Locks are pretty rubbish. The lock on your door is more of a "keep out" sign than an actual way to keep someone who wants to get in from coming in. My daughter was 5 or 6 when I first took her to @Defcon and she learned to pick locks in an hour.
1/
1/
So can you! Try Toool, The Open Organization of Lockpickers, and go to town. It's a super fun, soothing way to pass the day. Like knitting, but simultaneously more and less practical.
https://toool.us/
2/
https://toool.us/
2/
Once you've learned to pick locks, you get a profound realization about security: there are billion-dollar companies whose products are just GARBAGE and always have been, who, despite this, have been in business for decades or even centuries.
3/
3/
You also realize why: security is hard. Making locks that can be easily opened with a key, not easily opened without the key, can be serviced and mass produced? That's just hard.
4/
4/
Moreover, the materiality of locks - the fact that they're made from STUFF, and that STUFF has its own characteristics, flaws and behaviors, makes those problems a million times gnarlier.
5/
5/
For years, we've known that amateur lockpickers can reproduce your keys by taking pictures of them. There are even grocery store machines that take a picture of your key and duplicate it. The shape of your key is itself a security vulnerability.
6/
6/
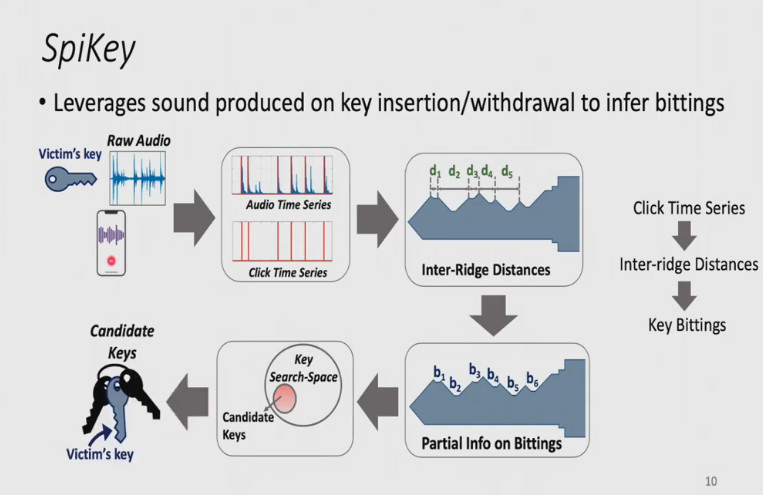
But it turns out it's not just the SHAPE of your key, it's the SOUND. #Spikey is an exploit from a NUS Comp Sci team lead by Soundarya Ramesh, laid out in this (paywalled) ACM Hotmobile paper.
https://dl.acm.org/doi/abs/10.1145/3376897.3377853
7/
https://dl.acm.org/doi/abs/10.1145/3376897.3377853
7/
Spikey is an acoustic attack on traditional six-pin locks. It analyzes a sound recording of a key entering the keyway and hitting the pins and infers what the key must look like based on the sounds.
https://cacm.acm.org/news/246744-picking-locks-with-audio-technology/fulltext
8/
https://cacm.acm.org/news/246744-picking-locks-with-audio-technology/fulltext
8/
The actual inference part works really reliably! Here's Ramesh demoing the technique:
9/
9/
The hard part isn't the analysis, it's obtaining the recording. You need to get a smartphone to within a few centimeters of the key as it enters the lock, which is pretty obvious. On the other hand, it may be possible to capture the audio by hacking a "smart" doorbell's mic.
10/
10/
Speaking as an author of technothrillers, this is a fantastic bit. (attn: @jonrog1).
What's more, it dispenses with the need for lockpicking altogether: obtain an advance recording, infer the key, make the key, enter the premises.
11/
What's more, it dispenses with the need for lockpicking altogether: obtain an advance recording, infer the key, make the key, enter the premises.
11/
Ramesh speculates that a generic defense against this attack can be found in subtle alterations in the geometry of the key - by making the ridges smoother, it could dampen the sounds they make when hitting the pins, frustrating attempts to infer the pin configuration.
12/
12/
If you want to learn lockpicking (and I think you should try!), I recommend the picks and practice locks from @SparrowsTools, which have never steered me wrong.
https://www.sparrowslockpicks.com/
eof/
https://www.sparrowslockpicks.com/
eof/

 Read on Twitter
Read on Twitter