How to build a secure and dependable Internet of Things?
I presented #InfluxDays yesterday about scaling trust in IoT & how we can build systems that put #ZeroTrust in weak network boundaries.
Twitter summary & some demos 1/n
@InfluxDB #InfluxDB
I presented #InfluxDays yesterday about scaling trust in IoT & how we can build systems that put #ZeroTrust in weak network boundaries.
Twitter summary & some demos 1/n
@InfluxDB #InfluxDB
It's been obvious for years that the digitization of the physical world
— or the Internet of Things — opens up tremendous potential and opportunities, across industries.
But ... 2/n
But ... 2/n
IoT, so far has struggled (failed?) to show business leaders that IoT based data and automation is dependable.
Something is fundamentally wrong ... it is too difficult and too expensive to build/maintain secure and private #IoT systems.
We need better development tools.
3/n ..
Something is fundamentally wrong ... it is too difficult and too expensive to build/maintain secure and private #IoT systems.
We need better development tools.
3/n ..
The assumption that all systems and traffic within a network boundary can be trusted is flawed.
Here's a connected switch, anyone on my home wifi can send it these messages & it will turn ON/OFF. A lot of IoT is built with implicit trust in the network it is deployed in
4/n ..
Here's a connected switch, anyone on my home wifi can send it these messages & it will turn ON/OFF. A lot of IoT is built with implicit trust in the network it is deployed in
4/n ..
We know, from experience, this network boundary based security model doesn't scale to modern needs. Even the most well funded, mature IT departments are abandoning it- Google's BeyondCorp.
Home networks don't stand a chance, Industrial networks get it wrong all the time.
5/n
Home networks don't stand a chance, Industrial networks get it wrong all the time.
5/n
My favorite example, of this, is a talk from @cybergibbons about weaknesses exposing drilling control at an oil rig, quote: "A lot of people say their Industrial Control Systems are air-gapped but what they mean is they think they are air-gapped"
6/n
6/n
For dependable IoT / IIoT we must build systems that
• place #ZeroTrust in network boundaries,
• instead *build trust in entities at the application layer*
7/n ..
#IoT #IIoT #Security
• place #ZeroTrust in network boundaries,
• instead *build trust in entities at the application layer*
7/n ..
#IoT #IIoT #Security
Build trust in entities at the application layer.
Security, Privacy and Trust are application layer concerns, IoT devs need app layer tools to easily reason about the trustworthy-ness of each individual message - a sensor reading, a control instruction, a software update.
8/n
Security, Privacy and Trust are application layer concerns, IoT devs need app layer tools to easily reason about the trustworthy-ness of each individual message - a sensor reading, a control instruction, a software update.
8/n
Build trust in entities at the application layer.
Simple functions to:
1. Safely provision, store, rotate, revoke keys at scale.
2. Establish end-to-end encrypted channels.
3. Easily issue, exchange, revoke credentials at scale.
Open Source Ockam
http://github.com/ockam-network/ockam
9/n
Simple functions to:
1. Safely provision, store, rotate, revoke keys at scale.
2. Establish end-to-end encrypted channels.
3. Easily issue, exchange, revoke credentials at scale.
Open Source Ockam
http://github.com/ockam-network/ockam
9/n
These are the open source tools that we're building at Ockam.
The project is heavily in development, if you're interested in dependable IoT, come help us build its foundation.
http://github.com/ockam-network/ockam
We're eager to learn about your real world IoT security challenges.
10/n
The project is heavily in development, if you're interested in dependable IoT, come help us build its foundation.
http://github.com/ockam-network/ockam
We're eager to learn about your real world IoT security challenges.
10/n
Our approach is to use proven cryptographic primitives to build a coherent suite of IoT specific protocols that are available as simple functions – functions that are easy to use correctly and hard to misuse.
http://github.com/ockam-network/ockam
11/n
http://github.com/ockam-network/ockam
11/n
Our secure channel design is based on the noise framework, is transport protocol agnostic & combined with our application layer routing provides mutually authenticated, end-to-end encrypted channels that can span multiple transport layer connections
http://ockam.io/learn/concepts/secure_channels
12/n
http://ockam.io/learn/concepts/secure_channels
12/n
Our enrollment protocol design uses Signal style X3DH to provide an asynchronous bootstrap of trust, to quickly enroll tens of thousands of devices.
