BREAKING: @Graphika_NYC has been digging into Russian info op #SecondaryInfektion for months. Today, we’re exposing its full scale.
6 years
7 languages
> 2,500 pieces of content
> 300 platforms (no, that’s not a typo)
And some truly epic fails.
https://secondaryinfektion.org/
6 years
7 languages
> 2,500 pieces of content
> 300 platforms (no, that’s not a typo)
And some truly epic fails.
https://secondaryinfektion.org/
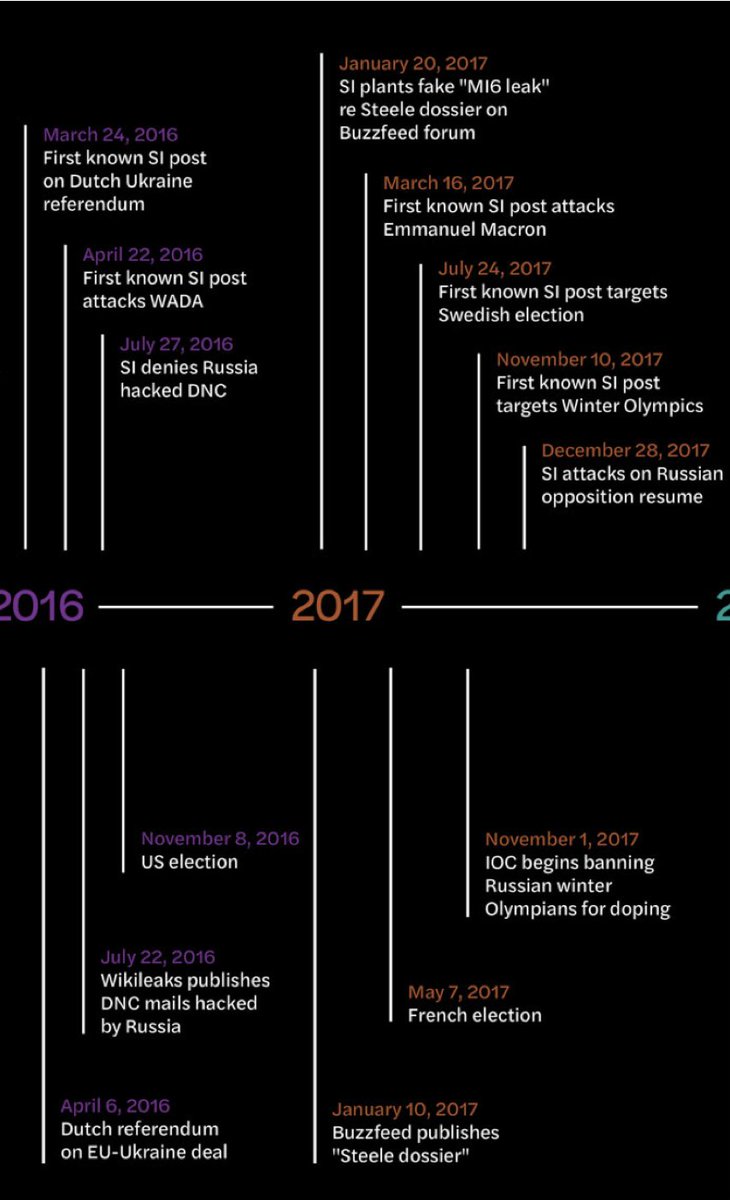
Top takeaways: 1) Secondary Infektion is a full-scale disinfo operation that’s been around at least six years.
We don’t know which entity is behind it, but they’re persistent, high-opsec, and a tough investigative nut to crack.
We don’t know which entity is behind it, but they’re persistent, high-opsec, and a tough investigative nut to crack.
This is a conservative estimate based on many interlocking criteria, including:
Short-lived, single-use burner accounts;
Forged documents;
Specific combinations of sites and fora;
Finds published by platforms (eg @Reddit).
We’re sure there's more to find.
Short-lived, single-use burner accounts;
Forged documents;
Specific combinations of sites and fora;
Finds published by platforms (eg @Reddit).
We’re sure there's more to find.
2) All the indicators point to a Russian origin. That includes the first attribution by @Facebook, content clues, language, context, and intersect with known Russian ops against targets such as @navalny, @wada_ama, @HillaryClinton and @EmmanuelMacron. https://about.fb.com/news/2019/05/more-cib-from-russia/
(Incidentally, big shoutout to the @Facebook investigative team for first finding this - and to the whole @Graphika_NYC team for all their dedication. It took a huge amount of digging to make the investigative breakthrough.)
Big thanks also to the teams at @Twitter, @Quora, @Reddit, @Google, @YouTube and @Medium for their thoughts and insights.
Best answer to cross-platform operations? Cross-platform responses.
Best answer to cross-platform operations? Cross-platform responses.
