My Nintendo Game and Watch arrived a day early! Let’s tear it down and see how it works - and how easy it is to hack it!
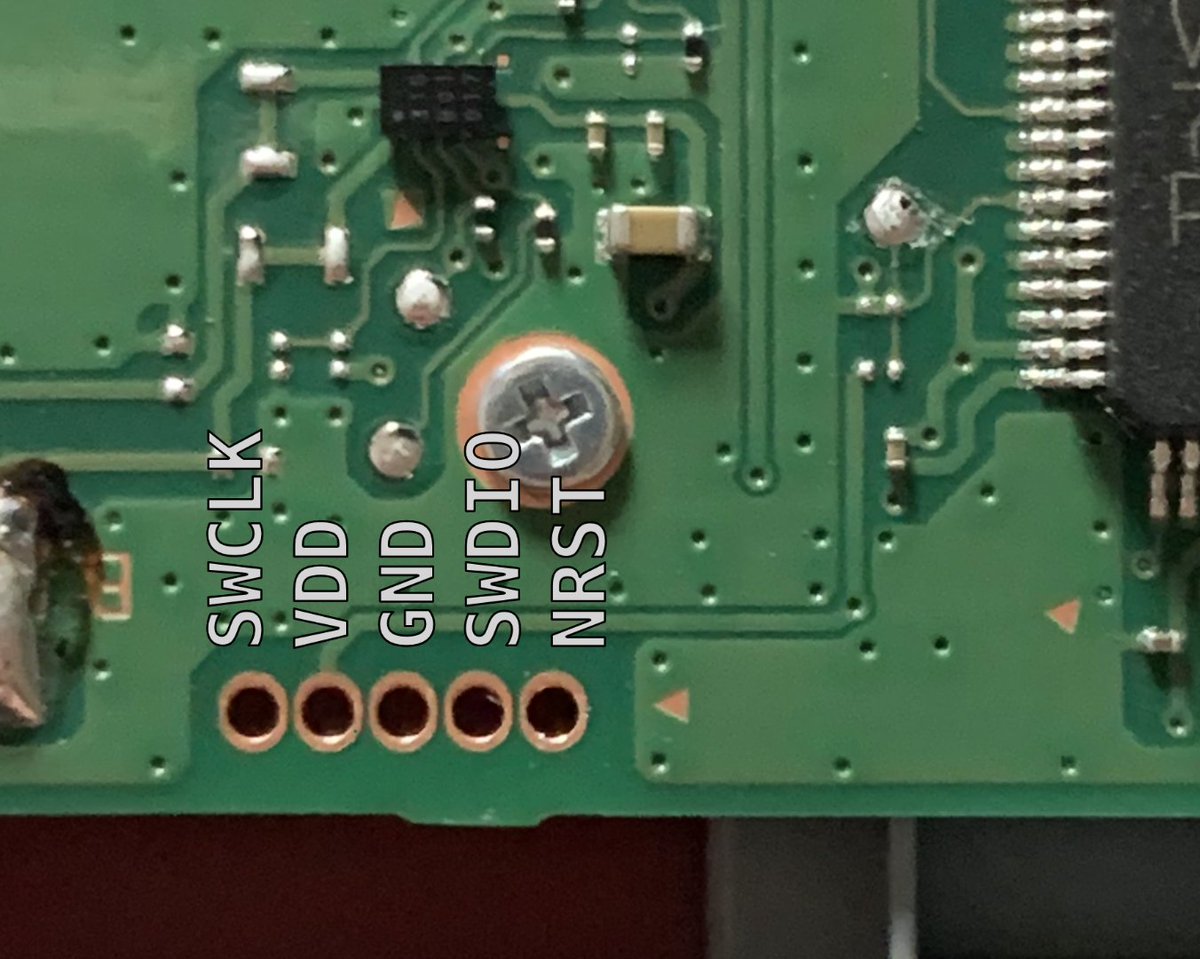
Interesting, an STM32H7B0VBT6 is the main processor! Cortex-M7, 128 KBytes Flash, 1024 KBytes of RAM. Also some unpopulated headers close by that expose SWD (the Arm Cortex-M debug interface)!
