 Today, we are exposing 6 years of "Secondary Infektion" activity, a persistent Russian information operation network which we've been investigating for months.
Today, we are exposing 6 years of "Secondary Infektion" activity, a persistent Russian information operation network which we've been investigating for months.It lives here, in 150 pages of details, with its database and carousel of forgeries (!): http://www.secondaryinfektion.org
Secondary Infektion:
 Spans at least 2014-2020
Spans at least 2014-2020
 Loves forgeries
Loves forgeries
 Operates in at least 7 languages
Operates in at least 7 languages
 Maintains high OPSEC throughout the years
Maintains high OPSEC throughout the years
 Leverages inauthentic single-use accounts on multiple platforms
Leverages inauthentic single-use accounts on multiple platforms
 Achieved minimal traction online (besides UK op., Nov. 19)
Achieved minimal traction online (besides UK op., Nov. 19)
 Spans at least 2014-2020
Spans at least 2014-2020 Loves forgeries
Loves forgeries Operates in at least 7 languages
Operates in at least 7 languages Maintains high OPSEC throughout the years
Maintains high OPSEC throughout the years Leverages inauthentic single-use accounts on multiple platforms
Leverages inauthentic single-use accounts on multiple platforms Achieved minimal traction online (besides UK op., Nov. 19)
Achieved minimal traction online (besides UK op., Nov. 19)
Secondary Infektion’s content seemed designed to provoke tensions between Moscow’s perceived enemies, and to attack Kremlin critics across the globe. We highlighted 9 main themes throughout the years:
We’ve seen Secondary Infektion “cross paths” with other actors in Russian IO on key campaigns, ex. targeting WADA in 2016, US elections in 2016, French election in 2017.
On these, Secondary Infektion seems to operate in parallel, not in tandem: https://secondaryinfektion.org/report/crossing-campaigns/
On these, Secondary Infektion seems to operate in parallel, not in tandem: https://secondaryinfektion.org/report/crossing-campaigns/
 Because of this network's structure, the set was painful to build. Our report is based on 2,500 content pieces we can assign with high confidence to the same set.
Because of this network's structure, the set was painful to build. Our report is based on 2,500 content pieces we can assign with high confidence to the same set.It is a conservative take: there is more to find, hence our sharing details and assets to empower others to do so
The departure point was a set of 21 assets shared by @Facebook more than a year ago:
https://about.fb.com/news/2019/05/more-cib-from-russia/
From then on, @benimmo relentlessly led an epic campaign to find the rest of the puzzle pieces scattered across the Internet.
One more proof that disclosures matter!
https://about.fb.com/news/2019/05/more-cib-from-russia/
From then on, @benimmo relentlessly led an epic campaign to find the rest of the puzzle pieces scattered across the Internet.
One more proof that disclosures matter!
 Please join me in a shout-out to my amazing Graphika team, who spent months down this rabbit hole: @bennimmo @realShawnEib @Lea_Ronzaud @rp2871, and @ChrisHernon + Tim Kostelancik who joined for this report. They are extraordinarily dedicated, thorough, careful colleagues
Please join me in a shout-out to my amazing Graphika team, who spent months down this rabbit hole: @bennimmo @realShawnEib @Lea_Ronzaud @rp2871, and @ChrisHernon + Tim Kostelancik who joined for this report. They are extraordinarily dedicated, thorough, careful colleagues 
 And let’s roll out the virtual red carpet for the many partners and collaborators who helped us piece this network together:
And let’s roll out the virtual red carpet for the many partners and collaborators who helped us piece this network together:
We took a whole-of-the-industry approach on this one: we’re grateful for partners at @Facebook @Quora @Twitter @Google @YouTube @Medium @reddit @Avaaz @BuzzFeed for help investigating and/or taking action on this network.
Note: this would not have been possible a few years ago, and while there is still plenty of work to do, it shows that we’ve made significant progress on the IO front.
We thought a lot about the right way to release this. We worked with affected platforms, shared drafts with academic colleagues, released assets for others to be able to reconstruct conclusions, etc. We hope this will contribute to best practices on researching and exposing IO.
