I received an odd pop-up yesterday morning. I misclicked a link on Google, and was informed I needed to update Flash for Safari! Oh my stars, it seems Flash is attacking from beyond the grave. Naturally, curiosity got the best of me. #FlashIsDead
This took me to another official looking site: clearly this must be an Apple-mandated update given how real this looks. (Note: if I wasn't some asshole looking for threads to pull at, this would actually look scarily legit, and probably tricks a lot of people).
Finally, when you download the malware, you get this helpful set of instructions on how to enable their dropper to do its work. Clearly these folks have invested heavily in User Experience testing! #UX #JIRATicketPlease
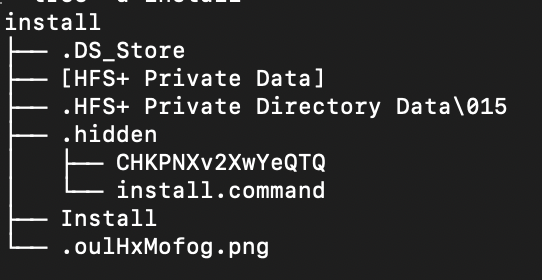
Once downloaded, I shuttled the DMG file off to a Linux analysis VM. A quick trip through dmg2img, then using p7zip gave me the contents of the dmg. Of course the .hidden directory is of interest. The Install script just references install.command hidden there.
This is a sophisticated installer... everything obfuscated! Of course, with some quick work, the install script was revealed to be a call to openssl enc. The key to wrap the command was simply the file name itself, then the file is unwrapped (using the same key, the same command)
Of course, this leaves us with many hours of staring at #Ghidra! This particular malware:
1. Was written in C++ (by some C programmers)
2. Is designed to hide its imports (i.e. uses dlopen/dlfcn/dlclose)
3. Works like a shell script (lots of calls to popen(3), system(2)).
1. Was written in C++ (by some C programmers)
2. Is designed to hide its imports (i.e. uses dlopen/dlfcn/dlclose)
3. Works like a shell script (lots of calls to popen(3), system(2)).
Speaking of a shell script - all the strings related to what this thing does are obfuscated... but in a kind of asinine way: adding random numbers to the valid string, and subtracting those numbers out later on. Of course, this is good enough to evade the strings command!
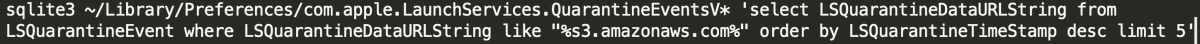
So what does this malware do that is particularly interesting? Well I found this snippet, once I figured out how to decode the strings. This grabs all the 'quarantined' URLs that Apple picked up that contain reference to an AWS S3 bucket. These are then sent up to the C&C server.
In the end, though, this dropper was engineered to be reliable. They seem to maintain different payloads for different versions of macOS. Based on the version of macOS a user is running, the dropper will download the appropriate version of the actual malware, and install it.

 Read on Twitter
Read on Twitter