3) Not all operations are created equal. SI had super high OPSEC and religiously used single-shot burner accounts, but that made it really, really hard for many stories to gain traction.
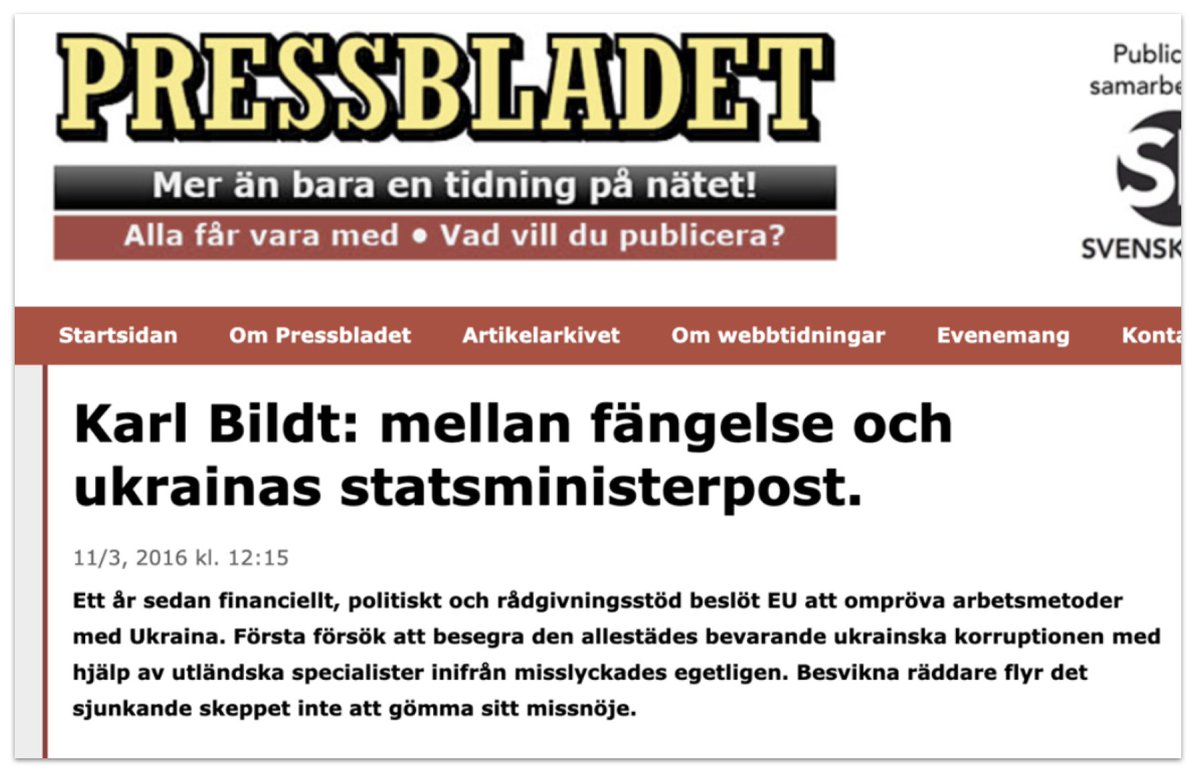
It might have helped if they’d been able to spell @carlbildt’s name, too.
It might have helped if they’d been able to spell @carlbildt’s name, too.
In other words, if you’re looking at an information operation, *don’t panic*. It may be viral, or it may have no impact at all.
Stick to the evidence. Evidence is everything.
Stick to the evidence. Evidence is everything.
4) We need to talk about leaks. The only time we know that SI got mainstream attention was when it leaked genuine UK-US trade documents before the UK election. https://graphika.com/reports/UK-trade-leaks/
How prepared are we all to understand and cope with interference by leaks before the US election?
Not just researchers and platforms, but media, parties, candidates, law enforcement and society?
Not just researchers and platforms, but media, parties, candidates, law enforcement and society?
