Finfisher/Finspy is malware made by Gamma, an Anglo-German cyber-arms dealer, and sold to the world's most despicable dictators and torturers. Microsoft Security has just published an extensive, fascinating analysis of its self-defense measures.
https://www.microsoft.com/security/blog/2018/03/01/finfisher-exposed-a-researchers-tale-of-defeating-traps-tricks-and-complex-virtual-machines/
1/
https://www.microsoft.com/security/blog/2018/03/01/finfisher-exposed-a-researchers-tale-of-defeating-traps-tricks-and-complex-virtual-machines/
1/
There are two big threats to malware: first, that it will be decompiled so that the vulnerabilities that it expoits can be patched, and second, that this decompilation process will yield fingerprints that allow security tools to reliable detect the malware's presence.
2/
2/
Malware authors put a lot of care into writing routines to frustrate analysis, and Finfisher goes above and beyond in detecting whether it is under examination and protecting itself from scrutiny.
3/
3/
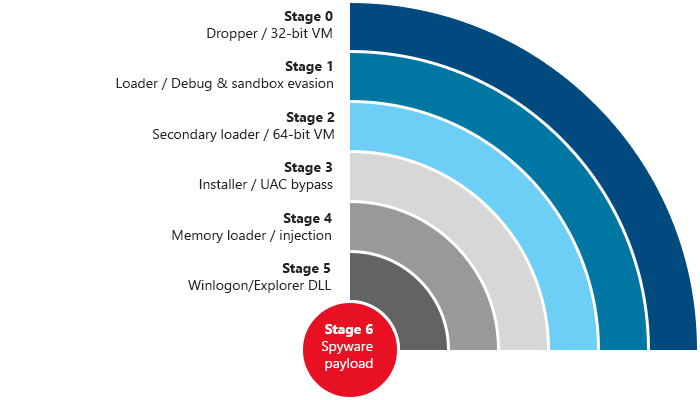
It starts with "spaghetti code" - breaking instructions into tiny fragments that jump one to the other, out of order, salted with junk instructions that do nothing.
All of this code gets executed to load up a virtual machine with its own opcodes.
4/
All of this code gets executed to load up a virtual machine with its own opcodes.
4/
The VM loads a bunch of subprograms that check for debuggers and sandboxes - indicators that the malware is running on a security analyst's workbench, rather than a target's system.
5/
5/
Then the system loads a bunch of fake bitmap images, throws away some of their headers, reassembles them, and decrypts data hidden in the resulting image.
Next comes ANOTHER virtual machine with its own, different opcodes, which decrypts and loads more software.
6/
Next comes ANOTHER virtual machine with its own, different opcodes, which decrypts and loads more software.
6/
This is the installer, which loads up a bunch of DLLs, and begins installation of the malware itself, which starts injecting code into the user's programs.
The injector also has countermeasures to defeat common detection methods.
7/
The injector also has countermeasures to defeat common detection methods.
7/
There's another round of obfuscation, and then various modules - customized based on the target - start loading.
It's a very clever piece of puzzlemaking, and an even more clever piece of detective work to solve it.
8/
It's a very clever piece of puzzlemaking, and an even more clever piece of detective work to solve it.
8/
It's also a fascinating glimpse into the bizarre problem of software figuring out whether it's running on a real computer or inside a researcher's VM.
This may be the key to how Marcus "Malwaretech" Hutchins saved the world from Wannacry ransomware.
9/
This may be the key to how Marcus "Malwaretech" Hutchins saved the world from Wannacry ransomware.
9/
Hutchins was examining Wannacry when he noticed that it was hardcoded to try to reach a nonexistent domain, …http://iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com . He registered that doman and stood up a webserver there and every copy of Wannacry in the world went dormant.
10/
10/
No one knows exactly what happened there, but it's likely that Wannacry's method for figuring out if it was in the Matrix or not was to try to contact a nonexistent website.
https://pluralistic.net/2020/05/13/malwaretech/#malwaretech
11/
https://pluralistic.net/2020/05/13/malwaretech/#malwaretech
11/
If the website answered, it would assume it was running in a researcher's test system and it would cease to function - so when Hutchins put up his webserver, every Wannacry instance on Earth decided it was under scrutiny and ceased all activity.
eof/
eof/

 Read on Twitter
Read on Twitter