Curious little phishing email just dropped into my inbox, using DPD as a lure rather than the usual Amazon/PayPal/Microsoft ruse.
The sender is a compromised http://Hotmail.com account, so nothing too special there. The two buttons use the same URL...
1/n
The sender is a compromised http://Hotmail.com account, so nothing too special there. The two buttons use the same URL...
1/n
The URL is www[.]caythuocnamchuabenh[.]com/redame
Looks like Vietnamese food website which may have been compromised or has a vulnerability which have been abused to redirect the user to the final phishing destination: https://ip-64-202-189-152[.]ip[.]secureserver[.]net/DPD
2\\n
Looks like Vietnamese food website which may have been compromised or has a vulnerability which have been abused to redirect the user to the final phishing destination: https://ip-64-202-189-152[.]ip[.]secureserver[.]net/DPD
2\\n
The DPD phishing site looks pretty convincing - a lovely copy and paste job  . They've even gone as far as to make up the parcel's history with recent dates and times... classy touch!
. They've even gone as far as to make up the parcel's history with recent dates and times... classy touch!
But what is the end goal here? Steal DPD login credentials? Redirect real deliveries?
3\\n
 . They've even gone as far as to make up the parcel's history with recent dates and times... classy touch!
. They've even gone as far as to make up the parcel's history with recent dates and times... classy touch!But what is the end goal here? Steal DPD login credentials? Redirect real deliveries?
3\\n
Turns out, it's like every other phish  They'd love you to reschedule your delivery, but unfortunately as we missed the first attempt, it'll cost us some money.
They'd love you to reschedule your delivery, but unfortunately as we missed the first attempt, it'll cost us some money.
After filling out the 'shipping address' for where we'd like it redelivered, we get to the good stuff..
4\\n
 They'd love you to reschedule your delivery, but unfortunately as we missed the first attempt, it'll cost us some money.
They'd love you to reschedule your delivery, but unfortunately as we missed the first attempt, it'll cost us some money.After filling out the 'shipping address' for where we'd like it redelivered, we get to the good stuff..
4\\n
Time to pay 
But uh oh, we can only pay via card - prepay account and PayPal are blanked out. Shame.
Submitting this send all the lovely data to a PHP script hosted on the same box: https://ip-64-202-189-152[.]ip[.]secureserver[.]net/DPD/php/status[.]php
5\\n

But uh oh, we can only pay via card - prepay account and PayPal are blanked out. Shame.
Submitting this send all the lovely data to a PHP script hosted on the same box: https://ip-64-202-189-152[.]ip[.]secureserver[.]net/DPD/php/status[.]php
5\\n
Credit where credit is due, they're thorough! They validate the card number to ensure it isn't made up (urgh, further effort!).
With a valid card number, they're cheeky enough to squeeze a few extra details out of you, pretending to be the Visa Verified screen.
6\\n
With a valid card number, they're cheeky enough to squeeze a few extra details out of you, pretending to be the Visa Verified screen.
6\\n
Once that's all done and dusted, they're nice enough to redirect us off to the real http://DPD.co.uk website.
What else is hosted on that IP address I wonder.. well, turned out, a tonne of DPD scams according to @urlscanio https://urlscan.io/search/#ip:%2264.202.189.152%22
https://urlscan.io/search/#ip:%2264.202.189.152%22
7\\n
What else is hosted on that IP address I wonder.. well, turned out, a tonne of DPD scams according to @urlscanio
 https://urlscan.io/search/#ip:%2264.202.189.152%22
https://urlscan.io/search/#ip:%2264.202.189.152%227\\n
Another lovely feature of @urlscanio is that you can search by the hash of the resources loaded by the page (so images, CSS, JS etc.) which means we can go fishing for phishing!
For example, lets take the 'main.css' file: https://urlscan.io/search/#hash%3Ac555831c27ebbbbd32dfeb7cd25a605f5c6ffa10e1cd431841f9672e1198f490
Few more hits
8\\n
For example, lets take the 'main.css' file: https://urlscan.io/search/#hash%3Ac555831c27ebbbbd32dfeb7cd25a605f5c6ffa10e1cd431841f9672e1198f490
Few more hits