 Coverage by @nakashimae & @craigtimberg for the @washingtonpost: https://twitter.com/nakashimae/status/1272908254260191236?s=20
Coverage by @nakashimae & @craigtimberg for the @washingtonpost: https://twitter.com/nakashimae/status/1272908254260191236?s=20
 And in the @WSJ, by @bobmcmillan https://www.wsj.com/articles/russia-linked-disinformation-campaign-spread-messages-across-multiple-platforms-to-elude-detection-new-report-says-11592319829
And in the @WSJ, by @bobmcmillan https://www.wsj.com/articles/russia-linked-disinformation-campaign-spread-messages-across-multiple-platforms-to-elude-detection-new-report-says-11592319829
 In @WIRED, @lilyhnewman on "The Russian Disinfo Operation You Never Heard About": https://twitter.com/lilyhnewman/status/1272909073386700801?s=20
In @WIRED, @lilyhnewman on "The Russian Disinfo Operation You Never Heard About": https://twitter.com/lilyhnewman/status/1272909073386700801?s=20
 And in the @nytimes through @AP's @DavidKlepper: https://www.nytimes.com/aponline/2020/06/16/business/ap-us-russia-disinformation-report-1st-ld-writethru.html
And in the @nytimes through @AP's @DavidKlepper: https://www.nytimes.com/aponline/2020/06/16/business/ap-us-russia-disinformation-report-1st-ld-writethru.html
 Loved the piece in the @thedailybeast by @arawnsley, and his thread for additional context and notes: https://twitter.com/arawnsley/status/1272907102474899459?s=20
Loved the piece in the @thedailybeast by @arawnsley, and his thread for additional context and notes: https://twitter.com/arawnsley/status/1272907102474899459?s=20
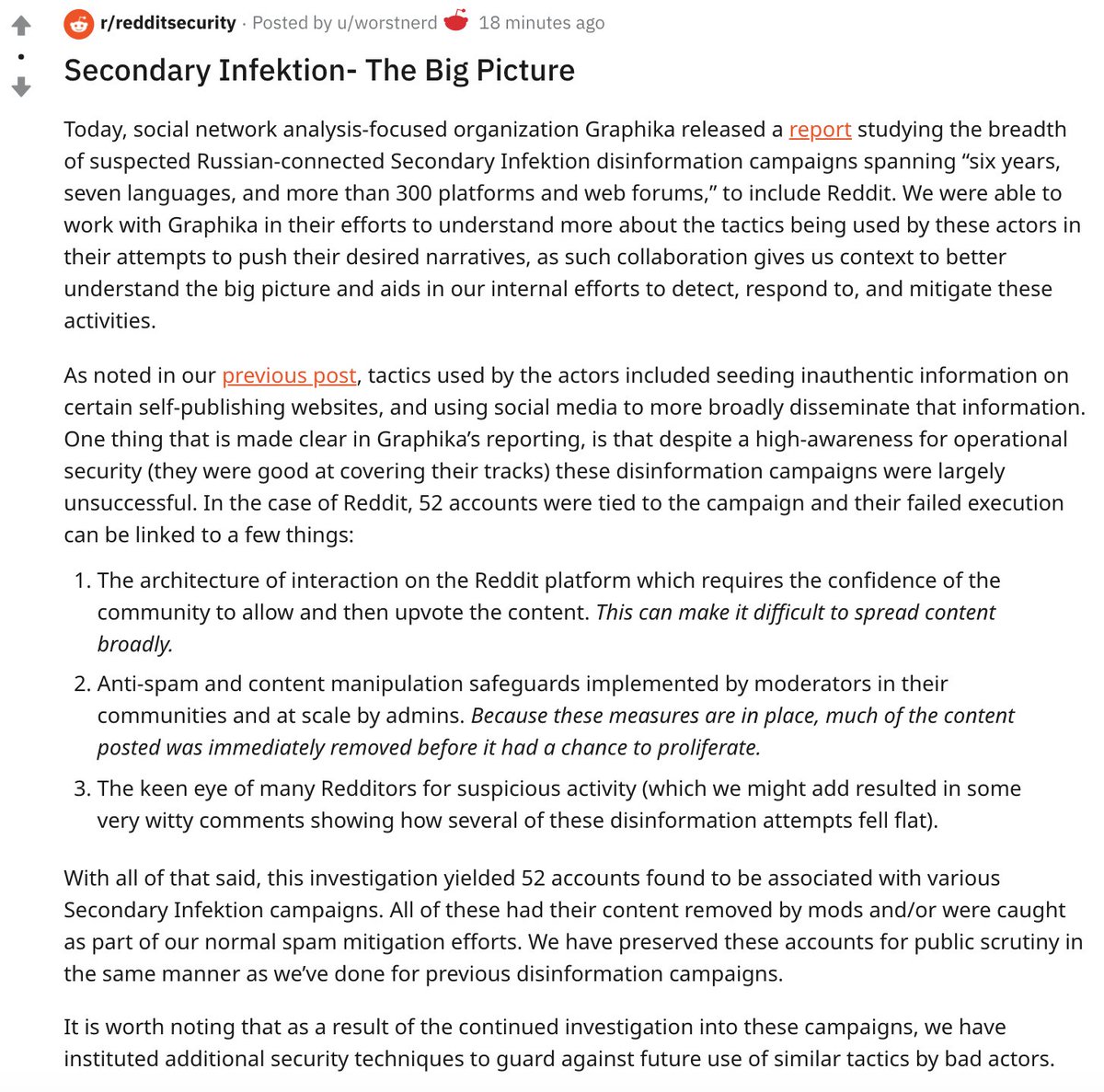
 And now up, a statement from the @reddit security team about our joint work on Secondary Infektion. Love the statement's name: "Secondary Infektion- The Big Picture".
