NEW RESEARCH from @citizenlab: 25+ countries have deployments of #Circles phone tracking & interception. They can probably target YOU. Here’s what this means… Quick #THREAD. https://citizenlab.ca/2020/12/running-in-circles-uncovering-the-clients-of-cyberespionage-firm-circles/
NEW RESEARCH from @citizenlab: 25+ countries have deployments of #Circles phone tracking & interception. They can probably target YOU. Here’s what this means… Quick #THREAD. https://citizenlab.ca/2020/12/running-in-circles-uncovering-the-clients-of-cyberespionage-firm-circles/
(2) #SS7 system handles call and text routing between carriers. It can be exploited to send your calls & texts to an attacker. Or track your location. Anywhere. From anywhere. #Circles (part of the NSO 'family') weaponizes these weaknesses as a service. https://en.wikipedia.org/wiki/Signalling_System_No._7
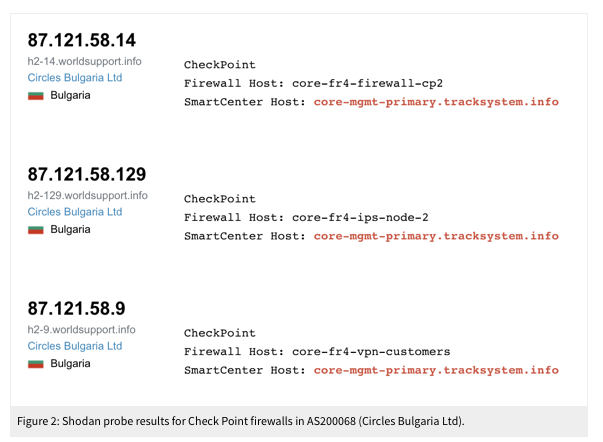
(3) Colleague @billmarczak developed a fingerprint for #Circles deployments by tracking the @CheckPointSW firewalls they used. Leveraged internet scanning, @shodanhq, @censysis, #Fofa & @rapid7.
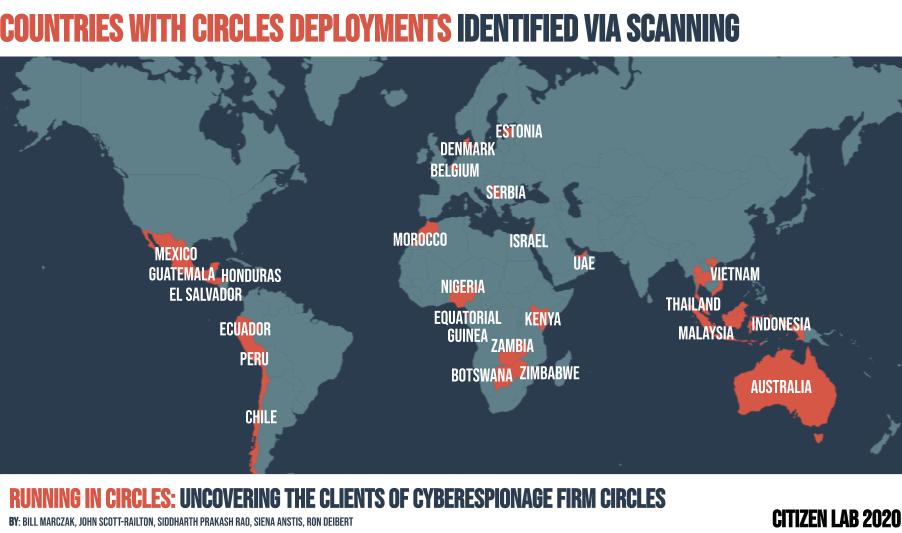
(4) Many serial abusers of surveillance tech & terrible human rights records roll #circles tech. Some may pose national security threats to US/ Canada / EU. Others… to critics & journalists around the world.
(5) Grave concern: two-factor authentication many Govs & businesses still use is vulnerable to #SS7 attack. Critical infrastructure risks & threats to Government operations. https://www.theverge.com/2017/7/10/15946642/two-factor-authentication-online-security-mess
(6) #SS7 vulnerabilities are well known. But governments = glacial. Keep getting captured by telco lobbyists. Result? Our texts, calls and phone locations are vulnerable to anyone who with a checkbook.
