~ Bitcoin 51% Attacks ~
If a single Bitcoin miner gains control of the majority of the network's hash power... what exactly can they do, and how?
They can't steal your coins, but they can swindle @PeterSchiff out of some gold bars. Here's how
If a single Bitcoin miner gains control of the majority of the network's hash power... what exactly can they do, and how?
They can't steal your coins, but they can swindle @PeterSchiff out of some gold bars. Here's how

1/ There are 2 main attacks someone can execute with 51% of the hash power:
1) Reorganize blocks in the chain to reverse transactions that they send
2) Prevent someone else's transaction from getting confirmed
We'll dive into the details of these but first some background:
1) Reorganize blocks in the chain to reverse transactions that they send
2) Prevent someone else's transaction from getting confirmed
We'll dive into the details of these but first some background:
2/ In the Bitcoin network, each block of transactions builds on top of the next one, creating an ever-growing chain of blocks that contain the history of transactions
3/ Now imagine Adam the attacker controls 51% of the hashing power and wants to pull off an attack
He arranges a deal with
@PeterSchiff to purchase 1000 BTC worth of gold bars, and they meet up in an alley in Puerto Rico
Adam sends Peter the 1000 bitcoin
He arranges a deal with
@PeterSchiff to purchase 1000 BTC worth of gold bars, and they meet up in an alley in Puerto Rico
Adam sends Peter the 1000 bitcoin
4/ Now Peter doesn't hand over the gold bars just yet - he knows he should wait for at least 6 block confirmations
But this is where Adam starts the attack
But this is where Adam starts the attack
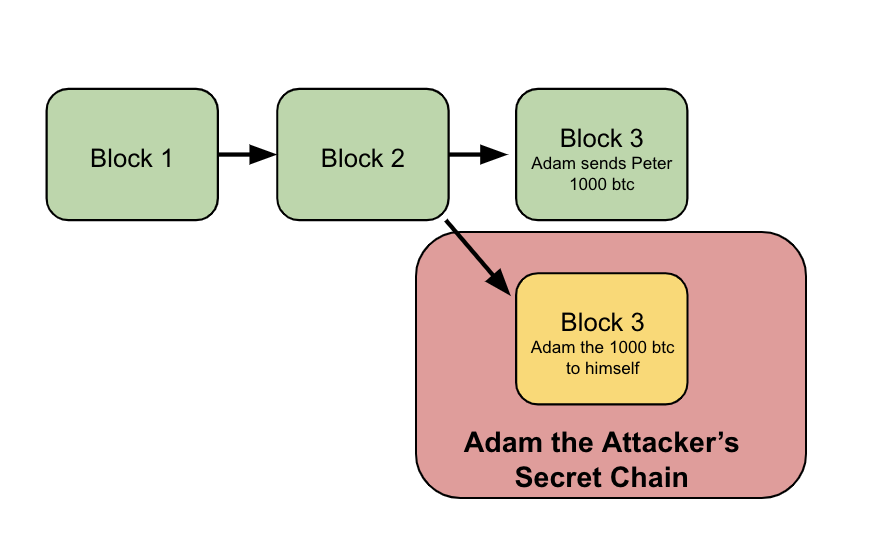
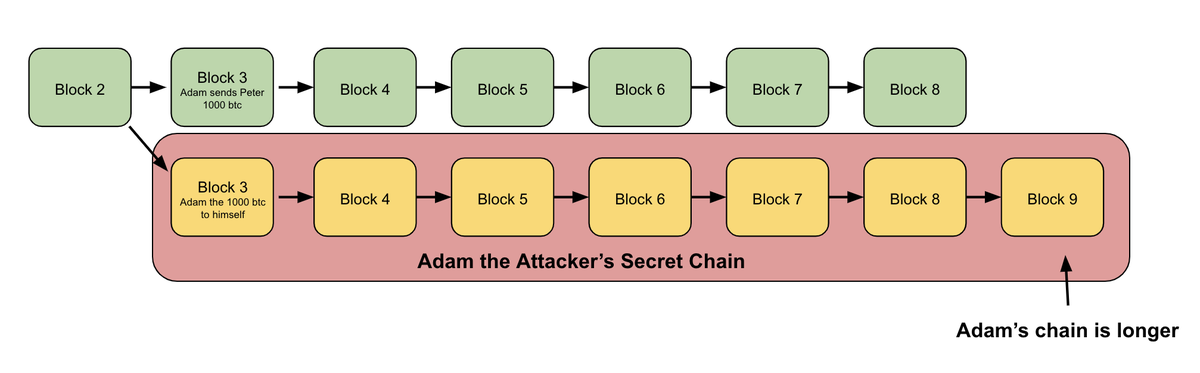
5/ Adam creates a separate transaction that spends the same 1000 bitcoin back to himself...
