If you want to get insights on privacy related app activity on Android with @fridadotre, there exist apps with extensive measures to prevent this (SafetyNet, advanced CertPinning, native 3rd party runtimes).
Pokemon Go is one of them. Used it as example to bypass most of them...
Pokemon Go is one of them. Used it as example to bypass most of them...
What is done:
1) privacy related Android APIs (LocationManager, TelephonyManager, JNI, Intent related methods etc) are hooked and call data is forward to a custom tool which stores it in elasticsearch
1) privacy related Android APIs (LocationManager, TelephonyManager, JNI, Intent related methods etc) are hooked and call data is forward to a custom tool which stores it in elasticsearch
2) mitmproxy intercepts all HTTPS traffic from the device and forwards occurring requests to my custom tool, too. Each request also contains the requesters original TCP socket data (from initial connection, before TLS handshake)
3) The tool processes incoming info from mitmproxy and associates it to source device+process+application. The data required to make this association is obtained from Frida-hooked http://libc.so calls for socket operations. Results are sent to elasticsearch, again
4) As the location related APIs are hooked anyways, a location in Berlin is spoofed
To allow all of this to work on an app like Pokemon Go, the following adjustments have been applied to a physical test device (Samsung Galaxy S5 running @LineageAndroid 16 == Android 9):
...
...
1) The device is "systemless" rooted with @topjohnwu's Magisk
2) To deploy the latest @fridadotre server for binary instrumentation, the Magisk plugin "MagiskFrida" is used
2) To deploy the latest @fridadotre server for binary instrumentation, the Magisk plugin "MagiskFrida" is used
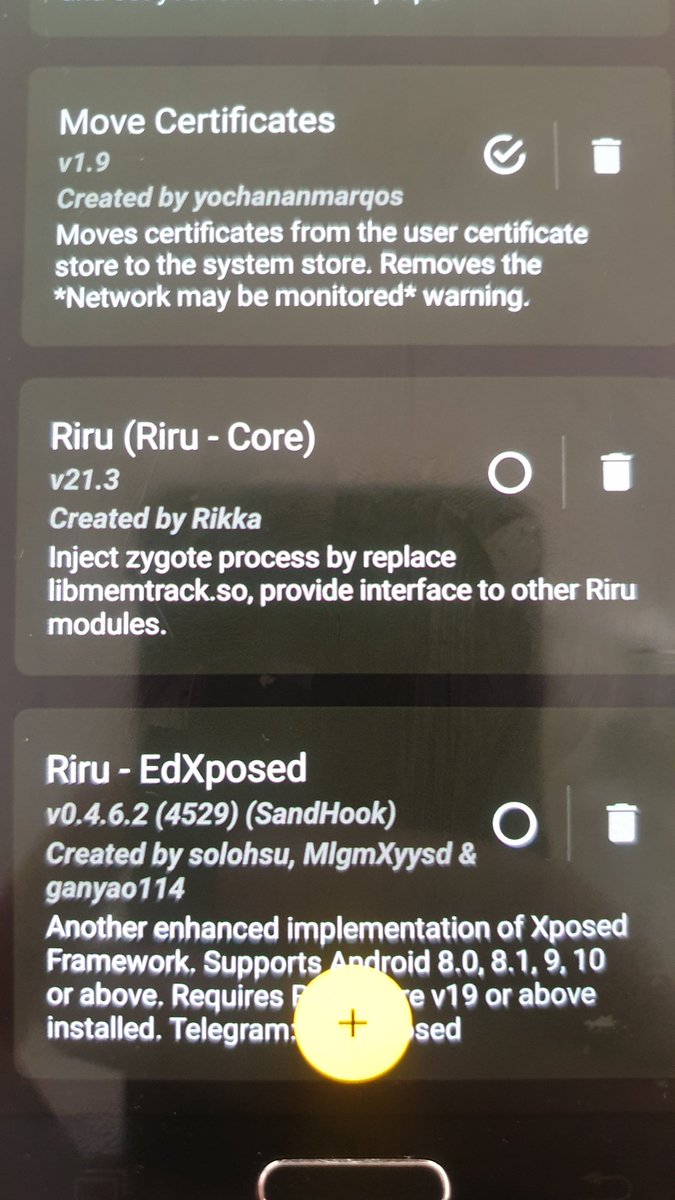
3) For HTTPS interception, the @mitmproxy CA certificate is placed in the System Store with the Magisk plug-in "Move Certificates"
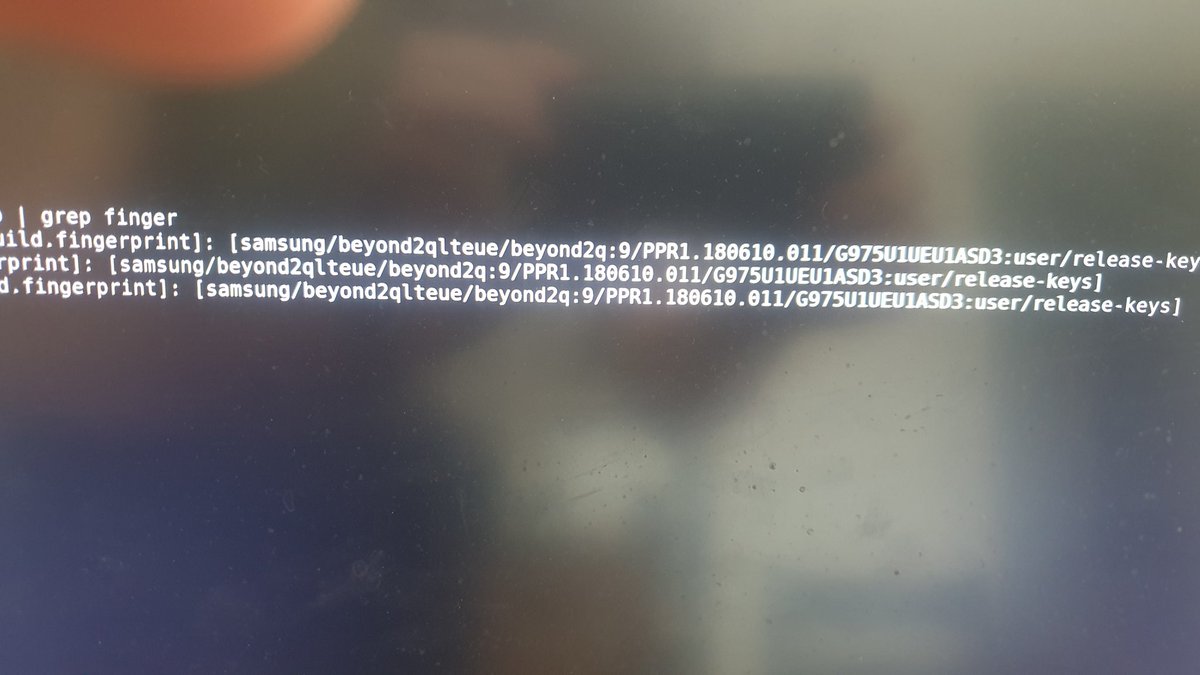
