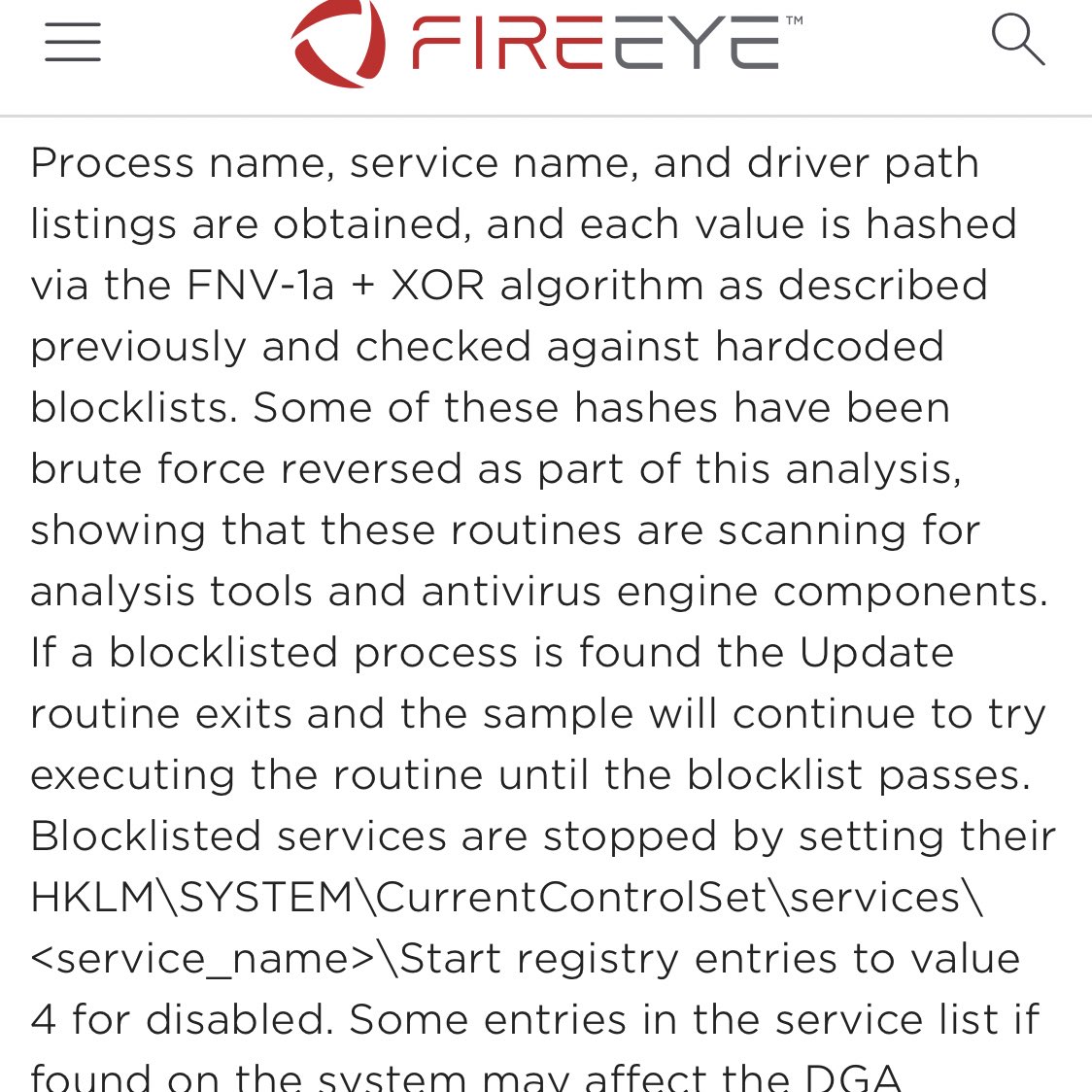
Watching a change roll-out across an organization eliminating irrelevant security exclusions is hugely rewarding. Normally these build-up over decades and nobody has the expertise or will to rock the boat to clean them out. Makes hiding by attackers in the noise so much easier.
Now there is a short, evidence-based exclusions list, and we don’t take preemptive requests. Modern security solutions are vastly more adaptive, and vendors only care about reducing support calls from people running Symantec 2003. They can’t be trusted to weigh your risks.
If you see a security exclusion on a server, does your entire team know if it’s legitimate? Do they know why it’s there?
If they saw an attacker change something, would they even notice? Or would it be hidden in the inexplicable cruft of your legacy debt?
If they saw an attacker change something, would they even notice? Or would it be hidden in the inexplicable cruft of your legacy debt?
Attackers don’t evade antivirus they’ll just fucking turn it off. Nobody is watching and they know it.
Until they run into me...

Fun fact: In one of the Microsoft antivirus policy documents they have a hidden note complaining about path-based exclusions in some other Microsoft documentation, then they proceed to recommend a more precise process-based exclusion instead.
It’s all cruft all the way down.
It’s all cruft all the way down.
I'm making myself look good by quoting myself saying things and comparing it to the FireEye report, but this isn't special.
This is evidence we collectively know how to do security right in theory, we have the fundamentals, it's not magic, it's operationalizing it that counts.
This is evidence we collectively know how to do security right in theory, we have the fundamentals, it's not magic, it's operationalizing it that counts.

 Read on Twitter
Read on Twitter