http://ockam.io/learn/concepts/enrollment
13/n
http://ockam.io/learn/concepts/enrollment
13/n
In our credentials protocol design we're considering using short group signatures and privacy pass to enable easy functions to exchange anonymous credentials in a variety of authorization and access control scenarios that are common in IoT
http://ockam.io/learn/concepts/machine-identities-and-credentials
14/n
http://ockam.io/learn/concepts/machine-identities-and-credentials
14/n
All of this is based on open research and libraries by several accomplished cryptographers
If you're interested in applying cryptographic tools to improve the physical connected systems around us, come contribute to the code or help us improve our design http://github.com/ockam-network/ockam
If you're interested in applying cryptographic tools to improve the physical connected systems around us, come contribute to the code or help us improve our design http://github.com/ockam-network/ockam
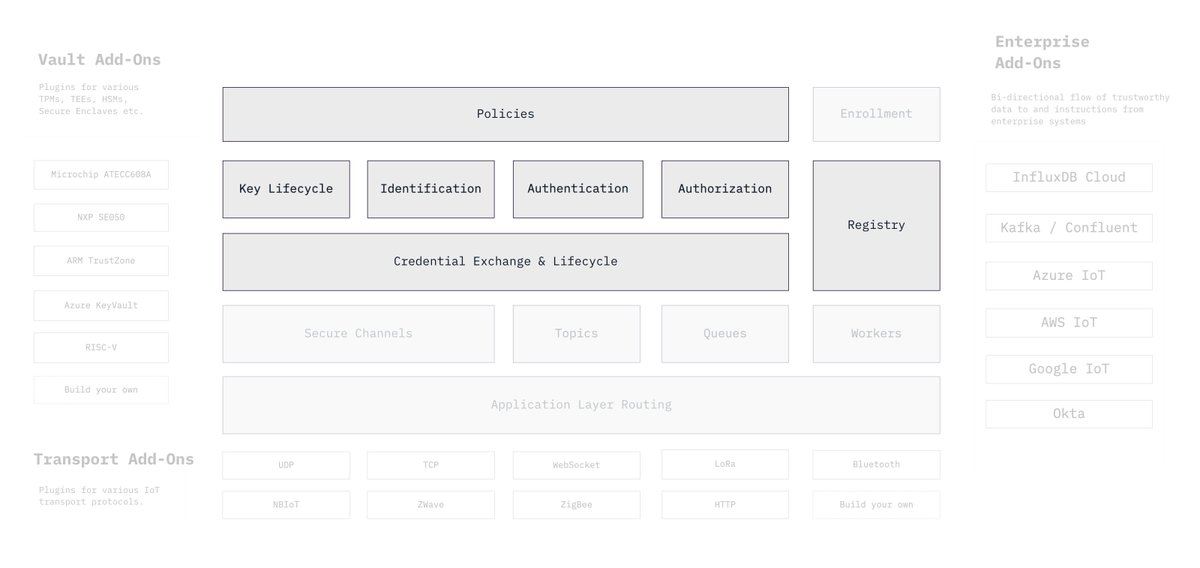
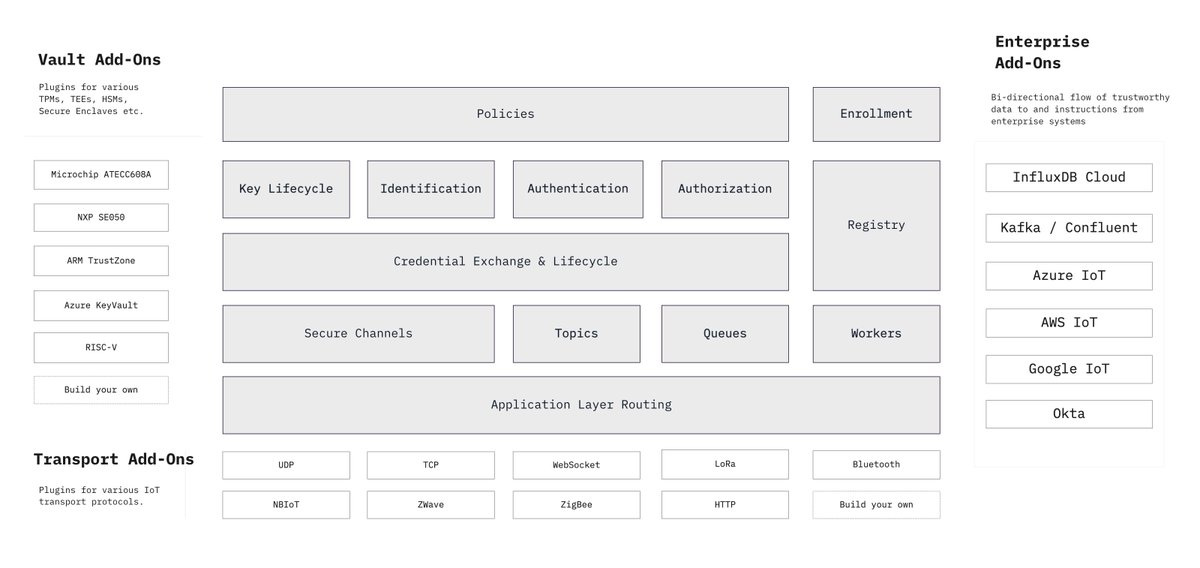
Our goal has been to make our suite of security protocols pluggable into the growing IoT ecosystem with Ockam Add-Ons:
1. Vaults - add-ons for TEEs. TPMs, HSMs etc.
2. Transports - add-ons for IoT transport protocols
3. Add-ons for enterprise systems
http://github.com/ockam-network/ockam
1. Vaults - add-ons for TEEs. TPMs, HSMs etc.
2. Transports - add-ons for IoT transport protocols
3. Add-ons for enterprise systems
http://github.com/ockam-network/ockam
At #InfluxDays yesterday we previewed add-ons for Telegraf and @InfluxDB to enable end-to-end encrypted flow of data from devices running Telegraf to the InfuxData TICK stack.
Here's some demos you can try:
https://www.ockam.io/learn/how-to-guides/using-add-ons/enterprise/influxdb/telegraf-influxdb-with-ockamd/
#InfluxDB
Here's some demos you can try:
https://www.ockam.io/learn/how-to-guides/using-add-ons/enterprise/influxdb/telegraf-influxdb-with-ockamd/
#InfluxDB
Here's another demo that you can try that shows tunneled end-to-end encrypted channels.
http://ockam.io/learn/how-to-guides/using-add-ons/enterprise/influxdb/connect-and-use-ockam-hub/
http://ockam.io/learn/how-to-guides/using-add-ons/enterprise/influxdb/connect-and-use-ockam-hub/

 Read on Twitter
Read on Twitter