1/ Tonight, we are going to discuss an accusation that vote tabulators in Michigan were connected to the Internet, made by a local radio show guy named Randy Bishop. His first hand testimony is here:
https://www.facebook.com/AnonymousUnitedFB/videos/381032016563540
https://www.facebook.com/AnonymousUnitedFB/videos/381032016563540
2/ The short answer is that no, he didn't see any Internet connection. He saw normal, expected operation of the machines. This is just an example how everything you can't explain is explained by the conspiracy.
3/ What he saw was Ethernet cables connected to a "router", connected to another "router", and then a cable going through a wall.
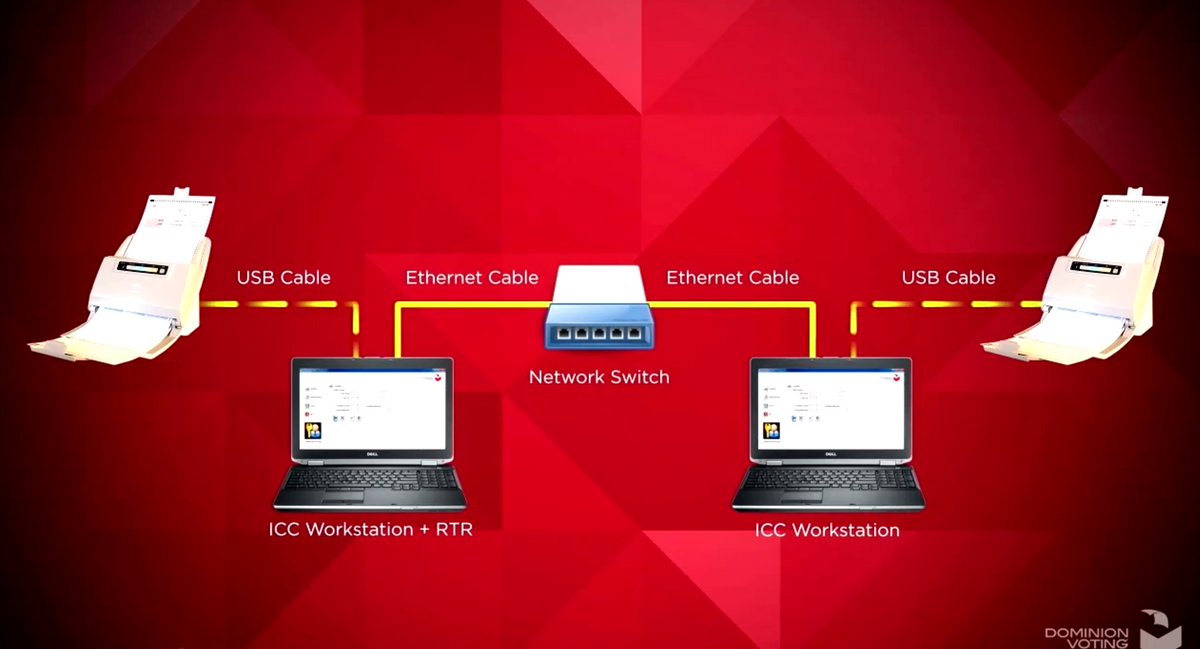
4/ What he describes are rows of scanners connected to desktop computers via USB, as shown here in the brochure from Dominion.
He claims that there's (illegally) Ethernet coming out the back of these computers.
https://www.dominionvoting.com/download/imagecast-central/?wpdmdl=67331&masterkey=5f10715444428
He claims that there's (illegally) Ethernet coming out the back of these computers.
https://www.dominionvoting.com/download/imagecast-central/?wpdmdl=67331&masterkey=5f10715444428
5/ That these are networked LOCALLY is normal, the expected operation of the system, as explained in their training video.