And then has his miners start mining a secret chain that includes this transaction, but does not include the transaction he sent to Peter
And then has his miners start mining a secret chain that includes this transaction, but does not include the transaction he sent to Peter
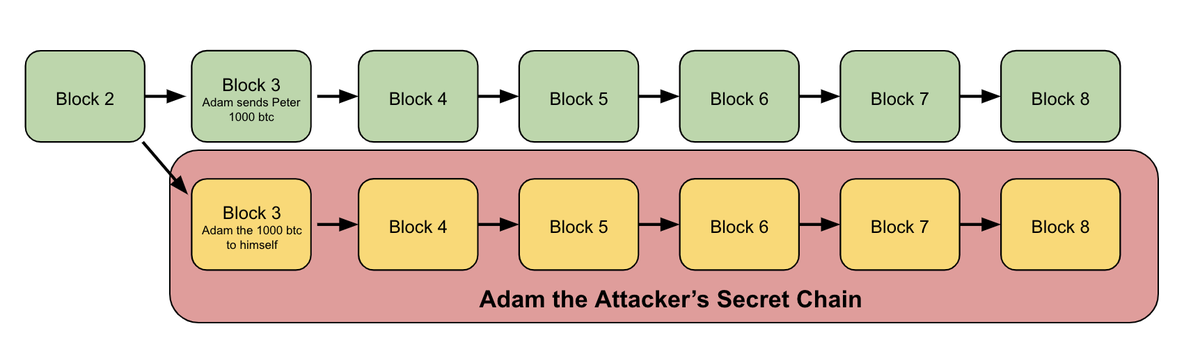
6/ Peter wants to wait for 6 confirmations before handing over the gold so they sit together in the alley and Peter talks the whole time
Meanwhile Adam's miners keep mining on a secret chain (hidden from the rest of the network), while the rest of the network mines the green one
Meanwhile Adam's miners keep mining on a secret chain (hidden from the rest of the network), while the rest of the network mines the green one
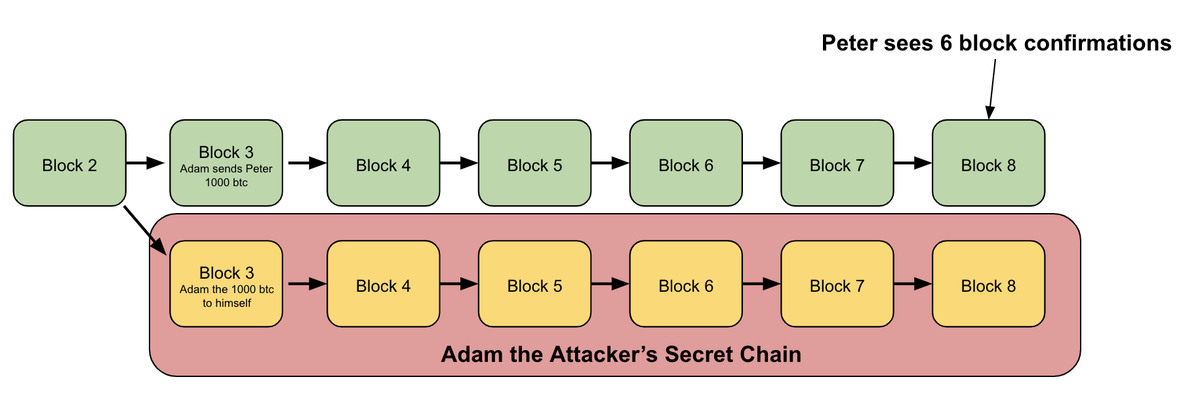
7/ Finally after 6 block confirmations on the green chain that the public can see, Peter is convinced the transaction is finalized and hands over the gold
8/ So Adam takes the gold and speeds away in his Lambo
