I watched a couple of talks from @haroonmeer today, & wanted to share a few insights. Mostly so I can sound smart by quoting him.
Talks:
Insights follow in no particular order, just reading my scribbled handwritten notes:
Talks:
Insights follow in no particular order, just reading my scribbled handwritten notes:
Insight 1:
Attackers have their specialisation; appsec, wifi, exploit writing, etc, but defenders are usually "that infosec guy" at a company. It's hard to beat an adversary when you're expected to know everything about everything.
I'd never thought about this before.
Attackers have their specialisation; appsec, wifi, exploit writing, etc, but defenders are usually "that infosec guy" at a company. It's hard to beat an adversary when you're expected to know everything about everything.
I'd never thought about this before.
Insight 2:
Attackers have the initiative - they can choose when to attack - but defenders choose the battleground. Defenders also get to see the whole chessboard, whilst attackers do not - need to leverage this advantage.
Attackers have the initiative - they can choose when to attack - but defenders choose the battleground. Defenders also get to see the whole chessboard, whilst attackers do not - need to leverage this advantage.
Insight 3:
Ye olde adage "Attackers only have to be successful once, defenders have to be successful 100% of the time" may not be as true as I thought. Flip it around; once an attacker's on the network they only need to trip up once and get detected ...
Ye olde adage "Attackers only have to be successful once, defenders have to be successful 100% of the time" may not be as true as I thought. Flip it around; once an attacker's on the network they only need to trip up once and get detected ...
... then roll in IR. I still think there's some truth - you have to defend every point but the attacker just needs to find that one unpatched box on the periphery - but it shakes it up when he knows he might get caught.
Insight 4:
It's embarrassing that often the pentest crew, after one month, know your network better than you. It's common enough that it's an inside joke in pentest circles, but there's no real excuse from the defenders side. You have the time, this is a priority.
It's embarrassing that often the pentest crew, after one month, know your network better than you. It's common enough that it's an inside joke in pentest circles, but there's no real excuse from the defenders side. You have the time, this is a priority.
Insight 5:
Management has already bought in! BlackHat is as big as rock concerts these days. You can't use the excuse any longer of "if only management understood, or would buy in"
Management has already bought in! BlackHat is as big as rock concerts these days. You can't use the excuse any longer of "if only management understood, or would buy in"
Insight 6:
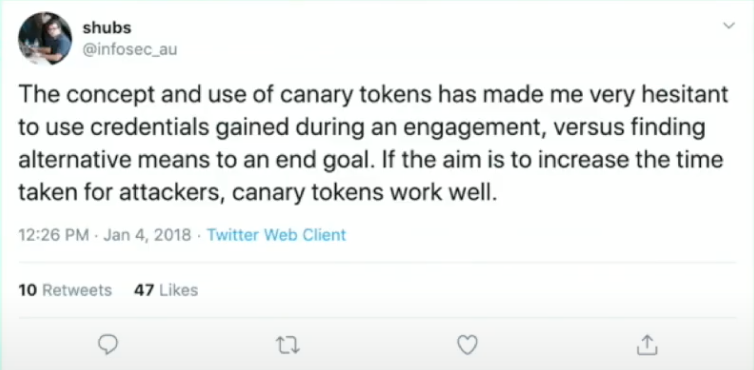
"Canary Tokens are stupid, but are useful and work, so aren't stupid."
There's a lot of value in applying simple 'hacky' solutions to defense - the same way we've always approached offense - perfect is the enemy of good here.
Defenders should be tooling too.
"Canary Tokens are stupid, but are useful and work, so aren't stupid."
There's a lot of value in applying simple 'hacky' solutions to defense - the same way we've always approached offense - perfect is the enemy of good here.
Defenders should be tooling too.
Insight 7:
The world (attack surface) is fluid - if you sit around waiting for $BIGVENDOR attackers will have moved on by the time they've built it (attacker advantage).
.... but, don't "not buy" anything, just don't buy stuff as a substitute for thinking.
The world (attack surface) is fluid - if you sit around waiting for $BIGVENDOR attackers will have moved on by the time they've built it (attacker advantage).
.... but, don't "not buy" anything, just don't buy stuff as a substitute for thinking.

 Read on Twitter
Read on Twitter