https://www.dominionvoting.com/training/icc-movie/index.html
https://www.dominionvoting.com/training/icc-movie/index.html
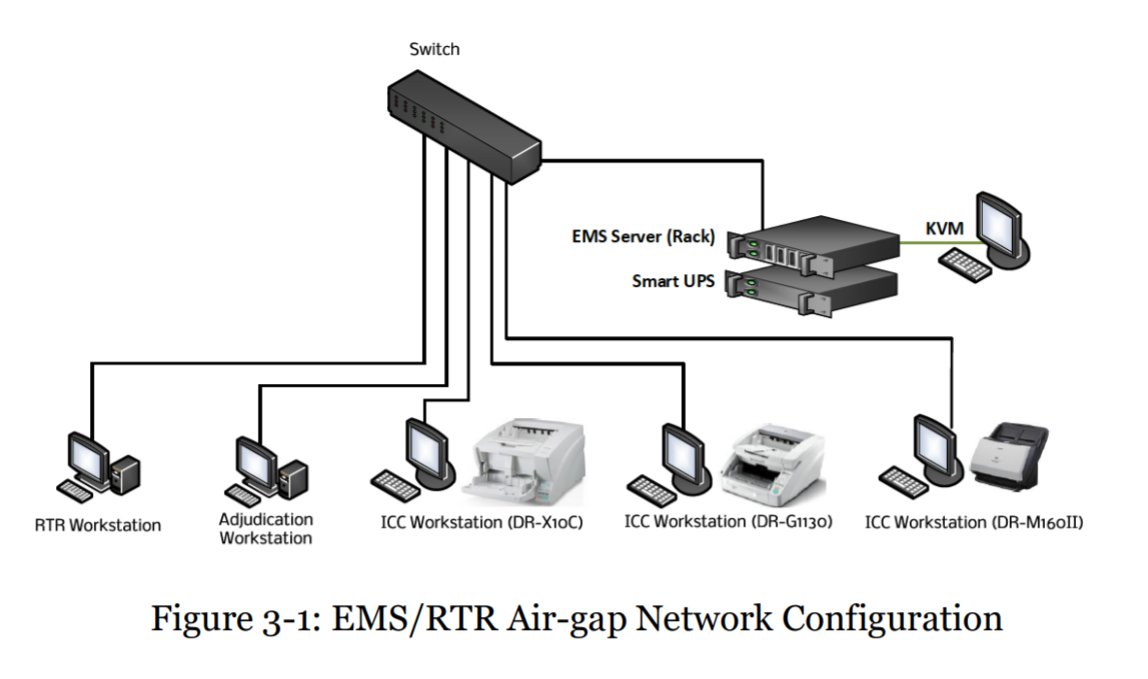
6/ All of these "ImageCast Central (ICC) Workstations" are on the same local Ethernet as the server, as described in the manual. They upload the raw images to the server.
https://votingsystems.cdn.sos.ca.gov/vendors/dominion/ds510-use-proc-jan.pdf
https://votingsystems.cdn.sos.ca.gov/vendors/dominion/ds510-use-proc-jan.pdf
7/ What he describes is how the thing was supposed to work. He didn't cite any evidence that anything was connected to the Internet, just his opinion that if an Ethernet cable exists and goes through a wall, it must go to the Internet.
8/ He describes enormous loops of Ethernet cables, as if this was something unexpected.
No. It was a temporary installation at the local convention center. This is exactly what you expect from such things.
No. It was a temporary installation at the local convention center. This is exactly what you expect from such things.
9/ When you build a permanent installation, installers buy raw cable, cut to precise lengths, and crimp on connectors themselves. When doing temporary installations, they just buy fixed lengths with connectors already on, which err on being too long rather than too short.
10/ I've been to so many conferences in convention centers, like RSAconf, HOPE, Defcon, etc., which huge piles of excess Ethernet cable. This is normality, not a secret plot to cover up a "router".
11/ BTW, the I've tried to do my best of tracking down his raw testimony so you can see it in context, as well as linking directly to source documents, so you can read them for yourself.