8\\n
We've just gained a whole bunch of new domains or compromised sites to sift through, but lets just quickly validate they're hosting the same phishing kit.. yup!
A look at one of the requests suggests they even went and registered a domain - dpdlocal-online[.]com
9\\n
A look at one of the requests suggests they even went and registered a domain - dpdlocal-online[.]com
9\\n
Registered a whole 46 days ago, on 2010-10-19, via Namecheap 
Sometimes you'll find lazy attackers who like to leave directory listing enabled, so simply traversing up one folder in the URL reveals a ZIP of the phishing kit, or the live source code being used
Fin.
10\\10

Sometimes you'll find lazy attackers who like to leave directory listing enabled, so simply traversing up one folder in the URL reveals a ZIP of the phishing kit, or the live source code being used

Fin.
10\\10

 Read on Twitter
Read on Twitter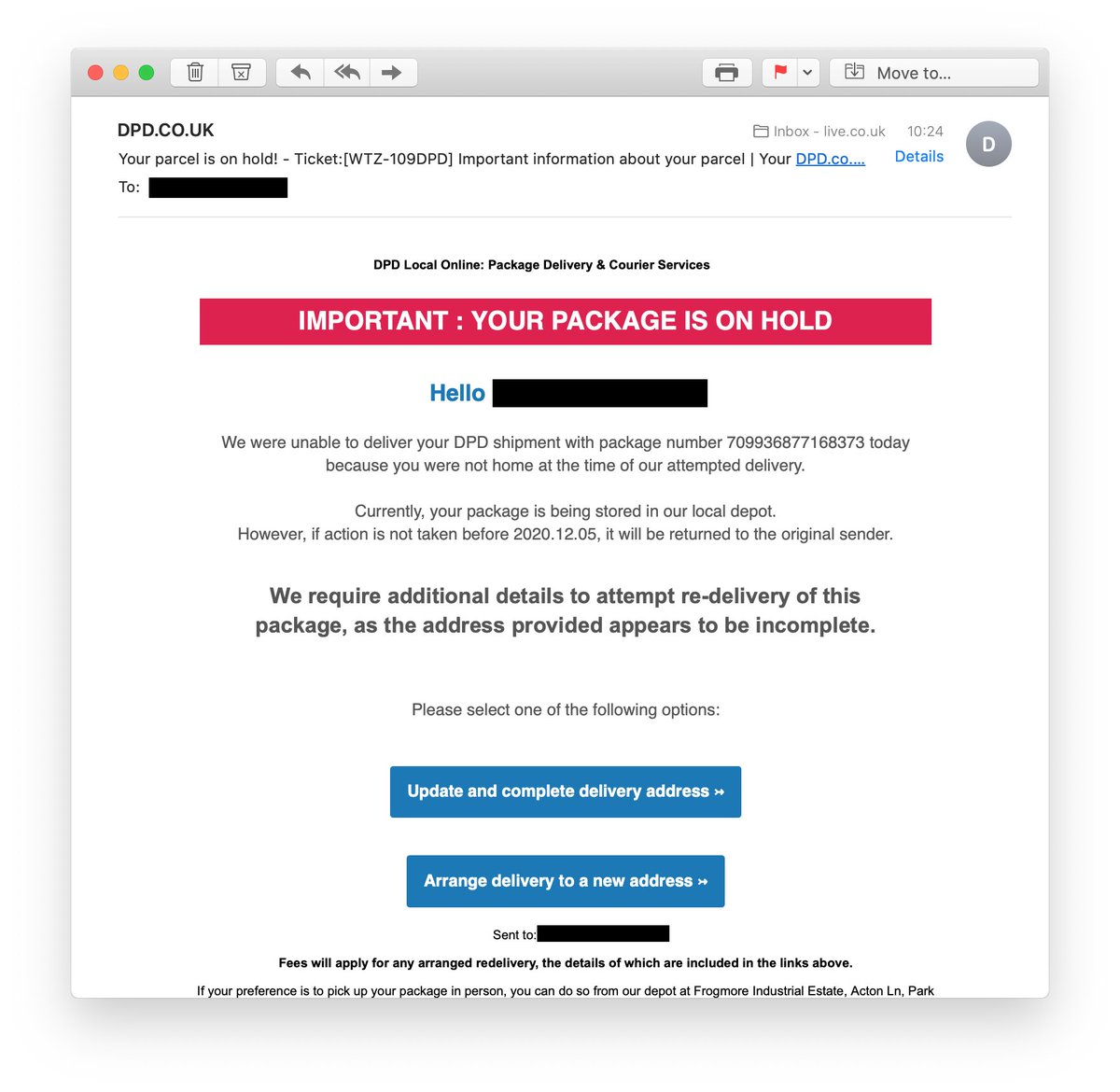
![The URL is www[.]caythuocnamchuabenh[.]com/redameLooks like Vietnamese food website which may have been compromised or has a vulnerability which have been abused to redirect the user to the final phishing destination: https://ip-64-202-189-152[.]ip[.]secureserver[.]net/DPD2\\n The URL is www[.]caythuocnamchuabenh[.]com/redameLooks like Vietnamese food website which may have been compromised or has a vulnerability which have been abused to redirect the user to the final phishing destination: https://ip-64-202-189-152[.]ip[.]secureserver[.]net/DPD2\\n](https://pbs.twimg.com/media/EoY1NwjXIAAEmvZ.png)
![The URL is www[.]caythuocnamchuabenh[.]com/redameLooks like Vietnamese food website which may have been compromised or has a vulnerability which have been abused to redirect the user to the final phishing destination: https://ip-64-202-189-152[.]ip[.]secureserver[.]net/DPD2\\n The URL is www[.]caythuocnamchuabenh[.]com/redameLooks like Vietnamese food website which may have been compromised or has a vulnerability which have been abused to redirect the user to the final phishing destination: https://ip-64-202-189-152[.]ip[.]secureserver[.]net/DPD2\\n](https://pbs.twimg.com/media/EoY1Ny1XYAAv0N5.png)


