When asking investigative questions, lots of folks tend to focus on behavioral things whose answer will only provide some subtle indicator of malice. This may lead to a lot of misplaced effort when there are better approaches. For example... 1/
Consider an alert for a malware family based entirely around a suspiciously formatted DNS query. A lot of analysts might dig into DNS: "Was the request successful?" or "Was the communication to IPs that the domain resolves to?", or "What was the frequency of the request?" 2/
These are fine questions, and you may have to answer them later if there is a confirmed infection. But, is that where you start? Remember, at this point, you're trying to decide whether the alert is true or not. Namely, is this malware on the machine? 3/
A quicker approach might be to perform an internet search and identify some other characteristics of the malware.
Which of those other features can you most readily identify on the network or host? Presence of a file, other network activity, a running/executed process, etc. 4/
Which of those other features can you most readily identify on the network or host? Presence of a file, other network activity, a running/executed process, etc. 4/
The alert only tells you that there is an indicator of the malware's presence. Now, you need to find one or two more. Their presence (or lack thereof) can help you quickly dispose the alert. 5/
If the malware is there, then you can move on to characterizing the other portions of the timeline -- what leads to the infection? what happened afterward? 6/
Googling malware families and identifying these characteristics feels like extra work because you're not actually digging through data. The truth is that you frontload the work here so you only have to make one or two highly efficient inquiries into data. 7/
New analysts resist this level of effort because it seems scattered and annoying. That gets much easier as you do more of it.
A big part of the work of the analyst is this sort of research, doing it efficiently, and being willing to do it frequently. 8/
A big part of the work of the analyst is this sort of research, doing it efficiently, and being willing to do it frequently. 8/
You can practice this too! Pick a rule (Suricata, Sigma, whatever) that references a feature of a malware family.
Now, do some research and find two more features you could quickly test for to prove or disprove that malware is on a system. 9/
Now, do some research and find two more features you could quickly test for to prove or disprove that malware is on a system. 9/
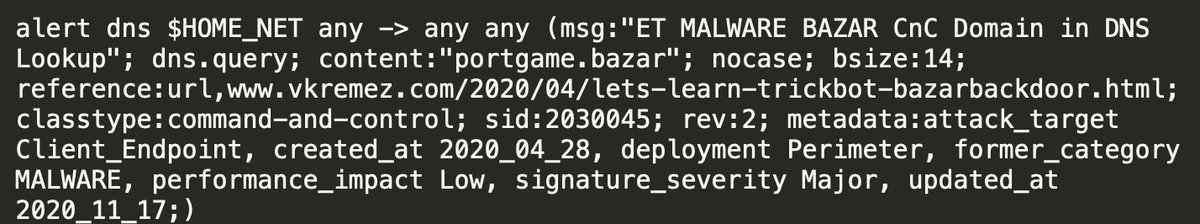
As a matter of fact, here's a Suricata signature for Bazar. Now, what is something else you could look for (not related to this specific domain) to prove/disprove the existence of this malware on a host?
10/10
10/10
(And if you take my Investigation Theory class, you can practice it, get my direct feedback, and I'll push you to ask better investigative questions.)
11/10
11/10

 Read on Twitter
Read on Twitter