12/ Anyway, it's debunked. He saw Ethernet cables. There were supposed to be Ethernet cable. None of his descriptions in any way describe evidence of an Internet connection. QED.
Oh, cool, this image from Elaine Cromie (Getty Images) shows the what things actually looked like, with the blue Ethernet cables:
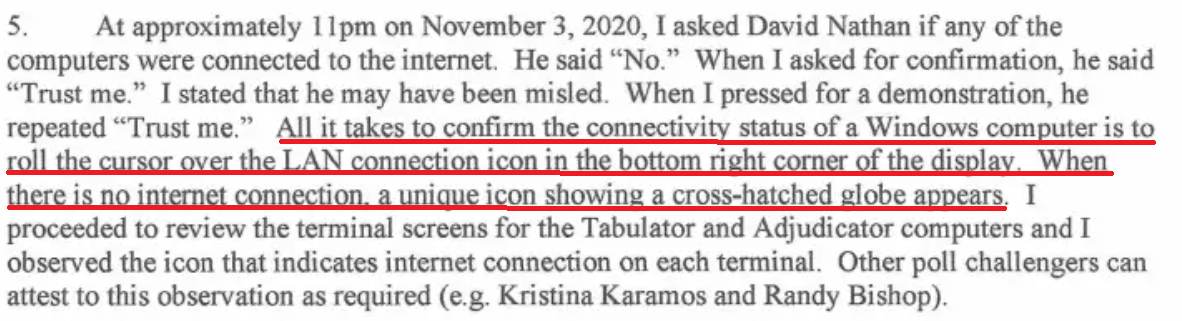
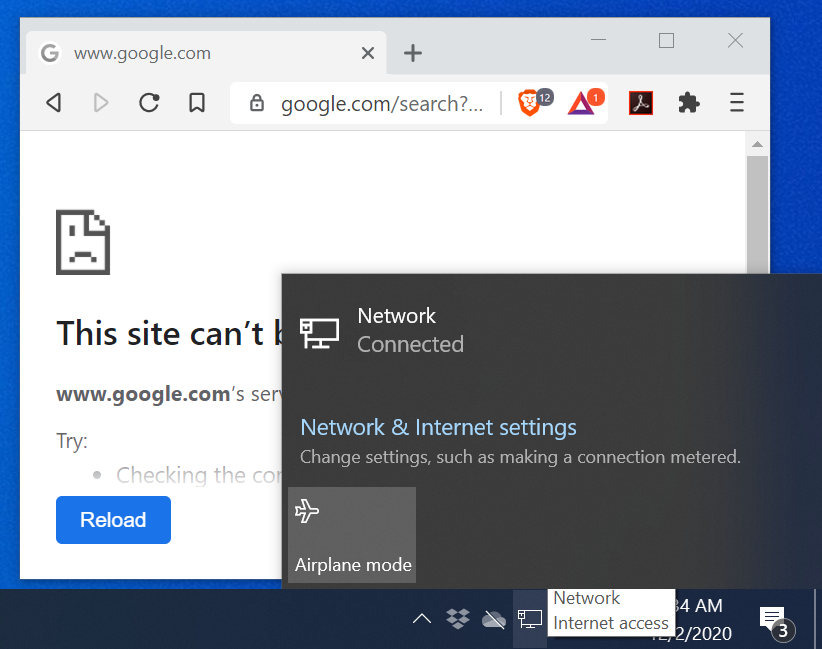
14/ BUT WHAT ABOUT this Colbeck guy who claims that he checked for Internet connectivity, specifically, the absence of the cross-hatched globe indicating Internet connectivity failure.