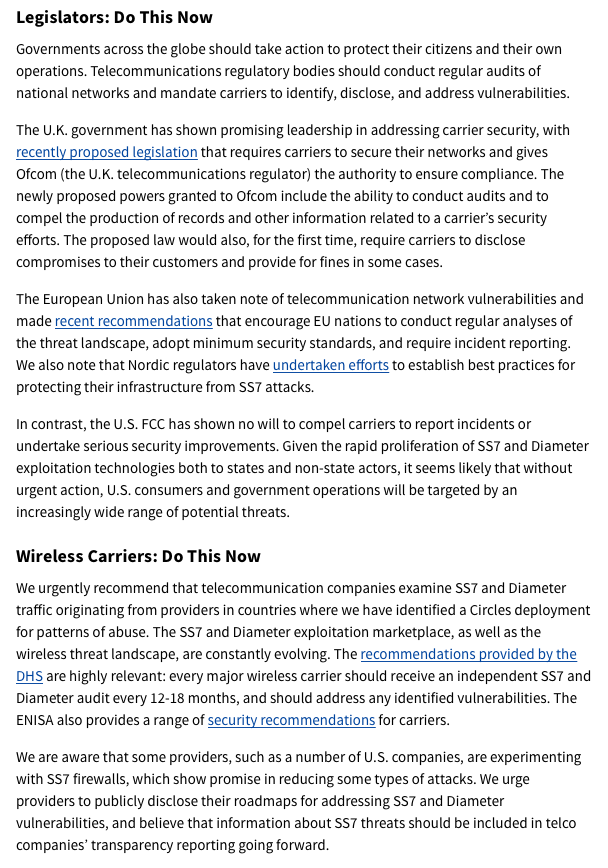
(7) UK @Ofcom showing some leadership. Looks like: mandatory audits of Telcos, compelled notification & more.
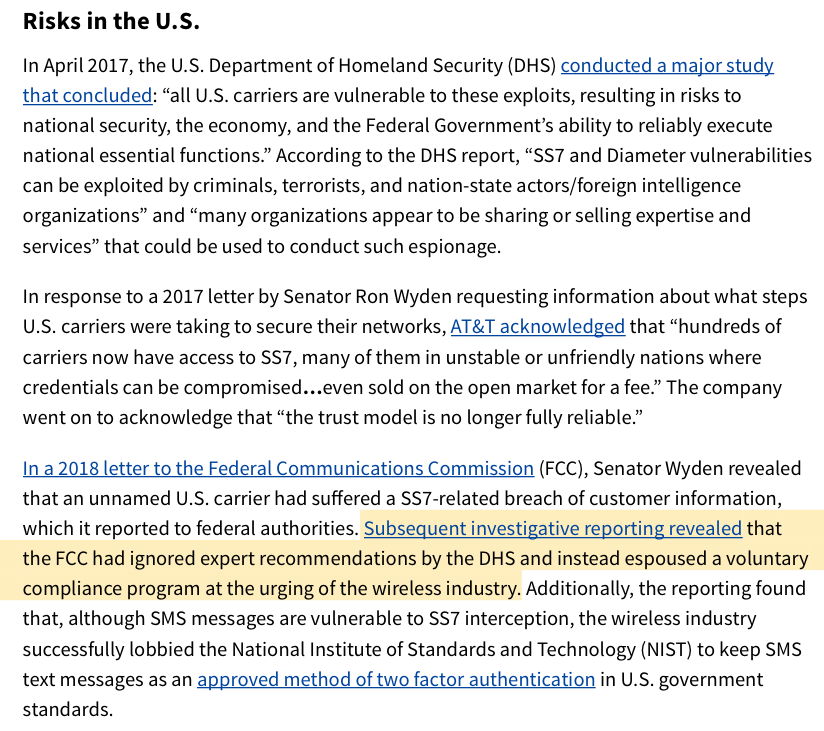
(8) US on the other hand: bad look. @DHS found @att @TMobile @Verizon vulnerable. But @FCC & @AjitPaiFCC sidestepped DHS recommendations & gifted telcos voluntary standards. Failing even so....
(9) Known breaches of SS7 within US per @Wyden. Government daily operations are at risk. Despite obvious peril @NISTcyber standards still include SMS as a 2nd factor for authentication… thanks to industry lobbying.
(10) Saudi Arabia among countries using SS7 to spy on phones WITHIN US. Sound bad? Still 50 days to change your legacy @AjitPaiFCC. https://www.theguardian.com/world/2020/mar/29/revealed-saudis-suspected-of-phone-spying-campaign-in-us
(11) Europe is a mix. EU working groups & @enisa_eu are pushing for improvements, but... majority of EU operators are vulnerable. Nordic countries showing more coherent leadership. https://www.enisa.europa.eu/publications/signalling-security-in-telecom-ss7-diameter-5g
(12) To do now:
-Legislators: Listen to your own experts. Require mandatory audits and notifications.