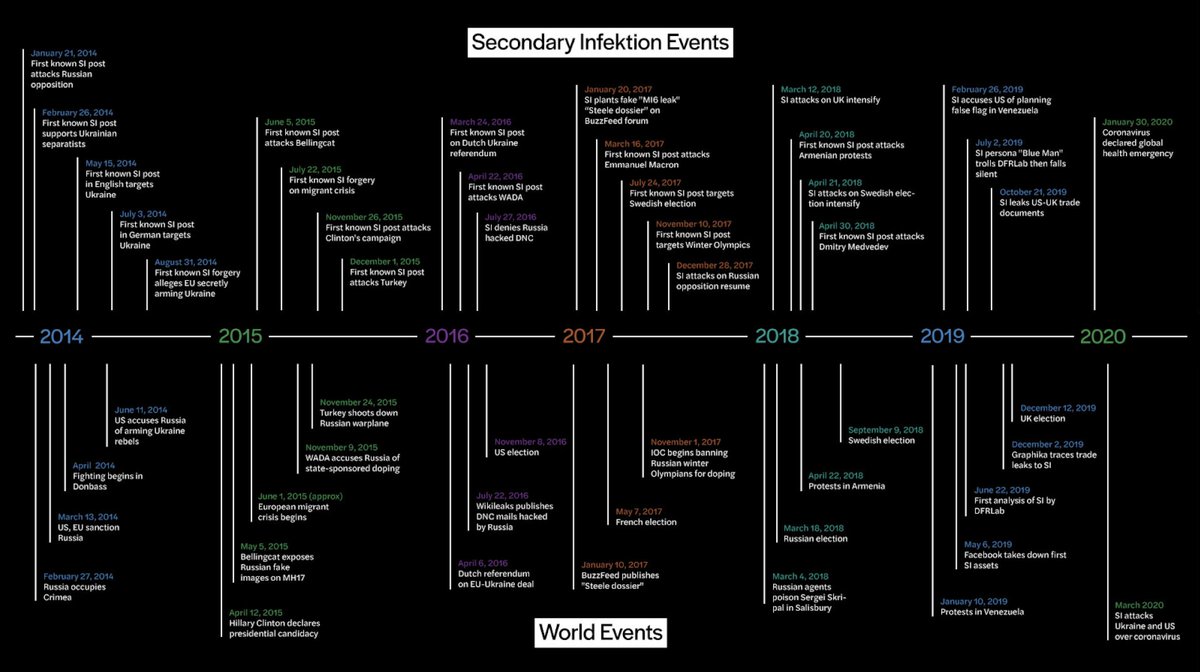
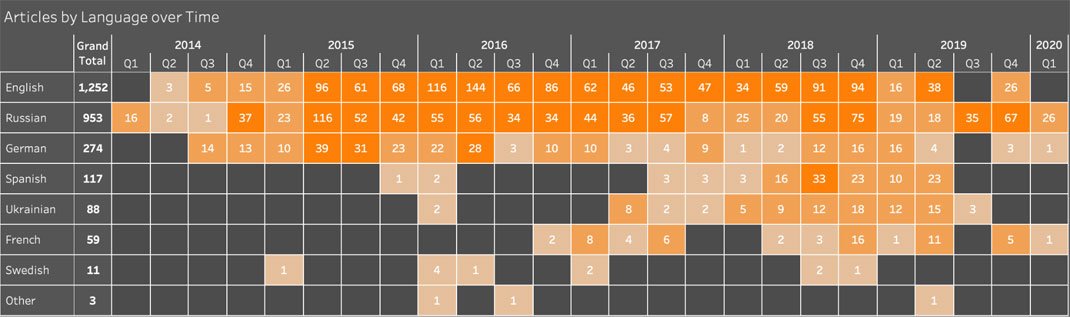
So, Secondary Infektion itself.
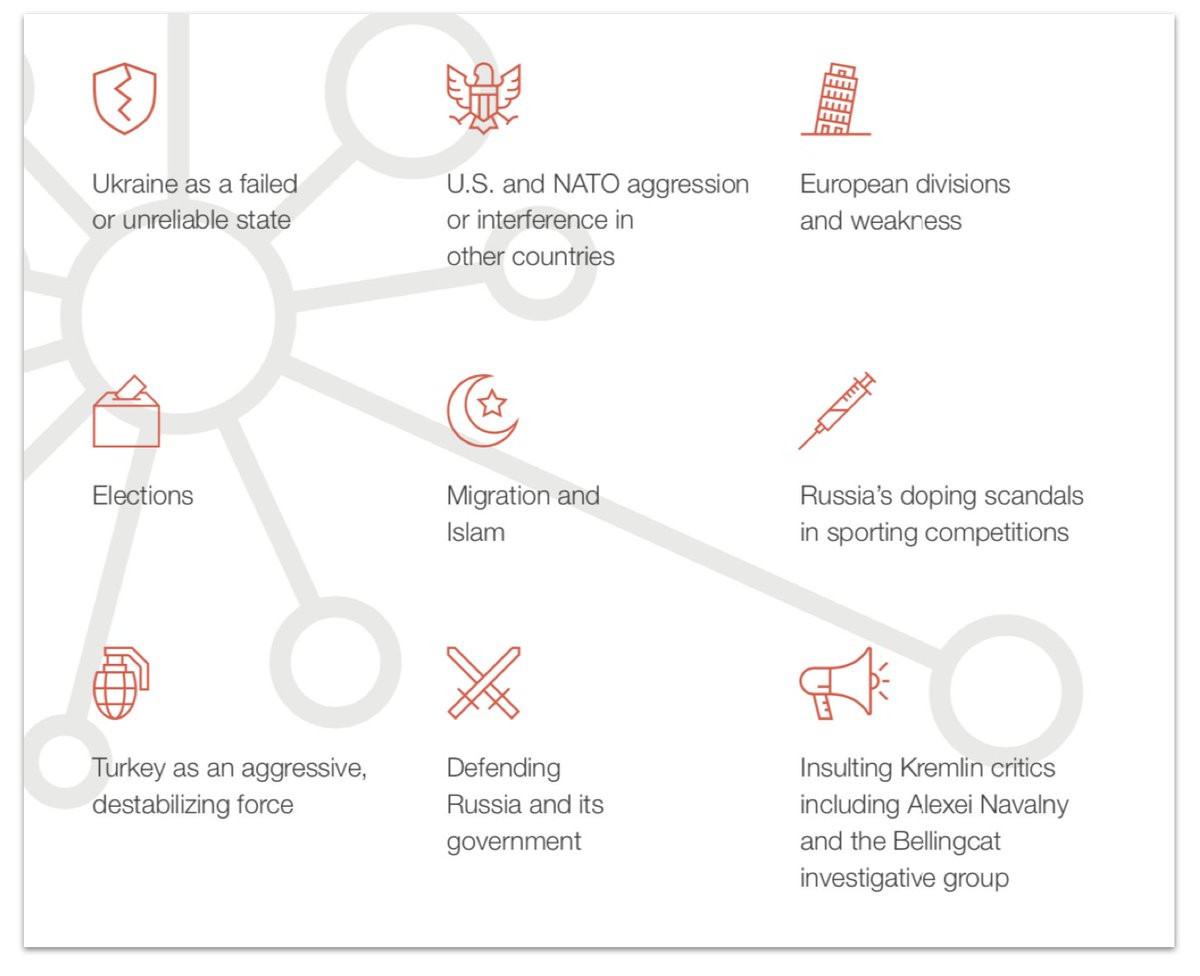
It posted stories on nine main subjects.
The top two? Portraying Ukraine as a failed or unreliable partner, and accusing the US, NATO and the West of interference and aggression.
It posted stories on nine main subjects.