Now at this point, because Adam controls a majority of the hashpower, his secret chain is likely longer (has more total proof-of-work) than the main chain
Now at this point, because Adam controls a majority of the hashpower, his secret chain is likely longer (has more total proof-of-work) than the main chain
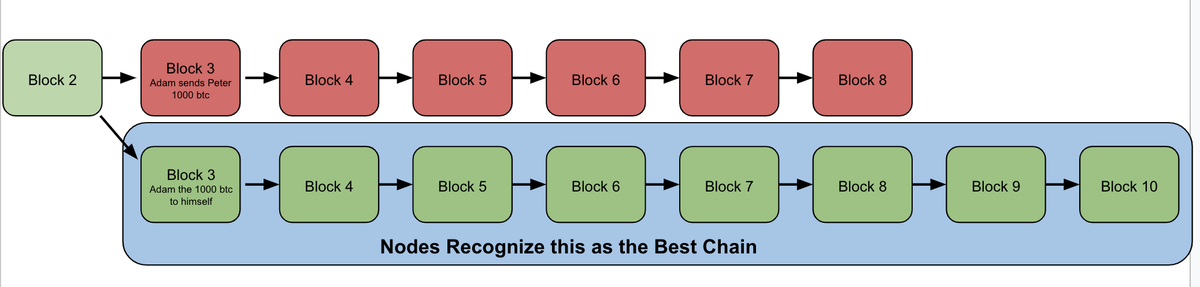
9/ So Adam's miners publish his chain to the network
All bitcoin nodes are programmed to accept the chain with the most work behind it with no questions asked
So they immediately all recognize Adam's secret chain to be the true chain, and invalidate the old one
All bitcoin nodes are programmed to accept the chain with the most work behind it with no questions asked
So they immediately all recognize Adam's secret chain to be the true chain, and invalidate the old one
10/ All new blocks are then created on top of this chain!
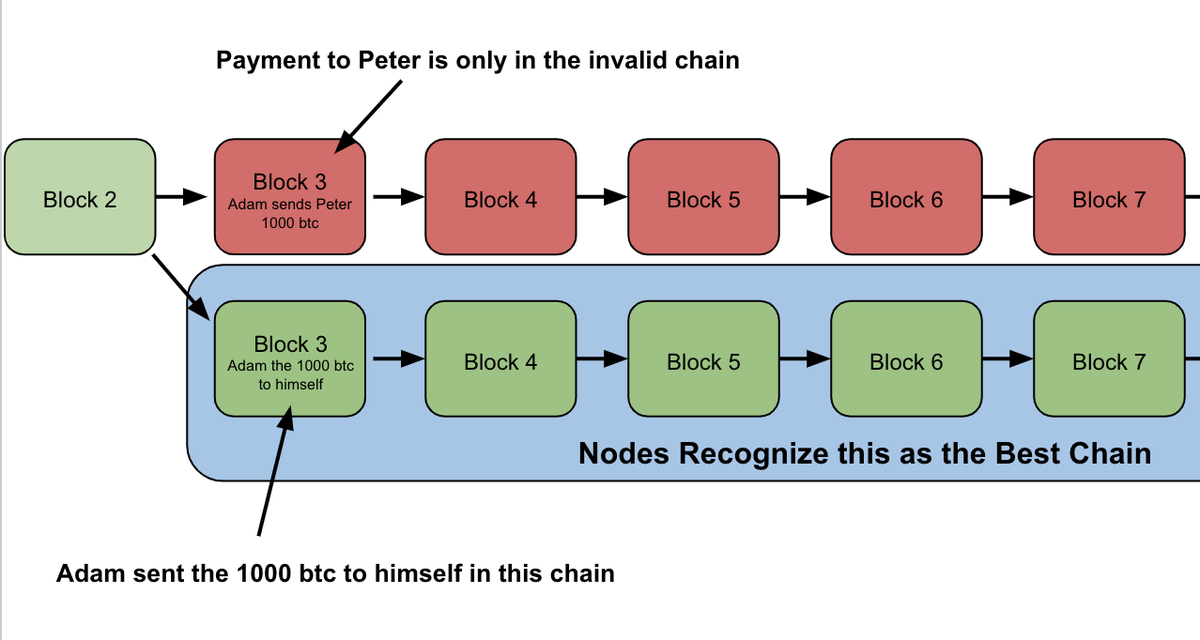
So what happened?
