BOLO for increased #Qbot activity delivering Cobalt Strike & #Egregor ransomware. If you see Qbot & recon/Cobalt Strike activity, move fast because a ransomware payload may be imminent. Behavioral analytics & detection opportunities in this thread. #RCintel #qakbot
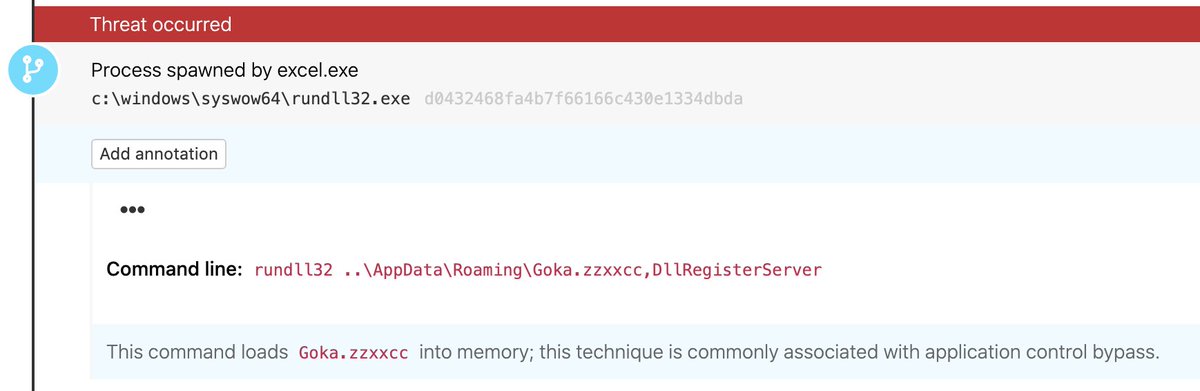
Qbot executes as a DLL using regsvr32.exe and (as of today) rundll32.exe as a child of excel.exe. You can detect Qbot’s use of rundll32 from today by looking for rundll32.exe loading a DLL with the command line including DllRegisterServer.
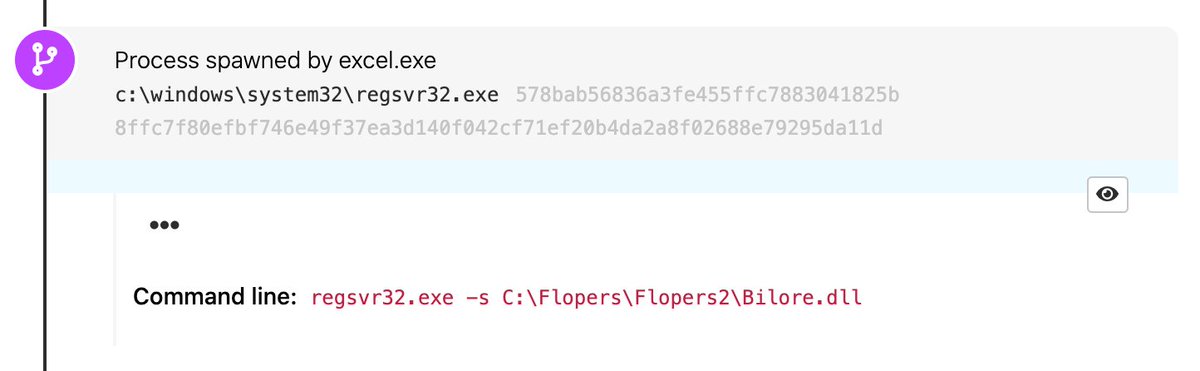
We saw Qbot use regsvr32.exe yesterday. You can detect this behavior by looking for regsvr32 launched as a child process of excel.exe. Additionally, the strings “C:\\Flopers” & “Bilore.dll” appear to be fairly unique.
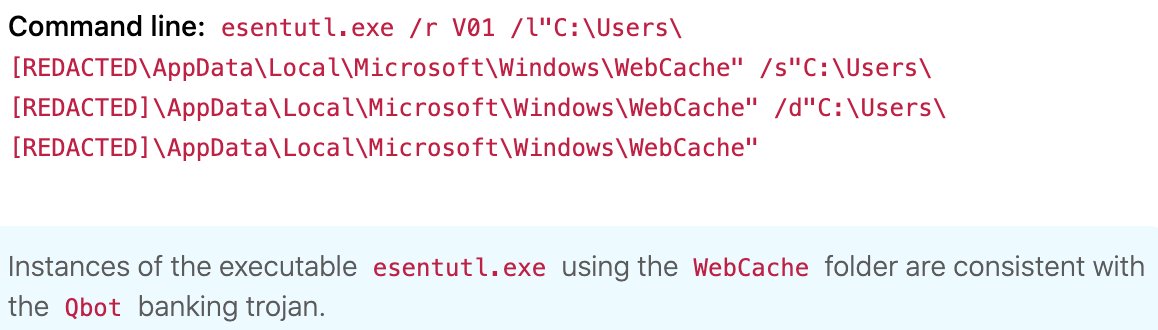
We’ve seen Qbot leveraging esentutl.exe to interact with the Windows web cache directory. Such activity is highly suspicious. You can detect it by looking for a process that is esentutl.exe executing in conjunction with a command line containing the term “WebCache”.
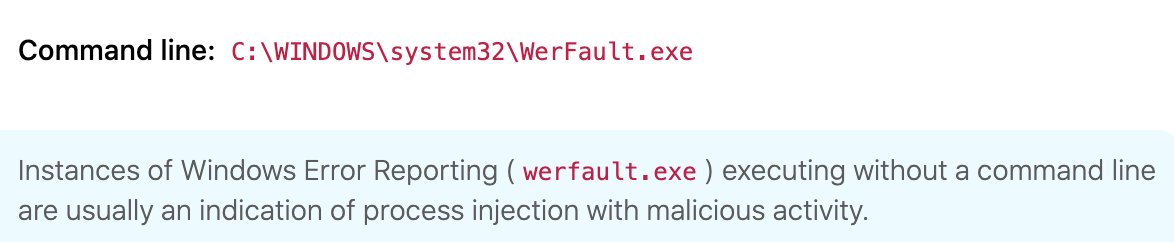
Qbot also injects malicious code into the Windows Error Reporting (werfault.exe) executable to evade detection. You can detect this activity by alerting on the execution of werfault.exe without a corresponding command line.

 Read on Twitter
Read on Twitter