The top two? Portraying Ukraine as a failed or unreliable partner, and accusing the US, NATO and the West of interference and aggression.
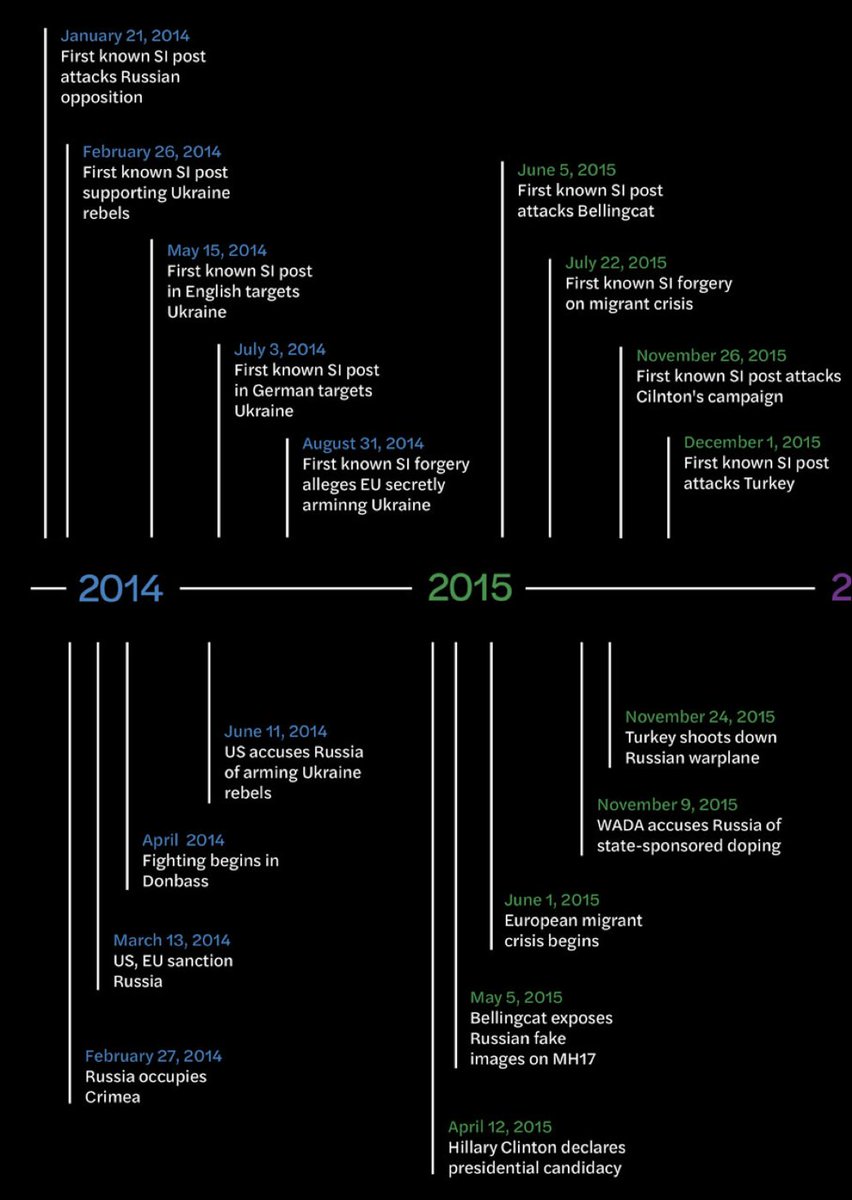
It started in 2014 by targeting the Russian opposition. After the Crimean annexation and MH17, it started posting in English and German, and attacking external critics, including @bellingcat and @eliothiggins.
