ok live thread of fun! i'm doing some sophisticated shit! (not really it's basic bitch stuff but lulz at FABULOUS SOPHISTICATED shit) so we are gonna test a security detection capability. We are doing to log into a high profile mailbox simulating a stolen credential scenario!
so hax so sophicated! brb need to clack clack clack
ok so i stole some creds! 133333333333333333337! Now i'm going to attemp to log in from a country where this user would never ever ever be (as in know where they are)
ok i have mailbox access from half way round the world! i've started to fuck about! 1 x email exfiltrated!
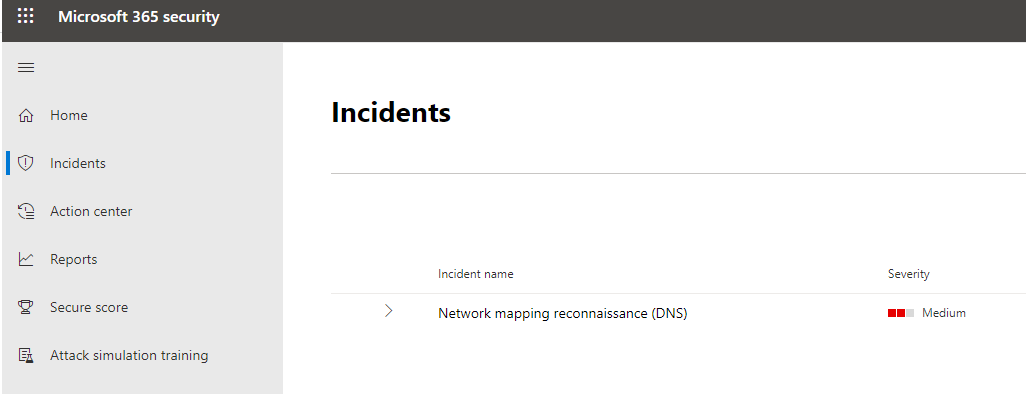
ok runbook BEC activated! To the OFFICE 365 ATP LOGS, SENTINEL LOGS, AD LOGS.. of fuck how many consoles!
no one else has noticed! pew pew goes the hacker frog! now it's Dan Vs Kermie Hax! can i stop him before he exfiltartes too much data???
the only thing here is COMPLEXITY! basic bitch attack.. but HARD AS fuck to even know what console to use! lol
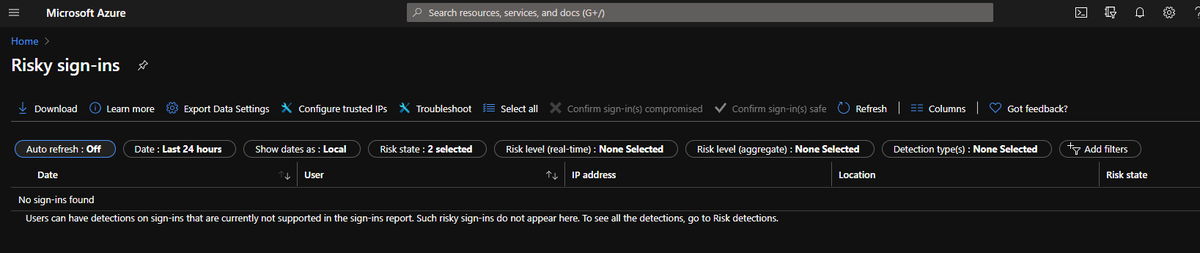
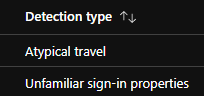
fuck twitte thread diverged. ok so we got to the part where it alerts on a risky but the risky sign in panel is empty. the normal sign in panel has K-Hax in singapore so like that's fucking confusing! but we got him!
ok fuck found sonme data.... the risky sign-ins page DOES NOT show the risky sign in from k-hax! bonkers. anyway we got him on two counts! K-HAX I'm coming for you little buddy!
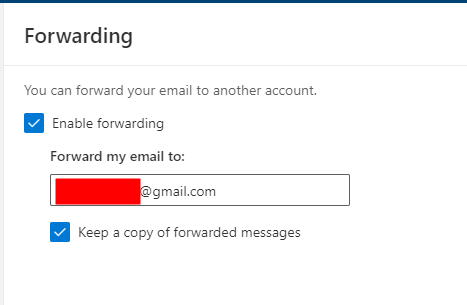
ok so we know i'm playing. me and K have shown that an an alert goes off for this scenario. it also highlights the need for MFA but also that isn't the only action on target. let's enable some forwarding :P coz evil K-HAX :D
and FUCK you cyber crims! the forwading test failed! we were unable to forward emails :P pow! so we detected K-Hax and we blocked the forwarding rule!
So now I've got an exec signed up to MFA. K-HaX thinks he can go again but BAM he is stopped by MFA!
and that my friends is how we walk someone through business email compromise and how we show the customer to enable MFA. Next time we are going to look at how we track more
and that my friends is how we walk someone through business email compromise and how we show the customer to enable MFA. Next time we are going to look at how we track more
So here we are! Happy and safe that we’ve helped move someone one more step forward! Loads more to make but this is how you start to win at security! One step at a time! 













if it was a sophisticated attack i would have come in from an IP near to the customer (if not one of their guest networks or a starbucks etc.), i would have not touched forwarding rules, I would have taken my time, i would have prepared to combat their MFA.

 Read on Twitter
Read on Twitter