If you remember, Adam's transaction to Peter was only included in the OLD chain
The new chain instead has a transaction of Adam spending those coins to himself!
So what happened?
If you remember, Adam's transaction to Peter was only included in the OLD chain
The new chain instead has a transaction of Adam spending those coins to himself!
11/ So by re-organizing the chain with his miners, Adam has essentially reversed his payment to Peter
And now Adam has all the gold bars AND his 1000 bitcoin, while Peter is left with nothing
And now Adam has all the gold bars AND his 1000 bitcoin, while Peter is left with nothing
12/ So that covers the first attack the Adam can execute with a majority of the hash-power
What about the second?
What about the second?
13/ The second attack is that Adam can prevent somebody else's transactions from being mined
He can do this by always excluding their transactions from blocks that he mines, and only mining on top of blocks that don't include those transactions
He can do this by always excluding their transactions from blocks that he mines, and only mining on top of blocks that don't include those transactions
14/ Adam's chain will always end up being the dominant chain, because he has a majority of the hash power
Now these censored transactions will still show up in bitcoin nodes, but they will have 0 confirmations as long as Adam is in control
Now these censored transactions will still show up in bitcoin nodes, but they will have 0 confirmations as long as Adam is in control
15/ So those are the two main types of attacks... But what can Adam *not* do?
All the bitcoin nodes still enforces the rules of the network, so he cannot:
- Create new coins out of thin air
- Send coins that don't belong to him
- Reverse other people's transactions
All the bitcoin nodes still enforces the rules of the network, so he cannot:
- Create new coins out of thin air
- Send coins that don't belong to him
- Reverse other people's transactions
16/ Anyway, that's a basic summary of 51% attacks
Generally bitcoiners are not too worried about this scenario playing out
A 51% attack is risky and extremely expensive to pull off, and with that much hash power, the game theory incentivizes them to just follow the rules
Generally bitcoiners are not too worried about this scenario playing out
A 51% attack is risky and extremely expensive to pull off, and with that much hash power, the game theory incentivizes them to just follow the rules
17/ Chain reorganizations of significant length never happen in Bitcoin, so if one does happen, it will be quite clear that something fishy is going on, and the attacker risks sacrificing all their future mining profits by hurting the integrity of the network
18/ Well there's your summary of 51% attacks, hope it was useful. Please add information in the comments if you think I missed something!
Also if you liked this thread, you might enjoy all my other educational threads linked here https://twitter.com/dannydiekroeger/status/1282000262782042117?s=20
Also if you liked this thread, you might enjoy all my other educational threads linked here https://twitter.com/dannydiekroeger/status/1282000262782042117?s=20
19/19
And considering signing up to my email list, where I send out notifications of new threads, and will keep you updated with any new content outside of Twitter http://dannydiekroeger.substack.com
And considering signing up to my email list, where I send out notifications of new threads, and will keep you updated with any new content outside of Twitter http://dannydiekroeger.substack.com

 Read on Twitter
Read on Twitter