In 2016, it targeted @wada_ama and @HillaryClinton’s campaign. In 2017, it targeted @EmmanuelMacron and @IOCmedia.
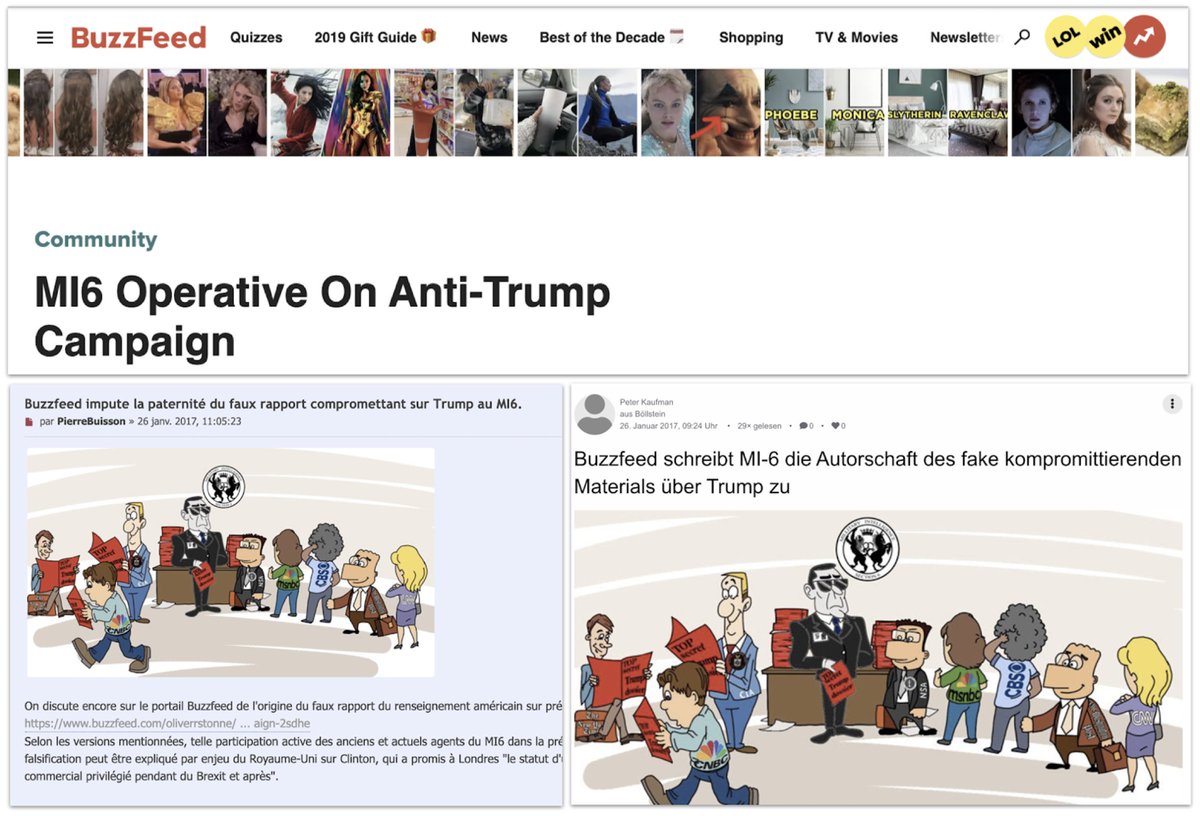
It tried to discredit the Steele dossier on Trump, too, by planting a story on the @BuzzFeed forum, and claiming it came from Buzzfeed itself.