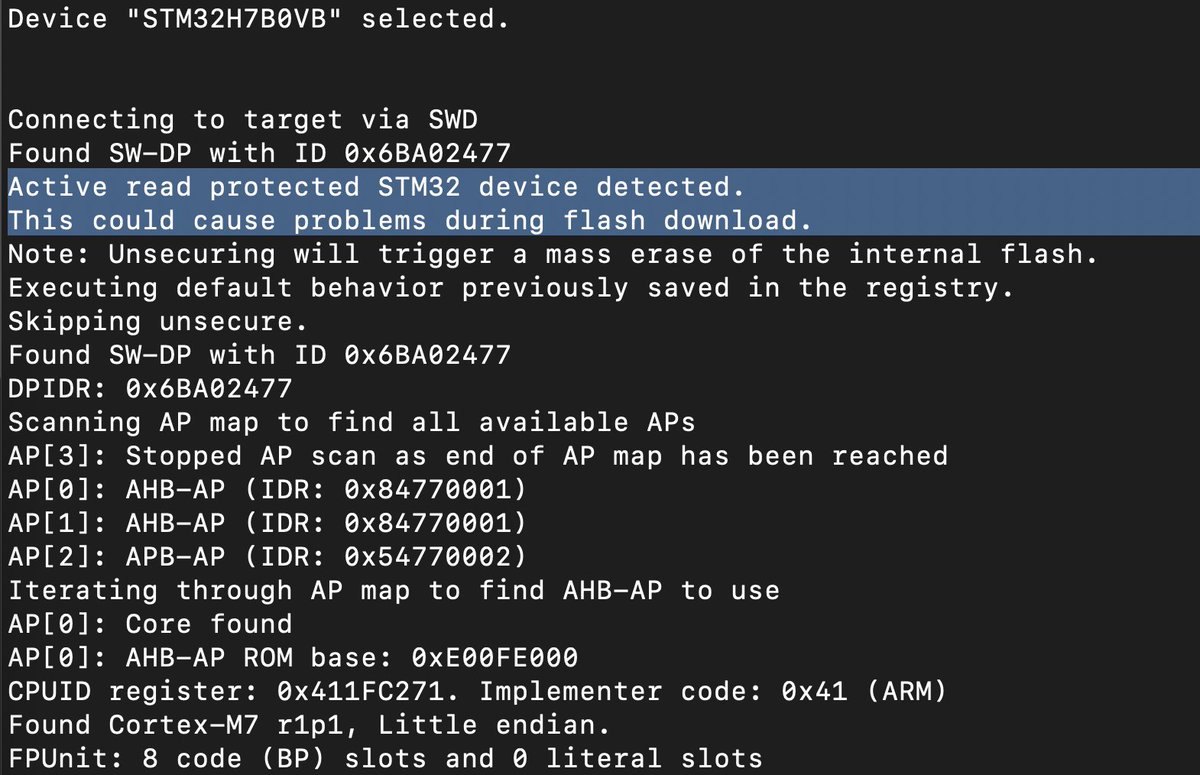
SWD is enabled, but the device is secure unfortunately, so we can't simply dump the firmware via SWD!
Thought I bricked it for a second, but removing the battery (the connector lifts UP!) fixed it *phew* - time to dump the flash!