https://www.scribd.com/document/483570436/Colbeck-Affidavit
https://www.scribd.com/document/483570436/Colbeck-Affidavit
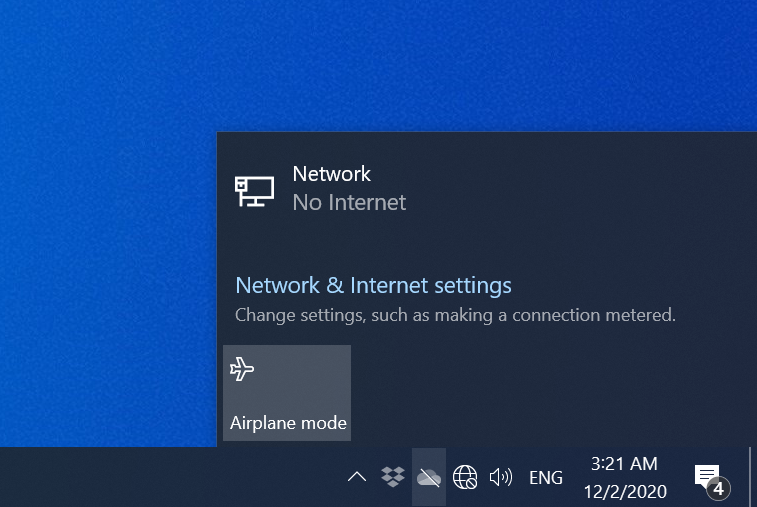
15/ What he's talking about is something that looks like the following. I created this by simply turning my router off and waiting a minute for my Windows desktop to complain about loss of Internet connectivity.
16/ But, this network status indicator can be turned off, as explained in this Microsoft knowledgebase article. It's likely the computers went through much more specialized configuration than just this, it's a typical corporate issue.
https://support.microsoft.com/en-us/help/4494446/an-internet-explorer-or-edge-window-opens-when-your-computer-connects
https://support.microsoft.com/en-us/help/4494446/an-internet-explorer-or-edge-window-opens-when-your-computer-connects
17/ Here's the screenshot of me disabling this, as per the knowledge base article, then again replicating the above problem. As this shows, the browser can't connect, but Windows now falsely claims there's connectivity.
18/ As the manual describes, these aren't generic Windows machines with the software installed. Instead, Dominion provides a complete image of the operating system, preconfigured. You can put the image on a generic computer, but it's not generic Windows
https://votingsystems.cdn.sos.ca.gov/vendors/dominion/ds510-use-proc-jan.pdf
https://votingsystems.cdn.sos.ca.gov/vendors/dominion/ds510-use-proc-jan.pdf
19/ Again, debunked. Again, no evidence. It's just things people don't understand, which they hope might be evidence, but which experts (e.g. me) find completely normal.
20/ "BUT WHAT ABOUT this other thing?"
Is this yet another thing that you don't understand? That you can't defend when I challenge you on it?
If that's the case, then you have your answer.
Is this yet another thing that you don't understand? That you can't defend when I challenge you on it?
If that's the case, then you have your answer.
21/ When we say "no evidence", that means you do understand it, cite references, describe things in specific detail, and defend it against challenge -- they way I have in threads like this.
If you can't, then it's not evidence.
If you can't, then it's not evidence.
22/ "But this expert..."
Show me evidence of their expertise. I mean things like published academic papers, talks at conferences, github accounts, technical blogposts, etc.
Being a colonel in charge of cyberwarfare activities doesn't mean they are an expert.
Show me evidence of their expertise. I mean things like published academic papers, talks at conferences, github accounts, technical blogposts, etc.
Being a colonel in charge of cyberwarfare activities doesn't mean they are an expert.
23/ I mean, our industry is full of people with irregular credentials, so a lot off irregular things I haven't thought of would be acceptable.
There are just too many clueless CISSPs or cyber-military officers to believe that's a credential.
There are just too many clueless CISSPs or cyber-military officers to believe that's a credential.
24/ In any event, my assertions above in this thread are based on anybody being able to reproduce and confirm them. You don't have to trust my expertise.
The expert you cite should similarly show their work.
The expert you cite should similarly show their work.

 Read on Twitter
Read on Twitter