-Telcos: audit every 12-18 mo for SS7 attacks. Make improvements. Don't hide behind lobbying.
-Legislators: Listen to your own experts. Require mandatory audits and notifications.
-Telcos: audit every 12-18 mo for SS7 attacks. Make improvements. Don't hide behind lobbying.
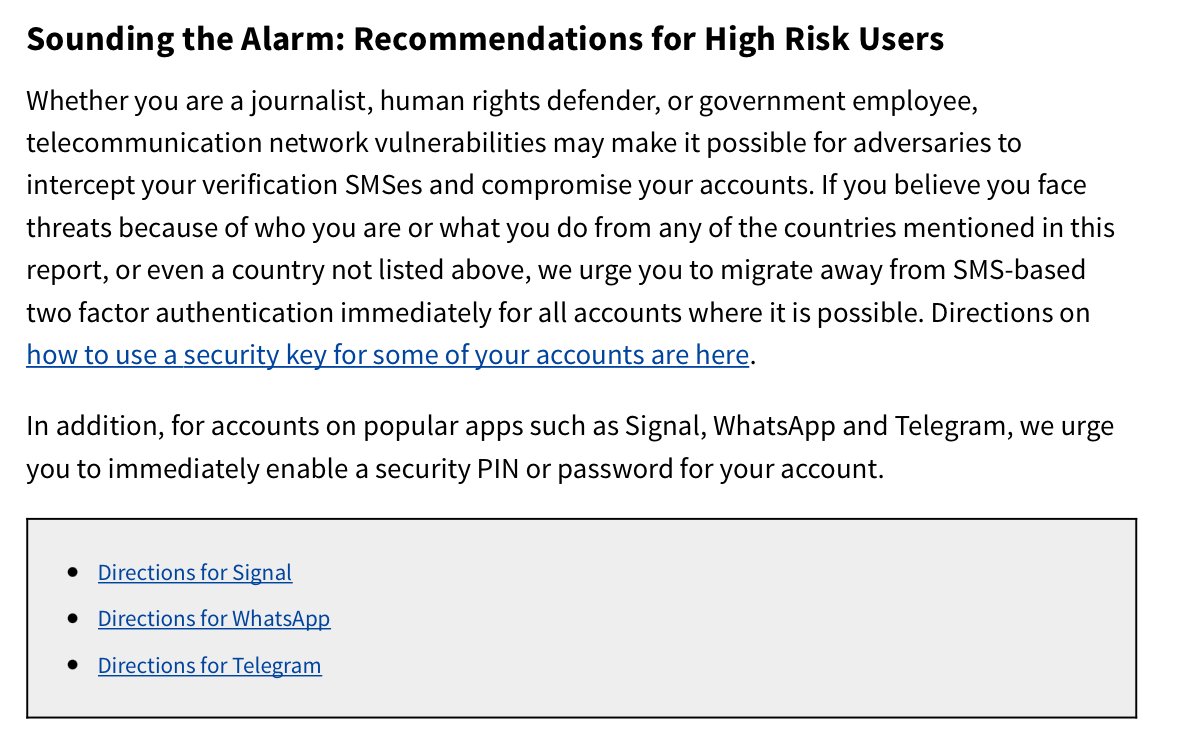
(13) Protect yourself from some #SS7 risks by moving away from texts for verification.
AND, add an additional factor to your messaging apps. Directions:
-Signal: https://support.signal.org/hc/en-us/articles/360007059792-Signal-PIN
-WhatsApp: https://faq.whatsapp.com/general/verification/how-to-manage-two-step-verification-settings/?lang=fb
-Telegram: https://telegram.org/blog/sessions-and-2-step-verification
AND, add an additional factor to your messaging apps. Directions:
-Signal: https://support.signal.org/hc/en-us/articles/360007059792-Signal-PIN
-WhatsApp: https://faq.whatsapp.com/general/verification/how-to-manage-two-step-verification-settings/?lang=fb
-Telegram: https://telegram.org/blog/sessions-and-2-step-verification
(14) PSA: Check out lead author @billmarczak's detailed thread & follow our coauthor @sidnext2none for research on telco security https://twitter.com/billmarczak/status/1333850197936414721

 Read on Twitter
Read on Twitter