(Hint: they have different URLs, h/t @CraigSilverman )
(Hint: they have different URLs, h/t @CraigSilverman )
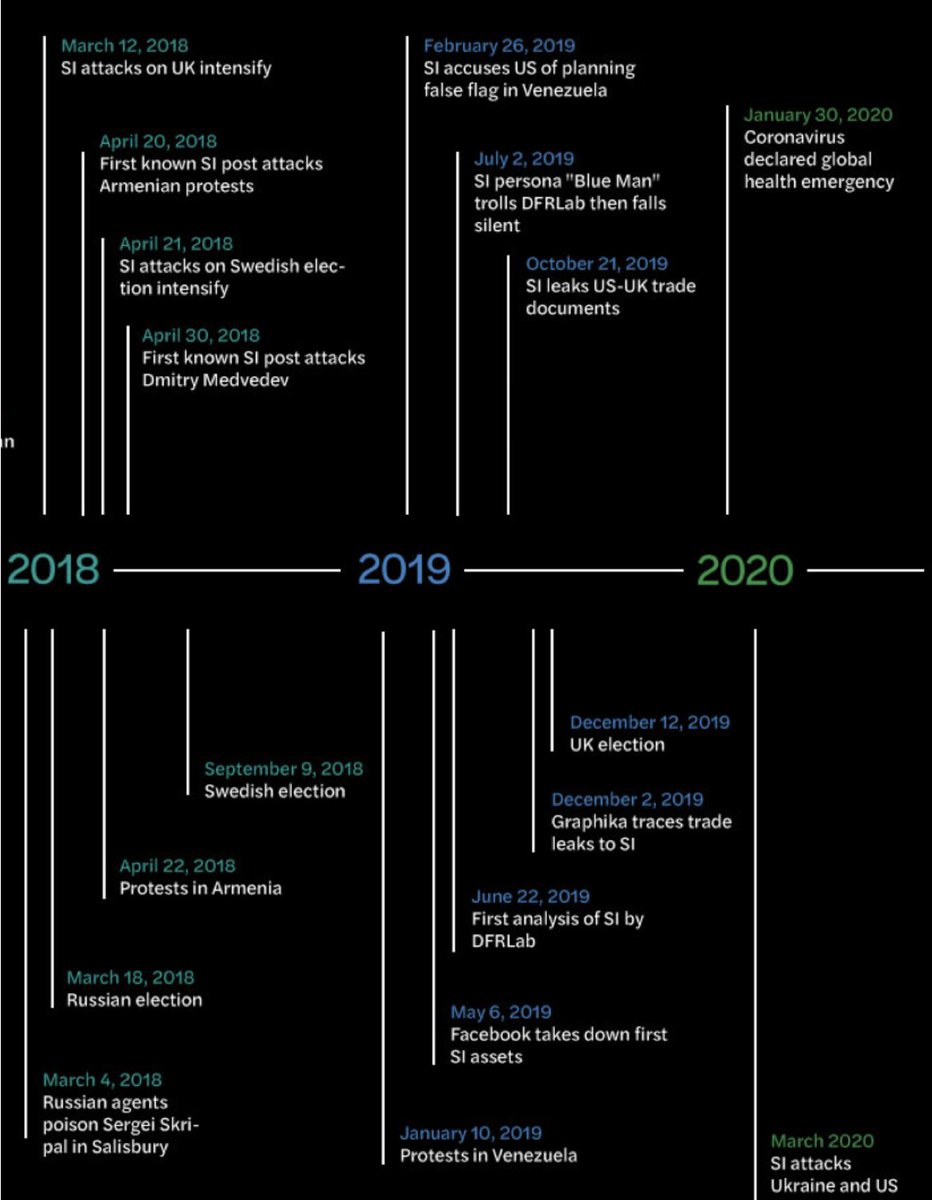
In 2018, it launched a big push against the UK after the Skripal poisoning. It also posted about the Swedish election and, weirdly, Dmitry @MedvedevRussia, just before his birthday.
We haven't seen much from them in 2020, but @arawnsley had a nice find of SI accusing the US of creating coronavirus.