![Time to pay But uh oh, we can only pay via card - prepay account and PayPal are blanked out. Shame.Submitting this send all the lovely data to a PHP script hosted on the same box: https://ip-64-202-189-152[.]ip[.]secureserver[.]net/DPD/php/status[.]php5\\n Time to pay But uh oh, we can only pay via card - prepay account and PayPal are blanked out. Shame.Submitting this send all the lovely data to a PHP script hosted on the same box: https://ip-64-202-189-152[.]ip[.]secureserver[.]net/DPD/php/status[.]php5\\n](https://pbs.twimg.com/media/EoY5YdKXUAI0tj7.jpg)
![Time to pay But uh oh, we can only pay via card - prepay account and PayPal are blanked out. Shame.Submitting this send all the lovely data to a PHP script hosted on the same box: https://ip-64-202-189-152[.]ip[.]secureserver[.]net/DPD/php/status[.]php5\\n Time to pay But uh oh, we can only pay via card - prepay account and PayPal are blanked out. Shame.Submitting this send all the lovely data to a PHP script hosted on the same box: https://ip-64-202-189-152[.]ip[.]secureserver[.]net/DPD/php/status[.]php5\\n](https://pbs.twimg.com/media/EoY5YfbWMAU_Itu.jpg)


![We've just gained a whole bunch of new domains or compromised sites to sift through, but lets just quickly validate they're hosting the same phishing kit.. yup! A look at one of the requests suggests they even went and registered a domain - dpdlocal-online[.]com9\\n We've just gained a whole bunch of new domains or compromised sites to sift through, but lets just quickly validate they're hosting the same phishing kit.. yup! A look at one of the requests suggests they even went and registered a domain - dpdlocal-online[.]com9\\n](https://pbs.twimg.com/media/EoY-KsEXIAE6NjN.jpg)
![We've just gained a whole bunch of new domains or compromised sites to sift through, but lets just quickly validate they're hosting the same phishing kit.. yup! A look at one of the requests suggests they even went and registered a domain - dpdlocal-online[.]com9\\n We've just gained a whole bunch of new domains or compromised sites to sift through, but lets just quickly validate they're hosting the same phishing kit.. yup! A look at one of the requests suggests they even went and registered a domain - dpdlocal-online[.]com9\\n](https://pbs.twimg.com/media/EoY-KuUXMAAzFZV.jpg)


