A thread on Dominion Democracy Suite. The US president is currently claiming that the electronic voting systems used in a number of states have been hacked, let's explore that possibility by looking at documents related to the environments and potential attack paths.
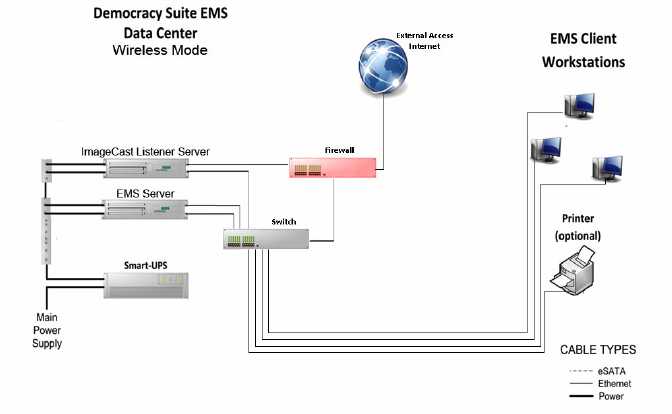
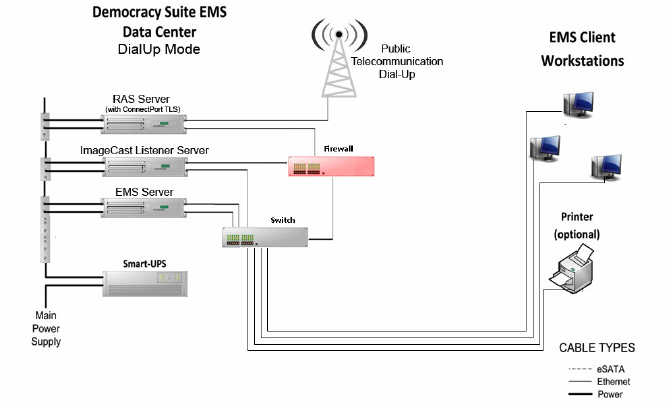
The above is a high-level block diagram of how the election networks are built and configured when Dominion Voting Suite is used. Before we look at potential places to install a backdoor, let's first take a look at the Election Management System (EMS).
Looking at configuration guides, see that software typically deployed in EMS for managing/monitoring an elections is out-of-date. Servers could be vulnerable to MS07-010 and the database components are typically legacy SQL servers, with a number of easily exploited components.
This type of environment wouldn't pose much of a challenge to low-skilled adversaries, and interestingly there is a "RAS" solution for providing remote connection which is a actually a commercial solution for remote RS-232 et all terminals - https://www.digi.com/products/networking/infrastructure-management/serial-connectivity/serial-device-servers/connectportlts
Moving on from the abysmal security in the EMS itself, the actual paper voting systems which are counted through an electronic tabulation machine are also very intriguing to the attacker. This is a "Dominion ImageCast ICP Tabulator", it's used for counting and verifying votes.
It's a perfect target for backdoors, thus it's getting alot of attention. The overall system design is interesting, it has number of FPGA's and peripherals for the counting sensors, CompactFlash card to store the result data and has a detachable modem for sending vote data to EMS
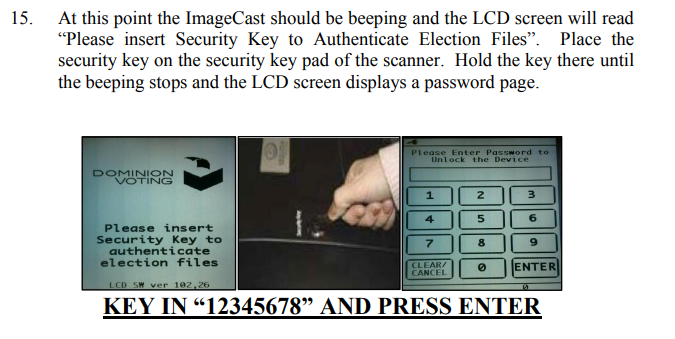
When an Administrator or Superuser (a Dominion Tech) wishes to reprogram the device or open/close the polls, they will use a commercial "iButton" which is a wireless RFID type key and an 8 digit pin code, which can be insecure values like 12345678. iButton's use SHA-1 or nothing.
There are so many different ways that someone could hack into a state using Dominion Democracy Suite, the XML posts for instance could contain XML Entity Injection for displaying the results on websites - but the crown jewels would be a backdoor on the tabulation machine.
A backdoor on the tabulation machine, which could be placed there from the EMS, modem (wardial much?), or by a malicious insider would be able to falsify voting dater that is later sent out to the rest of the world to falsely declare a winner. Election guru's thought of this too.
The device holds the ballets underneath in a secure storage which can be removed and then a manual count process undertaken to ensure that how the public voted is the same as how the electronic systems tabulated the results. Absentee ballots are more open to manipulation.
I have previously said paper based voting with no electronic components is the way to go and thread further compounds my views on the matter. I also believe that an independent review of the ballots and systems should be undertaken to prove or disprove cyber enabled voter fraud.
It doesn't look particularly challenging to tamper with a federal election in light of the vulnerabilities outlined here, it's more concerning that such an attack may go unnoticed unless the ballots are reviewed, the systems cannot be trusted in anyway but frequently are.

 Read on Twitter
Read on Twitter