Seems like every time there's a new disease, Russian info ops accuse America: remember the AIDS libel? https://www.thedailybeast.com/russian-trolls-hype-coronavirus-and-giuliani-conspiracies
Seems like every time there's a new disease, Russian info ops accuse America: remember the AIDS libel? https://www.thedailybeast.com/russian-trolls-hype-coronavirus-and-giuliani-conspiracies
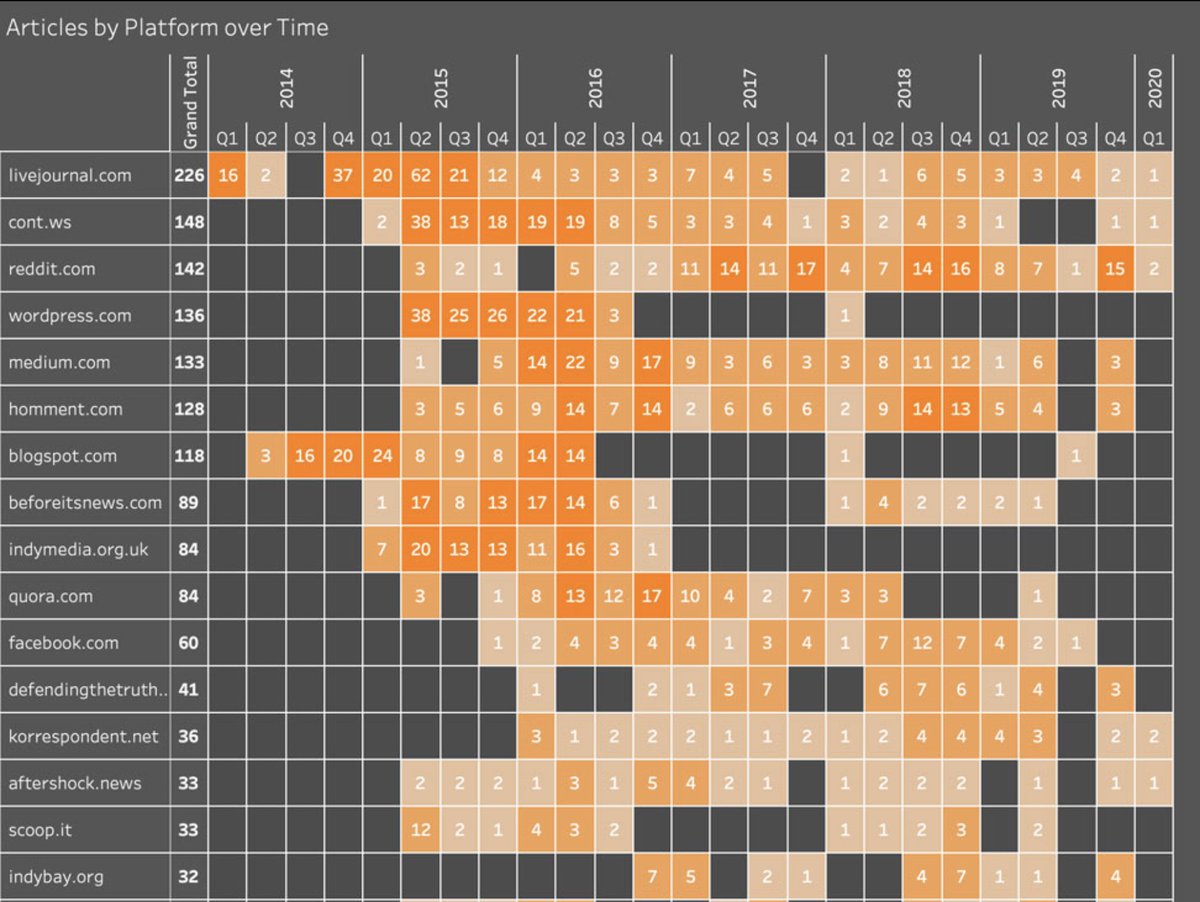
More than any other operation I’ve seen, SI was a cross-platform effort.
Over 300, at the latest count, and mostly *not* on the giant platforms.
Over 300, at the latest count, and mostly *not* on the giant platforms.
It changed over the years, especially as it added more languages into the mix.
At the start, a few repeat personas on Blogspot and Wordpress, mixed in with single-user burner accounts. By the end, almost all burners.
At the start, a few repeat personas on Blogspot and Wordpress, mixed in with single-user burner accounts. By the end, almost all burners.
The language mix evolved too. Russian and English were always the main ones, but don't get myopic here. German, French and Spanish were all in the mix.
When I say "single-use burner" accounts, these were accounts that were created, used and abandoned in less than an hour.
SI left hundreds of them behind.
SI left hundreds of them behind.
That's probably one reason so few of SI's stories had impact.
It's hard enough getting the first follower on social media. SI pretty much had to chase the first follower every time.
It's hard enough getting the first follower on social media. SI pretty much had to chase the first follower every time.
But it's also what made this a tough operation to unravel. If every asset only posts once, it's hard to find multiple stories from the same op.
We cracked that puzzle in January. Since then, the challenge has been the sheer volume of content we found.
We cracked that puzzle in January. Since then, the challenge has been the sheer volume of content we found.
Ultimately, almost none of SI's stories had mainstream impact. But it's really important to keep up the pressure.
Since the first @Facebook exposure a year ago, many investigators have uncovered parts of its work, including @DFRLab, @arawnsley and @RecordedFuture.
Since the first @Facebook exposure a year ago, many investigators have uncovered parts of its work, including @DFRLab, @arawnsley and @RecordedFuture.
Covert operations like this often don't look like a problem until suddenly, they are.
Remember the UK trade leaks, as reported by the great @jc_stubbs? https://www.reuters.com/article/us-britain-election-foreign/leak-of-papers-before-uk-election-raises-specter-of-foreign-influence-experts-idUSKBN1Y620A
Remember the UK trade leaks, as reported by the great @jc_stubbs? https://www.reuters.com/article/us-britain-election-foreign/leak-of-papers-before-uk-election-raises-specter-of-foreign-influence-experts-idUSKBN1Y620A
It's important to understand these operations and recognise their fingerprints, but not over-dramatise them.
That way, if they ever do land a big story, they can be exposed.