And now up, a statement from the @reddit security team about our joint work on Secondary Infektion. Love the statement's name: "Secondary Infektion- The Big Picture".https://reddit.com/r/redditsecurity/comments/ha885d/secondary_infektion_the_big_picture/
 Zooming on this bit of the @reddit statement: "It is worth noting that as a result of the continued investigation into these campaigns, we have instituted additional security techniques to guard against future use of similar tactics by bad actors."
Zooming on this bit of the @reddit statement: "It is worth noting that as a result of the continued investigation into these campaigns, we have instituted additional security techniques to guard against future use of similar tactics by bad actors." Glad to see this impact!

 Et en français, thanks to @martin_u from @lemondefr: https://www.lemonde.fr/pixels/article/2020/06/16/secondary-infektion-une-vaste-mais-inefficace-campagne-de-manipulation-du-web-venue-de-russie_6043081_4408996.html
Et en français, thanks to @martin_u from @lemondefr: https://www.lemonde.fr/pixels/article/2020/06/16/secondary-infektion-une-vaste-mais-inefficace-campagne-de-manipulation-du-web-venue-de-russie_6043081_4408996.html

 Read on Twitter
Read on Twitter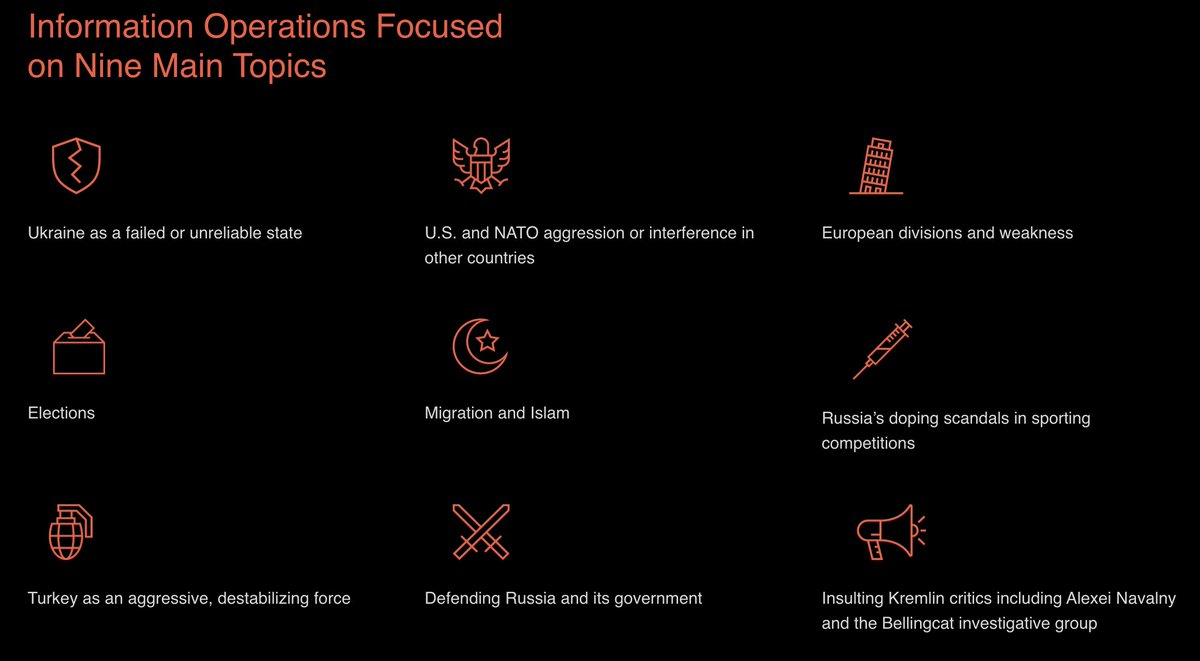

 somewhere on the website...
somewhere on the website...


