplest method is to block all ip traffic to and from all the DNS servers. This requires a maintained list of all global DNS servers and may break some things. Luckily, there's a pretty good one that exists.
2/
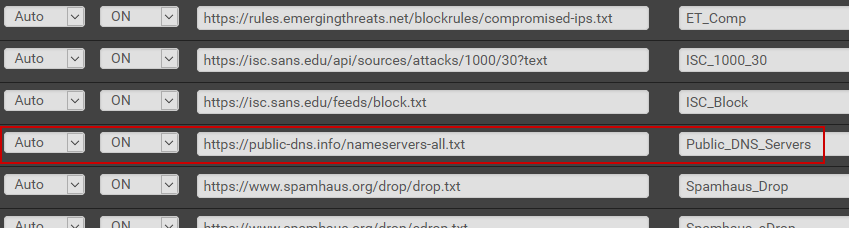
Site: https://public-dns.info/
List: https://public-dns.info/nameservers-all.txt
2/
Site: https://public-dns.info/
List: https://public-dns.info/nameservers-all.txt
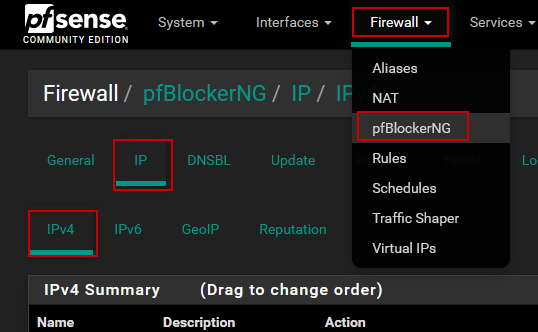
The article assumes you have pfSense. So do I. Head on over to pfBlockerNG (Firewall -> pfBlockerNG). You may need to add it if you don't see that option. My ISP ( @AskZiplyFiber) is ghetto and still doesn't support ipv6, so we're going to focus in ipv4. Go to IP -> IP4.
3/
3/
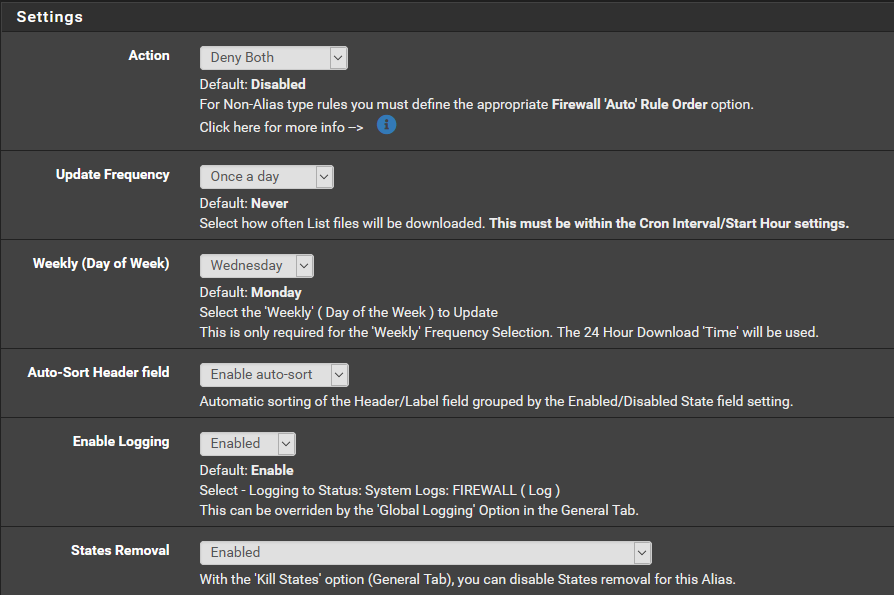
Hit Add. Enter the DNS server list. Set the Action to either Deny Outbound or Deny Both. Be nice to the folks hosting the list and only update once a day . I keep logging enabled so I can what devices on my network trying to communicate with ips in the list.
. I keep logging enabled so I can what devices on my network trying to communicate with ips in the list.
4/
 . I keep logging enabled so I can what devices on my network trying to communicate with ips in the list.
