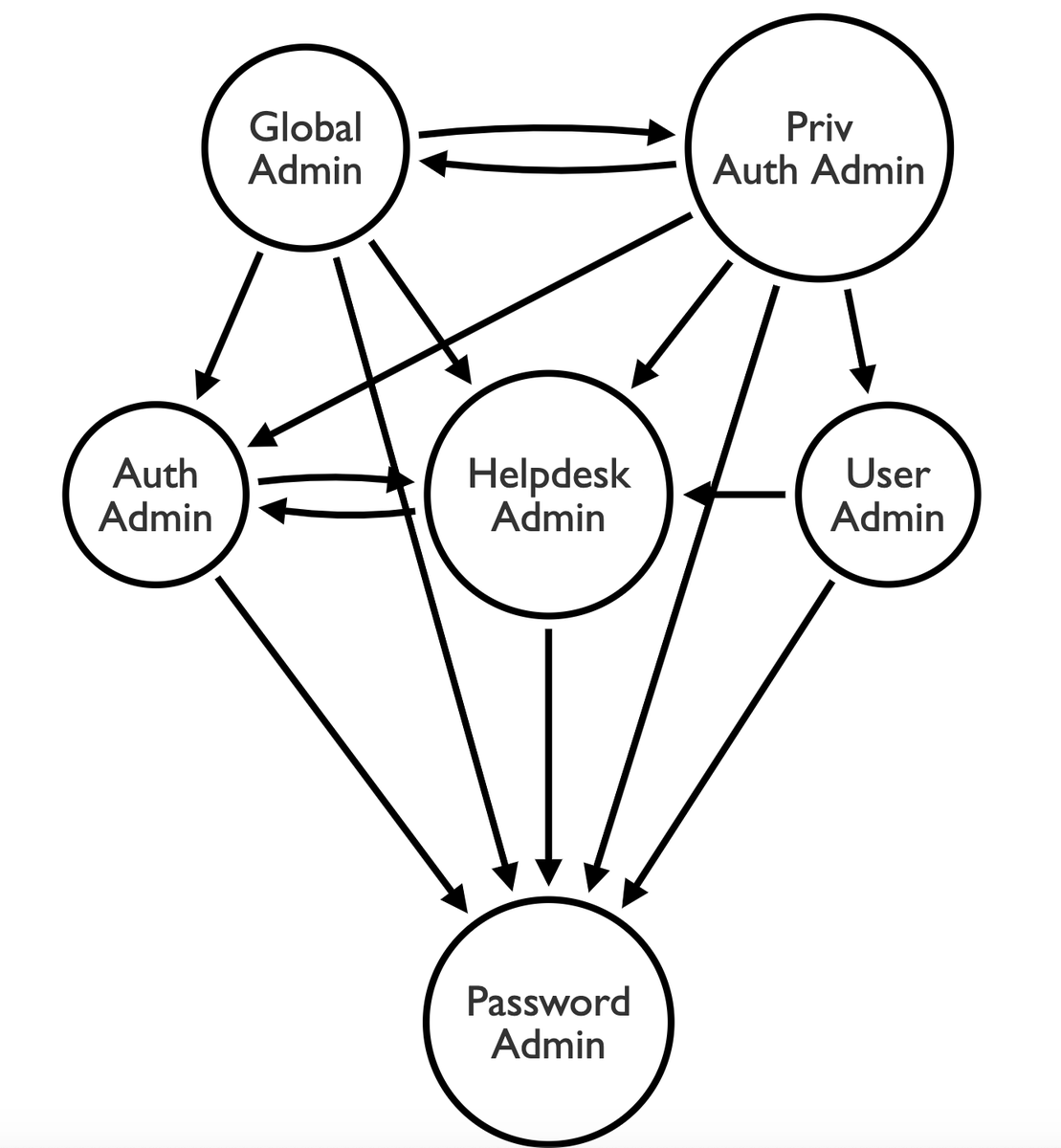
So what happens when we view this as a graph? If we model each node as a node and password reset rights as an edge, then view nodes in descending order of outbound edges (most privileged at top, least privileged at bottom, relative to each other), we learn a few things: https://twitter.com/_wald0/status/1327339539782897664
(2/5) 1. "Tier 0" roles like Global Admin and Priv Auth Admin are well-protected in this model.
(3/5) 2. "Tier 1" roles may not immediately be able to reset each others' passwords, but can through transitive control (attack paths) - User Admin can't directly reset an Auth Admin's password, but can reset a Helpdesk Admin's password and THEN reset an Auth Admin's password.
(4/5) 3. The "Password Admin" role (in and of itself) isn't enough to escalate up to Tier 1 or 0. For that matter, neither are the Tier 1 roles for esclating up to Tier 0. This model, while confusing, offers built-in protection against privilege escalation - when viewed by itself
(5/5) @JohnLaTwC said it best: "Defenders think in lists. Attackers think in graphs. As long as this is true, attackers win." See the whole graph and how you as a defender can effectively and easily audit attack paths in your Azure tenant: Register here: https://specterops.io/so-con2020/event-758916

 Read on Twitter
Read on Twitter