That way, if they ever do land a big story, they can be exposed.
Final point: one of the endearing things about SI was how bad some of its efforts were.
"First the Europe, then the rest"?
"First the Europe, then the rest"?
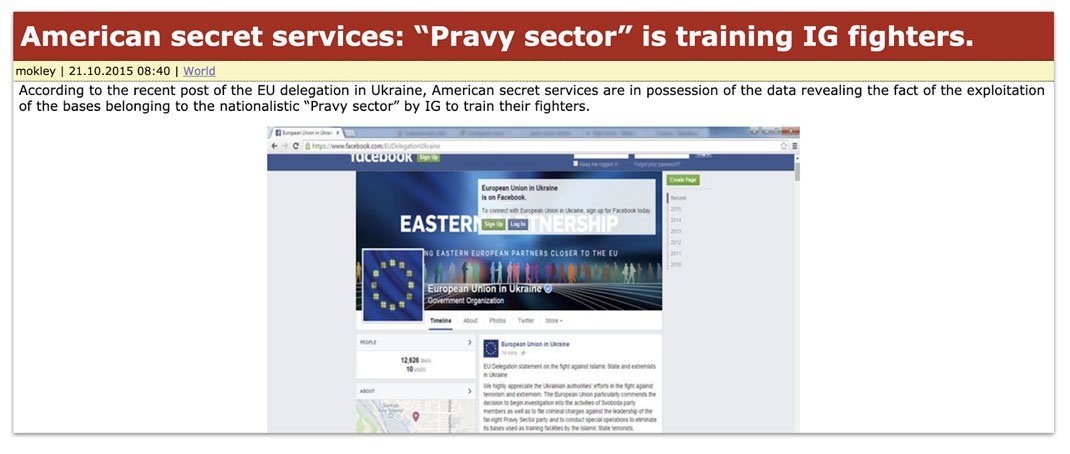
No, that's not @instagram fighters. It's based on the Russian acronym for Islamic State (ИГ, Исламское Государство.)
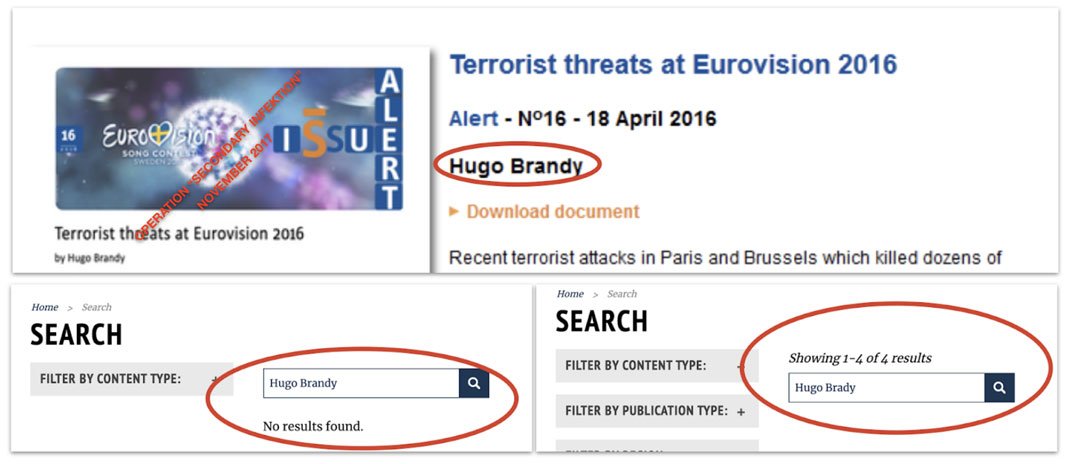
"Hugo Brandy."
We're not sure if they were trying to impersonate @hugobrady of @EU_ISS here, or just running out of inspiration for names.
We're not sure if they were trying to impersonate @hugobrady of @EU_ISS here, or just running out of inspiration for names.
Ultimate lesson? It's harder to run a viral information operation than you might think.
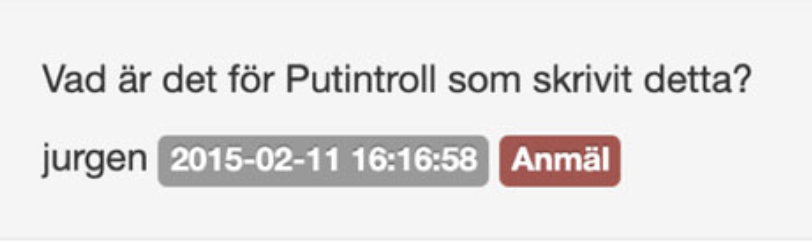
"What kind of Putin troll wrote this?"
An epitaph for #SecondaryInfektion... at least for now.
"What kind of Putin troll wrote this?"
An epitaph for #SecondaryInfektion... at least for now.

 Read on Twitter
Read on Twitter