. I keep logging enabled so I can what devices on my network trying to communicate with ips in the list.4/
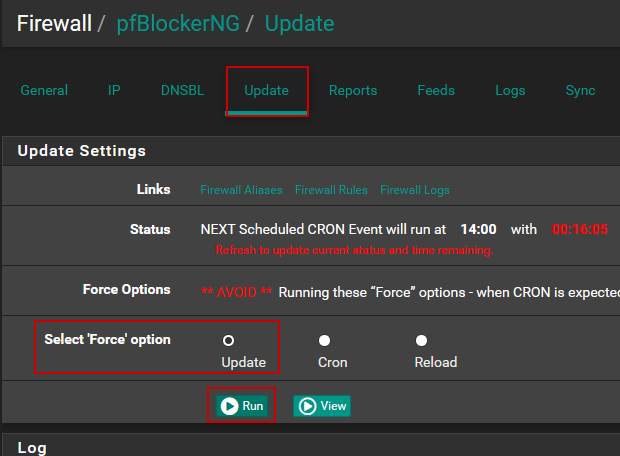
Don't forget to hit save at the bottom. Now, head over to Update and Force an, uh, Update.
Try it out: https://1.1.1.1
Next, what things is this going to break, how to unbreak them, and tips.
5/
Try it out: https://1.1.1.1
Next, what things is this going to break, how to unbreak them, and tips.
5/
* Don't forget to allow the DNS servers you use. If you use a pihole, use that as the source instead of ANY.
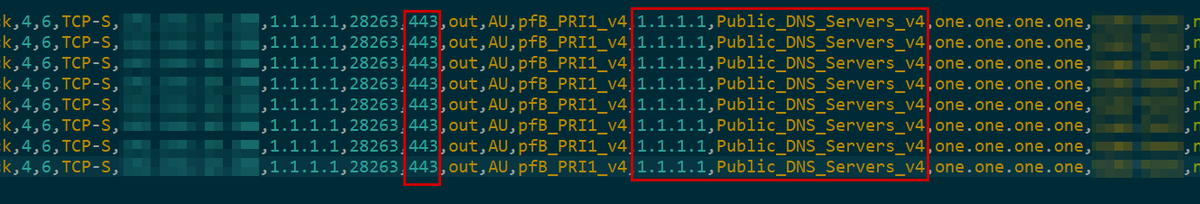
* This broke smart device X, my baby monitor, etc. Check your logs. See what's blocked. Set up a static DHCP reservation. Allow outbound for that device.
* Almost done
6/
* This broke smart device X, my baby monitor, etc. Check your logs. See what's blocked. Set up a static DHCP reservation. Allow outbound for that device.
* Almost done
6/
* To allow certain DNS servers, I prefer using a Firewall Alias. I'm a big fan of what @perezbox is doing with @cleanbrowsing. Add whatever DNS servers you use to your firewall chain.
7/
7/
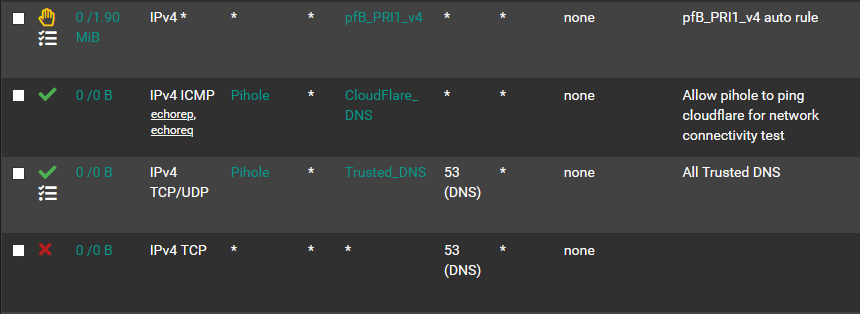
Here are the final FW rules:
1. Auto rule blocking lists from pfBlockerNG
2. Pihole fails connectivity tests if ICMP is blocked to Cloudflare
3. Allow my pihole to talk to my trusted DNS servers on port 53
4. Block all port 53 traffic
8/
1. Auto rule blocking lists from pfBlockerNG
2. Pihole fails connectivity tests if ICMP is blocked to Cloudflare
3. Allow my pihole to talk to my trusted DNS servers on port 53
4. Block all port 53 traffic
8/
If you're already running pfsense and a pihole, this is probably a 5-10 minute task and worth doing. Or just don't buy smart devices.  Good luck.
Good luck.
 Good luck.
Good luck.
In case the settings look a bit different, I'm running the 2.5 development builds of pfsense and verified the settings in both 2.2.5_37 and 3.0.0_3 of @BBcan177's pfBlockerNG-devel package.

 Read on Twitter
Read on Twitter