4) The Magisk plug-in "MagiskHide Props Config" is used to replace the properties for device fingerprints, with a one verified by Google (picture)
4) The Magisk plug-in "MagiskHide Props Config" is used to replace the properties for device fingerprints, with a one verified by Google (picture)
... depending on the device and ROM in use this is required to pass the SafetyNet integrity checks (the Lineage image for my device uses verified fingerprints already, but for an older Android version)
5) Further, to pass the SafetyNet checks, Magisk has to be hidden from the "Google Mobile Services (gms)" related processes.
6) Unfortunately, to pass the SafetyNet "Basic Integrity" check @XposedFramework (or EdXposed in my case) is a no-go.
At this point all SafetyNet checks should pass, although the device is rooted and has Frida-server running.
(If not, clearing the data cache for "Play Services" is a great help).
Also Pokémon Go should start up fine and related traffic could be intercepted with @mitmproxy
...
(If not, clearing the data cache for "Play Services" is a great help).
Also Pokémon Go should start up fine and related traffic could be intercepted with @mitmproxy
...
7) Traffic interception is not done transparently, instead I have applied the proper proxy settings to the device's WiFi connection
Two major issues are remaining:
1) Messing with certificate pinning fails, because Xposed is missing. Doing so with Frida hooks (f.e. TrustManager) mostly crashed my instrumented processes
2) @fridadotre spawn (gating) is not working (seems to be an issue with Magisk Hide)...
1) Messing with certificate pinning fails, because Xposed is missing. Doing so with Frida hooks (f.e. TrustManager) mostly crashed my instrumented processes
2) @fridadotre spawn (gating) is not working (seems to be an issue with Magisk Hide)...
... thus I'm currently stuck to attach to already running processes (no early instrumentation)
That's it so far!
That's it so far!
Forgot to mention: The lack of certificate pinning bypasses is no issue for Pokémon Go in the described setup, interception works anyways
 Read on Twitter
Read on Twitter