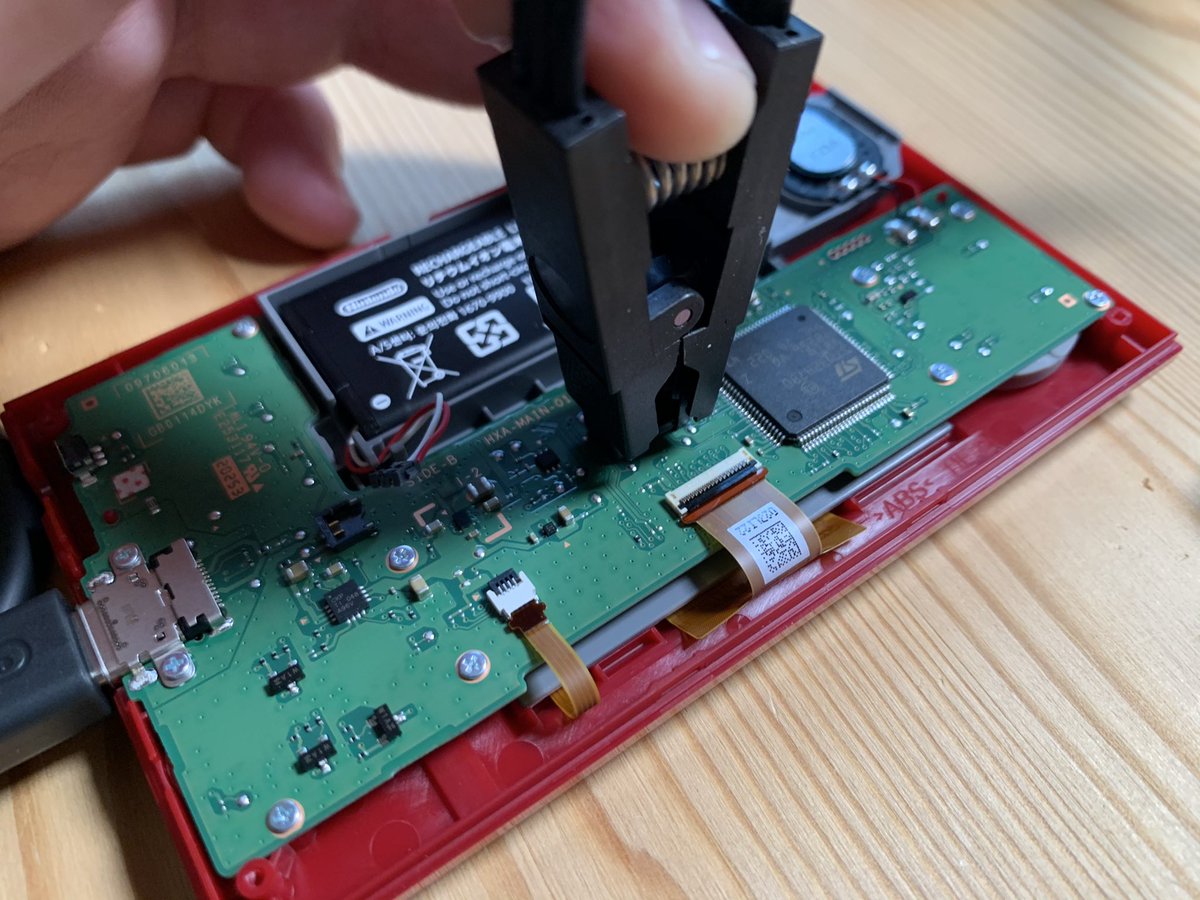
Dumped the flash using a Minipro and a SOIC8 clip - works in system! (Though I had the battery unplugged)
Checksums for those playing along at home:
MD5: 1f5a35ca9b4e6439639c70a01a113620
SHA256: e3a59ee061cd730957b17a34cde5575e49ef24168188b602ca317e8e1f3403fe
MD5: 1f5a35ca9b4e6439639c70a01a113620
SHA256: e3a59ee061cd730957b17a34cde5575e49ef24168188b602ca317e8e1f3403fe
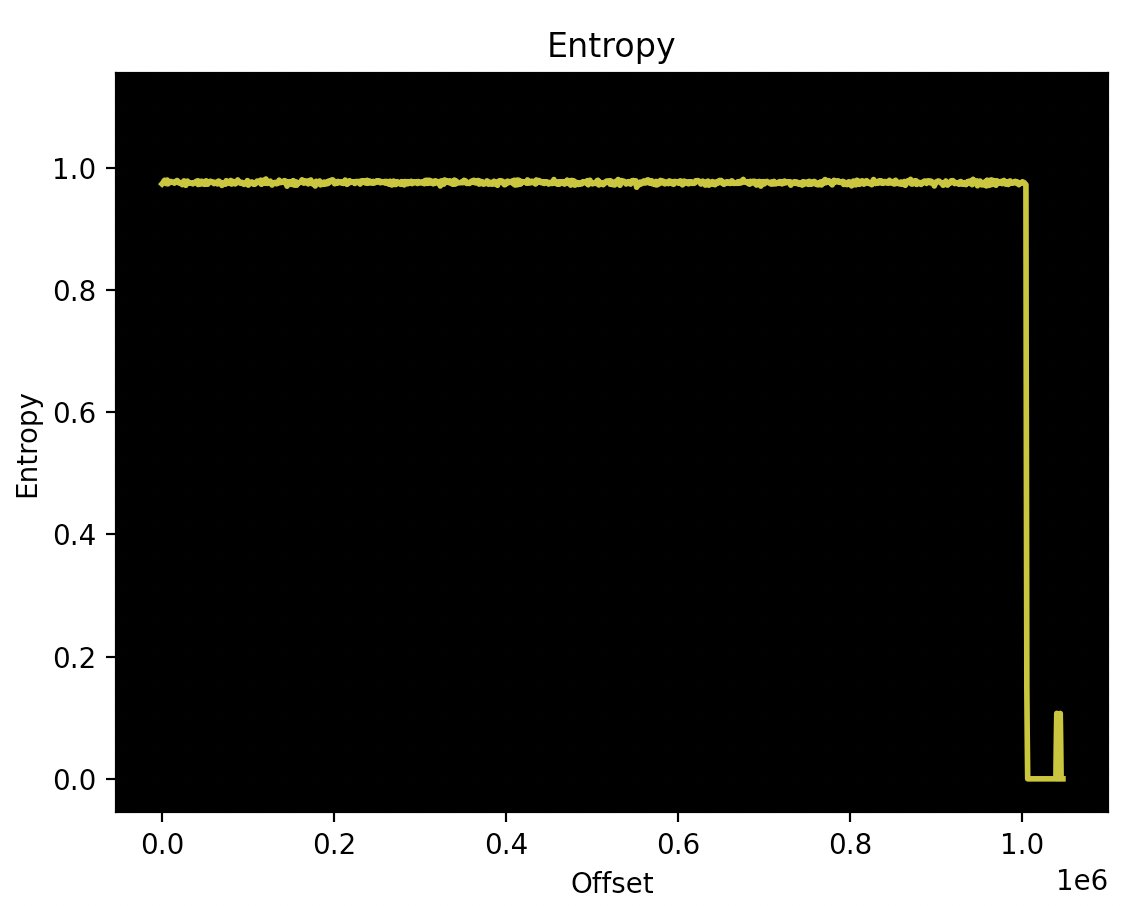
Checking the entropy of the dump it seems like it might be encrypted or compressed - no strings, no knows compression headers. Have to keep digging!
Soo.. Should I try to use a fault injection attack to gain access to SWD, which will risk bricking it?
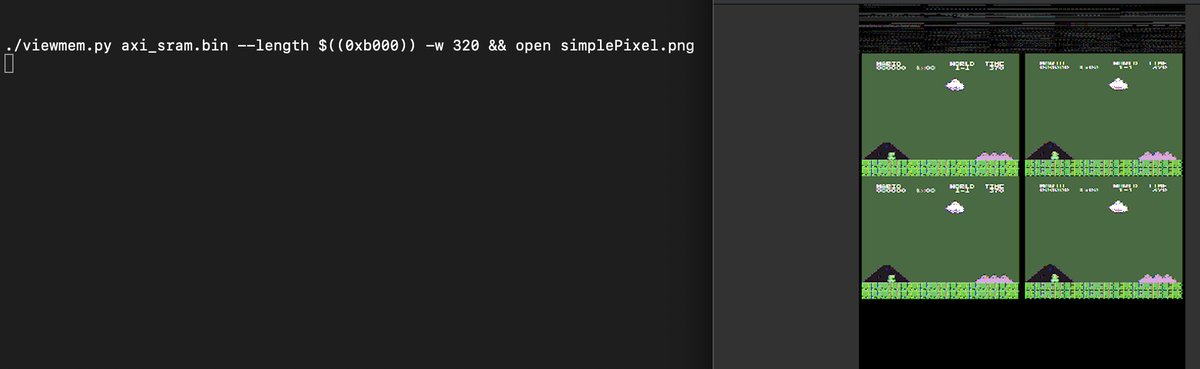
Awesome, seems like it loads a Super Mario Bros. NES ROM into RAM (device RAM contents left, original Super Mario Bros. ROM right)
Tried some simple stuff such as AES ECB with every possible key from the RAM contents, but no luck yet!
Some somewhat good news: I flipped some bits in the flash image and the device still boots. So no strong flash validation!
So, eventually managed to bypass the Game & Watch ROM encryption 1 day before the official release  Will try to release a video on it in the next few days with details on how that works!
Will try to release a video on it in the next few days with details on how that works!
 Will try to release a video on it in the next few days with details on how that works!
Will try to release a video on it in the next few days with details on how that works!

 Read on Twitter
Read on Twitter